IC34 Guide to IACS Cybersecurity Design and Networking
1/309
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
310 Terms
What is the primary focus of the IACS Cybersecurity course?
Design, implementation, and testing of cybersecurity in industrial automation and control systems.
What are some primary information sources for the course?
ISA/IEC 62443 standards, US Department of Homeland Security, NIST, and Center for Internet Security.
What are the three phases of the IACS Cybersecurity Lifecycle?
Assess, Develop & Implement, and Maintain.
What is the goal of the Assess phase in the IACS Cybersecurity Lifecycle?
To assign a Target Security Level (SL-T) and ensure that Achieved Security Level (SL-A) meets or exceeds it.
What happens during the Develop & Implement phase?
Countermeasures are implemented to meet the Target Security Level (SL-T).
What is the focus of the Maintain phase in the IACS Cybersecurity Lifecycle?
To ensure that Achieved Security Level (SL-A) is maintained and audited as necessary.
What is the first step in the Assess phase of the IACS Cybersecurity Lifecycle?
Conducting a High-Level Cyber Risk Assessment.
What is included in the Cybersecurity Requirements Specification?
It outlines the security requirements for industrial automation and control systems.
What is the significance of the ANSI/ISA-62443 standards?
They provide guidelines for security in industrial automation and control systems.
What is the role of periodic cybersecurity audits?
To assess and ensure the effectiveness of implemented cybersecurity measures.
What is the purpose of the Cyber Incident Response plan?
To outline procedures for responding to cybersecurity incidents.
What does the term 'system hardening' refer to?
The process of securing a system by reducing its surface of vulnerability.
What is the goal of network segmentation in cybersecurity?
To divide a network into smaller, manageable segments to enhance security.
What is the function of firewalls in cybersecurity?
To monitor and control incoming and outgoing network traffic based on predetermined security rules.
What is an Intrusion Detection System (IDS)?
A system that monitors network traffic for suspicious activity and alerts the user.
What does the acronym CEU stand for?
Continuing Education Units.
What is the importance of the Cybersecurity Acceptance Test Plan (CFAT/CSAT)?
To verify that cybersecurity measures meet specified requirements before deployment.
What does the Cybersecurity Management System include?
Policies, Procedures, Training & Awareness
What is the purpose of a Cybersecurity Requirements Specification (CRS)?
To outline the cybersecurity requirements for an IACS, including security levels and risk assessments.
What are the five Security Levels (SL) defined in ISA/IEC 62443?
SL 0: No requirements; SL 1: Protection against casual violations; SL 2: Protection against intentional violations with low resources; SL 3: Protection against intentional violations with moderate resources; SL 4: Protection against intentional violations with high resources.
What are the Four 'Ts' of Managing Risk?
Tolerate, Transfer, Terminate, Treat
What is the output of a risk assessment used for?
It serves as input for the development and implementation of security strategies.
What does SL-T stand for?
Target Security Level, which is the desired level of security for a specific zone or conduit.
What is the purpose of periodic cybersecurity audits?
To assess and ensure the effectiveness of the cybersecurity management system.
What information should a good risk assessment provide?
Risk profile, highest severity consequences, threats/vulnerabilities, target security levels, and recommendations.
What is included in the Cybersecurity Requirements Specification (CRS)?
SUC description, zone and conduit drawings, characteristics, operating environment assumptions, threat environment, security policies, tolerable risk, and regulatory requirements.
What is the purpose of the 'Deter' strategy in the Five 'Ds' of Treating Risk?
To discourage attackers from attempting a breach.
What does the 'Detect' strategy aim to achieve?
To monitor areas for unauthorized intrusion and respond appropriately.
What is the goal of the 'Delay' strategy?
To slow down an active intrusion to allow security response.
What is the 'Deny' strategy focused on?
Keeping unauthorized persons out while allowing authorized access.
What does the 'Defeat' strategy involve?
A security response to apprehend an intruder.
What is the significance of the security level correlation and iterative cycle?
It helps in assessing and improving the security posture of the system.
What is the purpose of developing a security strategy?
To identify zones, evaluate risks, establish target security levels, and develop access control measures.
What does SL-A represent?
Achieved security level, which is the current security level of a zone or conduit.
What does SL-C stand for?
Capability security level, the highest security level obtainable by a zone or component.
What is the role of surveillance technology in the 'Deter' strategy?
To make it obvious to potential intruders that they are being monitored.
What is the objective of the delay perimeter?
To slow down an intruder to allow security personnel to respond.
What is the importance of logical and physical boundaries in security documentation?
To define the scope and limits of security measures for each zone or conduit.
What are the main components of a security strategy for access points?
Identifying physical and cyber access points and developing corresponding security measures.
What does the term 'tolerable risk' refer to?
The level of risk that an organization is willing to accept.
What is the role of the ISA99 community?
To discuss and develop standards related to industrial automation and cybersecurity.
What is the purpose of establishing a Target Security Level (SL-T)?
To clearly communicate the desired security level for design and implementation.
What is meant by 'integrated, defense-in-depth' in the context of the Five 'Ds'?
A comprehensive approach that uses multiple layers of security measures to protect against threats.
What is the purpose of applying the 5Ds in IACS Cybersecurity?
To develop a multi-faceted physical and cybersecurity protection strategy.
What should security policies and procedures address?
Both physical and cybersecurity in the protection of assets.
What is required to establish physical security perimeters?
One or more barriers to unauthorized access to protected assets.
What is the objective of deterring cyber attacks?
To prevent attackers from attempting a breach of the system.
Name one strategy to deter cyber attacks.
Implementing policies and procedures.
What is the goal of detecting cyber attacks?
To monitor systems for unauthorized intrusion and respond appropriately.
What tools can be used for detecting cyber attacks?
Intrusion detection systems (IDS), security incident and event monitoring (SIEM), and anti-virus software.
What is the purpose of delaying cyber attacks?
To slow down an active intrusion to allow security teams to respond.
Name a strategy for delaying cyber attacks.
Implementing security hardening and patching.
What is the objective of denying cyber attacks?
To keep unauthorized users or software out while allowing authorized access.
What tools can be used to deny cyber attacks?
Firewalls, whitelisting, and intrusion prevention systems (IPS).
What does the 'defeat/respond' phase entail?
Taking action to eradicate intruders or malicious software and restoring normal conditions.
What is a secondary objective of the defeat/respond phase?
To retain forensic evidence to identify and apprehend the intruder.
What is included in a conceptual cybersecurity design specification?
Documenting new or upgraded security countermeasures to achieve the Target Security Level (SL-T).
What are the 7 Foundational Requirements (FR) in ISA/IEC-62443?
1. Identification and authentication control (IAC), 2. Use control (UC), 3. System integrity (SI), 4. Data confidentiality (DC), 5. Restricted data flow (RDF), 6. Timely response to events (TRE), 7. Resource availability (RA).
What does the SL vector method describe?
It describes security requirements for a zone, conduit, component, or system using multiple values instead of a single number.
What is the significance of the 'least privilege' principle?
It ensures that users have the minimum level of access necessary to perform their functions.
What is the role of access controls in foundational requirements?
Access controls must not prevent the operation of essential functions of high availability IACS.
What is the objective of the 'Deter' strategy in cybersecurity?
To discourage attackers from attempting to breach the system.
What is meant by 'security hardening'?
The process of securing a system by reducing its surface of vulnerability.
What is the function of intrusion prevention systems (IPS)?
To monitor network traffic for malicious activity and block it.
What is the purpose of multifactor authentication?
To enhance security by requiring multiple forms of verification before granting access.
What are some examples of delay strategies in cybersecurity?
Encryption, network segmentation, and access controls.
What is the importance of training personnel in cybersecurity?
To help them detect phishing and social engineering attacks effectively.
What does 'timely response to events' refer to in cybersecurity?
The ability to react quickly to security incidents to minimize damage.
What is a 'honey pot' system?
A security resource whose value lies in being probed, attacked, or compromised.
What does 'obscurity' refer to in deterrent strategies?
Making systems less visible or understandable to potential attackers.
What is the purpose of Authorization enforcement?
To ensure that only authorized users have access to the system.
What does SR2.02 refer to in wireless use control?
It refers to the management and control of wireless access to the system.
What is the significance of Session lock in control systems?
It prevents unauthorized access by locking user sessions after a period of inactivity.
What is the role of Active Directory in access control?
It provides centralized management for Windows-based systems and can also support Radius and LDAP.
What does FR3 focus on in System Integrity?
It ensures the integrity of the Industrial Automation and Control System (IACS) to prevent unauthorized manipulation.
What is meant by Communication integrity (SR3.01)?
It ensures that communication channels are secure and data is not altered during transmission.
What is the purpose of Data Confidentiality (FR4)?
To ensure the confidentiality of information on communication channels and in data repositories.
What technologies are used for Data Confidentiality?
Physical security, encryption/cryptography, and secure protocols.
What does FR5 aim to achieve regarding Restricted Data Flow?
It aims to limit unnecessary data flow by segmenting the control system via zones and conduits.
What is the function of Intrusion Detection Systems (IDS)?
To monitor network traffic for suspicious activity and potential threats.
What does FR6 emphasize in Timely Response to Events?
It emphasizes responding to security violations by notifying authorities and taking corrective action.
What is the role of Continuous Monitoring in security?
To ensure ongoing surveillance of the system for any security breaches or anomalies.
What does FR7 focus on regarding Resource Availability?
It ensures the availability of the control system against degradation or denial of essential services.
What technologies are utilized for Resource Availability?
Rate limiting firewalls, backup/restore tools, and Uninterruptible Power Supply (UPS).
What is the ISA 62443-4-1 framework about?
It outlines Product Security Development Life-Cycle Requirements for secure component development.
What does the term 'Defense in depth' refer to?
A security strategy that employs multiple layers of defense to protect information and systems.
What is the purpose of Change and version management in system integrity?
To track and control changes to system configurations and software to maintain integrity.
What does SR4.03 highlight in the context of Data Confidentiality?
It emphasizes the use of cryptography to protect sensitive information.
What is the significance of Error handling (SR3.07)?
To ensure that the system can gracefully handle errors without compromising security or functionality.
What does the term 'Malicious code protection' (SR3.02) refer to?
It involves measures to detect and prevent malware from affecting the system.
What is the purpose of Network segmentation (SR5.01)?
To isolate different parts of the network to enhance security and control data flow.
What does the term 'Least functionality' (SR7.07) imply?
It refers to configuring systems to provide only the necessary functions to reduce vulnerabilities.
What is the Capability Maturity Model Integration for Development (CMMI-DEV)?
A framework that ranges from Level 1: Initial to Level 4: Improving, focusing on continuous improvements in processes.
How many practice requirements are outlined in CMMI-DEV?
47 practice requirements covering development processes, threat modeling, and secure operation guidelines.
What does ISA/IEC-62443-4-2 provide?
Component requirements for four types of components: Software application, Embedded device, Host device, and Network device.
What is the purpose of ISA/IEC-62443-3-3?
It provides System Requirements (SR) and Requirement Enhancements (RE) for security.
What is the role of ISASecure in the certification process?
It uses certified components with matching or exceeding Security Level Capabilities (SL-C) to help in achieving Security Level Assurance (SL-A).
What are the seven foundational requirements in ANSI/ISA-62443-3-3?
They relate to Security Level Target Vector (SL-T) and technologies used per Foundational Requirement (FR).
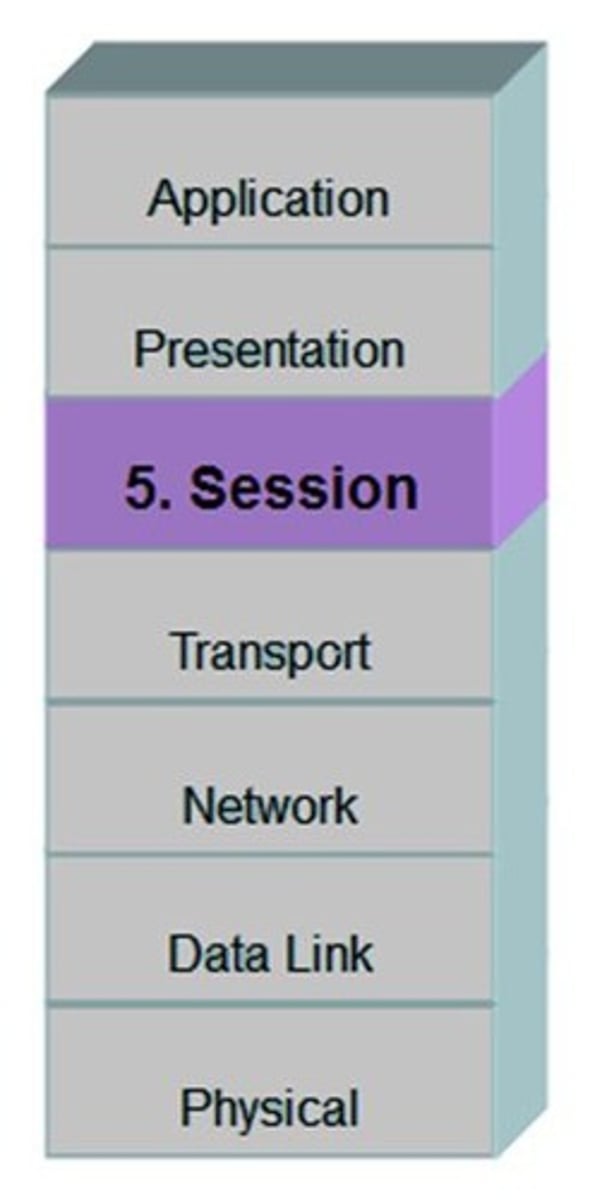
What is the ISO OSI Reference Model?
A conceptual model for communication developed in the 1980s that partitions the flow of data in a communication system.
What does Layer 1 of the OSI model define?
The physical protocols for transmitting messages between devices, including frequencies, voltages, and connectors.