AQA A-Level Computer Science Paper 2 - Data Compression, Graphics, Ciphers
0.0(0)
Card Sorting
1/22
Earn XP
Description and Tags
Last updated 5:55 PM on 1/9/23
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
23 Terms
1
New cards
lossy compression
some information is lost in the process of reducing the file’s size.
* e.g. reducing the resolution of an image or lowering the sample resolution of a sampled audio file.
* e.g. reducing the resolution of an image or lowering the sample resolution of a sampled audio file.
2
New cards
lossless compression
no loss of information when using lossless compression.
* e.g. size of a file can be reduced without decreasing its quality.
* RLE, dictionary-based.
* e.g. size of a file can be reduced without decreasing its quality.
* RLE, dictionary-based.
3
New cards
run length encoding (RLE)
reduces file size by replacing repeated information with one occurance of the repeated information followed by the number of times it is to be repeated.
4
New cards
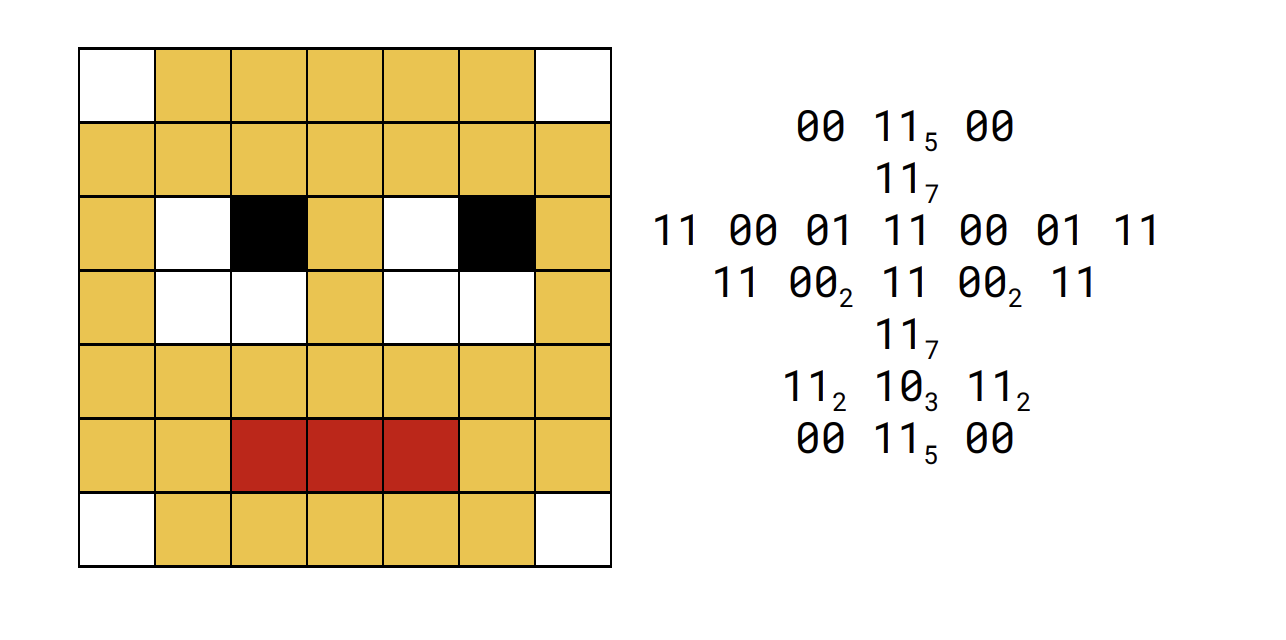
RLE in practice
* replaces repeated pixel with one pixel value and the number of repetitions as a subscript.
* third row of pixels has no repeated value so can’t be compressed.
* shows this compression is not suitable for all data.
* effective on files that contain a lot of repeated data rather than short files.
* third row of pixels has no repeated value so can’t be compressed.
* shows this compression is not suitable for all data.
* effective on files that contain a lot of repeated data rather than short files.
5
New cards
dictionary-based methods
reduces file size by appending a dictionary containing repeated data the file.
6
New cards
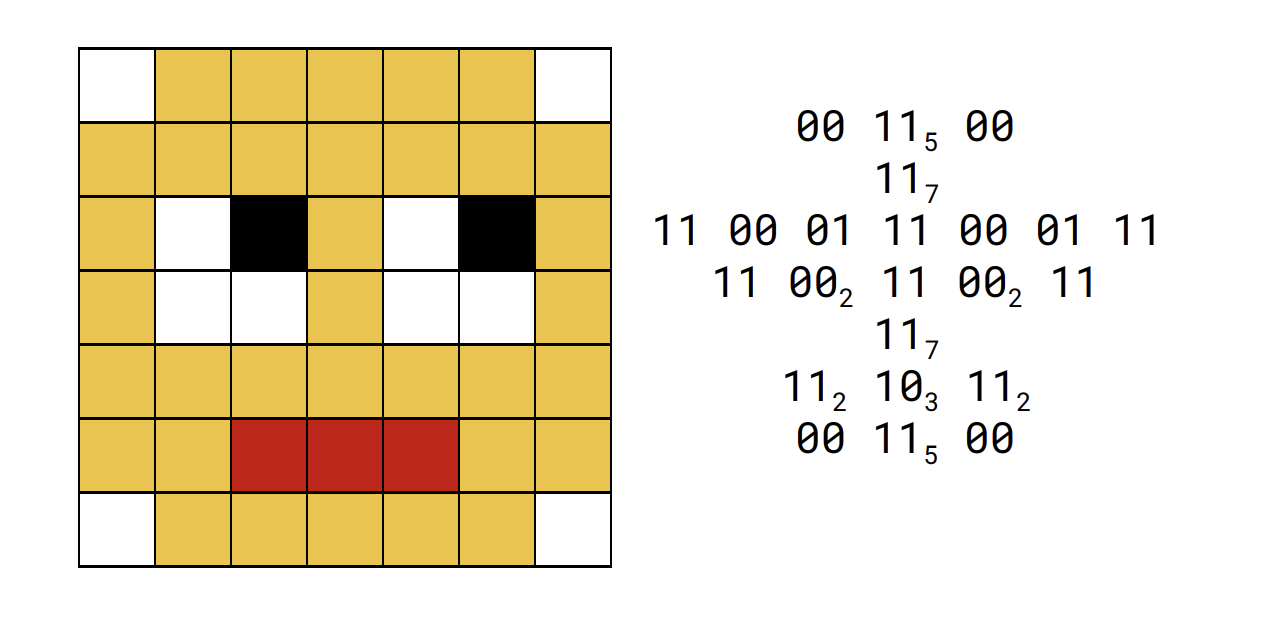
dictionary-based methods in pratice
* the image can be represented just using 1234251.
* significant reduction in size.
* dictionary has to be present in the file so this will increase the file size.
* effective on files that contain a lot of repeated data rather than short files.
* significant reduction in size.
* dictionary has to be present in the file so this will increase the file size.
* effective on files that contain a lot of repeated data rather than short files.
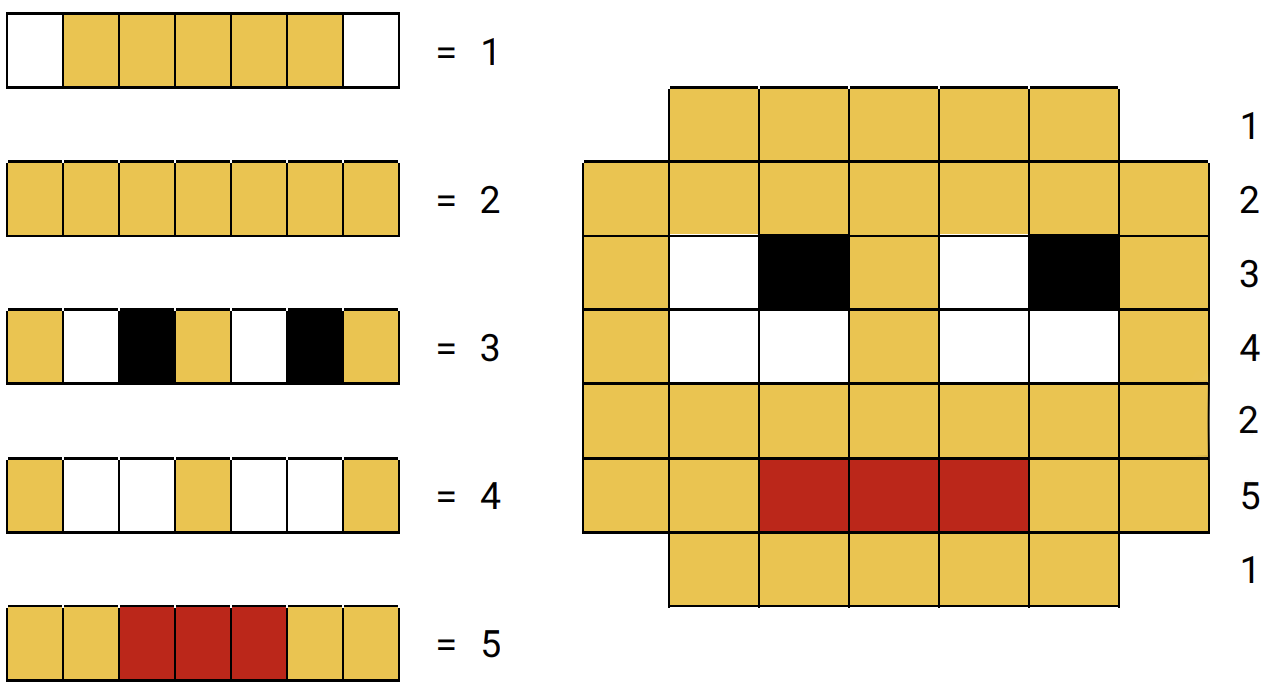
7
New cards
bitmapped graphics
image broken down into pixels, each of which has a binary value assigned to it.
8
New cards
resolution of bitmap
number and depth of pixels in an image.
* number of pixels = pixel width x pixel height
* number of pixels = pixel width x pixel height
9
New cards
colour depth of bitmap
number of bits assigned to a pixel.
* binary representation - each pixel is assigned 1 bit allowing for 2 different colours to be represented.
* binary representation - each pixel is assigned 1 bit allowing for 2 different colours to be represented.
10
New cards
storage requirement calculation
no. of pixels (width x height) x bit depth.
* this is the minimum as file may contain metadata.
* this is the minimum as file may contain metadata.
11
New cards
\
this image has a resolution of 49 bits.
* 7 x 7 = 49
\
this image has a colour depth of 2 bits.
* 4 different colours are represented.
* 00 = white, 01 = black, 10 = red, 11 = yellow
\
minimum storage required is 98 bits
* 7 x 7 x 2 = 98
* 7 x 7 = 49
\
this image has a colour depth of 2 bits.
* 4 different colours are represented.
* 00 = white, 01 = black, 10 = red, 11 = yellow
\
minimum storage required is 98 bits
* 7 x 7 x 2 = 98
12
New cards
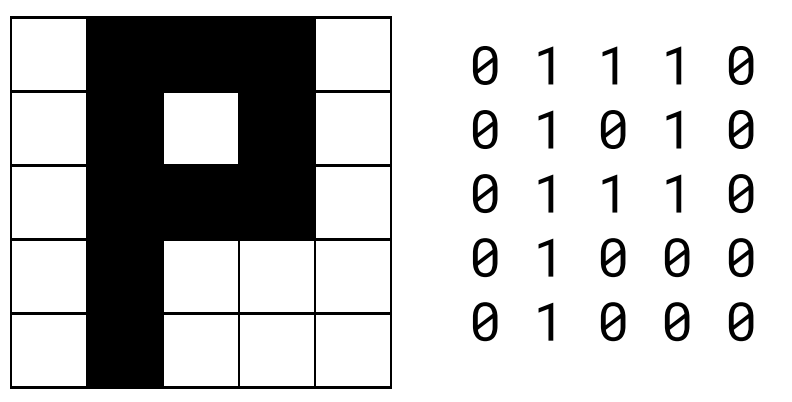
this image has a resolution of 4 bits.
* 2 x 2
\
this image has a colour depth of 1 bits.
2 different colours are represented
* 0 = white, 1 = black
\
minimum storage required is 4 bits
* 2 x 2 x 1 = 4
* 2 x 2
\
this image has a colour depth of 1 bits.
2 different colours are represented
* 0 = white, 1 = black
\
minimum storage required is 4 bits
* 2 x 2 x 1 = 4
13
New cards
vector graphics
represent images using geometric objects and shapes such as rectangles, circles and lines.
14
New cards
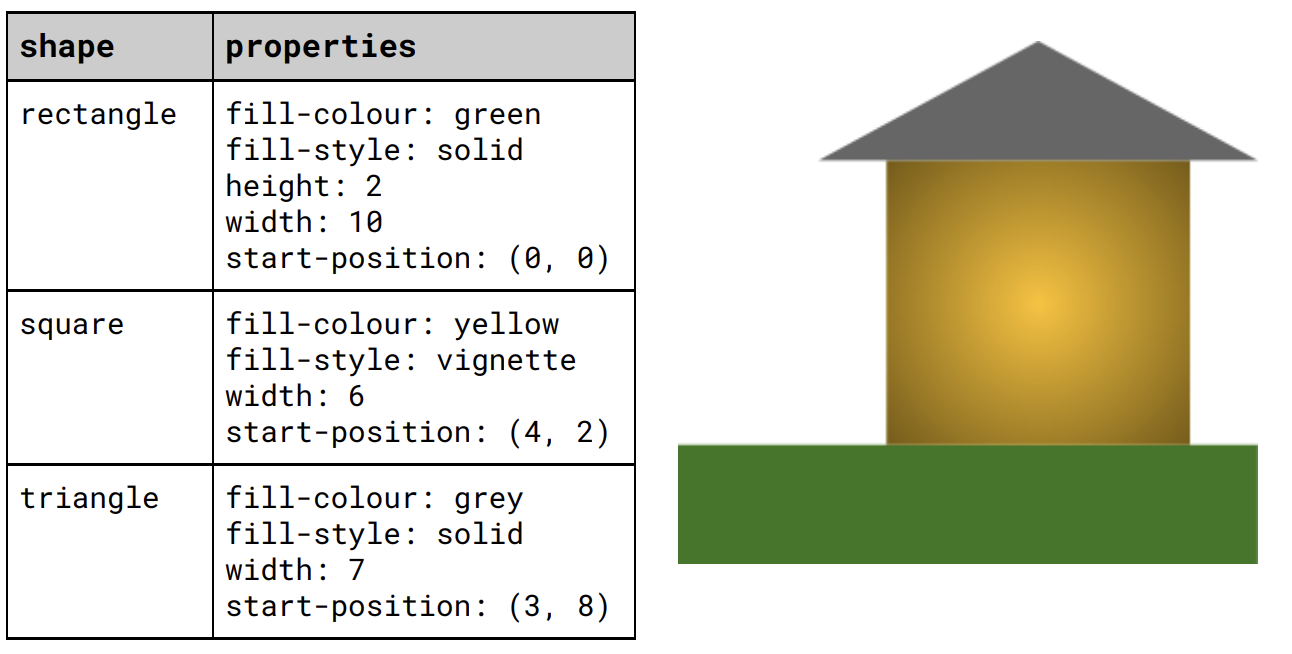
the properties of each geometric object or shape in the image are stored in a list.
* e.g. fill colour, fill style and dimensions
* e.g. fill colour, fill style and dimensions
15
New cards
vector graphics vs bitmapped graphics
* enlarging a bitmap image = blurry or even pixelated image.
* enlarging a vector graphic = in no loss of clarity.
* vector graphics for simple images which use shapes, like company logos.
* not good for photographs/detailed images.
* bitmapped graphics for both simple and detailed images, like company logos or photographs.
* vector graphics use less storage as information is stored for each shape.
* bitmapped graphics store information for every pixel.
* enlarging a vector graphic = in no loss of clarity.
* vector graphics for simple images which use shapes, like company logos.
* not good for photographs/detailed images.
* bitmapped graphics for both simple and detailed images, like company logos or photographs.
* vector graphics use less storage as information is stored for each shape.
* bitmapped graphics store information for every pixel.
16
New cards
vernam ciphers
* invented in 1917 by Gilbert Vernam
* one-time pad cipher
* only cipher considered perfectly secure because:
* each key only used once then destited
* encryption key is truly random and as long as the plaintext that is to be encrypted.
* key is securely shared in person
* one-time pad cipher
* only cipher considered perfectly secure because:
* each key only used once then destited
* encryption key is truly random and as long as the plaintext that is to be encrypted.
* key is securely shared in person
17
New cards
vernam cipher steps
1. align the characters of the plaintext and the key.
2. convert each character to binary (using an information coding system).
3. applying a logical XOR operation to the two bit patterns.
4. converting the result back to a character
18
New cards
computational security
* **all other ciphers** are, in theory, crackable, but not within a *reasonable timeframe* given current computing power.
* ciphers that use this form of security are said to rely on computational security.
* ciphers that use this form of security are said to rely on computational security.
19
New cards
symmetric encryption
the same *private key* is used to both encrypt and decrypt the data.
20
New cards
disadvantages of symmetric encryption
* keys must be kept secret and it is necessary to cycle through keys.
* keys must be shared in advance. can’t be done with individuals you haven’t previously communicated with.
* if you send key across the network unencrypted, an eavesdropper could intercept the communication and retrieve the key.
* keys must be shared in advance. can’t be done with individuals you haven’t previously communicated with.
* if you send key across the network unencrypted, an eavesdropper could intercept the communication and retrieve the key.
21
New cards
asymmetric encryption
a *public key* is used *encrypts* any data and a separate *private key* is used *decrypt.*
22
New cards
public key
key is shared publicly and used by sender to encrypt the data they wish to send to receiver.
23
New cards
private key
key is kept secret by receiver and is never shared as it is the key that is used to decrypt the encrypted data.