Week 7 - Security Testing
1/17
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
18 Terms
What is the goal of software testing?
verifying that software meets its functional and non-functional requirements
What is security testing?
Evaluating software against security requirements to identify vulnerabilities and verify security mechanisms.
Define Connectivity
e.g., cloud computing, location-based services
What is a vulnerability (ISO 27001)?
A weakness in assets that can be exploited by threats.
What are the two main types of security testing?
1. Static Testing – review without execution
a. Examples: code reviews, design reviews, static code analysis tools
2. Dynamic Testing – Execution-based validation
a. Run the software and compare actual vs expected outputs
What are the two main types of security testing purposes?
Security functional testing – validating security features work as intended.
Security vulnerability testing – identifying unintended system vulnerabilities.
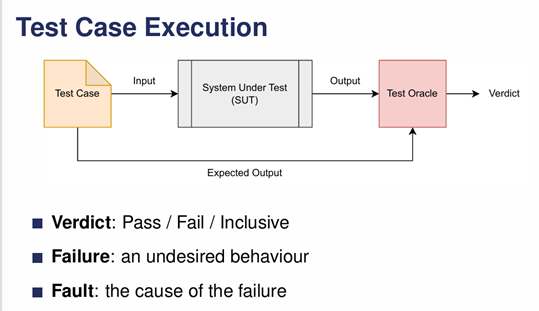
Describe a test case execution
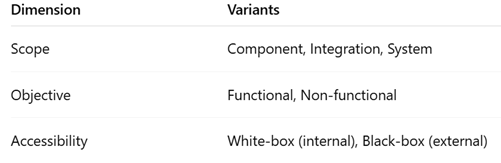
How would you describe testing dimensions diagram?
What is Model-Based Testing (MBT)?
A method where test cases are automatically generated from models representing expected system behaviour.
Why is security testing hard?
Traditional “librarian” approach = rerun known exploits (test cases from a database)
Problems:
Doesn’t find new vulnerabilities
Only catches known patterns
However, this works because developers repeat mistakes
What are the three key tasks in MBT?
Design a functional test model
Determine test generation criteria
Generate the tests
What is Model-Based Security Testing (MBST)?
MBT that incorporates attacker models, vulnerability models, and properties models (e.g., CIA goals).
What’s the difference between Exploitation and Attack?
Exploitation: Using malicious input to exploit a vulnerability.
Attack: Executing an exploitation to violate a security property.
Security Testers play the role of a hacker to exploit system’s vulnerabilities.
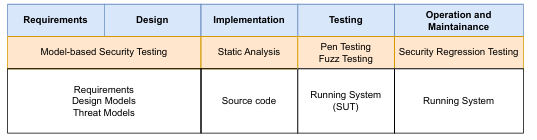
State the 4 security testing techniques in SDLC
what is an attack tree?
- A tree where:
o Nodes = attack goals or actions
o Edges = dependencies (AND, OR, SAND)
What is an Abstract Test Case (ATC)?
- A sequence of attack actions
- ATC succeeds if all steps succeed —> vulnerability confirmed
- ATC fails if attack is blocked —> protection works
Benefits of MBT:
- Early and explicit review of system behaviours
- Better documentation of test cases
- The ability to automatically generate useful tests and measure and optimize test coverage
what input models can we use for MBST?
- Attacker models – capabilities and attack goals
- Vulnerability models – known weaknesses encoded
- Security property models – what must not be violated