Computer Science AS / A Level Year 1 Full Content
1/411
Earn XP
Description and Tags
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
412 Terms
What is the ALU and what operations does it perform?
The ALU completes all of the arithmetical and logical operations. Arithmetical operations include all mathematical operations such as addition and subtraction on fixed or floating-point numbers. Logical operations include Boolean logic operations such as AND, OR, NOT, and XOR.
What is the main function of the processor?
The processor is the brain of a computer and executes instructions, which allows programs to run.
What are the responsibilities of the Control Unit (x5)?
The Control Unit directs the operations of the CPU. Its jobs include:
Controlling and coordinating the activities of the CPU.
Managing the flow of data between the CPU and other devices.
Accepting the next instruction.
Decoding instructions.
Storing the resulting data back in memory.
What are registers and what is their general purpose?
Registers are small memory cells that operate at a very high speed. They are used to temporarily store data, and all arithmetic, logical, and shift operations occur in these registers.
What is the purpose of the Program Counter (PC)?
Holds the address of the next instruction to be executed.
What does the Accumulator (ACC) do?
Stores the results from calculations, from the ALU
What is the function of the Memory Address Register (MAR)?
Holds the address of a location that is to be read from or written to.
What is the role of the Memory Data Register (MDR)?
Temporarily stores data that has been read or data that needs to be written.
What does the Current Instruction Register (CIR) do?
Holds the current instruction being executed, divided up into operand and opcode.
What are buses in the CPU and what do they connect?
Buses are a set of parallel wires which connect two or more components inside the CPU. The three buses (data, control, and address) are collectively called the system bus.
What is bus width and how does it affect data transfer?
The width of the bus is the number of parallel wires it has. It is directly proportional to the number of bits that can be transferred simultaneously at any given time. Buses are typically 8, 16, 32 or 64 wires wide.
Describe the Data Bus.
This is a bi-directional bus (meaning bits can be carried in both directions) used for transporting data and instructions between components.
Describe the Address Bus.
This bus transmits the memory addresses specifying where data is to be sent to or retrieved from. The width of the address bus is proportional to the number of addressable memory locations.
Describe the Control Bus and its signals.
This is a bi-directional bus used to transmit control signals between internal and external components. It coordinates the use of the address and data buses and provides status information. Control signals include bus request, bus grant, memory write, memory read, interrupt request, and clock.
What is assembly language, and how is an instruction structured in the CIR?
Assembly code uses mnemonics (e.g., ADD for addition) to represent instructions, providing a simplified way of representing machine code.
In the Current Instruction Register (CIR), an instruction is divided into an operand and an opcode.
The operand contains the data or the address of the data, while the opcode specifies the type of instruction to be executed.
What is pipelining and how does it improve efficiency?
Pipelining is the process of completing the fetch, decode, and execute cycles of three separate instructions simultaneously.
It holds appropriate data in a buffer near the CPU until required, aiming to reduce the amount of the CPU kept idle.
While one instruction is being executed, another can be decoded, and another fetched. It is separated into instruction pipelining and arithmetic pipelining.
What is the Fetch-Decode-Execute Cycle?
It is the sequence of operations that are completed in order to execute an instruction.
Describe the steps of the Fetch phase in the F-D-E Cycle.
PC → MAR
The Program Counter (PC) holds the address of the next instruction. This address is copied into the Memory Address Register (MAR).Memory read (RAM → MDR)
The instruction at that address is fetched from main memory. It travels along the data bus into the Memory Data Register (MDR).MDR → CIR
The fetched instruction in the MDR is then copied into the Current Instruction Register (CIR).PC incremented
The Program Counter is incremented so it points to the next instruction (ready for the next cycle).
Describe the Decode phase in the F-D-E Cycle.
The contents of the Current Instruction Register (CIR) are split into operand and opcode.
Describe the Execute phase in the F-D-E Cycle.
The decoded instruction is executed.
What are the three main factors affecting CPU performance?
Clock speed, number of cores, and the amount and type of cache memory.
How does clock speed affect CPU performance?
The clock speed is determined by the system clock, an electronic device that generates signals (switching between 0 and 1). All processor activities begin on a clock pulse (when the clock changes from 0 to 1), so a higher clock speed means more operations can start per second.
Tell me about the clock in a computer
This synchronises the different components in a CPU by providing an electrical pulse.
The pulse is created by a quartz crystal, but an ADC (Analogue to digital converter) changes this to more sudden changes in p.d.
The components usually synchronise to the very start of an on signal.

How do multiple cores affect CPU performance?
A core is an independent processor capable of running its own fetch-execute cycle.
A computer with multiple cores can complete more than one fetch-execute cycle at any given time, theoretically allowing tasks to be completed much faster (e.g., twice as fast with dual cores).
However, not all programs can efficiently utilise multiple cores if not designed to do so.
What is cache memory and how does it improve performance?
Cache memory is the CPU’s onboard memory. Instructions fetched from main memory are copied to the cache, allowing quicker access if they are required again. As the cache fills up, unused instructions are replaced.
Describe Level 1 Cache.
Very fast memory cells with a small capacity (2-64KB).
Describe Level 2 Cache.
Relatively fast memory cell, with a medium-sized capacity (256KB-2MB).
Describe Level 3 Cache.
Much larger and slower memory cell compared to Level 1 and Level 2.
What are the key characteristics of Von Neumann Architecture?
This architecture includes basic computer components (single control unit, ALU, registers, and memory units).
It uses a shared memory and a shared data bus for both data and instructions.
It is built on the stored program concept.
What are the advantages of Von Neumann Architecture?
Cheaper to develop as the control unit is easier to design. Programs can be optimised in size, this makes it flexible: no space is wasted.
What are the disadvantages of Von Neumann Architecture?
The data and instructions have to share a bus, and this slows down transfer.
Memory cells cannot be specialised to handle data and instructions, as they can differ in structure quite a bit.
What are the key characteristics of Harvard Architecture?
Harvard architecture has physically separate memories for instructions and data.
This design is useful when memories have different characteristics (e.g., read-only instructions, read-write data), and allows for optimising the size of individual memory cells and their buses.
What are the advantages of Harvard Architecture?
Quicker execution as data and instructions can be fetched in parallel. Memories can be different sizes, which can make more efficient use of space. It is more commonly used with embedded processors, where speed takes priority over complexity.
What are the disadvantages of Harvard Architecture?
Space can be wasted such as if data RAM is full, but instruction RAM is empty.
Programming can be harder and more complex.
How do contemporary processors use architecture?
Contemporary processors use a combination of Harvard and Von Neumann architecture.
Von Neumann is used when working with data and instructions in main memory,
but Harvard architecture is used to divide the cache into instruction cache and data cache.
What are RISC processors characterized by (x5)?
RISC processors have a small instruction set.
Each instruction is approximately one line of machine code and takes one clock cycle.
Pipelining is possible.
The compiler has to do more work to translate high-level code,
More RAM is required to store the code.
What are CISC processors characterized by (x6)?
CISC processors have a large instruction set, aiming to accomplish tasks in as few lines of assembly code as possible.
These instructions are built into the hardware.
They are now more used in microcontrollers and embedded systems.
The compiler has less work to translate high-level code.
Less RAM is required since the code is shorter.
However, many specialised instructions are made, even though only a few of them are used.
What is a GPU and what are its uses?
A GPU is a specialised processor designed for parallel processing, originally to handle graphics rendering. It contains hundreds or thousands of smaller cores that can perform many calculations simultaneously, making it ideal for tasks that can be split into parallel operations.
Parallel architecture → many cores working at once.
Optimised for repetitive maths (e.g. vectors, matrices).
Works with the CPU: CPU handles sequential tasks, GPU handles parallel ones.
It is used in repetetive tasks such as graphics rendering and AI.
CPU vs GPU:
CPU → few powerful cores, sequential tasks.
GPU → many weaker cores, parallel tasks.
GPUs are best when a problem can be divided into many independent operations.
What is a coprocessor?
This is a type of processor that works alongside the main CPU, taking over specific tasks to free up the CPU, like mathematical calculations or graphics rendering.
What are multi-core systems?
Multi-core CPUs have multiple independent cores that can complete instructions separately, resulting in higher performance.
They generally perform better in larger projects than parallel systems.
What are parallel systems?
Parallel systems accomplish a similar task to multi-core systems but can complete tasks with a single core by using threading.
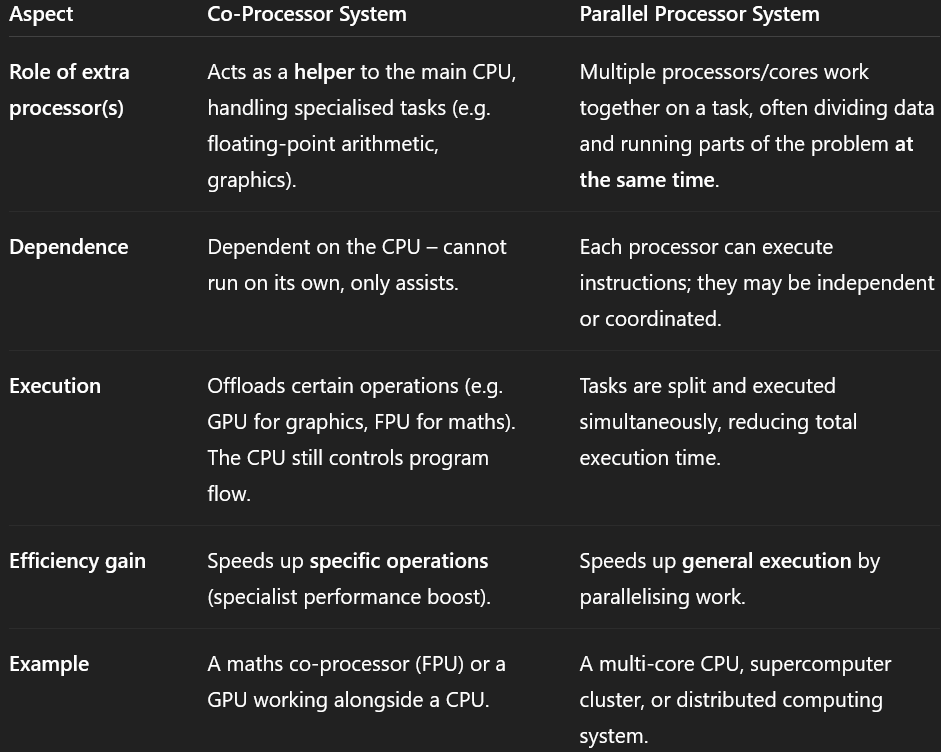
Compare Co-Processor System and Parallel Processor Systems
What is an input device? Provide examples.
An input device is one which can be used to put data and information into a computer. Examples include a keyboard, webcam, magnetic stripe reader, and barcode reader.
What is an output device? Provide examples.
An output device is one which can be used to send information from the computer. Examples include speakers, printers, and a projector.
Can a device be both an input and an output device? Provide an example.
Yes, a small number of devices can be categorised as both input and output devices. For example, a touch screen outputs information visually while acting as a device for touch input.
How do optical devices store and read information?
Optical devices are read from and written to using lasers. Binary information is represented by portions of the disc (pits and lands) which either reflect or scatter the incident laser light, written in spiral tracks. Pits represent a 0 and lands represent a 1.
Describe CDs and their characteristics.
Types of CDs?
CDs use optical technology to store small quantities of information, most commonly for audio files, text, and digital images.
They are portable but are easily damaged by scratches, have limited storage capacity, and relatively slow transfer speeds.
Varieties include CD-R (write once), CD-RW (rewritable), and CD-ROM (read-only after production).
Describe DVDs.
Similar to CDs, DVDs are optical devices with a higher storage capacity than CDs, making them suited to storing digital videos.
Describe Blu-Ray discs.
An advancement over DVDs, Blu-ray discs have more than five times as much storage than traditional DVDs, useful for storing high-resolution films.
How do magnetic devices store binary information?
Magnetic devices represent binary information using two magnetic states: polarised and unpolarised. These two states (1 and 0) are read by a read/write head.
Describe HDDs and their characteristics.
HDDs typically have high capacities (500GB to 5TB).
They work by rotating magnetic platters at high speeds under a read/write head on an actuating arm.
Disadvantages include somewhat slow data transfer speeds and a tendency to become damaged by movement due to brittle platters and moving parts.
They spin 3600 to 7200rpm.
Describe magnetic tape.
First used in the 1950s, magnetic tape stores data magnetically on long stretches of tape wound onto reels.
It was a bulky way to store data, though improvements were made.
Describe floppy disks.
A floppy disk comprises a thin magnetic disk enclosed in plastic, making them incredibly portable for exchanging small amounts of data.
They had a typical storage capacity of 1MB, with some later versions up to 200MB.
How does flash storage work and what are its key properties (x4)?
Flash storage is fast and compact, using silicon semiconductors (NAND and NOR logic gates) to store electrical charge in one of two states (high or low) representing binary values.
Information is stored in blocks, which form pages. It can be electronically erased and reprogrammed, is non-volatile (retains data without power).
NOR is preferred for small data, NAND for larger files.
Generally, it is more expensive per gigabyte than magnetic and optical storage.
Describe SSDs and their advantages/disadvantages.
SSDs are extremely light and portable and have no moving parts, making them much more resistant to damage from movement than HDDs.
They are renowned for their high data transfer rates.
The primary disadvantages are their cost (though decreasing)
and their limited lifespan, as repeated writing increases the required voltage until pages become un-writable.
What is RAM and its characteristics?
RAM is a type of fast primary storage used to store data and programs the computer is currently using, which speeds up execution.
It has higher access speeds than even flash memory.
RAM is volatile, meaning it loses its information when power is lost, so it's used for temporary storage while the computer is running, not personal files.
It is more expensive per gigabyte than secondary storage devices.
What is ROM and its characteristics?
ROM, as the name suggests, cannot be modified once programmed; the state of its memory cells does not change.
It is useful for storing fixed sequences of instructions, like a computer’s startup (bootstrap) routine.
ROM is non-volatile, meaning it retains its data even when the computer is powered off.
What is virtual (cloud) storage and its advantages/disadvantages?
Virtual storage is the name given to storing information remotely so that it can be accessed by any computer with access to the same system, for example over the Internet.
Examples include cloud storage services (Google Drive, Microsoft OneDrive) and networked storage.
While convenient to access and share (often an abstraction of multiple drives acting like one), its disadvantages include limitations of a user’s network speed and high costs.
What is software mailing?
Usually a rental service, for movies etc.
Back in the day it was used for CDs, DVDs, Blu-Ray
The box needs to be well packaged to prevent damage.
What is an operating system?
A collection of programs that work together to provide an interface between the user and the computer.
They enable user communication with the computer and manage low-level tasks like memory and resource management.
What first happens when a computer is turned on?
Bootloader in ROM loads the OS to RAM, when the computer is switched on.
3 types of user interface.
Graphical - Normal Windows
Text-Based - Command Line
Natural language - Alexa
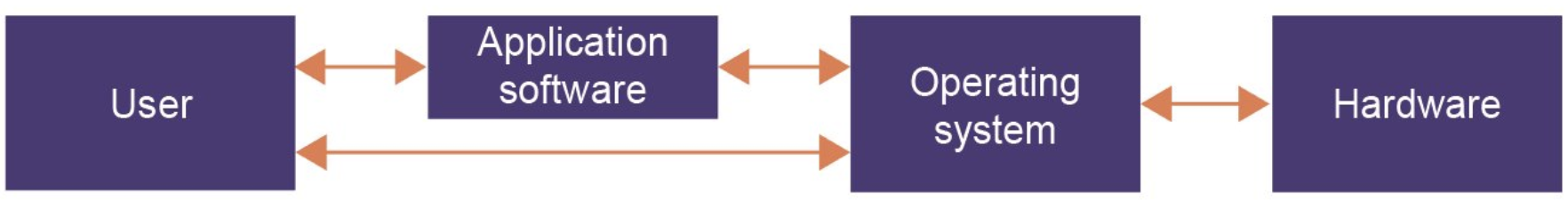
Explain the dynamic between hardware, application software, OS and the user.
Name the essential features an operating system provides (x7).
IF PUMAS
Interrupts
File
-
Peripherals
UI
Memory
Anti-malware
Scheduling
What is the role of memory management in an OS?
To ensure main memory is shared fairly and efficiently between multiple programs and applications, especially when main memory is not large enough for all programs being used.
It uses paging, segmentation, and virtual memory.
What is paging in memory management?
Memory is split into equal-sized sections called pages. Programs are also made of equally-sized pages, which can be swapped between main memory and the hard disk as needed.
What is segmentation in memory management?
Memory is split into logical-sized divisions called segments, which vary in size. These segments represent the structure and logical flow of a program, allocated to blocks of code like conditional statements or loops.
What is virtual memory?
Uses a section of the hard drive to act as RAM when main memory is insufficient. Sections of programs not currently in use are temporarily moved to virtual memory via paging, freeing up RAM.
What is "disk thrashing" and what causes it?
When the computer 'freezes' due to pages being swapped too frequently between the hard disk and main memory. More time is spent transferring pages than running the program, worsening as virtual memory fills.
What are interrupts?
Signals generated by software or hardware to indicate to the processor that a process needs attention. They have different priorities, which the OS must consider when allocating processor time.
Where are interrupts stored, and how are they ordered?
Interrupts are stored in a priority queue within a special register called an interrupt register, ordered by their priority.
When does the processor check for interrupts during the F-D-E cycle?
The processor checks the contents of the interrupt register at the end of each Fetch-Decode-Execute cycle.
What happens if a high-priority interrupt exists?
The current contents of the CPU's special purpose registers are temporarily transferred into a stack.
The processor then loads the appropriate Interrupt Service Routine (ISR) into RAM, and a flag is set to signal the ISR has begun.
What happens after an interrupt has been serviced?
The flag is reset, the interrupt queue is re-checked for higher priority interrupts.
If no more or only lower priority interrupts exist, the contents of the stack are transferred back to the registers, and the F-D-E cycle resumes.
What is the purpose of scheduling in an OS?
To ensure all sections of programs being run ('jobs') receive a fair amount of processing time. This is done using various scheduling algorithms.
What characterises pre-emptive scheduling?
Jobs are actively made to start and stop by the operating system.
Examples include Multilevel Feedback Queues, Shortest Remaining Time, and Round Robin.
What characterises non-pre-emptive scheduling?
Once a job is started, it is left alone until it is completed.
Examples include First Come First Served and Shortest Job First.
Describe Round Robin scheduling.
Each job is given a time slice of processor time. Once all jobs in the queue have used their slice, the OS grants another equal slice to each. This continues until a job is completed.
Disadvantage: Longer jobs take much longer due to inefficient splitting, and it doesn't consider job priority.
Describe First Come First Served scheduling.
Jobs are processed in the chronological order by which they entered the queue.
Advantage: Straightforward to implement.
Disadvantage: Does not allocate processor time based on priority.
Describe Multi-level Feedback Queues scheduling.
Uses multiple queues, each ordered based on a different priority.
Disadvantage: Can be difficult to implement due to deciding which job to prioritise based on a combination of priorities.
Describe Shortest Job First scheduling.
The queue is ordered by time required for completion, with the longest jobs serviced last. Best suited for batch systems.
Disadvantages: Requires the processor to know or calculate job duration (not always possible), and there's a risk of processor starvation for longer jobs if short jobs keep being added.
Describe Shortest Remaining Time scheduling.
The queue is ordered by the time left for completion, with jobs having the least time serviced first.
Disadvantage: Risk of processor starvation for longer jobs if short jobs are continuously added.
What is a distributed operating system?
Run across multiple devices, allowing the load to be spread across multiple computer processors when a task is run.
What are embedded operating systems?
Built to perform a small range of specific tasks, and catered towards a specific device.
They have limited functionality, are hard to update, but consume significantly less power.
What is a multi-tasking operating system?
Enables the user to carry out tasks seemingly simultaneously by using time slicing to quickly switch between programs and applications in memory.
What is a multi-user operating system?
Multiple users make use of one computer (e.g., a supercomputer). Requires a scheduling algorithm to ensure fair sharing of processor time and avoid processor starvation.
What is a real-time operating system?
Designed to perform a task within a guaranteed time frame, commonly used in time-critical computer systems.
Crucial for safety in applications like nuclear power station control or self-driving cars.
What is the BIOS and its initial role upon computer startup?
The first program that runs when a computer is switched on.
The Program Counter points to its location.
It's responsible for running key tests before the operating system is loaded into memory.
Why are interrupts needed?
Efficient Handling of I/O Devices
Without interrupts, the CPU would need to constantly check (poll) devices like keyboards, disks, or network cards to see if they need attention.
Interrupts allow devices to signal the CPU only when they actually need service, freeing the CPU to work on other tasks in the meantime.
Responsiveness to Critical Events
Some events, like a hardware fault (e.g., power failure, memory error) or a high-priority task (e.g., handling incoming network packets), require immediate attention.
Interrupts ensure the CPU can pause its current task and quickly deal with urgent events, improving system reliability and responsiveness.
Support for Multitasking and Real-Time Systems
Operating systems rely on timer interrupts to switch between processes, ensuring fair CPU sharing and enabling multitasking.
In real-time systems, interrupts allow the CPU to meet strict timing constraints by handling time-sensitive tasks immediately when they occur.
Name some key tests performed by the BIOS. (x3)
Why is this important?
POST (Power-on self-test): ensures hardware is connected and functional.
Checking CPU clock, memory, and processor are operational.
Testing for external memory devices.
It's critical because the OS can only load into RAM after these checks.
What are device drivers?
Computer programs provided by the operating system that allow the operating system to interact with hardware. They communicate hardware requests to the OS.
What makes device drivers specific?
They are specific to the computer's architecture (e.g., different for smartphones, games consoles, desktop PCs) and also specific to the operating system installed on the device.
What is a virtual machine?
A virtual machine (VM) is a software-driven computer that runs within a physical machine. It mimics a complete computer system, including virtual CPU, memory, storage, and network interface.
What is intermediate code?
Code that is halfway between machine code and object code. It is independent of the processor architecture, making it usable across different machines and operating systems.
What are common uses and benefits of virtual machines?
Creating a development environment for programmers to test programs on different operating systems, saving time and money.
Protection from malware (malware affects the VM, not the device).
Running incompatible software (programs for different OS or versions).
What is a primary disadvantage of running intermediate code in a virtual machine?
Can be considerably slower compared to running low-level code on the device it was designed for.
What is applications software?
Application software is any computer program that is intended for end-user use – not operating, administering or programming the computer. An application is any program that can be categorized as application software. An application is mostly designed to perform one specific task.
It requires systems software to run.
Examples: desktop publishing, word processing, spreadsheets, web browsers.
What is systems software?
Low-level software responsible for running the computer system smoothly, interacting with hardware, and providing a platform for applications software.
The user does not directly interact with it.
Examples: library programs, utility programs, operating system, device drivers.
What are utilities in the context of system software?
Key pieces of system software integral to ensuring the consistent, high performance of the operating system.
Each utility program has a specific function linked to the maintenance of the operating system.
Utility software is a type of system software designed to help analyse, configure, optimise, or maintain a computer. While not essential for the basic functioning of the operating system, these programs perform specific tasks to enhance performance, security, and efficiency. Examples include disk defragmentation, antivirus software, and backup utilities.
What does a compression utility do?
Enables files to be compressed and decompressed, used for transmitting large files over the Internet or for scanned files.