Developing an Information Security Program
1/134
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
135 Terms
Information Security Program
Structure managing risks to information assets.
Functional Components
Key elements of an information security program.
Organizational Culture
Shared values influencing security program structure.
Security Personnel Budget
Funds allocated for security staff and resources.
Security Capital Budget
Funds for security infrastructure and technology.
Job Titles in InfoSec
Roles within an information security program.
Security Education Program
Training initiatives for security awareness and skills.
Project Management Role
Overseeing security projects within the organization.
Internal Factors
Elements within the organization affecting security activities.
External Factors
Outside influences impacting security program organization.
Planning Security Programs
Strategies based on organization size and needs.
Security Initiatives
Actions taken to enhance information security posture.
Complex Organizational Infrastructures
Challenges faced by larger organizations in security.
Staffing Information Security
Recruiting and managing security personnel effectively.
Security Spending
Declines as organizations grow, limiting security effectiveness.
Risk Assessment
Identifying and evaluating potential security risks.
Risk Management
Strategies to mitigate identified security risks.
Systems Testing
Evaluating security measures for effectiveness.
Policy
Guidelines governing security practices and procedures.
Legal Assessment
Evaluating legal implications of security measures.
Incident Response
Actions taken to address security breaches.
Planning
Strategizing security measures for future needs.
Measurement
Evaluating effectiveness of security implementations.
Compliance
Adhering to laws and regulations regarding security.
Centralized Authentication
Single point for user identity verification.
Systems Security Administration
Managing security for organizational systems.
Training
Educating staff on security practices.
Network Security Administration
Protecting network infrastructure from threats.
Vulnerability Assessment
Identifying weaknesses in security systems.
CISO
Chief Information Security Officer, oversees InfoSec.
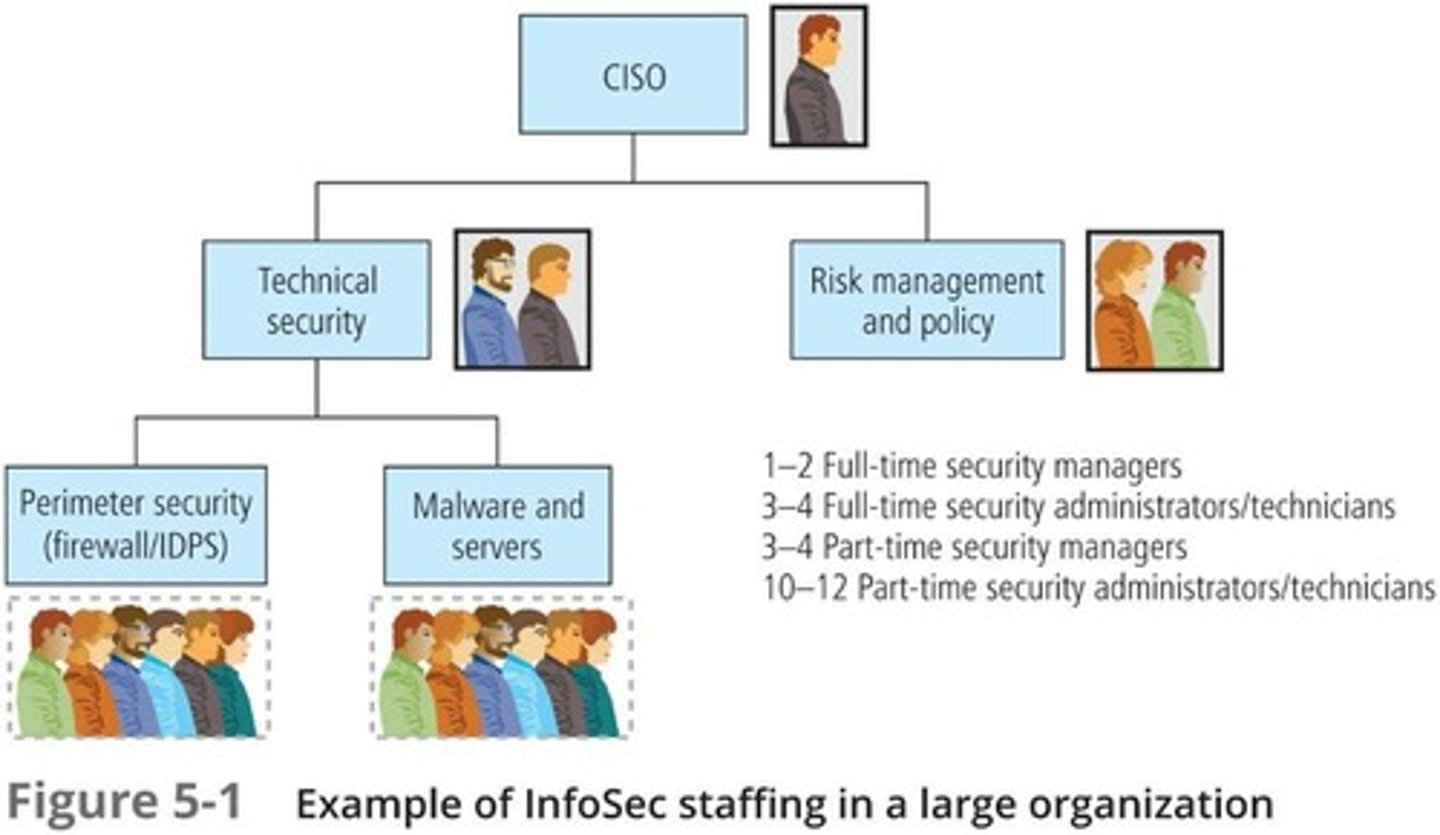
InfoSec Department
Group managing organization's information security.
Security Functions
Duties split among various organizational groups.
Medium-Sized Organizations
Implement multi-tiered security with fewer groups.
Small Organizations
Often rely on one security administrator.
SETA Programs
Security Education, Training, and Awareness initiatives.
Security Education
Formal learning for InfoSec roles.
Security Training
Hands-on instruction for secure operations.
Delivery Methods
Various formats for training implementation.
Security Awareness
Programs to inform about security importance.
Employee Accountability
Holding staff responsible for security actions.
Security Consultants
Independent experts providing security advice.
Security Technicians
Entry-level roles configuring security tools.
Security Analysts
Specialized roles designing security solutions.
Security Managers
Oversee daily InfoSec operations.
ISACA Certifications
Certifications for IT governance and security.
CISM
Certified Information Security Manager credential.
CISA
Certified Information Systems Auditor credential.
CGEIT
Certified in Governance of Enterprise IT.
CRISC
Certified in Risk and Information Systems Control.
GIAC Certifications
Technical certifications from SANS organization.
CISSP
Certified Information Systems Security Professional.
SSCP
Systems Security Certified Practitioner certification.
Security Awareness Components
Materials used for awareness programs.
Project Management in InfoSec
Managing security as both process and project.
Help Desk Personnel
Support staff identifying security issues.
Security Officers
Blend physical and IT security roles.
Security Staffers
Perform routine security monitoring tasks.
Security Awareness Techniques
Methods to engage employees in security.
Security Awareness Conferences
Events to promote security awareness.
Security Policy Development
Creating guidelines for organizational security.
Incident Management
Responding to and managing security incidents.
Compliance Enforcement
Ensuring adherence to security policies.
Vulnerability Management
Ongoing process of addressing security weaknesses.
Information Security Governance
Framework for managing security at an enterprise level.
Physical Security
Protection of physical assets and facilities.
Cybersecurity Analyst
Professional analyzing and improving security measures.
Security Risk Assessment
Evaluating potential threats to information assets.
Disaster Recovery Planning
Preparing for recovery from security incidents.
Project
Temporary activity to create specific product or service.
Process
Ongoing operations not limited to projects.
Project Management
Application of skills to meet project requirements.
PMBoK
Project Management Body of Knowledge by PMI.
Initiating
First process in project management lifecycle.
Planning
Defining project scope and resources needed.
Executing
Carrying out project plans and tasks.
Controlling
Monitoring project performance and making adjustments.
Closing
Finalizing all project activities and deliverables.
Project Success Criteria
On time, within budget, meets specifications.
Work Breakdown Structure (WBS)
Tool for breaking project into major tasks.
Projectitis
Excessive focus on documentation over meaningful work.
Project Milestones
Key points for monitoring project progress.
Iterative Projects
Projects that are repeated over time.
Performance Measures
Metrics to evaluate project success.
Project Constraints
Limitations on project scope, quality, or budget.
Resource Assemblage
Gathering resources temporarily for project completion.
Detailed Blueprint
Comprehensive plan for project activities.
Responsibilities Identification
Assigning roles to reduce ambiguity in projects.
Quality Requirements
Minimum standards that project deliverables must meet.
Common Reference Tool
Resource for all team members to enhance productivity.
Proactive Control
Anticipating issues before they affect project outcomes.
WBS Task List
List of major tasks in project management.
Task Attributes
Essential details for each task in WBS.
Work Accomplishment
Activities and deliverables to be completed.
Estimated Effort
Hours or workdays needed for task completion.
Skills Required
Common or specialty skills for task performance.
Task Interdependencies
Relationships between tasks affecting scheduling.
Task Sequencing
Ordering tasks for efficient project management.
Network Scheduling
Method for sequencing tasks in project plans.
PERT
Diagramming technique for project task dependencies.
Critical Path Method
Technique for identifying longest project duration.