Computer Science Y9 EOY Exam Revision
1/73
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
74 Terms
What is the Copyright Designs and Patent Act of 1998?
It is illegal to copy, modify or distribute software, music, videos or other intellectual property without permission from the author.
What is the Data Protection Act of 2018?
Personal data must be fairly and lawfully processed
Personal data must be obtained for specified, explicit and legitimate purposes
Personal data must be adequate, relevant and not excessive
Personal data must be accurate and up to date
Personal data must not be kept for longer than is necessary
Personal data must be handled in a way that ensures security
What is the Computer Misuse Act?
So to make sure the people who gain access to our data without permission are prosecuted the UK Parliament created the Computer Misuse Act which made three new offences:
1) Accessing computer material without permission.
2) Accessing computer material without permission with intent to commit further criminal offences.
3) Altering computer data without permission.
What number system do humans use?
Base 10 (denary)
What numbers does Base 10 use?
0 to 9 (inclusive)
What number system do computers use?
Base 2 (binary)
What are the binary place values going from left to right?
128 64 32 16 8 4 2 1
Convert 88 into binary
010001110
What are the binary addition rules?
0 + 0 = 0
0 + 1 = 1
1 + 1 = 0 carry 1
1 + 1 + 1 = 1 carry 1
What is 'overflow' in binary addition?
When we add binary numbers together and we end up with a number that is too big to hold in 1 byte.
What number system does hexadecimal use?
Base 16
What is 10, 11, 12, 13, 14 and 15 (denary) equal to in Hexadecimal?
A, B, C, D, E and F
Convert 87 into Hexadecimal.
87/16 = 5 remainder 7
So: 57
Convert F3 into denary.
F = 15, So: 15x16 = 240 3 x 1 = 3 240 + 3 = 243
What is ASCII?
American Standard Code for Information Interchange
What is the ASCII value for A?
65
What is the ASCII value for Space?
32
What are all digital images made up of?
Tiny squares called pixels
What number represents white?
1
What number represents black?
0
How many colours would a colour depth of n create?
2ⁿ
In a colour depth of two, what is the binary number for black, white, blue and red?
Black: 00
White: 11
Red: 10
Blue: 01
In a colour depth of three, what are the binary numbers for all colours?
Black: 000
Blue: 001
Green: 010
Cyan: 011
Red: 100
Magenta: 101
Yellow: 110
White: 111
What is resolution?
The resolution of an image is a way of describing how tightly packed the pixels are.
What is compression?
Compression is the process of encoding, restructuring or otherwise modifying data in order to reduce its size.
What are the 2 types of compression?
Lossy & Lossless
What is lossy compression?
Lossy compression removes data permanently, so the file can never return to its original form; this reduces the size of a file.
What is lossless compression?
Lossless compression reduces the size of a file without any damage to the file or reduction in quality; however it doesn't reduce the file size as much as lossy compression.
What is a cipher?
A cipher is a way of disguising a message.
What is a Caesar cipher?
A substitution cipher that shifts characters a certain number of positions in the alphabet.
What is Brute Force?
An attempt to gain access by bombarding it with guesses until the password is found.
What is a box cipher?
The box cipher is a cryptographic technique that arranges plaintext characters in a grid, then applies transposition and permutation to encrypt the message.
What is a Vignere cipher?
The Vigenère cipher is a polyalphabetic substitution cipher that encrypts plaintext by shifting each letter according to a keyword, repeating the keyword if necessary, providing stronger encryption than simple monoalphabetic ciphers.
What is a substitution cipher?
The substitution cipher is a method of encryption where each plaintext character is replaced with a corresponding ciphertext character based on a fixed system, typically a one-to-one mapping of letters in the alphabet.
What is a keyboard cipher?
The keyboard cipher is a simple encryption technique that involves shifting characters by a fixed number of positions on a keyboard layout to generate ciphertext from plaintext.
What is a book cipher?
The book cipher is a cryptographic method that encodes plaintext by referencing specific words or passages in a pre-agreed book, where each word or phrase corresponds to a particular letter or group of letters in the message, offering a form of encryption through association with literature.
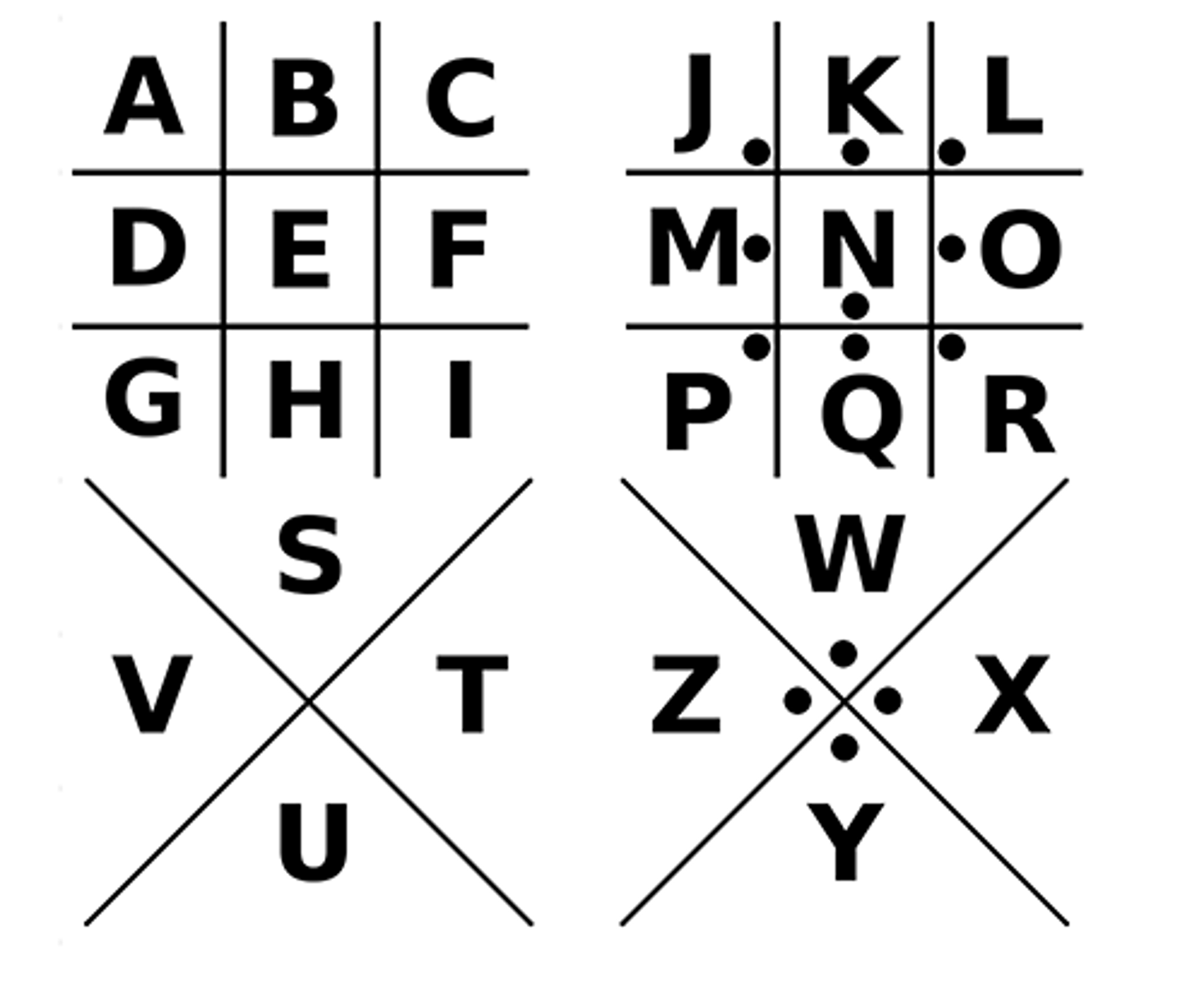
What is a pigcode cipher?
The Pigpen cipher, also known as the Masonic cipher, is a substitution cipher that replaces letters with symbols based on a grid of lines and dots, often resembling pigpens, to obscure the plaintext message.
What is symmetric encryption?
Encryption where two people agree on a key in private beforehand, and then send messages using that key. The same key is used to encrypt and decrypt that message.
What is asymmetric encryption?
Where there is a public key, that is accessible to everyone, so that they can encrypt their messages, but only one person has the private key to decrypt the messages.
What is a public key?
A key that is open to the public and can be accessed by anyone to encrypt a message.
What is a private key?
A key that is only accessible to one person and only they can decrypt the messages that were sent using the public key.
What is sequence in python?
A program that runs in order.
What is selection in python?
When a program will need to make a decision based on an input, or as the result of a calculation.
What is iteration in python?
When all/some of the program has to repeat. This can be done in two ways: count-controlled (for loop) or condition-controlled (while loop)
What is a variable?
A temporary place to hold data that can be changed.
What do x,y,z mean in the following code:
for i in range(x,y,z)
print(i)
x is the start the point (inclusive)
y is the end point (exclusive)
z is the step (how much it increments by)
When printing in python, what will this print? print(name, "owes £", amount) name = Dave amount = 3.50
Dave owes £ 3.50
When using a comma, you can't control the spacing.
When printing in python, what will this print? print(name + "owes £" + str(amount))name = Dave amount = 3.50
Dave owes £3.50 When using a plus, you can control the spacing, but you need to cast into a string before concatenating the strings.
What do str(), int(), and float() do and what is this process called?
str() converts anything in the brackets to a string
int() converts anything in the brackets to an integer
float() converts anything in the brackets to a float
This process is called casting.
What are the symbols for mathematical operations in python?
+ is addition
- is subtraction
* is multiplication
/ is division
** is exponentiation (powers)
// is integer division (only integers, no remainders/decimals)
% is modulo (only gives the remainder)
What do the following symbols mean?:
'=='
'!='
'>='
'<='
Equal to
Not equal to
Greater than or equal to
Less than or equal to
What are the logical operators in python?
and, or, not
What are the 2 types of search algorithms?
Linear and Binary
How does the Linear searching algorithm work?
1) Find out the length of the data set.
2) Set the position to 0.
3) Check the value held in the position.
4) Does it match our search value? If it does, the value is found. End the search.
5) If not, add 1 to the position value and repeat from step 3.
6) If we have reached the length of the data set, search value not found.
It checks each value in the data set until the search value is found.
How does the Binary searching algorithm work?
1) Find the length of the data set
2) Calculate the midpoint of the data set.
3) Use this as search position.
4) If the search value is found, the search ends.
5) If the value at the midpoint is less than the value to be found, the list is divided in half. The lower half of the list, with midpoint is ignored and the search keeps to the upper half of the list.
6) Otherwise, if the value at the midpoint is greater than the value to be found, the upper half, with midpoint of the list is ignored and the search keeps to the lower half of the list.
7) The search moves to the midpoint of the remaining items, if length of data is greater than 0. Repeat the process from step 2.
If length of the data set reached and no value found, end the search.
THE DATA MUST BE ORDERED.
How does the bubble sort algorithm work?
It looks at two elements and swaps them if they in the wrong order. For example, if I had the list: 1 5 3 6 2
The algorithm would first check 1 and 5. It would leave them and move on. Then it would check 5 and 3. It would swap them around. It would check 5 and 6. It would leave them and move on. It would then check 6 and 2, and swap them around. A PASS has been completed. The algorithm would then repeat the process until there are no swaps required for a pass to happen.
How would you print 'John' from the list?: friends = [Alex', 'William', 'John', 'Harry']
print(friends[2])
What does 'len' do?
Calculates the length of a list.
How would you add an item to the end of a list?
listname.append(item)
How would you add an item to a list at a specific position?
listname.insert(position, item)
How would I remove an item from a list?
del listname[position]
How would I sort a list?
listname.sort()
What are the two sub-programs in python?
Function and Procedure
What is the difference between a function and a procedure?
What is the difference between a function and a procedure?
A function returns a value. A procedure prints out a value.
How do you create a sub-program?
You use the keyword def:
def functionname():
What is an parameter?
A variable in a function that takes in an input.
def function(variable):
variable is the parameter
What is an argument?
The value that is held in the parameters of the sub-program.
def function(variable):
print(variable)
What would this sub-program print?
def function(a,b):
print(a+b)
function(7,9)
16
What would this sub-program print?
def function(a,b):
return(a*b)
variable = function(3,4)
print(variable)
12
What is a bit?
A binary digit, a 0 or a 1.
What is a nibble?
Half a byte or 4 bits
What is a byte?
8 bits
What is a kilobyte?
1024 bytes - this continues for every subsequent prefix.
What is the order of prefixes?
Bit, Nibble, Byte, Kilobyte, Megabyte, Gigabyte, Terabyte, Petabyte, Exabyte, Zettabyte, Yottabyte, Ronnabyte, Quettabyte