MS-900 Fun
1/264
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
265 Terms
Power Virtual Agent
a chat bot for integration with Microsoft Teams
Azure Virtual Desktop
Employees frequently work from home. They must be able to access custom applications that are not installed on their personal laptops
Endpoint Configuration Manager
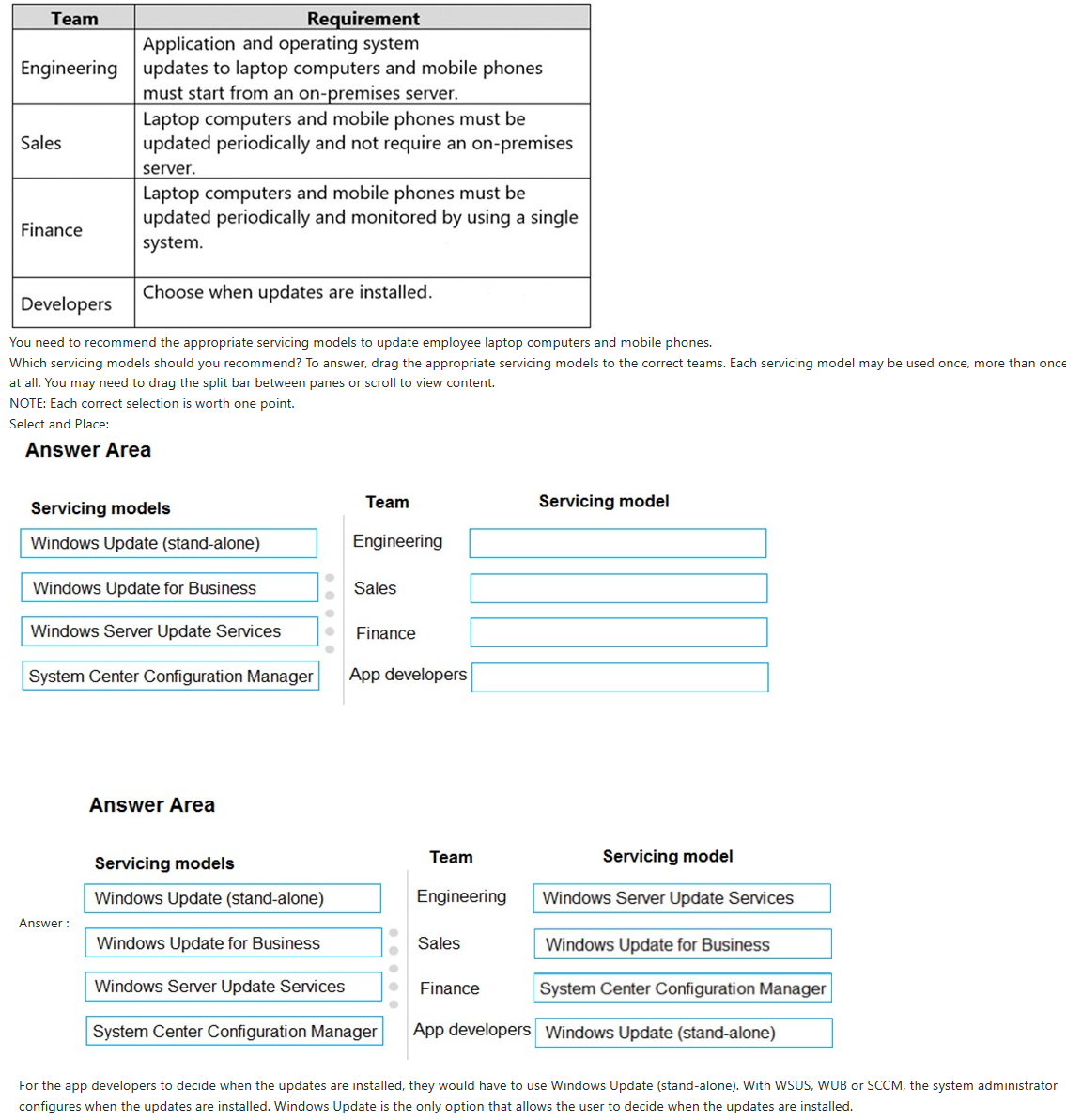
A company uses Microsoft 365 and Windows 10. You need to identify which servicing tools the company should use for Windows 10.
Cloud App Security
solution between the user and the provider to provide control over data travel and sophisticated analytics to identify cyberthreats across cloud services
Microsoft 365 E5, Office 365 E5
phone system deployment, minimize costs
Service Health
View the history of service incidents and advisories that have been resolved.
Track the status of issues reported by people in your organization over the last 30 days.
View service incident, typically involving noticeable user impact.
Teams
The company requires the sales team to record all live demonstrations for training purposes.
Which of the following Microsoft tools can host meetings, and records a live event for customers to discuss new product offerings?
MyAnalytics
suggestions in Microsoft Outlook to review outstanding tasks
suggestions in Microsoft Outlook to delay delivery of emails
Direct model
Cloud Solution Provider (CSP) license is used when partners buy Microsoft products and subscriptions directly from Microsoft and sell them to their clients via their own sales staff?
Entra ID P1 and P2
Users who are based on-premises must be able to reset their own passwords. The company plans to purchase Entra ID licenses
AIP Premium P2
protect documents and emails by automatically applying classifications and labels
Everything but SCOM - Config mgr, Office Deployment Tool, and Intune.
A company needs to ensure that Microsoft 365 Apps for enterprise is installed on all employee computers. Which three tools can you use to deploy Microsoft 365 Apps for enterprise?
Current channel
Update channel Provides the newest features as soon as they are ready
Intune (MEM)
how to register their personal home devices with the company's IT environment for secure access to corporate resources.
Microsoft Defender for Office 365
Helps protect against malicious attachments and links that are sent through email
Is a cloud-based email filtering service that helps protect your organization against advanced threats to email and collaboration tools, like phishing, business email compromise, and malware attacks.
Azure Information Protection
Is a cloud-based solution that enables organizations to classify, label, and protect documents and emails based on their sensitivity
Regional Compliance page of the Services Trust portal
Your company plans to open a new office in the United Kingdom.
You need to provide penetration test and security assessment reports for the new office. Where can you locate the required reports?
Endpoint Manager
Employees use personal devices to access company data in the cloud. You need to restrict employees from copying data to personal OneDrive folders.
Purview Information Protection
can classify and protect information for on-premises file servers
Secure Store
Analyze the security posture within its organization to enable opportunities for improvements in Microsoft 365 identities, data, apps, devices, and infrastructure.
GA only
You use products that are in private preview, public preview, or general availability (GA). You need to determine at which phases you can receive support from the Microsoft 365 admin center
Azure Virtual Desktop
Employees frequently work from home. They must be able to access custom applications that are not installed on their personal laptops.
Endpoint Configuration Manager
You need to identify which servicing tools the company should use for Windows 10.
From SA USL
Existing Volume Licensing agreement and exclusively on-prem.
Add-on USL
Purchased MS Office 2019 for all emps without Volume Licensing. Minimize cost.
From SA USL
Latest version of software, transition to the cloud
Direct bill
Partners purchase MS subscription from MS and sell via in-house sales staff.
Indirect reseller
Providers purchase MS subscription from MS and sell to customers thru third parties
Buy licenses from MS authorized dealer
Company does not provide managed services or direct customer support. Earn commissions on each license sold.
Direct model
Partners buy MS products and subscriptions directly from MS and sell to clients via own sales staff
Direct model
You should meet the following prerequisites:
• Active Microsoft Partner Network ID (MPN ID) for the location you’re enrolling
• Existing customer support infrastructure
• Existing customer billing infrastructure
• Funds to invest in technical integration and support readiness
Indirect model (CompuNet)
Need some infrastructure support for services like billing.
• Indirect providers offer billing, customer service, and technical support during the sales cycle and post deal closing.
• They handle a lot of the backend processes, enabling the indirect reseller to focus on finding and closing deals. Indirect providers typically are large, well-vetted companies.
• In the indirect model, your organization would likely be an indirect reseller.
• Indirect resellers are responsible for finding customers and selling. Due to the support from indirect providers, you can focus on selling and growing your customer base.
MS approach to privacy
BLT SCC - Benefits to you, Legal protections, transparency, security, no content targeting, control
Privacy Risk Management policies
meant to be internal guides and can help you:
• Detect overexposed personal data so that users can secure it.
• Spot and limit transfers of personal data across departments or regional borders.
• Help users reduce the amount of unused personal data that you store
Activity Explorer
Helps discover which file labels were changed, and which files were modified.
Context Explorer
It enables administrators to gain visibility into the content that has been summarized in the overview pane.
Drill down to find emails (Microsoft Exchange) and documents (OneDrive and SharePoint) that’s been labeled based on
• Sensitive info types
• Sensitivity labels
• Retention labels
Classifier
is a machine learning model that can take records of data and classify (categorized) by applying a label from a predetermine list of categories
Trust Documents
provides a wealth of security implementation and design information with the goal of making it easier for organizations to meet regulatory compliance objectives.
• Audit Reports provides a list of independent audit and assessment reports on Microsoft's Cloud services is displayed.
• Data Protection contains a wealth of resources such as audited controls, white papers, FAQs, penetration tests, risk assessment tools, and compliance guides.
Compliance solutions
integrated capabilities you can use to help you manage end-to-end compliance scenarios.
• The solution catalog is organized into sections that contain information cards for each compliance solution available in your Microsoft 365 subscription.
Sentinel
• Security information event management (SIEM)
• Security orchestration automated response (SOAR)
Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for:
• Alert and attack detection
• Threat visibility
• Proactive hunting
• Threat response
Microsoft Defender for Cloud Apps
Cloud Access Security Broker (CASB) that sits between the user and the cloud service provider to gatekeep access in real-time to cloud resources.
Microsoft Defender for Cloud Apps is built on a framework that follows 4 principles:
• 1. Discover and control the use of Shadow IT
• 2. Protect against cyberthreats and anomalies
• 3. Protect your sensitive information anywhere in the cloud
• 4. Assess the compliance of your cloud apps
Device enrollment and Devices blades
Deploy Surface running Win 10 using Autopilot. Use CSV via Device Management Portal
WINDOWS virtual desktop
Allow users to use unsuited apps for Win 10 devices.
Azure AD Conditional Access
Make sure members of Global Admin are protected. Use dynamic risk profiles.
Entra ID - formerly AD FS
Hybrid, use smart card for authentication. Certificate-Based Authentication (CBA): Users can authenticate using X.509 certificates on their smart cards directly against Microsoft Entra ID during Windows sign-in.
Smart Card Sign-In: Users present their physical or virtual smart card, enter their PIN, and authenticate. This process provides a primary refresh token (PRT) from Microsoft Entra ID after successful sign-in.
Intune App Protection
Prevent emps from copying info to their OneDrive.
Azure Info Protection
Add an Entra subscription to your M365 tenant.
Enable the default Entra ID Protection Policy.
Configure data governance strategy for data classification. Classification should be enforced
Publish labels. Apply supervision policies.
Office 365 ProPlus
Deploy Office using subscription based model. Allow Office app settings to be enforced via group policy.
Legacy apps that use message based intelligence
Apps that remain in a hybrid environ after migration
Public cloud
provide on-demand environment
provide fail-over capabilities between resources that you manage and resources in other regions
Private cloud
Deploy virtual machines that support USB devices
Migrate all SharePoint data and Exchange mailboxes to Microsoft 365.
The company runs SharePoint Server and Exchange Server in an on-premises datacenter. The site collection for the finance department is currently encrypted using third-party software.
You need to move as many services to Microsoft 365 as possible.
Paas
website hosting
Iaas
a virtual machine that runs Linux
Both cloud and on-prem
allow to monitor usage of the file storage
Entra App proxy
Yes - you can secure web apps that are published thru Entra Application proxy by using MFA in the cloud.
No - You can secure web apps that are publshed thru Entra App proxy by using MFA Server on-prem
3 features of Iaas
real time monitoring
servers and storage
firewall and network
Azure virtual machine is Iaas
Azure virtual machine is Iaas
Iaas does not include OS
Provides servers, VMs, storage, and networks
Power Apps is Paas
Power Apps is Paas
Azure Virtual Machines is Iaas
Azure Virtual Machines is Iaas
Iaas
enables users to build server based IT workloads in cloud
Teams
not available on-prem
Public preview
can be turned on for evaluation
private preview
avail to specifc customers
compliance testing completed
task you can perform on a deactivated device
Print a doc
Direct team members to sign in to their devices using their Microsoft Azure AD credentials.
Deploy Win 10 devices using Windows Autopilot. Ensure they can access OneDrive content at remote sites.
MyAnalytics
Included in O365 E5 license.
Provides emp work and collab metrics
Workspace Analytics
Can be purchased only as add-on license
Permits upload of custom org data
Provides team work and collab metrics
M365 Usage Analytics. Number of users active today and last month. It’s an Adoption metric.
MoMReturning users.
Exchange Server and Exchange Online
Exchange Web Services (EWS) access to accounts
Info rights mgt, archiving and legal holds.
Surface devices on Win 10, using Autopilot. Use a CSV to ensure devices are ready for deployment. Which blades use?
Devices and Device Enrollment
Private
Complete compliance testing
Public preview
complete QA testing for recently released features
General Availability
prepare QA results and end-user docs
Deploy the app to all devices by using Microsoft Intune.
A company has offices in multiple regions. The company has a Microsoft 365 subscription.
The company is developing a line-of-business (LOB) app. The app must meet the following requirements.
✑ Ensure availability regardless of an employee's location.
✑ Track the devices on which the app is installed by using Microsoft cloud services.
Upgrade devices to use O365 ProPlus
Implement with Win Autopilot
Upgrade all devices to Win 10
Deploy policies using Intune
Win Virtual Desktop
Users need to use incompatible apps on Win 10
Intune
Users need to be prevented from copying company data from managed apps installed on unmanaged devices.
Three methods to deploy O365 ProPlus
SCCM from local dist source.
Use ODT to dl install files to local dist source.
Enable users to dl and install ProPlus from the O365 portal.
Windows update
Limited control over feature updates and ability to manually defer updates
Endpoint Config Mgr
Full control over feature updates and multiple deployment options
Deploy O365 ProPlus using Autopilot
Use self-install on O365 dashboard
Enable auto-deployment of O365 on all devices
Servicing models (image)
image
Change update channels for M365 using two methods
Group Policy
Office Deployment tool
Azure Virtual Desktop
Provides access to full desktop thru browser
Provides access to virtualized app in cloud
Does NOT provide access to offline desktop
You can use co-management if use Config manager to deploy apps and Conditional access policies
Yes
You can use Win Autopilot to manage Office, Edge, or Windows settings
No
You can use Desktop Analytics if use Config Mgr and need to ID app compatibility issues with Win 10
Yes
Booking calendar
schedule vacation for technicians a biz closures
Booking page
schedule customer appts
staff page
view tech’s working hours
MyAnalytics
Does NOT supports PowerBI templates
Does support Outlook add-ins
Workplace Analytics
Supports weekly email digests
A company is evaluating the differences between Microsoft Exchange on-premises and Exchange online.
You need to select the appropriate product for each requirement.
Exchange online directly applies sec updates to Exchange server
Exchange on prem used for M365 groups to send email
Exchange on prem uses Bookings
Intune
can use conditional access policies
Use an @ symbol
User gets email notification shows preview of the doc
Doc can open to comment in the file
User can respond to comment directly in the file
Report - Active users
IDs number of product licenses
DLP
IDs rules applied to info classified as sensitive