CompTIA A+ Test Corrections 1 >:p
1/36
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
37 Terms
DOS
Disk-based CLI OS from 80s-90s replaced with GUI systems
Windows can be a
PC and mobile OS
System Configuration
A Windows utility (msconfig.exe) that can identify what processes are launched at startup and can temporarily disable a process from loading.
What to do if Windows Defender starts blocking software/updates?
add an exception
Best physical laptop threat protection
Bitlocker (or disk encryption in general)

Implicit allow/deny
automatically denies all traffic unless explicitly permitted; minimizes unauth access
Explicit allow/deny
requires specific perms be set for access; more labor-intensive
LCD vs OLED
LCD: lightweight, low power, inexpensive, difficult to replace lights
OLED: thinner and lighter, no glass, accurate color, used on smartphones/tablets, emits light when receiving an electrical current
VA LCD
good color, slower response times
NFC
considered secure b/c of short distance and can be used to automate tasks (e.g, alarm silencing or logging into device)
Mobile display components
LCD, digitizer (turns physical input into electrical signals), glass cover
When to replace mobile display
When one component breaks
MAM and MDM
safeguards corporate data by managing all mobile devices on a corporate network
NFC support on iPhones
iPhone 6 and older: NFC only w/ Apple Pay
iPhone 7 and newer: 3rd party app for read/write NFC tags
iPhone12 and newer: Built-in NFC tag capabilities
2.4GHz vs 5GHz
5GHz: greater bandwidth, faster, more interference
2.4GHz: frequency have greater range, lower data transmission rates, 3 non-overlapping channels
Wireless Internet Service Provider
also called long-range fixed wireless: installed in areas with little to no wired infra (rural)
Default gateway/router internal address
address to the network's router
A router has both
an internal and external address
internal address
The private IP address that is translated to an external IP address by NAT (remains hidden by NAT).
External address
The public IP address that NAT uses to communicate with the external network.
What does the CPU require in order for virtualization to be enabled?
SLAT
Dual channel motherboard
4 memory slots, two RAM banks with two slots each
same channels are color-coded
Single RAM still works when on dual channel MB
Duplex fiber connectors
SC & LC
SC connector
- Type of connector used in fiber optic cabling.
- Snap-in with 2.5 mm ferrule.

LC Connector
- Type of connector used in fiber optic cabling.
- Uses a connector likened to RJ-45. It has a smaller form factor and uses 1.25 mm ferrule.
- Preferred for single mode.

VM Sprawl
occurs when an organization has many VMs that aren't managed properly (uncontrolled growth)
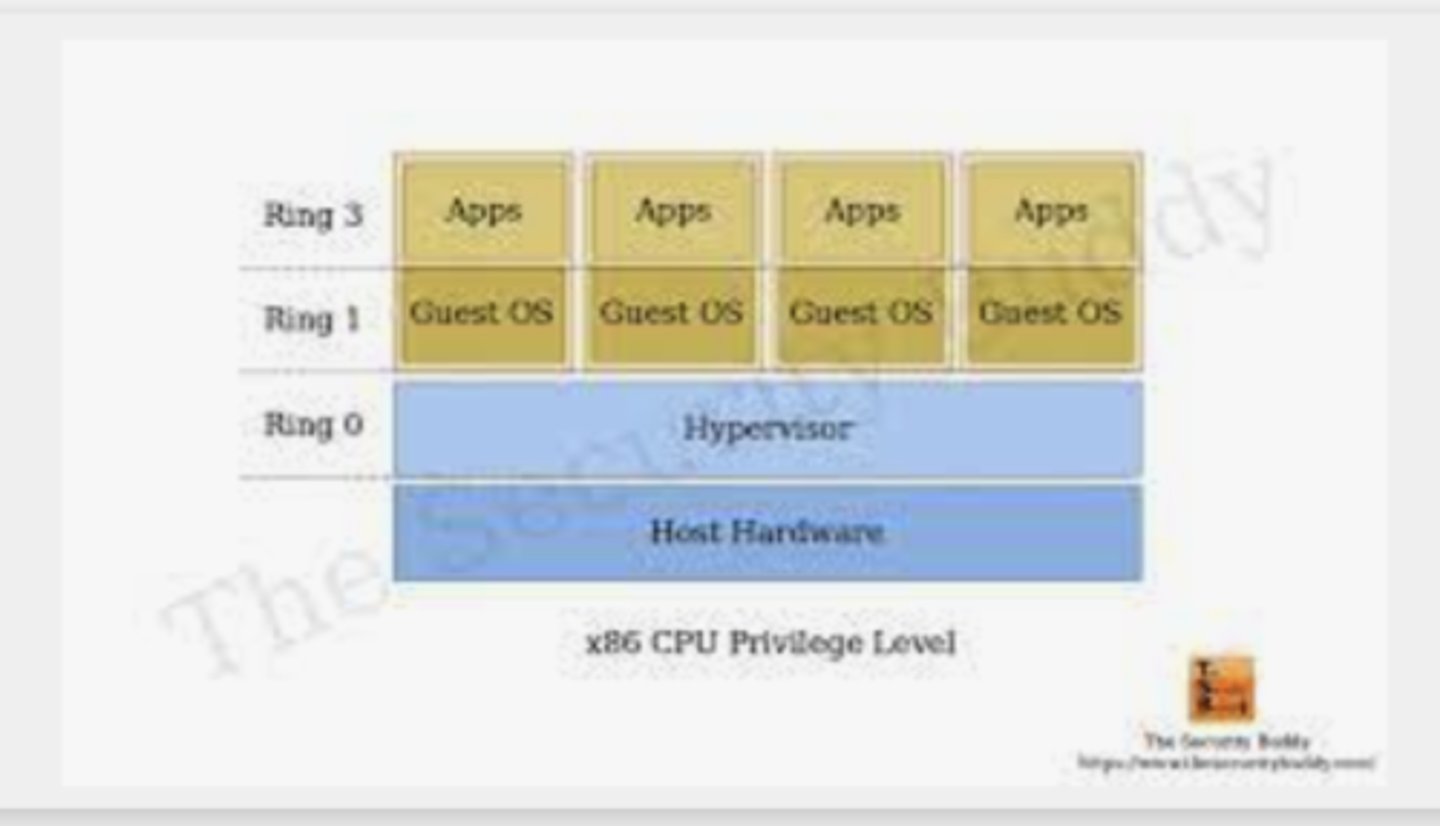
VM Sprawl Avoidance
A policy for developing and deploying VMs must be established and enforced.
On-premises vs Cloud VDI
On-premises: hosted on local server
Cloud VDI: stored on remote server
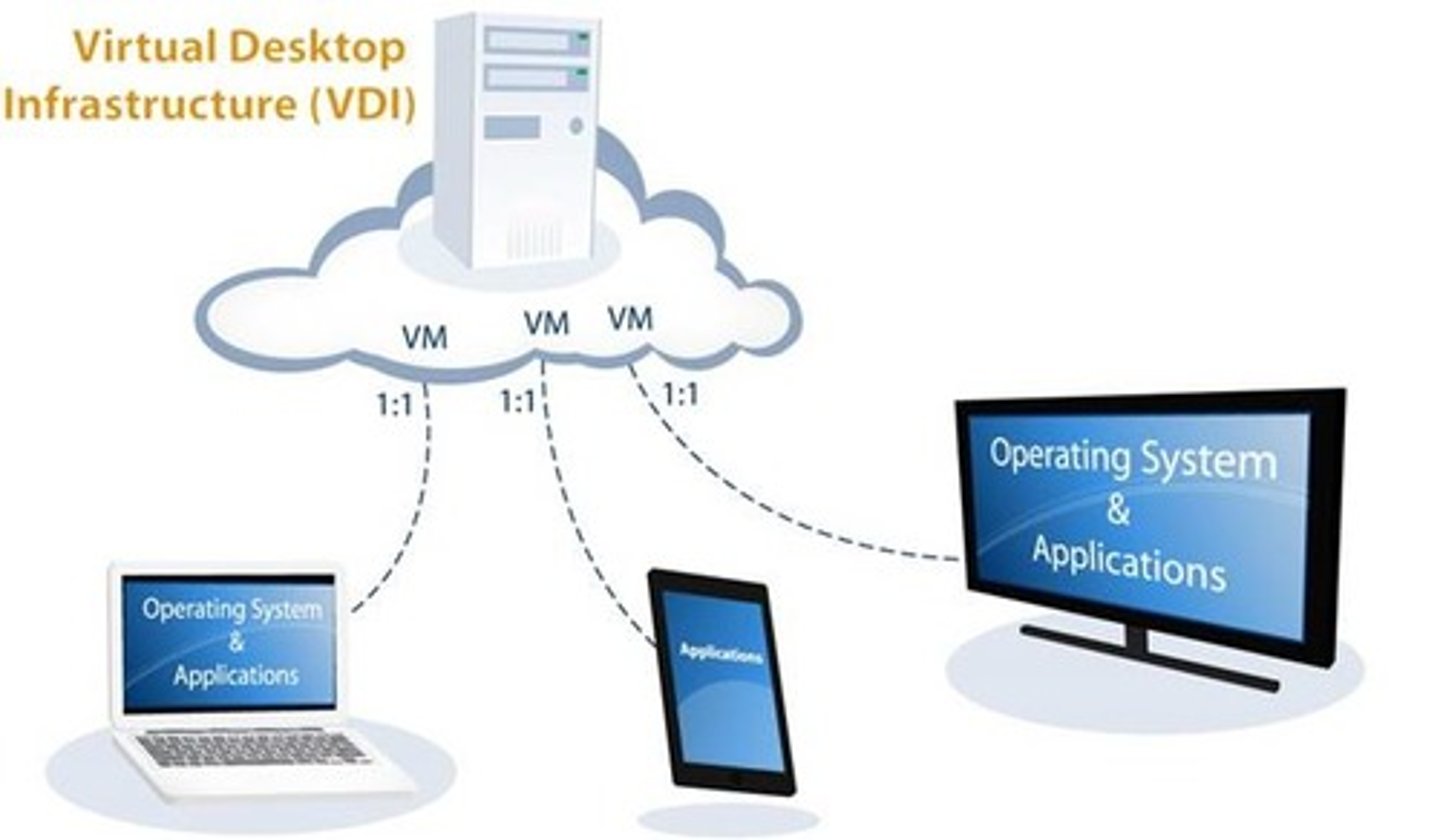
VDI (Virtualization Desktop Infrastructure)
Virtualization software designed to reproduce a desktop operating system as a virtual machine on a remote server.
VM Escape
An attack that allows an attacker to access the host system from within a virtual machine.
VM Escape Protection
The primary protection is to keep hosts and guests up to date with current patches.
NAT mode
VM obtains IP addressing information from its host
NAT Network
Can create a virtual network within the VM that has buffer to the outside world using NAT
Bridged Mode
- vNIC accesses physical network using host machine's NIC
- Obtains own IP address, default gateway, and netmask from DHCP server on physical LAN
host-only mode
VMs communicate only with each other and host.
Internal Network
A virtual network that can be accessed by virtual machines and the Hyper-V host.
Broken components that can cause ghosting
cleaning blade and erasure lamps