Ch 23 config magement and missed Missed
1/102
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
103 Terms
CRC (Cyclic Redundancy Check) errors occur when a network device detects a mismatch between the checksum calculated at the transmitting end and the checksum received at the receiving end. This mismatch indicates that the data has been altered during transmission, likely due to errors in the physical layer.
CRC errors are typically indicative of physical layer issues
What is a characteristic of encryption in wireless networks
prevent the interception of data as it transmits a network
What are 2 characteristics of the distribution layer in a 3 tiered network architecture?
A serves as the network aggregation point
B provides a boundary between layer 2 and 3 communication
C designed to meet continuous redundant uptime requirements
D is the backbone for the network topology
E physical connection point for a LAN printer
B provides a boundary between layer 2 and 3 communication
C designed to meet continuous redundant uptime requirements
Not A cuz distribution layer is the ag point in a 2 tiered network this question is about 3.
Makes forwarding decisions based on MAC addresses
What is a characteristic of a Layer 2 switch?
The subset of all collisions that happen after the 64th byte of the frame has been TXed are called late collisions
Typically causes of late collisions are segment cable lengths in excess of the maximum permitted for the cable type. a collision wave is not detected by the transmitting station until after the 64 bytes slot time since it has to travel an excessive distance.
When a late collision wave is detected, the frame is not retransmitted by the MAC sublayer. Upper layer protocols must deduce that something went wrong and implement retransmission of the frame. This takes time and so late transmission can cause excessive delays.
The subset of all collisions that happen after the 64th byte of the frame has been TXed are called late collisions
Typically causes of late collisions are segment cable lengths in excess of the maximum permitted for the cable type. a collision wave is not detected by the transmitting station until after the 64 bytes slot time since it has to travel an excessive distance.
When a late collision wave is detected, the frame is not retransmitted by the MAC sublayer. Upper layer protocols must deduce that something went wrong and implement retransmission of the frame. This takes time and so late transmission can cause excessive delays.
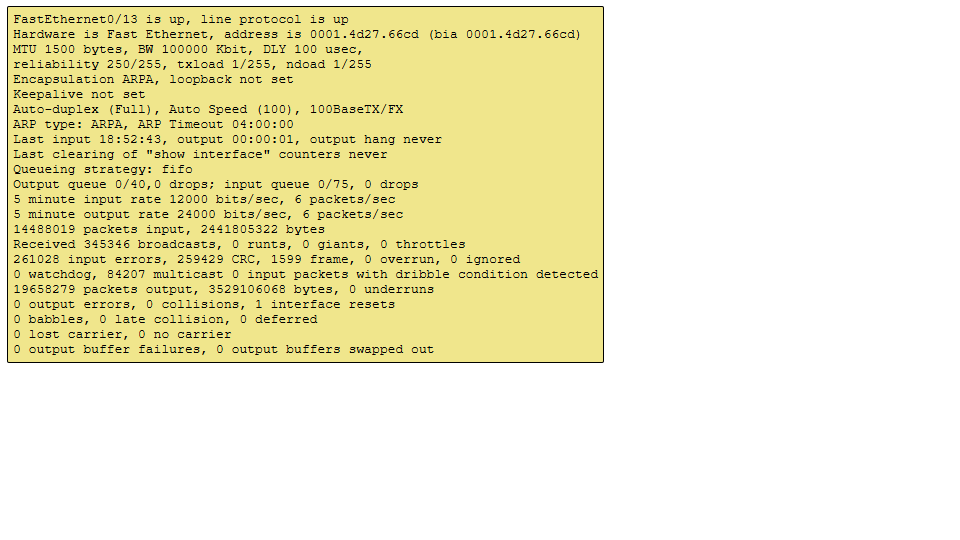
Whats wrong with this output?
The output shows a signif number of input errors, CRC error and frame errors. These errors are indicative of physical layer issues like
faulty cable, bad connectors or interference
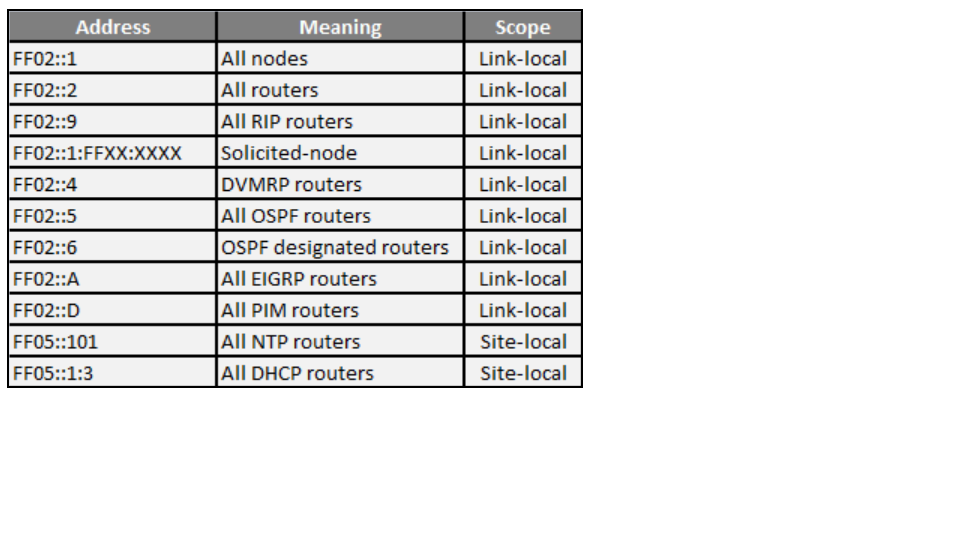
look at table
look at table
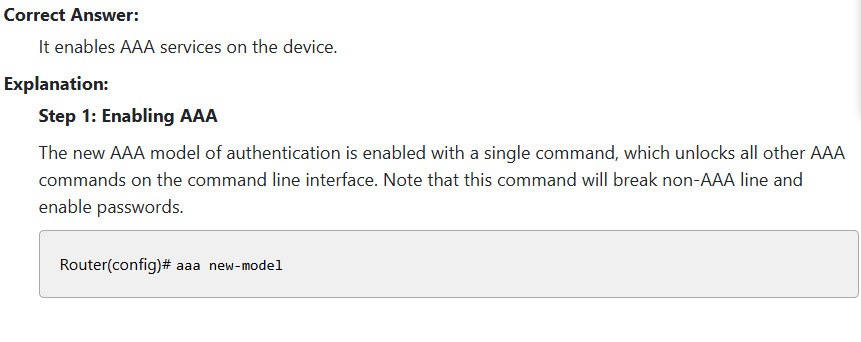
It enables AAA services on the device.
It is used for configuring RADIUS
Pgs 754 Ansible, 700 NCM,384 RADIUS, 386 TACACS+
The new AAA model of Authentication is enabled with a single command, which unlocks all other AAA commands on the CLI. Note that this command will break non AAA line and enable passwords
what doe s this command do?
Router (config)# aaa new-model
1000-Base-SX
The physical layer specification for Gig E over fiber optic over cabling defined in IEEE802.3z.
The SX system operates in full duplex with multimode only.
Advanced Encryption Standard
Cisco Access points provide WPA2-PSK (TKIP), WPA2-PSK (AES) and WPA2-PSK (TKIP/AES) as WPA2 encryption options.
AES is a more secure encryption protocol option introduced with WPA2 and is currently the strongest encryption type with WPA2-PSK
AES
LC to SC
GBIC and SFP are both hot swappable input/output devices that plug into a physical port or a slot. GBIC is commonly used with Gig Ethernet and Fibre Channel. But its applications are not limited to these 2 types. There is FE Fast Ether GNIC, BIDI GBIC, CWDM GBIC, DWDM GBIC. Generally GBC is with the SC connector.
SFP came into existence later then GBIC. SFP transceivers are designed to support SONET, GigE, Fibre Channel, and other commo standards. SFP is usually with LC connectors. SFP is also known as mini-GBIC because it has the same functionality as GBIC but in a smaller form factor.
GBIC uses SC while SFP uses LC.
Which cable type must be used to interconnect one switch using 1000 BASE-SC GBIC modules and another switch using 1000 BASE-SX SFP modules?
LC to SC
LC to LC
SC to ST
a number of runts can show duplex mismatch. Runts can be caused by collisions so check if collisions are incrementing if not suspect duplex mismatch
a number of runts can show duplex mismatch. Runts can be caused by collisions so check if collisions are incrementing if not suspect duplex mismatch
DevOps is a software development approach that emphasizes collaboration between development (Dev) and IT operations (Ops) teams to deliver software faster and more reliably. It combines cultural philosophies, practices, and tools to automate and integrate processes, fostering continuous improvement and faster delivery of value to customers.
DevOps
IaC
practice where infrastructure is managed and provisioned using machine-readable definition files, like code, rather than through manual processes or interactive configuration tools. This allows for automation, consistency, and repeatability in managing infrastructure resources, similar to how software code is managed.
Infrastructure as Code
idempotence
a principal of IaC where the configuration will be applied only to a target environment if it will result in a change.
In essence, idempotence simplifies the development and maintenance of systems by allowing for safe and reliable retries and by ensuring consistent state management, especially in the face of potential errors or network issues
Ansible
Python based config management tool that uses YAML playbooks to push configs to nodes. It is an agentless solution offering wide support for network devices because is uses SSH to reach nodes. Ansible does support both push and pull methods. CCNA book states it only pushes a config…
playbook
set of YAML instructions saying what should be applied to a target device. Used with Ansible.
what are the Pros of Ansible
Easy install and setup
powerful orchestration
supported by most enterprise-grade vendors
supports both push and pull modules
Agentless model is faster and less complicated than the agent model
Sequential execution order makes deployments predictable.
what are the Cons of Ansible
requires root SSH access to Linux nodes
It is not as mature as Puppet or Chef.
Ansible has several scripting components so the syntax can vary
Its focused on orchestration over config management so Ansible does NOT protect against configuration drift.
Troubleshooting can be tricky compared to Chef or Puppet
No native config rollback on failure
agentless mode
A deployment model that does not require agents on target machines, simplifying management and reducing complexity.
anti software
commonly referred to as anti-virus or anti-malware is specifically designed to protect endpoints form attacks.
It prevents, detects and removes malicious software and provides real time protection against threats like viruses, trojans, spyware, and ransomware.
Which protocol does the AP use to draw power from a connected switch?
A Internet Group Management Protocol
B Adaptive Wireless Path Protocol
C Cisco Discovery Protocol
D Network Discovery Protocol
C CDP
explanation
CCNA has trick questions
CDP does not provide power to the AP but CDP is used by AP and WLC to negotiate and monitor Power over Ethernet (PoE) Levels.
so CDP is the most right answer
IaaS
Provides the computing infrastructure , physical or VMs and other resources like virtual-machine disk image library, block and file based storage, FWs, load balancers, IP addresses, virtual LANs
Infrastructure as a Service
ex
Amazon, EC2, Windows Azure, Rackspace, Google Compute Engine.
Paas
provides computing platforms which include OS, programming language execution environment, DB, and webserver
Platform as a Service
ex
AWS Elastic Beanstalk, Windows Azure, Heroku, Force.com, Google App Engine, and Apache Stratos
SaaS
provided access to application software also called on demand software. You do not have to install, setup and the running of the software. Service providers will do that for you. You will just have to pay and use it through some client.
Software as a service
ex
Google Aps, Windows Office 365
An org has decided to use cloud based services. Which cloud service allows the org to install its own OS on the VM.
IaaS
Infrastructure as a Service
Provides the computing infrastructure , physical or VMs and other resources like virtual-machine disk image library, block and file based storage, FWs, load balancers, IP addresses, virtual LANs
ex
Amazon, EC2, Windows Azure, Rackspace, Google Compute Engine.
FTP uses 2 separate connections, one for control and one for data. Control connection uses port 21 while the data connection uses a different port. Typically port 20 but is dependent on if Active or Passive mode is used.
FTP uses 2 separate connections, one for control and one for data. Control connection uses port 21 while the data connection uses a different port. Typically port 20 but is dependent on if Active or Passive mode is used.
What is an agent in SDN?
an agent is a software component that acts as an intermediary between an SDN controller and network devices. It facilitates communication and translates instructions between the controller and the devices, enabling the controller to manage and configure the network.
WPA3 Enterprise
Provides additional protections for networks transmitting sensitive data by offering the equivalent of 192 bit cryptographic strength. WPA3 networks use a suite of 192 bit cryptographic tools to ensure consistent protection across network.
Cisco supports 2 WPA3 modes and they are WPA3 Enterprise and WPA3 Personal
WPA3 Personal
allows for better password authentication even when using noncomplex combinations. WPA3 uses Simultaneous Authentication of Equals (SAE) to provide strong defense against password guessing.
SAE is a secure key establishment protocol
Cisco supports 2 WPA3 modes and they are WPA3 Enterprise and WPA3 Personal
What are 2 differences between WPA2 and WPA3.
WPA2 uses 128 bit encryption, while WPA3 supports 128 and 192 bit key encryption
WPA3 uses AES for stronger encryption than WPA2, which uses TKIP.
?
WPA3 introduced several enhancements to improve security over its predecessor, WPA2. The key enhancements include:
1. Forward Secrecy: This ensures that even if a session key is compromised, it cannot be used to decrypt past communications.
2. Simultaneous Authentication of Equals (SAE): This is a new handshake protocol used in personal mode (WPA3-Personal) that replaces the Pre-Shared Key (PSK) exchange. SAE ( Simultaneous Authentication of Equals) provides stronger protection against offline dictionary attacks.
WPA3 introduced several enhancements to improve security over its predecessor, WPA2. The key enhancements include:
1. Forward Secrecy: This ensures that even if a session key is compromised, it cannot be used to decrypt past communications.
2. Simultaneous Authentication of Equals (SAE): This is a new handshake protocol used in personal mode (WPA3-Personal) that replaces the Pre-Shared Key (PSK) exchange. SAE (Simultaneous Authentication of Equals) provides stronger protection against offline dictionary attacks.
Which two components comprise part of a PKI (public Key Infrastructure)? (Choose two)
A RSA token
B Clear-text password that authenticates connections
C One or more CRLs (Certificate Revocation List)
D Preshared key that authenticates connections
E CA that grants certificates
C One or more CRLs (Certificate Revocation List)
E CA that grants certificates
What are two characteristics of a public cloud implementation? (Choose two.)
A It is a data center on the public Internet that maintains cloud services for only one company.
B It provides services that are accessed over the Internet.
C It enables an organization to fully customize how it deploys network resources.
D It is owned and maintained by one party, but it is shared among multiple organizations.
E It supports network resources from a centralized third-party provider and privately-owned virtual resources.
B It provides services that are accessed over the Internet.
D It is owned and maintained by one party, but it is shared among multiple organizations.
Private cloud
The private cloud model refers to cloud computing resources used exclusively by a single business or organization. A private cloud can be located in your on-site data center or hosted in the cloud by a service provider.
Public cloud
When an organization deploys a public cloud model, all hardware, software, and supporting infrastructure is owned and managed by a service provider, which is delivered exclusively over the Internet. You access these services and manage your account through a web browser.
Hybrid cloud
A hybrid cloud computing model combines public and private clouds to share data and applications. Hybrid clouds connect infrastructure and applications between cloud-based resources with existing resources not located in the cloud. This approach gives your business greater flexibility and deployment options.
The ansible.cfg file is entirely optional because if Ansible can’t find the setting, it’ll just use the default values when doing the task.
but…
What is the order Ansible will use to look for the setting file?
By default it will first look in ANSIBLE_CONFIG variable to see if a path is set.
If not then it checks ansible.cfg in the current directory that you are running the playbook from.
Next it will look in the Home directory.
Finally it will look /etc/ansible.
It is recommended to use the /etc/ansible when you can.
The Ansible inventory file tells Ansible which target nodes to connect to and gives it info on how it should make the connection. The file also allows you to group nodes for easier administration. By default Ansible will check the hosts file under /etc/ansible when trying to access a node.
The Ansible inventory file tells Ansible which target nodes to connect to and gives it info on how it should make the connection. The file also allows you to group nodes for easier administration. By default Ansible will check the hosts file under /etc/ansible when trying to access a node.
Running commands without a playbook (usually for troubleshooting) is called Ad-Hoc commands.
Running commands without a playbook (usually for troubleshooting) is called Ad-Hoc commands.
Whitespace is very important in YAML. The TAB key is a huge no no with playbooks…always use the spacebar.
Whitespace is very important in YAML. The TAB key is a huge no no with playbooks…always use the spacebar.
Inventory (Ansible)
Defines the nodes that ansible knows about and groups them so they can be referenced, The inventory also includes connection instructions to be executed.
Playbook (Ansible)
a YAML file that contains a set of instructions to be executed.
Multiple plays can exist in a playbook, which allows the playbook to apply configuration to different nodes in different sections.
Play (Ansible)
Variables (Ansible)
you can customize variables in your playbook
Templates (Ansible)
You can use Python’s Jinja2 templates with your playbooks, which is really helpful for network administration.
Handlers (Ansible)
These are alot like tasks, except they’re only called to an event like service starting.
Roles (Ansible)
Allows you to spread out playbooks across several folders to make the configurations more modular, scalable and flexible.
Modules (Ansible)
Built into Ansible, modules are files that describe how Ansible will achieve a given task and are written in Python. You can write your own. Cisco has 69 modules in the current version of Ansible that cover everything from IOS to their UCS server platform.
Cisco Unified Computing System (UCS) is an integrated data center platform that combines computing, networking, storage access, and management into a single system
Facts (Ansible)
These are global variables that contain a ton of information about the systems, including vital stats like the systems IP address.
Tasks (Ansible)
an action the playbook applies like installing Apache on a Linux box.
Ansible Tower
a paid version via RedHat that adds central management to Ansible that improves security because you can control who can run playbooks through Role Based Access Control (RBAC). Ansible Tower also provides a single point for integration with other tools. RedHat offers a free version that supports 10 hosts.
AWX
The upstream development version of Ansible Tower, that’s kind of like Fedora vs Red Hat Linux. You can use it for free, but there's less reliability since there can be frequent changes with little testing. There is limited support available.
AWX is an open-source, community-developed project that provides a web-based user interface, REST API, and task engine on top of Ansible. It is the upstream project from which Red Hat Ansible Automation Platform's automation controller (formerly Ansible Tower) is derived
Puppet
Puppet is an open-source automation tool that can be used to manage and configure various types of devices. It is more popular than Ansible with sysadmins. Puppet used to require an agent so it could only run on devices that support that like Cisco Nexus. For CCNA know Puppet generally requires an agent even though now the tool supports agentless configuration.
Puppet Pros
Prevents configuration drift through compliance automation and reporting tools because the agent continuously checks in with the Puppet master to make sure it’s compliant with the manifests.
Strong web UI
More mature solution then ANSIBLE
easy set up
Puppet Cons
You have to learn Ruby to get good with Puppet and Ruby is not widely used by the network community.
Lacks a push system so changes only occur when nodes check in
the master-agent architecture complicates redundancy and scalability.
Puppet Master
The Master server that controls the configuration on manged nodes.
Puppet Agent Node
A node controlled by the Puppet Master
Manifest
a File containing instructions to be executed in Puppet.
Resource (Puppet)
Declares a task that needs to be executed and how. For example , if we install Apache on a Linux box, we can declare Apache and make sure it states is set to install
Module (Puppet)
a group of manifests and related files organized nicely to make life easier
Class (Puppet)
You can use classes to organize the manifest file just as you can use programming languages like Python
Facts (Puppets)
Global Puppet variables that contain a ton of info about the system like the systems IP
Services (Puppet)
Used to control services on a node
Cookbook
a file containing a set of instructions to be executed.
a Chef term for file that holds recipes
Recipe
An Action that the cookbook applies, like installing Apache on a Linux box
Chef term
Chef Notes
Computer that Chef Manages
Knife
Command line tool for managing Chef through the server API
Chef Server
The master server that manages all the nodes and cookbooks
Chef Manager
The web interface for Chef Server-the API is used for communication
Workstation (Chef)
A computer you perform configuration related tasks from like when creating a cookbook
Bookshelf
a place to store cookbook content
Used with Chef
Chef server has only a single version, the open source tool we are free to use on any Linux box. Chef workstation can run on both Linux and Windows.
Chef server has only a single version, the open source tool we are free to use on any Linux box. Chef workstation can run on both Linux and Windows.
Chef Pros
very flexible for OS and middleware management
Developer focused
the architect suit large scale deployments
Sequential execution order
great reporting
support hosted cloud offerings
Chef Cons
Steep learning curve
Complicated install and setup
Lacks a push system so changes only occur when nodes check in
Chef
Ruby based configuration tool that uses cookbooks to apply configurations. Chef is the most advanced solution in book and is better suited for programmers because its more structured and has a strong developer focus. It also requires that nodes have an agent deployed for it to be able to manage them. Chef can’t push configurations.
Puppet
a Ruby based configuration management tool that uses custom manifest files to configure devices. It requires an agent to be installed on the nodes, so it has less network support. Puppet also doesn’t support pushing configuration to nodes. Instead, the configuration is applied when the agent checks in. Puppet does support Cisco network devices that can install the Puppet agent.
Which configuration management solutions require agents?
Chef and Puppet both require agents
What does Ansible call the file that holds the configuration that should be applied to nodes.
Playbook is the Ansible file that holds configurations that is applied to the nodes.
Which configuration management solution is best suited for managing Cisco Devices
Ansible
What language does Ansible use in playbooks
Ansible uses YAML in playbooks
Which configuration management solution uses Manifests?
Puppet uses a manifest file
Which configuration management solution uses an inventory file?
Ansiible uses an inventory file
Puppet is based on what language?
Ruby is the language used in both Puppet and Chef
What connection method does Ansible use?
Ansible uses SSH to connect to Linux and network systems and Powershell to manage Windows systems.
Which configuration management solution is best suited for sysadmins?
Puppet is best suited for sysadmins
YAML file cannot contain which type of character
TAB
Which command do you use to run an Ansible playbook?
A Ansible-doc
B Ansible-execute
C Ansible-playbook
D Run-Playbook
C Ansible-playbook
Which command do you use to look up a module in Ansible?
A Ansible-doc
B Ansible-execute
C Ansible-playbook
D Run-Playbook
A Ansible-doc
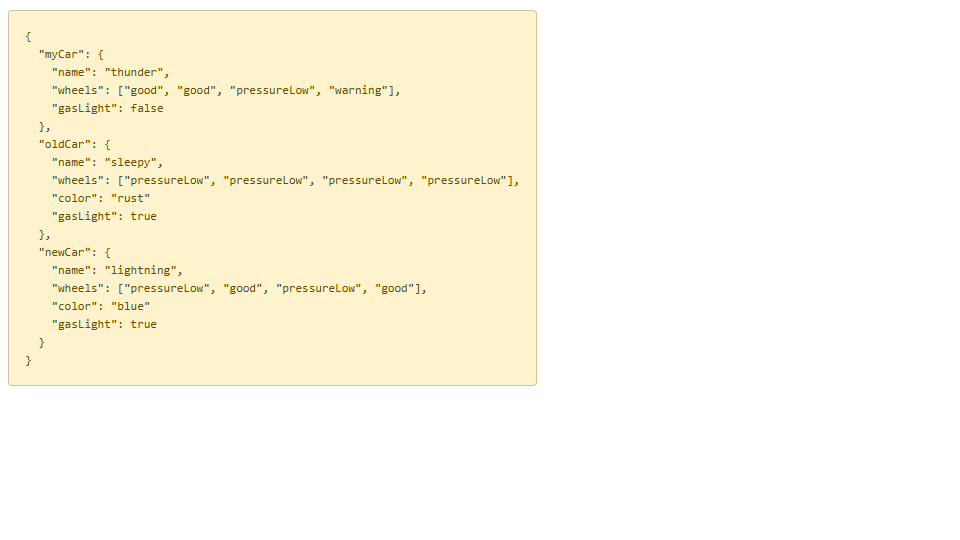
JSON define element guidelines
An object is an unordered set of name/value pairs. An object begins with {left brace and ends with }right brace. Each name is followed by :colon and the name/value pairs are separated by ,comma.
An array is an ordered collection of values. An array begins with [left bracket and ends with ]right bracket. Values are separated by ,comma.
A value can be a string in double quotes, or a number, or true or false or null, or an object or an array. These structures can be nested.
A string is a sequence of zero or more Unicode characters, wrapped in double quotes, using backslash escapes. A character is represented as a single character string. A string is very much like a C or Java string.
A key is a string that acts as an identifier for the associated value.
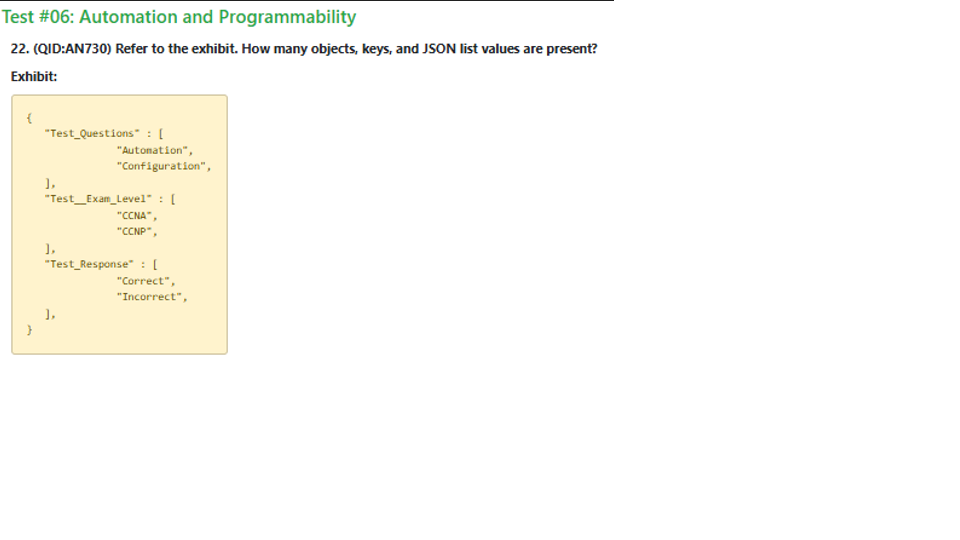
A 3 Objects, 2 Keys, and 3 JSON list values
B 1 Object, 3 Keys, and 2 JSON list values
C 3 Objects, 3 Keys, and 2 JSON list values
D 1 Object, 3 Keys, and 3 JSON list values
D 1 Object, 3 Keys, and 3 JSON list values
The entire JSON structure is a single object.
There are three keys: "Test_Questions", "Test_Exam_Level", and "Test_Response".
Each of the keys maps to a list value.
"Test_Questions" maps to ["Automation", "Configuration"],
"Test_Exam_Level" maps to ["CCNA", "CCNP"].
"Test_Response" maps to ["Correct", "Incorrect"].
Therefore, there is one main object, three keys, and each key corresponds to a list value (3 list values total).
What is the function of the Norhtbound API?
It provides a path of communication between an SDN controller and a network application.
Which components are contained within a virtual machine?
configuration files backed by physical resources from the Hypervisor
Explanation:
"configuration files backed by physical resources from the Hypervisor"
Virtual machines consist of configuration files (such as VMX files for VMware) and virtual disks (such as VMDK files for VMware). These configuration files define the virtual hardware
and settings of the VM, which are then backed by the physical resources (CPU, memory, storage, network) managed by the hypervisor.
Which two events occur automatically when a device is added to Cisco DNA Center? (Choose two.)
A The device is placed into the Provisioned state.
B The device is assigned to the Global site.
C The device is assigned to the Local site.
D The device is placed into the Managed state.
B The device is assigned to the Global site.
D The device is placed into the Managed state.
Explanation:
"When you successfully add, import, or discover a device, DNA Center places the device in the Managed state and assigns it to the Global site by default."
Which REST method updates an object in the Cisco DNA Center Intent API?
A POST
B GET
C PUT
D PATCH
E DELETE
C PUT
In RESTful APIs, the PUT method is used to update an existing resource or object. If the resource exists, it will be updated with the new data provided; if it does not exist, a new resource might be created at that URI, depending on the API's implementation.

What is represented by the word ge3/36 in the JSON schema.
Explanation:
Value
An array in JSON is a list of values enclosed in square brackets []. The entire structure in the exhibit is an array.
An object in JSON is a collection of key-value pairs enclosed in curly braces {}. Each element within the array is an object
A key in JSON is the name part of a key-value pair, such as "interface". "ge3/36" is the value associated with the key "interface"
Which interface type enables an application running on a client to send data over an IP network to a server?
A Northbound Interface
B Application Programming Interface
C Southbound Interface
D Representational State Transfer Application Programming Interface
B Application Programming Interface
Explanation:
"Application Programming Interface (API)"
APIs provide a set of rules and protocols that allow different software applications to communicate with each other. In the context of the question, an API allows an
application on a client to send data over an IP network to a server. The other options refer to different types of interfaces but are not specifically associated with
application communication over an IP network.
API
An API is a set of rules and specifications that allows different software systems to communicate and interact with each other, enabling them to share data and functionality. APIs act as intermediaries, allowing applications to access and utilize the services or data of other applications without needing to know the intricate details of how those services are implemented
Application Programming Interface