Useful acronyms for Computer Science
0.0(0)
Card Sorting
1/65
Earn XP
Description and Tags
Last updated 5:57 AM on 10/9/22
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
66 Terms
1
New cards
Good luck
)
2
New cards
Translators
C ompiler
I nterpreter
A ssembler
I nterpreter
A ssembler
3
New cards
Central Processing Unit
R egisters
C ontrol Unit
C lock
A rithmetic Logic Unit
B us
C ontrol Unit
C lock
A rithmetic Logic Unit
B us
4
New cards
Functions of an OS
S torage allocation
P rocessor
A pplications
M emory
I nput/Output devices
A ccess rights (security)
P rocessor
A pplications
M emory
I nput/Output devices
A ccess rights (security)
5
New cards
Cyber Security threats
W eak /Default Passwords
O ut of date software
R emovable media (USBs)
M isconfigured access rights
M alicious code (malware)
S ocial Engineering
techniques
O ut of date software
R emovable media (USBs)
M isconfigured access rights
M alicious code (malware)
S ocial Engineering
techniques
6
New cards
Social Engineering Techniques
B lagging
P hishing
P harming
S houldering
P hishing
P harming
S houldering
7
New cards
Malware
V iruses
A dware
T rojans
S pyware
A dware
T rojans
S pyware
8
New cards
Security Measures
B iometric measures
(e.g. mobile devices)
E mail confirmations
C APTCHA (or similar)
A utomatic software
updates
P assword systems
(e.g. mobile devices)
E mail confirmations
C APTCHA (or similar)
A utomatic software
updates
P assword systems
9
New cards
Networks Security Measures
F irewall
A uthentication
M AC Address filtering
E ncryption
A uthentication
M AC Address filtering
E ncryption
10
New cards
IP layer
A pplication Layer
T ransport Layer
I nternet Layer
L ink layer
T ransport Layer
I nternet Layer
L ink layer
11
New cards
TCP / IP layer and protocols
A pplication Layer (HTTP(S), IMAP, SMTP, FTP)
T ransport Layer (TCP, UDP)
I nternet Layer (IP)
L ink Layer (Ethernet, Wi-fi)
T ransport Layer (TCP, UDP)
I nternet Layer (IP)
L ink Layer (Ethernet, Wi-fi)
12
New cards
CPU
Central Processing Unit
13
New cards
RAM
Random Access Memory
14
New cards
ROM
Read Only Memory
15
New cards
HDD
Hard Disk Drive
16
New cards
ODD
Optical Disk Drive
17
New cards
CD
Compact Disk (stores 640 mb)
18
New cards
DVD
Digital Versatile Disk (stores 4.7 gb)
19
New cards
MDD
Magnetic Disk Drive
20
New cards
HDMI
High Definition Multimedia Interface
21
New cards
USB
Universal Serial Bus
22
New cards
VGA
Video Graphics adapter
23
New cards
MICR
Magnetic Ink Character Recognition
24
New cards
OMR
Optical Mark Recognition
25
New cards
OCR
Optical Character Recognition
26
New cards
MCR
Magnetic Chip Readers
27
New cards
MSR
Magnetic Stripe Readers
28
New cards
CRT monitor
Cathode Ray Tube monitor
29
New cards
LCD monitor
Liquid Crystal Display monitor
30
New cards
TFT monitor
Thin Film Transistor monitor
31
New cards
R
Recordable
32
New cards
RW
Rewrite
33
New cards
EPROM
Electronically Programmable Read Only Memory
34
New cards
OS
Operating System
35
New cards
MS DOS
Microsoft Disk Operating System
36
New cards
GUI
Graphics User Interface
37
New cards
WIMP
Windows Icons Menus Pointers
38
New cards
WYSIWYG
What You See Is What You Get
39
New cards
CLI
Command Line Interface
40
New cards
HTML
Hyper Text Markup Language
41
New cards
LAN
Local Area Network
42
New cards
WLAN
Wireless Local Area Network
43
New cards
WAN
Wide Area Network
44
New cards
VPN
Virtual Private Network
45
New cards
p2p
Peer to Peer
46
New cards
NIC
Network Interface Card
47
New cards
IP
Internet Protocol
48
New cards
CSS
Cascading Style Sheet
49
New cards
URL
Uniform Resource Locator
50
New cards
HTTP
Hyper Text Transfer Protocol
51
New cards
ISP
Internet Service Provider
52
New cards
MODEM
Modulator Demodulator
53
New cards
.com
international
54
New cards
.co
company
55
New cards
.ac
university
56
New cards
.org
non-profitory
57
New cards
.info
information
58
New cards
.edu
educational establishment
59
New cards
.sch
school
60
New cards
CC
Carbon Copy
61
New cards
BCC
Blind Carbon Copy
62
New cards
RAID
Redundant Array of Inexpensive Disks
63
New cards
NOT gate
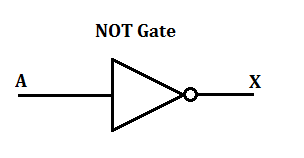
64
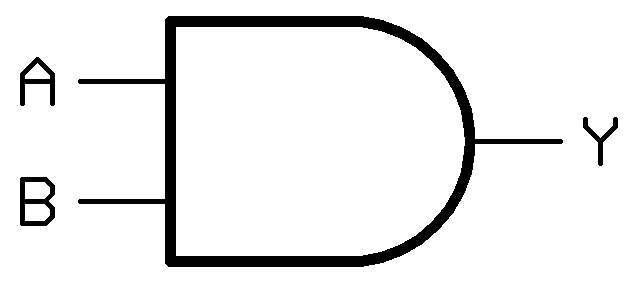
New cards
AND gate
65
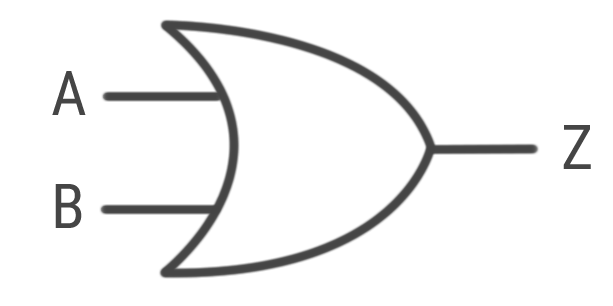
New cards
OR gate
66
New cards
XOR