MyFirstAttempt
1/23
Earn XP
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
24 Terms
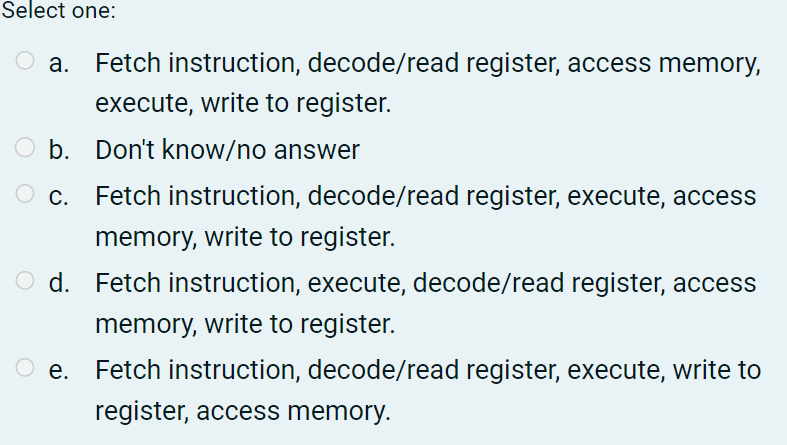
Which is the correct ordering of the stages of the MIPS pipeline?
Fetch instruction, decode/read register, execute, access memory, write to register.
Suppose the cache access time of a computer is 10ns and its main memory access time is 15 times slower. Assuming that the cache hit rate is 70%, what is the effective access time (EAT) for the processor to access an item in the cache?
EAT = 0.7*10ns + (1-0.7)*150ns = 52ns
The correct answer is: 52ns
What is a gibibyte, according to the ISO standard?
The correct answer is: 1,073,741,842 bytes.
What are the binary and decimal representations of the hexadecimal number F4?
To convert from base 16, we remember that F4h means
F x 16^1 + 4 x 16^0
15 x 16 + 4 x 1
240 + 4
24410
The correct answer is: Binary: 11110100 Decimal: 244
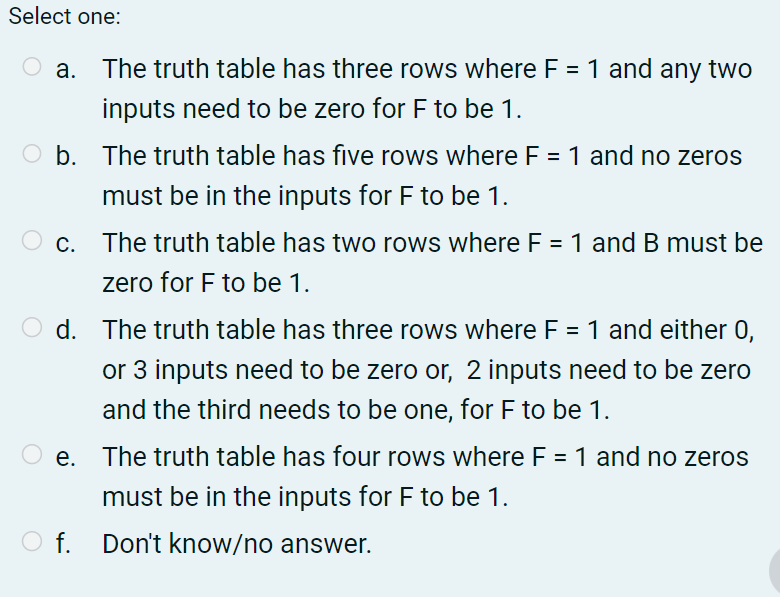
Which of the following statements is the most accurate description for the sum-of-products expression below?
F = ABC + A'B'C + A'B'C'
When you see "OR," it means the expression becomes true if any of the connected parts are true.
Inverted variables (like NOT A or NOT B) mean that those inputs must be zero for that part to be true.
So, when you combine these, it tells you when the whole expression is true based on specific conditions.
The correct answer is: The truth table has three rows where F = 1 and either 0, or 3 inputs need to be zero or, 2 inputs need to be zero and the third needs to be one, for F to be 1.
What is the maximum number of instructions that can be executed simultaneously for the MIPS pseudo-code below?
add a, b, c
sub d, b ,c
add g, e ,d
add h, e, f
sub a, a, b
Instructions 1 and 2 can run together because they don't change any inputs.
Instruction 2 depends on Instruction 3 (d).
Instructions 3, 4, and 5 don't depend on each other.
The largest group of instructions that don't depend on each other is 3.
Mixing instruction types doesn't matter in this case.
Answer is 3.
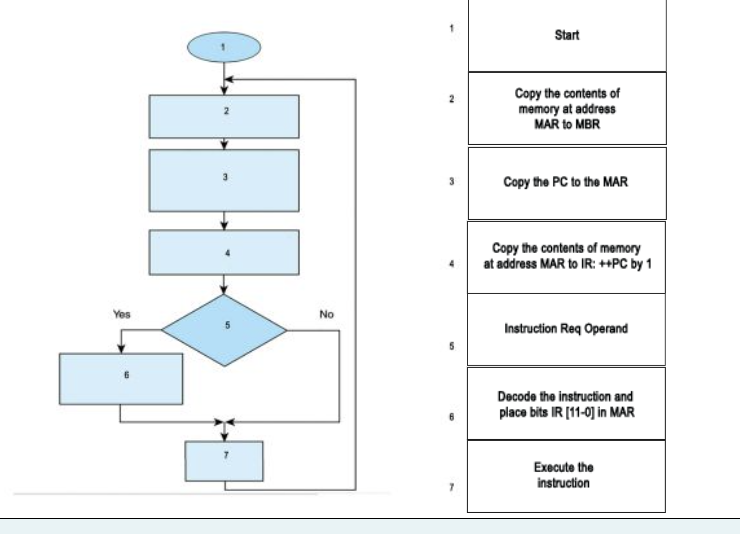
Drag and drop the correct steps of The Fetch–Decode–Execute Cycle in the following flow chart
execute at end
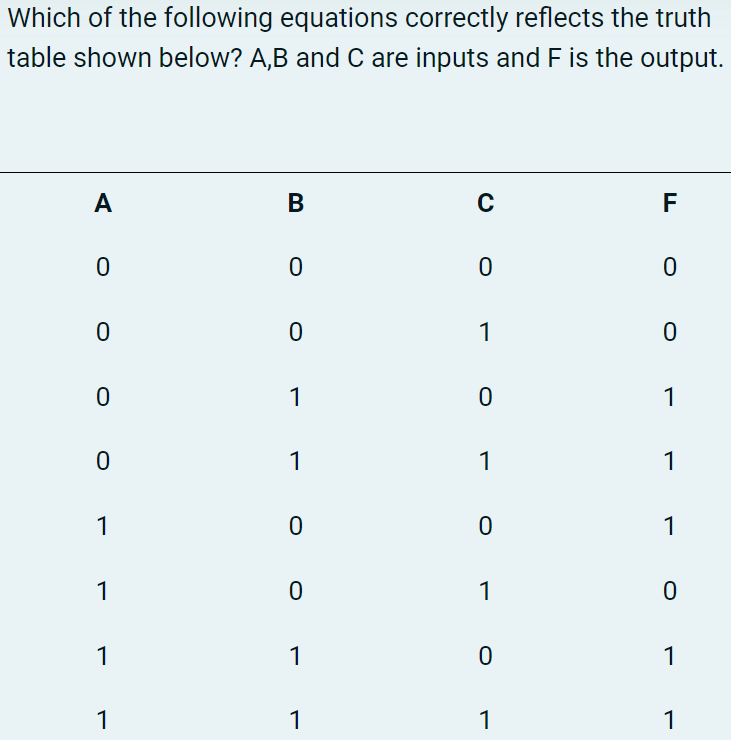
a.
F = (AB'C + A'BC' + A'BC' + A'B'C + A'B'C')'
b.
F = AB'C + A'BC' + A'BC' + A'B'C + A'B'C'
c.
Don't know/no answer
d.
None of these expressions
e.
F = (A'BC ' + A'BC + AB'C' + ABC' + ABC)'
f.
F = A'BC' + A'BC + AB'C' + ABC' + ABC
The F output is given as a sum-of-products expression where each product (AND) should correspond to a row where F = 1.
The correct answer is: F = A'BC' + A'BC + AB'C' + ABC' + ABC
Which MARIE instruction is being carried out by the microoperation that follows?
PC ← X
Jump X
Why is 2’s complement a good way of representing negative numbers?
No special sign bit, easy to implement in hardware, no -0
Which of the following is not an advantage of a CISC architecture?
a.
Specialist instructions to aid the programmer in common tasks.
b.
Specialist instructions that can be optimised in hardware.
c.
Variable instruction lengths to optimise code density.
d.
Rich variety of addressing modes to aid the programmer
e.
Don't know/no answer
f.
Fixed-length, regular format instruction
Having all of the instructions the same length and in a regular format is a RISC feature, as it simplifies decode and execution logics.
The correct answer is: Fixed-length, regular format instructions.
What is the correct result of the operation below? The initial numbers should be considered as unsigned integers. The result should be given in 2's complement. (Hint: use 2's complement arithmetic to perform the operation.)
00001111 - 00010101
To perform the subtraction we find the negative of the subtrahend:
00010101 (subtrahend)
11101010 (1's complement, flip one bit)
00000001 (add 1)
11101011 (2's complement of the subtrahend)
perform the addition:
00001111
11101011 +
11111010 (this is the result in 2's complement or -6 in decimal
The correct answer is: 11111010
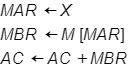
Which MARIE instruction is being carried out by the microoperations that follow?
The correct answer is: Add X
How many superscalar execution units could be used for the MIPS pseudo-code below? Assume no register forwarding.
add a, b, c
add c, b ,c
add f, c ,d
add h, e, f
add f, h, b
The number of execution units that can be used is limited to the largest sized block of non-dependent instructions. All instructions have some dependency with another.
The correct answer is: c
Which of the following is the best description of the concept of sequential locality?
Sequential locality refers to the common feature of programs that instructions tend to be accessed sequentially.
The correct answer is: Instructions tend to be accessed sequentially.
Consider the next MARIE instructions: Load, Add, Store, Subt, Input and Output. Which of the following MARIE registers is not always used in the FDE cycle of the above instructions?
a.
InREG
b.
PC
c.
AC
d.
MAR
The correct answer is: InREG
Which of the following is the best description of ‘branch prediction’?
A method to avoid control hazards by predicting what way a conditional branch instruction will execute in advance.
Which of the following is the best description of a ‘stall’?
A stall occurs in response to a control hazard. It involves waiting for the next instruction to be fetched after a branch is taken.
The correct answer is: Waiting for the next instruction to be fetched after a branch is taken.
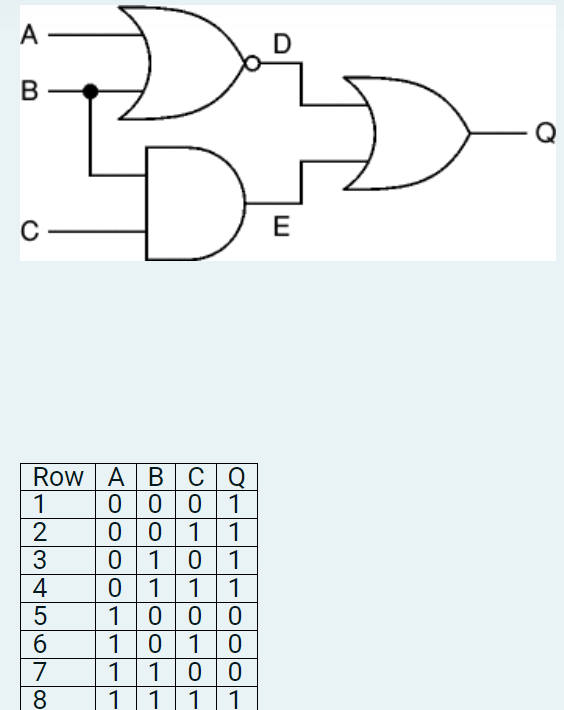
Given the logic circuit and table below (with output Q), which line of the table does not correspond to the behaviour of the logic circuit?
a.
Row 2
b.
Row 6
c.
Don't know/no answer
d.
Row 3
e.
Row 1
f.
Row 4
g.
Row 5
h.
All rows are correct
i.
Row 7
j.
Row 8
Row 3 is in error as the output of the NOR-gate (D) and AND-gate (E) are zero, leading to an output of the OR-gate (Q) of zero.
The correct answer is: Row 3
What are the two fields in an Instruction?
Opcode, Address
Suppose we have a byte-addressable computer using direct mapping with 16-bit main memory addresses and 32 blocks of cache. If each block contains 8 bytes, determine the size of the block field.
Question 37Select one:
a.
16
b.
5
c.
32
d.
8
e.
3
f.
Don't know/no answer
The total size of the tag, block and offset fields is 16.
32 = 25 blocks of cache can be indexed with 5 bits, so block is 5 bits.
Since each block has 8=23 bytes we need 3 bits for the offset to access each byte in the block.
Finally, the tag field is: 16 - 5 - 3 = 8.
The correct answer is: 5
Which of the following is the best description of a ‘control hazard’?
A control hazard occurs when an instruction I has been loaded to a pipeline although due to some condition check which is already being executed in the pipeline it turns out that I should not be executed.
The correct answer is: Executing an instruction in the pipeline whose execution depends upon a yet unknown condition check.
What is the difference in operation between a LOAD x and a LOADI x instruction?
The LOAD loads the value at address x to the AC; the LOADI loads the value found in the location addressed by the value in x to the AC