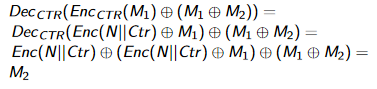2: Symmetric Key Cryptography
5.0(1)
Card Sorting
1/32
Earn XP
Description and Tags
Last updated 9:42 AM on 5/8/23
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
33 Terms
1
New cards

Cryptography
The process of transferring messages between participants without anyone else being able to read or modify them.
2
New cards

Issue with unsecured channels
It can be infiltrated by a malicious actor to either listen to messages or even change them altogether.
3
New cards

Code
A way to represent data, e.g. morse code, ASCII, hex and base64.
4
New cards

Caeser Cipher
A cipher that replaces reach letter with one three to the right, e.g. A becomes D.
5
New cards

Kerckhoff’s Principle
A cipher should be secure even if the attacker knows everything other than the key.
6
New cards
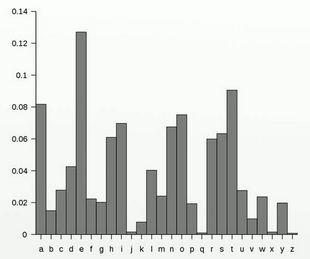
Frequency Analysis
Counts the number of times a symbol and pair of symbols appear in an attempt to crack a cipher.
7
New cards
Symmetric Cryptography
Cryptography where the sender and receiver have the same keys.
8
New cards
Arithmetic Modulo N
Where you can count up to n - 1 and then loop back to 0.
9
New cards
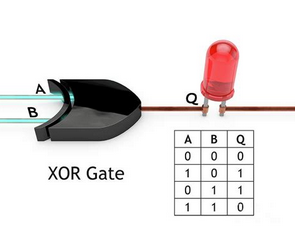
XOR
Binary addition modulo 2.
10
New cards
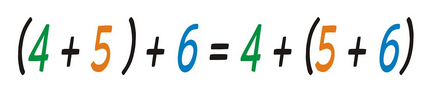
XOR properties
Associative and commutative, for all bitstrings M, M XOR 0 = M and M XOR M = 0.
11
New cards
One-Time Pad
A key that XOR/Adding to the ciphertext produces the plaintext.
12
New cards
One-Time Pad Properties
The key needs to be as long as the message and only used once.
13
New cards

Advanced Encryption Standard (AES)
A state-of-the-art block cipher that works on blocks of 128 bits.
14
New cards
AES Properties
Generates 10 round keys from a single 128-bit key, uses one permutation (shifting rows) and uses three substitutions (substitute bytes, mix columns and add round key).
15
New cards
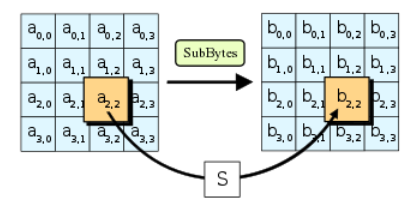
Substitute Bytes
Substitutes bytes using finite field arithmetic.
16
New cards
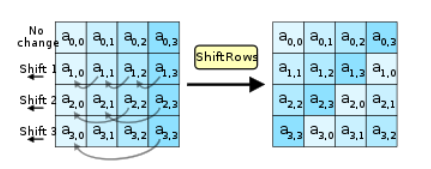
Shift Rows
Shifting rows moves the 2nd row by one byte to the left, 3rd row two bytes to the left and the 4th row three bytes to the left.
17
New cards
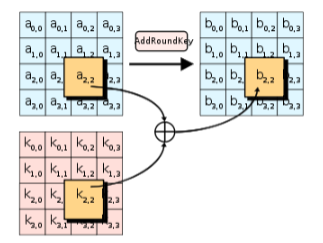
Add Round Key
Applies XOR to the block and the 128-bit round key, generated from the main key.
18
New cards
Data Encryption Standard
A previous standard of symmetric encryption. It was designed by IBM in the early 70’s before the NSA fixed the key length to 56 bytes and added S-boxes.
19
New cards

S-Boxes
A type of substitution in DES that makes it resistant to differential cryptanalysis - without them, DES would’ve been broken in the 90’s.
20
New cards

Triple DES
DES that takes three keys - encrypts a message with the first one, decrypts it with the second key, and encrypts it with the third key. All keys being equal is just DES.
21
New cards

Padding
Extra bytes added to the end of a message if a message is not the right size for block ciphers to work with. The bytes must not be random, and must not just be 0’s.
22
New cards
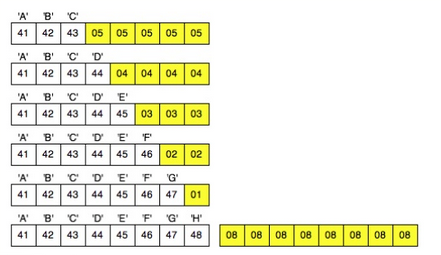
PKCS 5/7 Padding
Used to indicate the padding in a message, i.e. if there is one byte of space to fill, write 01, two bytes, write 0202, three bytes, 030303… if the message goes to the end of the block, add a new block of 16161616…
23
New cards
PKCS 7 Padding
Covers 16 bytes of space.
24
New cards
PKCS 5 Padding
Covers 8 bytes of space.
25
New cards
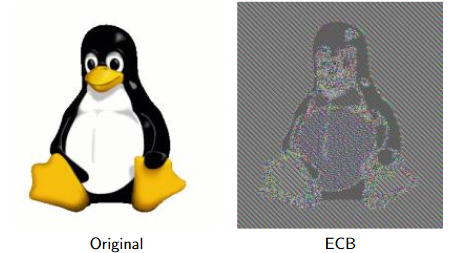
Electronic Codebook Mode (ECB)
Each block is individually encrypted. They are encrypted in the same order as plaintext blocks. Thus, repeated blocks are revealed by the ciphertext.
26
New cards
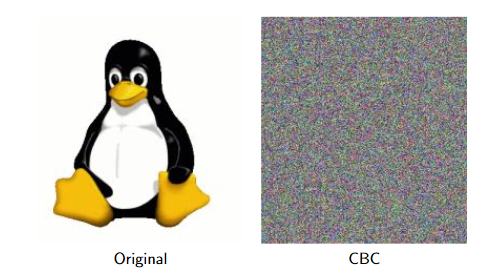
Cipher Block Chaining Mode (CBC)
Each block is XOR’d with the previous block - start with a random initialisation vector (IV).
27
New cards
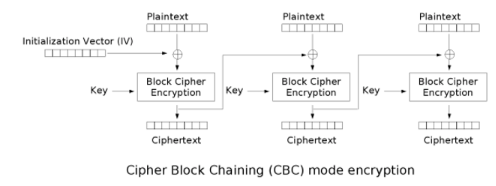
CBC Encryption
1. Split up the plaintext into blocks.
2. XOR the first block with the IV.
3. Encrypt using the key.
4. Take that ciphertext block and XOR it into the next plaintext block.
5. Encrypt that block using the key.
6. Repeat from step 4 until all of the plaintext blocks are encrypted.
28
New cards
CBC Decryption
1. Split up the ciphertext into blocks.
2. Decrypt the first block with the key.
3. XOR result with the IV.
4. Take next block and decrypt it with the key.
5. XOR result with previous result.
6. Repeat until all blocks are decrypted.
29
New cards

Probabilistic Encryption
Uses random events to make every encryption different, e.g. a random event.
30
New cards
Non-Random IVs
Non-Random IVs can easily allow encryption to be cracked - e.g. the Zerologon vulnerability in Windows servers. With that information, authentication could be bypassed and domain controller passwords reset.
31
New cards
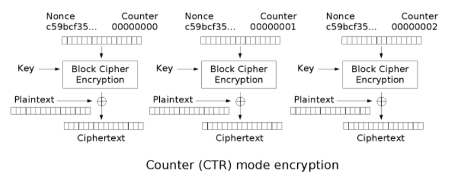
Counter Mode (CTR)
Where each block in plaintext is encrypted with the key then XOR’d with the IV added to the value of the counter (e.g. 0 for the first block, 1 for the second block, etc.).
32
New cards
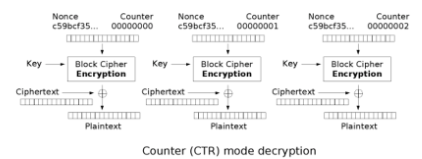
CTR Decryption
1. Split the ciphertext into blocks
2. Take the nonce
3. Encrypt it with the key
4. XOR it with the first ciphertext block
5. Add 1 to the counter
6. Encrypt the nonce and counter added together
7. XOR the next ciphertext block
8. Repeat from step 5 until all blocks are decrypted
33
New cards
CTR Plaintext Attack
If you know the plaintext, you can change the encrypted message. This is done by XOR’ing the plaintext message with the message you want, then XOR’ing the encrypted message with that.