CoSCi 2023 Past Paper THEORY
1/36
Earn XP
Description and Tags
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
37 Terms
An office building has desktop computers connected in a network.
One reason for networking computers is to enable technicians to maintain
them remotely.
State two other reasons for connecting computers in a network
Access the Internet
Allow data/files/information to be shared
Provide communication (email, social media, online meeting, chat)
Provide collaboration (editing online docs)
Access to data must be controlled.
Identify one reason that encryption is used.
A To compress the file so it takes up less storage space
B To make sure both sender and receiver use the same key
C To make sure data is only understood by the intended receiver
D To stop malicious hackers getting into a computer network
The correct answer is C
A is not correct because compression does not encrypt a file
B is not correct because encryption does not ensure both sides use the same key
D is not correct because encryption does not stop hackers accessing a network
File servers are in a small room at the back of an office.
The office has a burglar alarm.
Give two other ways that the servers can be secured using physical methods
Lock on doors
Biometrics/ key cards
Security guards
Surveillance cameras
Phishing is a type of social engineering.
State what is meant by the term social engineering
manipulation technique that exploits/relies on human behaviour to trick people to reveal sensitive information
5G is a communication standard.
Identify the characteristic that is true for the 5G communication standard.
A It has a high transmission latency
B It has built-in security
C It has a lower bandwidth than 3G and 4G
D It uses wireless communication
The correct answer is D
A is not correct because 5G does not have a high transmission latency
B is not correct because a 5G does not have built-in security
C is not correct because 5G does not have a lower bandwidth than 3G and 4G
Programmers write and test code.
They use modular testing.
State what is meant by the term modular testing
Testing each block of code/subprogram/function independently (as it is written/finished)
Computer scientists are viewed as professionals, in the same way that doctors are
viewed as professionals.
Give two ways that computer scientists can demonstrate professionalism.
Behave in ethical/legal/moral ways
Attend computer science related conferences/gatherings
Stay up to date with changes in the field/read up-to-date publications
Avoid bias when making design choices
Identify the expression to give the number of unique binary patterns that can be stored in six bits.
A 6²
B 6 × 2
C 6² – 1
D 2^6
The correct answer is D
A is not correct because 6² stores 36 patterns, not 64 patterns
B is not correct because 6 × 2 stores 12 patterns, not 64 patterns
C is not correct because 6² – 1 stores 35 patterns, not 64 patterns
Software programs carry out tasks on computers.
A headteacher uses a computer simulation to model the effect of increasing class sizes.
Explain one problem with using simulations to predict the effects of changes.
If the data is incomplete/inaccurate the answers from the model might not be right
If the assumptions the model is based on are inaccurate the answers from the model might be incomplete/inaccurate
Images are stored as files before being displayed or printed.
Give one measurement of image resolution.
Pixels per inch/ppi
Pixels per centimetre/ppc
Dots per inch/dpi
Increasing the colour depth of an image leads to an increase in the image file size.
Describe the reason for the increase in file size.
Each pixel/colour in the image will require more bits to store
Software is divided into two categories.
Describe one difference between system software and application software.
System software is used to maintain/run the operation of the system/hardware whereas application software allows the user to carry out a task
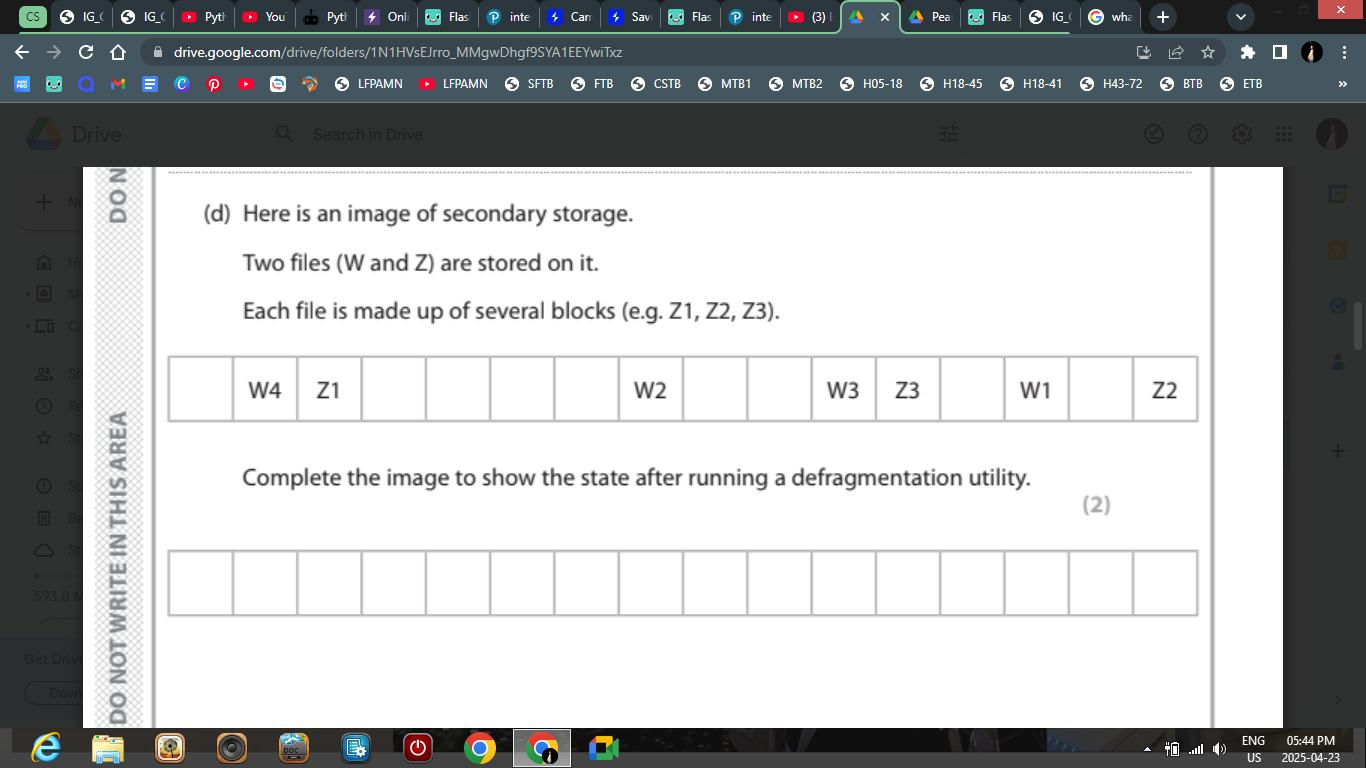
Here is part of a file that contains electric meter readings.
04631 04984 05103 05163 05271 05383 05487 05722
Explain the effect on the file of applying a run-length encoding algorithm to this data file.
The file size will not be decreased/will increase because there are very few/no repeating patterns / because a run length of one would be added to each digit
What is the correct programming language translator for
this task:
A guessing game that can be used on
different computing platforms
Interpreter
What is the correct programming language translator for
this task:
A screen driver for a new
smartphone
Assembler
A new version of a spreadsheet
program for sale next year
Compiler
Control software for an embedded system inside a new washing machine
Assembler
Identify the measurement of network speeds.
A Mebibits per second
B Mebibytes per second
C Megabits per second
D Megabytes per second
The correct answer is C
A is not correct because mebibits is a measure of storage capacity
B is not correct because mebibytes is a measure of storage capacity
D is not correct because transmission speeds are measured only in bits per second, not bytes per second
Data packets contain the addresses of the sender and the receiver. Complete the table to give the number of bits that make up each type of network address.
Type Example Number of bits
IPv4 192.169.0.3
IPv6 1050:a500:00c0:0440:0006:0300:700d:436f
(1) IPv4 192.169.0.3 - 32 bits
(2) IPv6 1050:a500:00c0:0440:0006:0300:700d: 436f - 128 bits
Data packets travel over physical media.
Describe one difference between the media used by a wired network and a wireless network.
In a wired network packets travel over (copper/fibre-optic) cables/ electrical or light signals,
whereas in a wireless network packets travel over the air
Some people confuse Ethernet and Wi-Fi.
Describe what is meant by the term Ethernet.
Networking technology which uses a wired method to connect devices in a LAN such as computers, routers and printers
Follow specific protocols to ensure data is sent and received correctly
Used on a wired network/connection using Ethernet cables
Defines how packets are checked for errors
Defines speed of transmission
A single physical box connects a desktop computer to the Internet.
The box incorporates three different components.
Complete the diagram to show the names of the components in the correct order.
Desktop computer → ______ → _______→ ______→ Internet
Desktop computer → Switch → Router → Modem → Internet
Users enter passwords when logging onto a network and when creating accounts using a web page.
Describe one difference between validation and authentication.
VALIDATION: used to check that data/password entered by user is fit for processing/meets specified requirements
AUTHENTICATION: used to verify identity of user/prove that users are who they say they are
assembler
type of computer program that translates assembly language code into machine code so the computer's processor can directly execute it
interpreter
program that executes instructions written in a programming language directly, without requiring them to be pre-compiled into machine code
compiler
program that translates a programming language's source code into machine code which a computer can understand and execute
Computers are made up of hardware components.
Complete the diagram by adding directional arrows between the components to show the flow of communication.
Speaker CPU Mouse USB device
Mouse → CPU
CPU → Speaker
CPU ←→ USB Device
Identify what is stored in ROM.
A The software firewall
B The basic input output system
C The operating system
D The user interface code
The correct answer is B
A is not correct because a firewall is an application that is loaded after the device is booted
C is not correct because the operating system is loaded after the device is booted
D is not correct because the user interface is loaded after the device is booted
Cache is used as temporary storage.
One type of cache is located between main memory and the CPU.
Explain one reason cache is used in a computer.
Cache makes up for the difference in speed of two devices because it is very high-speed memory
Cache is high-speed memory which acts as a buffer between a faster and a slower device
It speeds up processing because active/commonly used instructions and data are stored nearer to the CPU / the CPU doesn’t have to wait while instructions/data are fetched from RAM
A washing machine uses several different embedded systems.
One embedded system uses a switch to identify the type of wash cycle selected by the user.
Describe one other example of an embedded system found in a washing machine.
Uses a sensor to check the water level in the machine
Uses a thermometer to check the water temperature
Uses a timer to control the time required for the wash cycle/rinse/drain/spin
Uses a motor to rotate the drum
A warehouse has an automated alarm system.
When the alarm system is activated it will sound if:
• a movement sensor (M) is activated
• a pressure pad (P) is activated
• a key code (C) to deactivate the alarm system has not been entered.
Construct a logic statement, using AND, OR and NOT with the letters M, P and C, to show the conditions that will sound the alarm.
• M OR P
• NOT C
• <expr1> AND <expr2> (1)
Example statements:
(M OR P) AND (NOT C)
(M OR P) AND NOT C
(M AND NOT C) OR (P AND NOT C)
M AND NOT C OR P AND NOT C
A computer with a single CPU runs several processes at the same time.
This computer is multitasking.
Describe how the operating system enables processes to share a single CPU.
1. The operating system uses a scheduler to control processes
2. The operating system holds processes in a queue
3. Some processes may be given higher priorities than others
4. Each process gains accesses to the CPU for a short time / time slice to execute
5. Processes are swapped to/from (the queue / CPU)
Programmers share algorithms with different people and write algorithms for different reasons.
(a) A programmer is showing a new algorithm to a group of non-technical managers.
State an appropriate method for writing the algorithm.
Justify your answer.
Method:
Justification:
Method
Flowchart
Justification
It is a visual representation / does not use many words /
does not rely on use of English language
It does not rely on understanding specific syntax
Overview without unnecessary detail
OR
Method
Pseudocode/structured English/written description
Justification
It does not rely on understanding specific syntax
It uses English language words
Figure 1 shows an algorithm that displays a string based on the number input by the user.
1 SEND ("Enter a number: ") TO DISPLAY
2 RECEIVE inNum FROM (INTEGER) KEYBOARD
3 IF ((inNum = 1) OR (inNum = 2)) THEN
4 IF (inNum = 1) THEN
5 SEND ("First") TO DISPLAY
6 ELSE
7 IF (inNum = 2) THEN
8 SEND ("Second") TO DISPLAY
9 END IF
10 END IF
11 ELSE
12 SEND ("Invalid input") TO DISPLAY
13 END IF
Give one reason why the selection statement on line 7 is not required.
The test on line 3 has already limited the values to 1 and 2
The only value left for inNum to be (on line 7) is 2
Figure 2 shows an algorithm that manipulates arrays.
The algorithm works with any number of scores.
1 SET oldScores TO 10, 20, 30, 40, [ 50]
2 SET newScores TO 0, 0, 0, 0, [ 0]
3 SET newIndex TO 0
4
5 FOR oldIndex FROM (LENGTH (oldScores) - 1) TO 0 STEP -1 DO
6 SET newScores[newIndex] TO oldScores[oldIndex]
7 SET newIndex TO newIndex + 1
8 END FOR
(i) Describe what happens to the variable oldIndex when line 5 is executed.
(ii) State the purpose of the algorithm in Figure 2.
(i)
The oldIndex value will go from highest to lowest the step value is negative/decremented by 1 (each iteration)
(ii)
Reverse the (array of) scores
Copy the oldScores into newScores, in reverse order
Cloud storage has become an increasingly popular service.
Discuss the benefits and drawbacks of using cloud storage.
Growth
Higher bandwidth available both on wired and wireless networks
Reduced costs of large capacity storage devices
Improved levels of encryption / authentication
Increased trust in service providers
Growth of service provider options
Increased business models that aid scalability regarding storage capacity and costs
Benefits
Sharing / collaboration on documents and setting of access permissions
Access from any location connected to a WAN
Reduced cost of local computing devices with less storage required
Built in backups of data on server-based systems
Drawbacks
Increased security risks incurred from outsourcing a service
Relies on high-speed network connections
Reliance on service providers continuing to provide a high level of service
Increased chances of external data breaches
Identifying responsibilities for data breaches / legal jurisdiction
Increased power consumption from server systems and associated cooling systems
Increased use of networks and network traffic which will have an impact on other network users