2.4 - CompTIA A+ Core 2
2.4a - Malware: Professor Messer
Malware
Malware: Malicious software - programs designed to harm/impede regular computer functions.
How to avoid malware: Keep your OS updated, and avoid suspicious applications/hyperlinks.
Trojan

Trojan: Malware disguised as a non-malicious file that tricks users into executing it. Replication is not a priority for Trojans - they are typically spread by social engineering and circumvent existing security, although some AV programs may catch them when they run.
Rootkit

Rootkit: Malware designed for Unix/Linux systems that embed themselves deep into operating systems, sometimes into OS kernels, and modify core system files. Not commonly seen on most systems due to the secure boot functionality for UEFI BIOSes, and can be removed with a rootkit-specific AV tool.
Virus

Virus: Malware that can replicate from computer to computer, but it needs human execution to start (i.e., executing a program) - viruses often replicate through a network or through removable drives (e.g., USB drives).
Spyware
Spyware: Software designed to gather information from a computer without the user's knowledge, often used to track online activity or steal personal information.
Ransomware
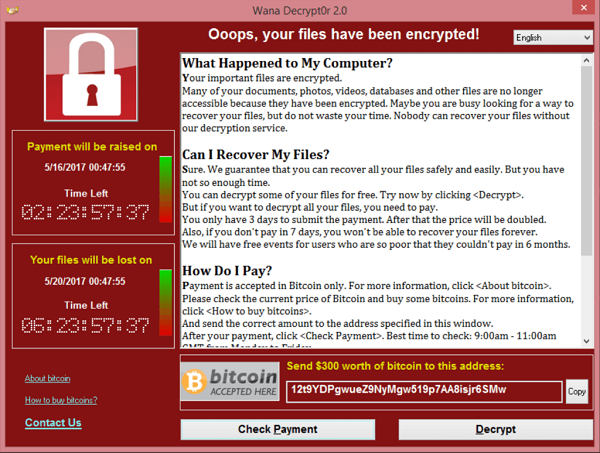
Ransomware: Malicious software that encrypts a user's files, rendering them inaccessible until a ransom is paid to the attacker. Still leave the OS running - delete all files available to remove the ransomware and restore from a known good backup to ensure that no remnants of the ransomware
Keylogger

Keylogger: Malware designed to capture a user’s keyboard input and on-screen information to obtain sensitive data such as usernames, passwords, and credit card information.
Boot sector virus
Boot sector virus: A virus that embeds itself into the boot sector of a hard drive and is able to relaunch every time the operating system begins (boots). Also prevented by Secure Boot in a UEFI BIOS.
Cryptominer

Cryptominer: Malware designed to utilize the victim’s computer resources for cryptocurrency mining.
Stalkerware
Stalkerware: Malware/spyware designed for the unwanted surveillance of individuals, often working in stealth mode or otherwise not visible to the user.
Fileless
Fileless malware: A type of malicious software that operates in the memory of the system (e.g., Metasploit Meterpreter shells), leaving no trace on the hard drive and making detection by traditional antivirus programs more difficult.
Adware
Adware: Software that automatically displays or downloads unwanted advertising material when a user is online.
Potentially unwanted program (PUP)
Potentially unwanted program (PUP): A potentially unwanted program (PUP) is a program that may be unwanted, despite the possibility that users consented to download it. Often downloaded in conjunction with a program that the user wants.
2.4b - Anti-Malware Tools: Professor Messer
Tools and methods
Recovery Console/environment/modes
Windows Recovery Environment: Windows command line that operates from the recovery partition (typically X:, or some other drive letter), instead of the traditional C: drive. Allows the user to remove malware before the system boots - very powerful and should be used as a last resort.
Endpoint detection and response (EDR)
Endpoint detection and response (EDR): A security solution that continuously monitors and responds to advanced threats on endpoints, providing real-time threat detection, investigation, and remediation capabilities.
Managed detection and response (MDR)
Managed detection and response (MDR): A service that leverages human expertise and automated tools to monitor, detect, and respond to threats, often providing a more comprehensive security approach than traditional EDR solutions.
Extended detection and response (XDR)
Extended detection and response (XDR): A cybersecurity approach that integrates data from multiple tools and layers (endpoints, networks, cloud, etc.) to provide a holistic view of threats.
Antivirus
Antivirus: Software designed to identify, contain, and remove viruses from computer systems. Often bundled with anti-malware software. Modern systems have behavior detection capabilities and don’t require a specific set of signatures.
Anti-malware
Anti-malware: Software designed to identify, contain, and remove malware from computer systems. Often bundled with antivirus software. Modern systems have behavior detection capabilities and don’t require a specific set of signatures.
Email security gateway
Email security gateway (SEG): Email security product that analyzes malicious emails and filters them before they reach a user’s inbox.
Software firewalls
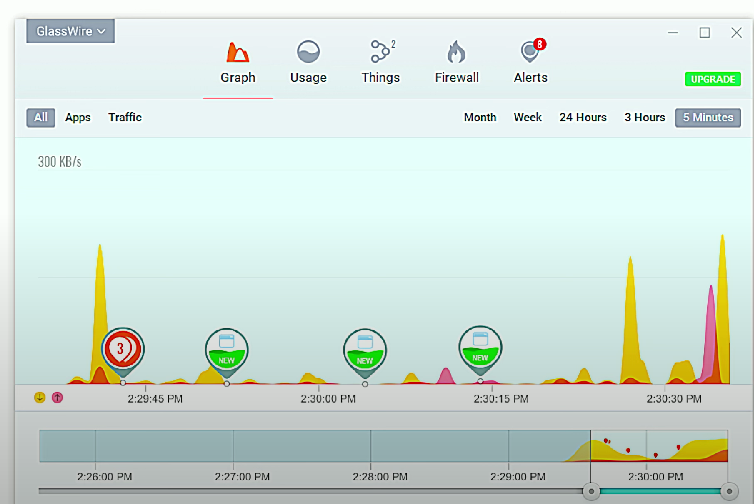
Software firewall: Software that controls incoming and outgoing network communications for malicious activity, preventing malware from accessing an OS via a network.
User education regarding common threats
Antiphishing training: Extensive training to help users recognize and avoid phishing attempts, including suspicious emails and websites that may compromise their personal information, along with social engineering techniques.
OS reinstallation
OS reinstallation: Reinstalling the entire operating system to remove a malware infection. Alternatively, you can restore the system from backup, as long as the backup is not infected.