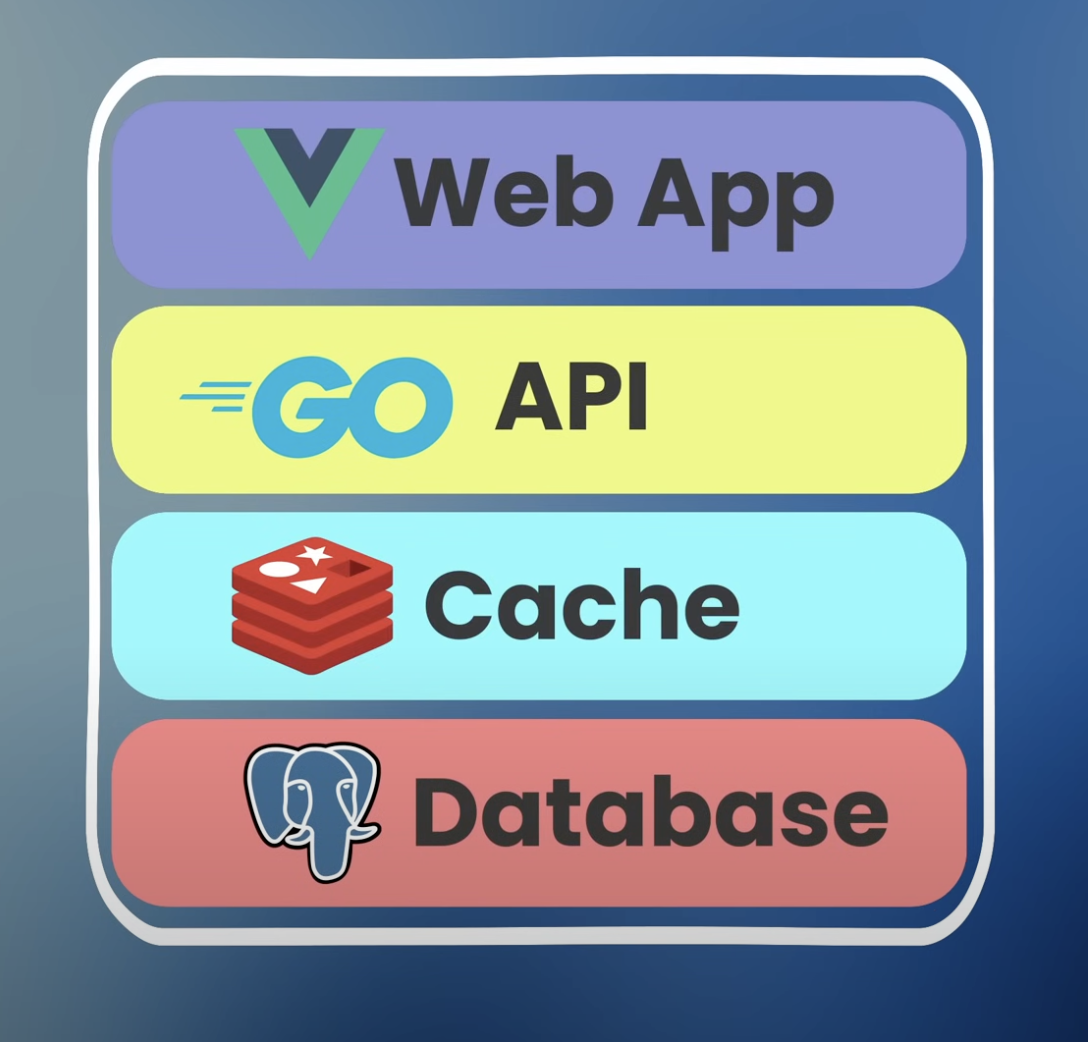
Full Stack Key Ideas (System Design)
1/16
Earn XP
Description and Tags
Some various key ideas in full stack / system design.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
17 Terms
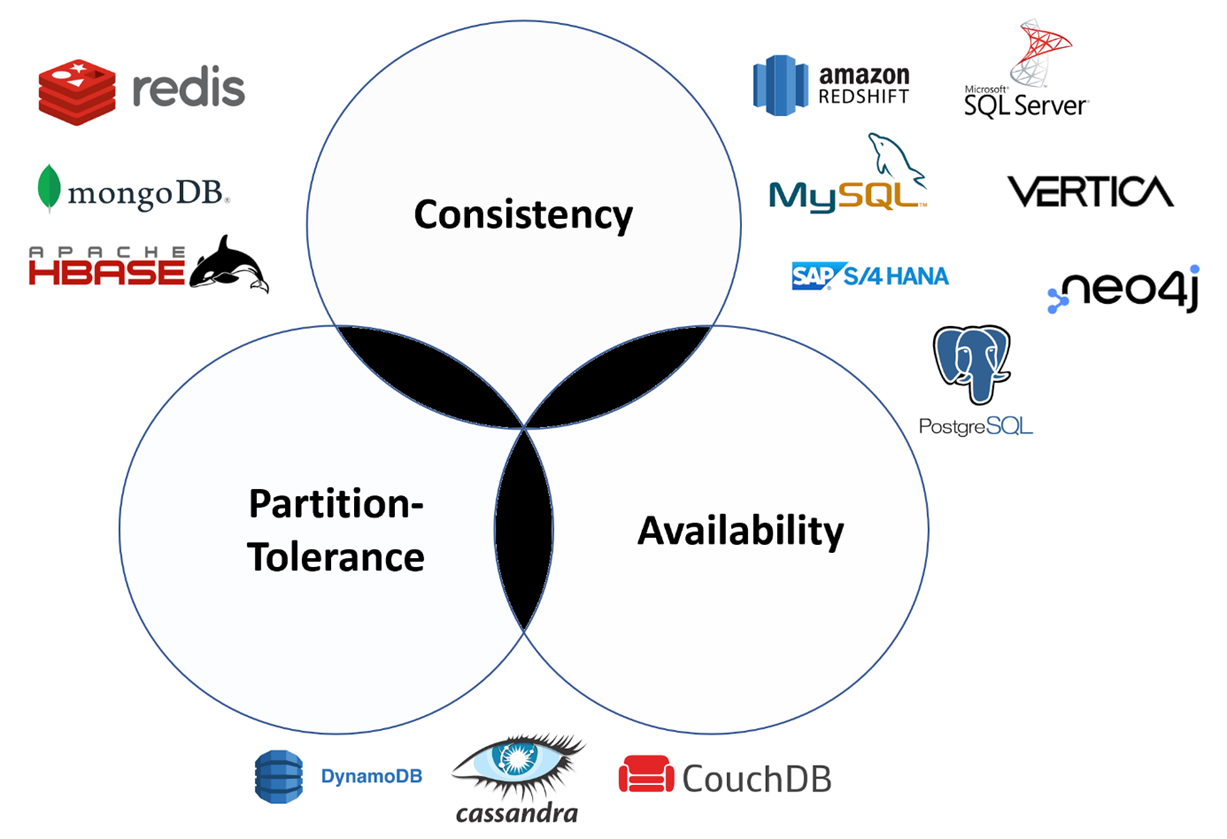
The CAP theorem
A Distributed system can deliver only two of three desired characteristics: consistency, availability and partition tolerance
C - data is the same across nodes
A - data is available even if some nodes are down
P - data is available even if there is a “partition” in communication between 2 or more nodes
https://medium.com/@kmrpushkar09/cap-theorem-explained-consistency-availability-partition-tolerance-19d151db54f3
https://stackoverflow.com/questions/36404765/why-isnt-rdbms-partition-tolerant-in-cap-theorem-and-why-is-it-available/64427972#64427972
Microservice Architecture
Microservice architecture is a design approach where an application is built as a collection of small, independent services.
Generally each service focuses on a specific business function
Server Penetration Testing
What is K6? What are the 4 types of pen tests in K6?
K6 - load testing tool that can be used to test the performance and reliability of systems
Loading testing - tests system performance under typical load
Stress testing - test gradual traffic increase to identify system limits
Spike testing - tests how the system handles sudden and extreme traffic increases
Soak testing - tests long term run times for memory leaks, usage, cpu usage etc..
Picking a Backend Language
JavaScript - Useful for a full-stack development team.
Python, Ruby - Rapid prototyping & fast development cycles. Good for internal tools especially
Java, C# - Large enterprise level systems.
Go, Rust - performance critical OR concurrent application
Picking a Database
SQL - Best for apps that requires complex queries, transactions or reporting. Anything relational. Would i put it in an excel spreadsheet? Ex) Banking systems, ecommerce apps.
NoSQL - Best for apps that need flexible data models & real-time analytics.
Fallicies of Distributed Systems
The network is reliable:
This assumption overlooks the reality of network failures, including connection drops, hardware issues, and intermittent outages. In practice, applications need to account for retries, timeouts, and error handling to maintain reliability.
Latency is zero:
This fallacy assumes instant communication between nodes, but real-world networks introduce latency. Latency affects data synchronization, responsiveness, and performance, especially across large distances or high traffic networks.
Bandwidth is infinite:
The assumption here is that the network can handle unlimited data transfer. In reality, bandwidth is finite, and congestion can slow down data transmission. Systems must be designed to handle varying bandwidth limits and prioritize data as needed.
The network is secure:
Complacency regarding network security results in being blindsided by malicious users and programs that continually adapt to security measures.
Topology doesn’t change:
This fallacy assumes a static network structure, but in reality, networks evolve, with nodes joining, leaving, or changing locations. Distributed systems need to dynamically adapt to changes in topology to remain functional.
There is one administrator:
This assumption overlooks the complexity of administrative control in distributed systems, often involving multiple administrators with differing permissions. Role-based access control and clear governance are necessary to manage this effectively.
Transport cost is zero:
Assuming no cost for data transfer ignores both monetary costs (e.g., cloud data transfer fees) and resource costs (e.g., CPU, memory). Optimizing data transfer reduces these costs and improves efficiency.
The network is homogeneous:
This fallacy assumes all nodes are identical in terms of performance, location, and capabilities. However, networks are often heterogeneous, with a variety of devices, configurations, and power. Distributed systems must handle differences in node capabilities and manage compatibility.
https://en.wikipedia.org/wiki/Fallacies_of_distributed_computing
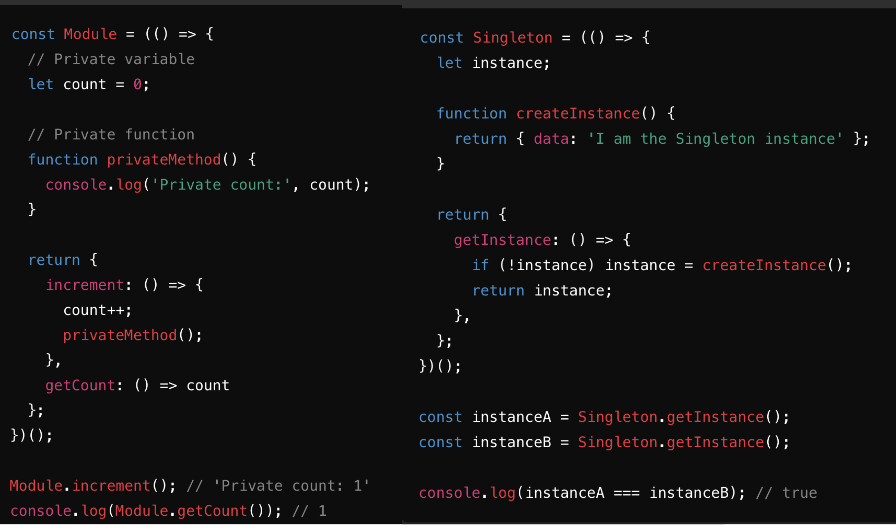
Javascript IIFE.
The Singleton & Module Instantiation Patterns.
The Singleton pattern restricts the instantiation of a class to a single object. It’s useful when exactly one instance of a class is needed to coordinate actions across a system, such as for configuration settings, caching, or logging.
The Module pattern encapsulates private variables and functions while exposing only the public API, enabling modular and organized code. It leverages closures to create private state, often used for organizing code into logical units like services or utilities.
IIFE - Immediately Invoked Function Expression
Javascript Scopes.
Closure & Hoisting
Block vs Function Scope.
Closure - A closure is a feature in JavaScript where an inner function has access to its outer function’s variables, even after the outer function has finished executing
Hoisting - Hoisting is a JavaScript mechanism where variable and function declarations are moved to the top of their containing scope (either the global scope or a function scope) during the compile phase.
ES6 let/const vars sit at block-scope which is anything wrapped in a block “{…}”. The ES5 var variable sits at function scope. When hoisted ES5 var is set to undefined, while let/const sit in a “Temporal Dead Zone” and will trigger a reference error if attempted access.
Graph Algorithms Big 3
Dikstra’s
Breadth-First Search (BFS)
Depth-First Search (DFS)
BFS explores nodes level by level, starting from a source node. It is used to find the shortest path in an unweighted graph and can be implemented using a queue.
Time Complexity: O(V + E), where V is the number of vertices and E is the number of edges.
DFS explores as far down a branch as possible before backtracking. It is used for tasks such as finding connected components, topological sorting, and pathfinding.
Time Complexity: O(V + E)
Dijkstra’s Algorithm: Finds the shortest path between two nodes in a weighted graph with non-negative edge weights. It uses a priority queue to greedily select the next node with the smallest tentative distance.
Time Complexity: O(V^2) (with an unoptimized priority queue), O(E + V log V) with a min-heap.
Used to find the shortest paths in networks, such as GPS or internet routing
Data Structure - Graph’s
(un)directed, (un)weighted, (a)cyclic & (un)connected
Representations.
Directed vs. Undirected: In a directed graph, edges have a direction (from node A to node B), while in an undirected graph, edges are bidirectional.
Weighted vs. Unweighted: In a weighted graph, edges carry a weight or cost, representing something like distance or time. In an unweighted graph, all edges are considered equal.
Cyclic vs. Acyclic: A cyclic graph has at least one cycle (a path that starts and ends at the same node), while an acyclic graph has no cycles.
Connected vs. Disconnected: A connected graph has a path between every pair of nodes, while a disconnected graph does not.
Graph Representation:
Adjacency Matrix: A 2D array where the element at [i][j] is non-zero if there is an edge between nodes i and j.
Adjacency List: A list of lists, where each node has a list of adjacent nodes.
PWAs (Progressive Web App) & Chrome Extensions.
PWAs are built on top of modern web technologies but provide a native-like experience
- The core feature of a PWA is its offline-first capability, enabled by service workers. These are JavaScript files that run in the background, intercepting network requests, caching resources, and enabling the app to work offline or with poor connectivity
- Responsive Design, Lazy loading, native feel
Chrome Extensions can modify the content of web pages by injecting content scripts. This allows frontend developers to improve or extend the UI and UX of the sites users are visiting, without modifying the underlying code of the page itself.
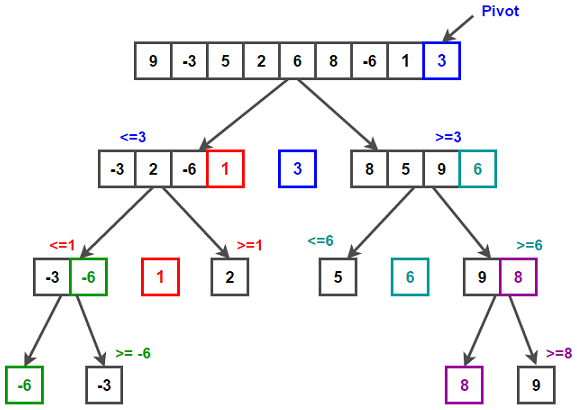
Quicksort & Partition Algorithm.
Time Complexity - O(n*log(n)) in the best and average cases, and O(n^2) in the worst case → happens when bad pivots chosen.
Space Complexity - Can be done in place for O(1) space.
Quicksort is a divide-and-conquer algorithm that sorts an array by partitioning it into smaller sub-arrays based on a pivot element. The partition algorithm rearranges the elements so that those less than the pivot come before it and those greater come after.
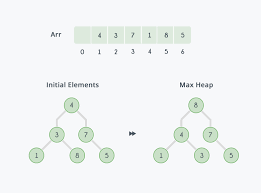
Heap sort
Heapsort is a comparison-based sorting algorithm that uses a binary heap data structure. The algorithm is as follows
1. Build a max heap from array. The maximum element is now in its correct position. → O(n)
2. Call “Heapify” on the remaining elements to rebuild the max heap → O(log n). Repeat until heap size 1.
The max heap can be represented in place in the array."
Heap sort is not a stable sort meaning equal elements may not end up in the same order once sorted.
Auxiliary Space & Space Complexity.
Space Complexity - The amount of space relative to input size an algorithm takes. Ex): Input: [0..n] → Complexity O(n)
Auxiliary Space - The extra space or temporary space used by an algorithm apart from the input data. Example in a merge sort we use additional arrays to hold the merged output, leading to a complexity of O(n).
Redis
What is it? How does it work? How should it be used?
Redis is an open-source, in-memory data structure store, often used as a database, cache, and message broker. It works by storing data in key-value pairs and supports various data structures such as strings, hashes, li
sts, sets, and sorted sets, enabling fast access and manipulation of data.