2.4 - CompTIA A+ Core 2
1/22
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
23 Terms
Malware
Malicious software designed to harm or impede regular computer functions.
Trojan

Malware disguised as a non-malicious file that tricks users into executing it; not focused on replication - they are typically spread by social engineering.
Rootkit

Malware that embeds deep into operating systems, modifying core system files; may require a specific AV tool for removal.
Virus

Malware that replicates from computer to computer but needs human execution to start.
Spyware
Software designed to gather information without the user's knowledge, often used for tracking online activity.
Ransomware
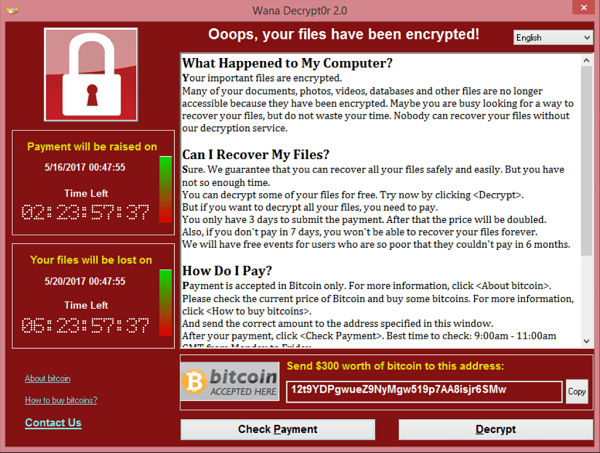
Malicious software that encrypts files, demanding ransom for decryption while keeping the OS running.
Keylogger

Malware that captures keyboard input to obtain sensitive data such as usernames and passwords.
Boot sector virus
A virus that embeds itself into the boot sector of a hard drive, relaunching every time the operating system starts.
Cryptominer

Malware that utilizes the victim's computer resources for cryptocurrency mining.
Stalkerware
Malware designed for unwanted surveillance of individuals, often operating in stealth mode.
Fileless malware
Malicious software that operates in system memory, leaving no trace on the hard drive.
Adware
Software that displays or downloads unwanted advertising material when online.
Potentially unwanted program (PUP)
A program that may be unwanted, often downloaded alongside desired software.
Windows Recovery Environment
A command line environment that operates from the recovery partition and allows full administrative control over Windows, enabling malware removal before the system boots.
Endpoint detection and response (EDR)
Security solution that continuously monitors for and responds to advanced threats on endpoints.
Managed detection and response (MDR)
Service using human expertise and automated tools to monitor, detect, and respond to threats.
Extended detection and response (XDR)
Cybersecurity approach integrating data from multiple sources (endpoints, networks, cloud, etc.) to provide a comprehensive view of threats.
Antivirus
Software designed to identify, contain, and remove viruses from systems.
Anti-malware
Software designed to identify, contain, and remove malware from systems.
Email security gateway (SEG)
Product that analyzes and filters malicious emails before they reach users' inboxes.
Software firewall
Software controlling network communications, preventing malware from accessing an OS.
Antiphishing training
Training that helps users recognize and avoid phishing attempts and suspicious activities.
OS reinstallation
Reinstalling an operating system to remove a malware infection, or restoring from a backup.