CSE 130 FINAL PART 2
1/17
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
18 Terms
Define batching, dallying, speculation
Batching: handle requests as a group (e.g. multiple writes at once)
Dallying: delay a request
Speculation: read next likely data
What is burst in queueing/overload?
Brief increase in the request rate above average
Two types of locality of reference
Temporal: recent items likely to be referenced again soon
Spatial: “near” items likely to be referenced
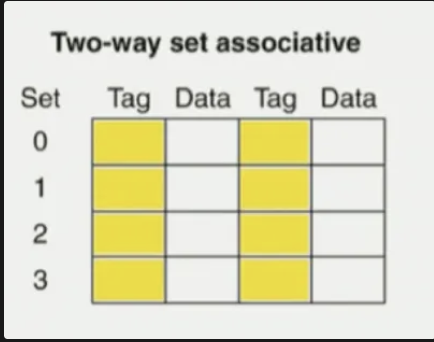
Three types of cache associativity
Fully associative: data can be anywhere in the cache
Direct-mapped: each data mapped to exactly one cache line
N-way associative: cache divided into sets, each set contains n cache lines
What is page fault?
CPU uses a virtual address, but the page is not currently loaded in physical memory → OS loads the page from disk
FIFO vs LRU
FIFO: no rearrangements
LRU: every time it is used, move to headClock
Explain removal policy: Clock
Second chance without the need to shift elements (use a rotating hand like a clock)
When referenced, set reference bit to 1
When evicting, if reference bit == 1, set it as 0 and move on to next target (same as putting it at the tail)
NRU
Remove in this order:
Not referenced, not dirty
Not referenced, dirty
Referenced, not dirty
Referenced, dirty
Best removal policy?
OPT
Three types of misses
Compulsory miss: first miss
Capacity miss: # of cache blocks < # blocks needed by program
Conflict miss: miss that can be avoided by a fully-associative cache
(T/F) Kerckhoff’s doctrine relies on hiding the methods/logic for security.
False, relies on the strength of the key
Single node system vs multi node system
Single node system: attacker only observes timing and inputs/outputs
Multi node system: observe messages but can drop and change messages
Note: Attackers cannot directly see internal state of a program, execute code, or decrypt/impersonate an encrypted message
What is a corner case bug?
A bug that happens in rare conditions that lie at the corner of the program (e.g. goto fail)
What is principle of least privilege?
Always grant the least amount of access to users
What is unsanitized input attack?
Exploit when system neglects to verify user input (e.g. SQLi, heartbleed)
What is a side channel attack?
Using implicit inputs and outputs such as timing and electricity current to guess hidden data
Dependency vulnerability
Systems security depends on xyz (e.g. software vendors as an attack vendor)
What are operational errors as an attack vector?
Flawed code/logic (e.g. WWII Enigma cipher machine decoded due to flawed encryption)