Network midterm
1/78
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
79 Terms
CH.1 :
Tell me the 3 legs of Security trinity
1) prevention , 2) detection , 3) response
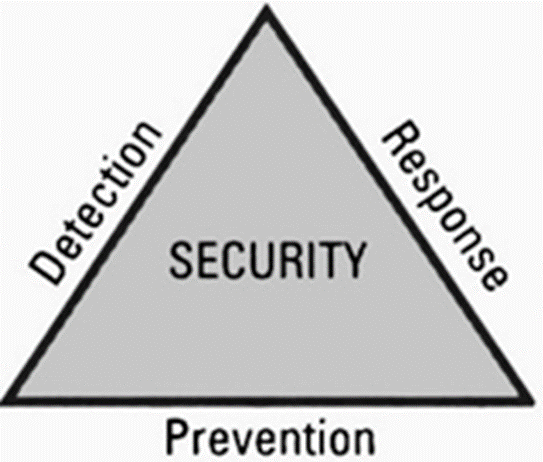
Explain each of the Security trinity
prevention : provides some level of security and implements measures to prevent exploitation of vulnerabilities
Detection : preventative measures that are implemented , procedures need to be put in place to detect potential security problems or breaches in the event preventive measures fail
Response: Organizations need to develop a plan that identifies the appropriate response to a security breach
What are examples of prevention measures?
firewalls
IPS
Access control
Patch management
Examples of Detection measures?
IDS
SIEM
Behavioral analysis
Anomaly Detection
What are the Goals of Network Security?
Confidentiality : privacy or secrecy and refers to the protection of information from unauthorized disclosure
Integrity: the ability to protect information, data, or transmission from unauthorized , uncontrolled , or accidental alternations
Availability : whether the network , software , system , and hardware are available and reliable and can recover quickly in an event of a interruption service

Who are Potential attackers?
Script Kiddes and Opportunistic attackers : have limited technical skills and often use pre-existing tools an scripts to launch attacks
Hackers and Cybercriminals: more advanced technical skills and target organizations for financial gain
Insiders: have legitimate access to systems but misuse that access for personal gain or to harm organization
Nation-State Actors and APTs: state-sponsored attackers which have significant resource an advanced capabilities
Hacktivists: attackers motivated by political or social causes and target organizations to raise awareness or promote their ideology
Tell me the Steps of an attack in detail?
1. Probe for information : The first step in an attack is to probe the system for any information that can be used to attack it. To provide information, such as the type of hardware used, version of software or firmware, and even personal information about the users and that includes ping sweeps of the network to determine if a system responds, port scanning for seeing what ports may be open, queries that send failure messages back to a system when a delivery problem has been detected, and password guessing.
2. Penetrate any defenses- Once a potential system has been identified and information about it has been gathered, the next step is to launch the attack to penetrate the defenses. These attacks come in a variety of forms, such as manipulating or breaking a password.
3. Modify security settings- Modifying the security settings is the next step after the system has been penetrated. This allows the attacker to re-enter the compromised system more easily. Also known as privilege escalation tools, there are many programs that help accomplish this task.
4. Circulate to other systems- Once the network or system has been compromised, the attacker then uses it as a base to attack other networks and computers. The same tools that are used to probe for information are then directed toward other systems.
5. Paralyze networks and devices- If the attacker chooses, he or she may also work to maliciously damage the infected computer or network. This may include deleting or modifying files, stealing valuable data, crashing the computer, or performing denial of service attacks.
name me the different types of Security Principles and what each of them do?
Layering : creating a barrier of multiple defenses that can be coordinated to thrawt a variety of attacks
Limiting access to information reduces the threat against it and only those who must use data should have access
Diversity: Using diverse layers of defense means that breaching one security layer does not compromise the whole system
Obscurity: hiding what gees on inside a system or organization and avoiding clear patterns of behavior makes attacks from the outside much more difficult
Simplicity: Keeping a system simple from the inside but complex on the outside
What are the Typical weakness in a secure network design?
1) Single points of failure : a pinch point relying on a single hardware server or network channel
2) Complex dependencies: the failure of individual systems or services that shouldn't affect the overall performance of other network services
3) Availability over confidentiality and integrity: often tempting to take shortcuts to get a service up and running and compromising security might represent a quick fix but create a long term risks
4) Lack of documentation and change control: network segments and services might be added without proper change control procedures , leading to lack of visibility into how the network is constituted
5) If the network architecture is "flat" (that is, if any host can contact any other host), penetrating the network edge gives the attacker freedom of movement.
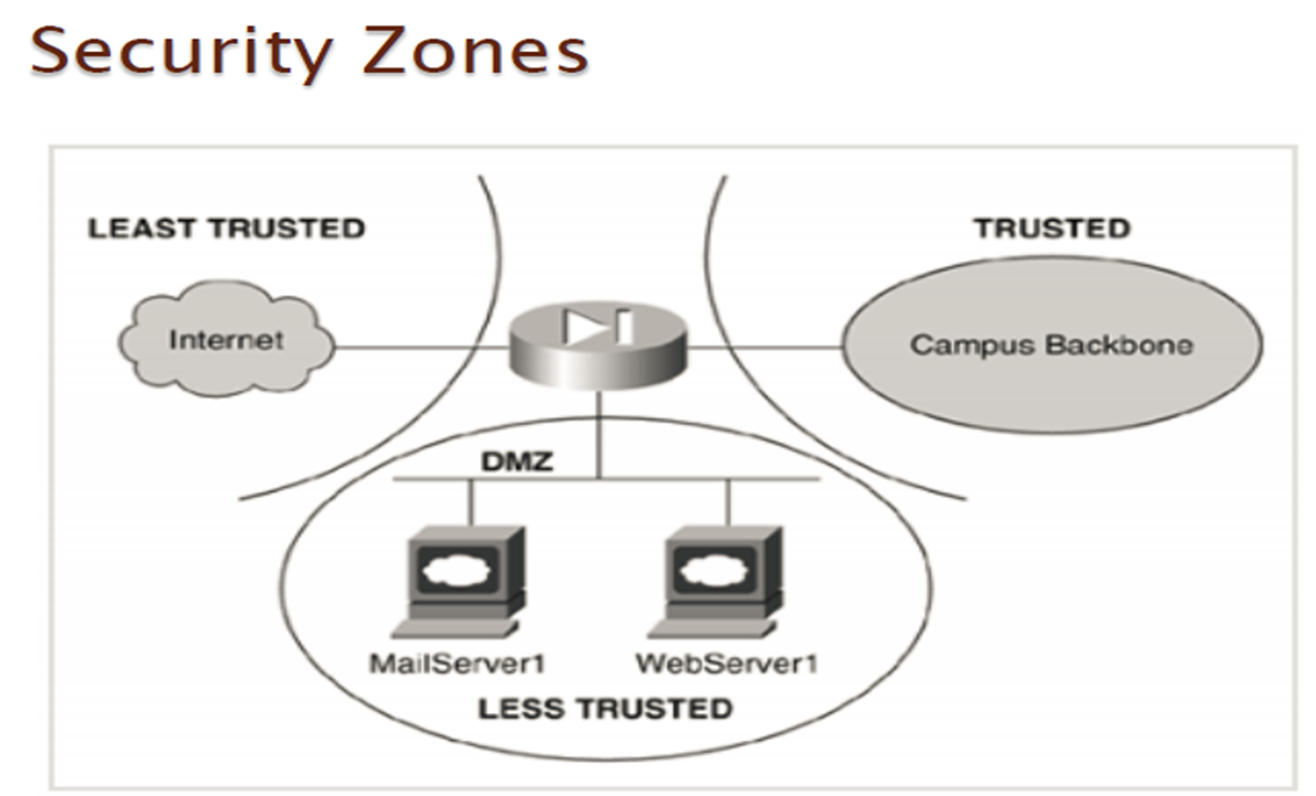
What are the Security Zones ?
CH2:
What are the 2 broad categories of network vulnerabilities?
Those based on the network transport media
Those found in the network devices themselves
Explain what is Network transport media based vulnerabilities
Its when you’re monitoring network traffic which can be done in two ways:
Port mirroring
Network Tap
What is Port mirroring?
is a network feature that allows the traffic passing through a specific network port to be copied and sent to another port for analysis or monitoring purposes. It is commonly used for network troubleshooting, security monitoring, and performance analysis.
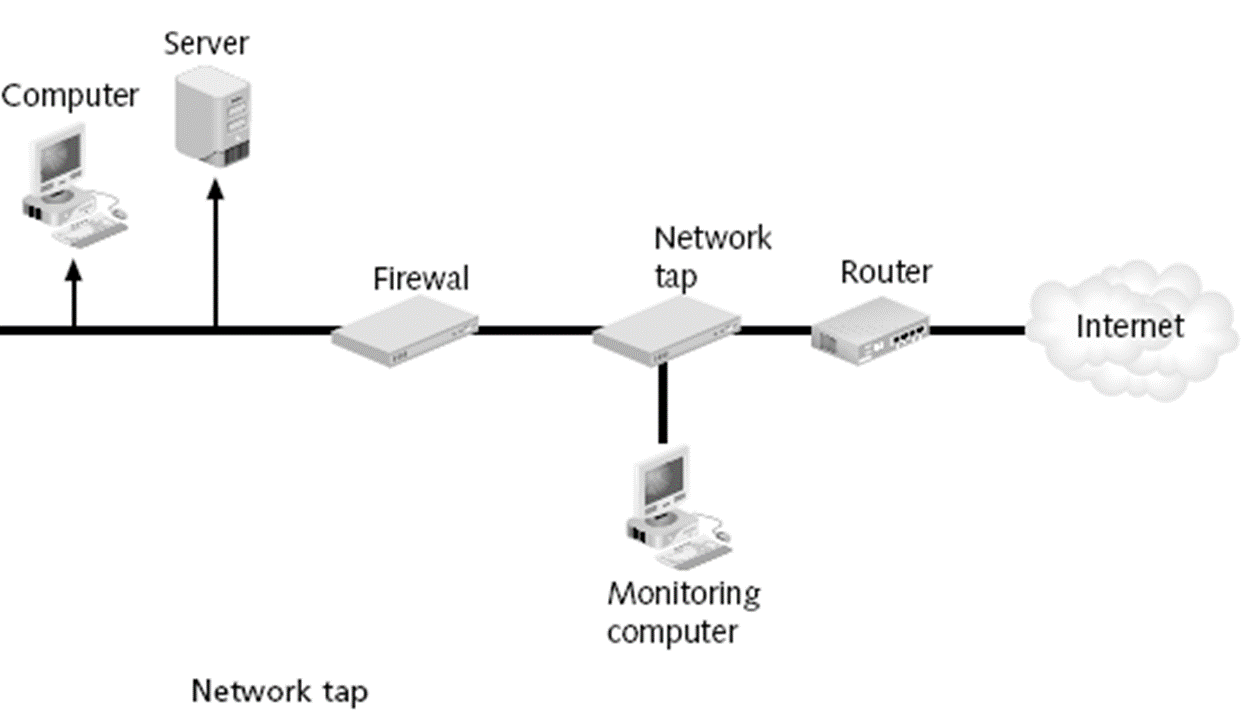
what is network tap
Explain what is Network Tap?
is a second method for monitoring traffic is to install a network tap. and its a separate device that can be installed between two network devices, such as a switch, router, or firewall, to monitor traffic.
What are Network Device Vulnerabilities?
Weaknesses in network devices themselves can also be targets for attackers. Common network device vulnerabilities include:
Weak passwords
Default accounts
Back doors, and Privilege escalation.
Weak passwords:
If a device is protected by a weak password, it can be vulnerable to many password-based attacks
Default accounts
User account on a device that is created automatically by the device instead of by an admin
Back Door:
An account that is secretly setup without admins knowledge or permission that cannot be easily detected and allows remote device access to the device
Privilege escalation:
Operating system, many applications, & network devices can be victims of privilege escalation .
What are two Types of Network Threats?
Active attack : in which unauthorized change of the system is attempted
Passive attack : characterized by the interception of messages without modification
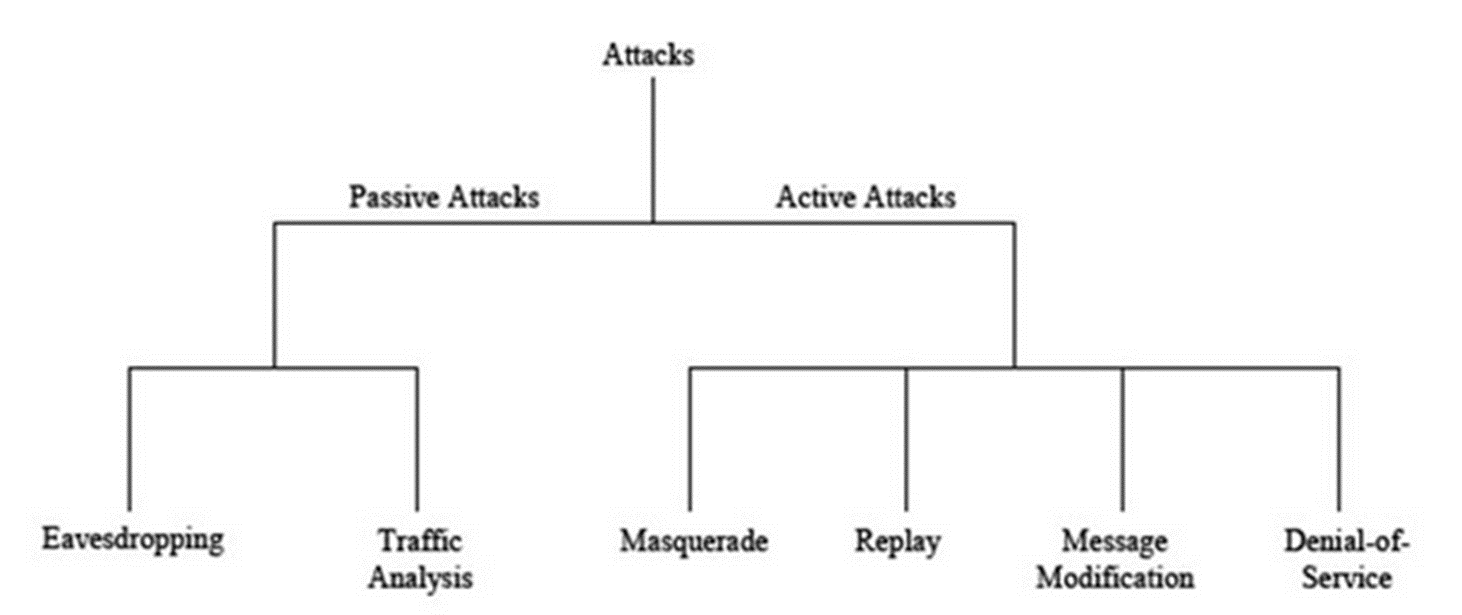
What are the categories of attacks?
¨There are different categories of attacks that are conducted against networks. These categories include:
Denial of service,
Spoofing,
Man-in-the-middle, and
Replay attacks.
Denial of service
attack attempts to consume network resources so that network or its devices cannot respond to legitimate requests
Spoofing
pretending to be someone or something else by presenting false information. Spoofing can take many forms, such as spoofed emails, IP spoofing, DNS Spoofing, GPS spoofing, website spoofing, and spoofed calls.
( being identical at everything)
Man-in-the-middle attack
attack make it seems that two computers are communicating with each other, when actually they are sending and receiving data with a computer between them ( man in the middle or sniffing)
Sniffing vs Spoofing
Spoofing and sniffing are both techniques used in computer networks, but they serve different purposes. Spoofing involves impersonating another entity or device to deceive or gain unauthorized access. It can be used to manipulate data, disguise identity, or launch attacks. On the other hand, sniffing refers to the act of intercepting and capturing network traffic to analyze or extract information. It is commonly used for network troubleshooting or monitoring purposes. In summary, spoofing is about deception and impersonation, while sniffing is about capturing and analyzing network data.
Replay Attacks
an attacker could capture the message sent from the network device to the server. Later, he could send that original message to the server and the server may respond, thinking it came from the valid device.
Possible security measures are?
Authentication
Non-repudiation
Biometrics
Cryptography
Digital Signature
PKI
Ch.3 :
Define what is Digital ID
it means of proving your identity or that you have been granted permission to access information on network devices or services
Certificate of Digital ID
a set of keys to encrypt and validate the connection. These certificates are issued by a certification authority (CA) and are signed with the CA's private key. The role of the CA is to guarantee the identity of each party participating in the transaction.
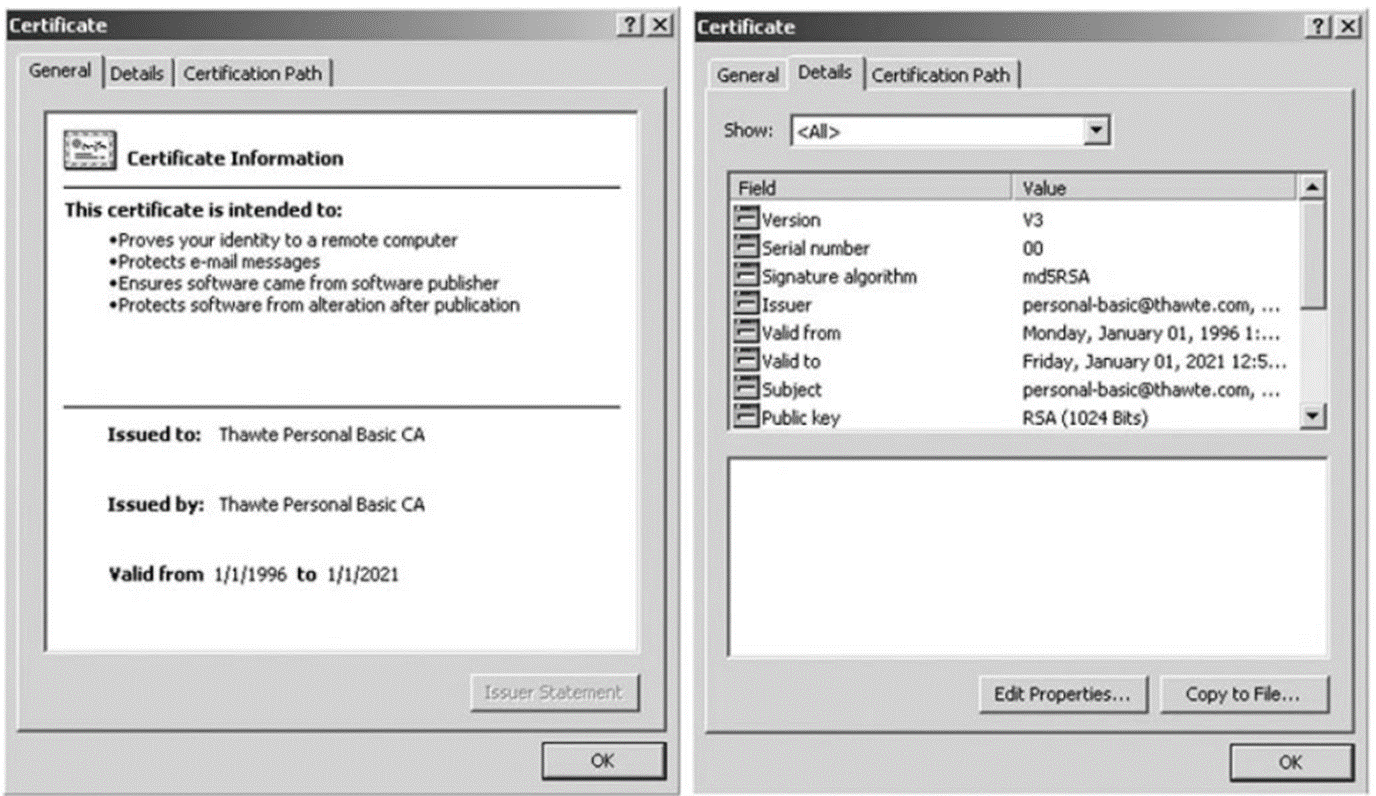
How to know if its a Secure Website?
In a website you could access the website/server certificate to know or you could see the website if its HTTPS which is secure not anyone can access tis website but if its HTTP its not secure and anybody ca access that website.
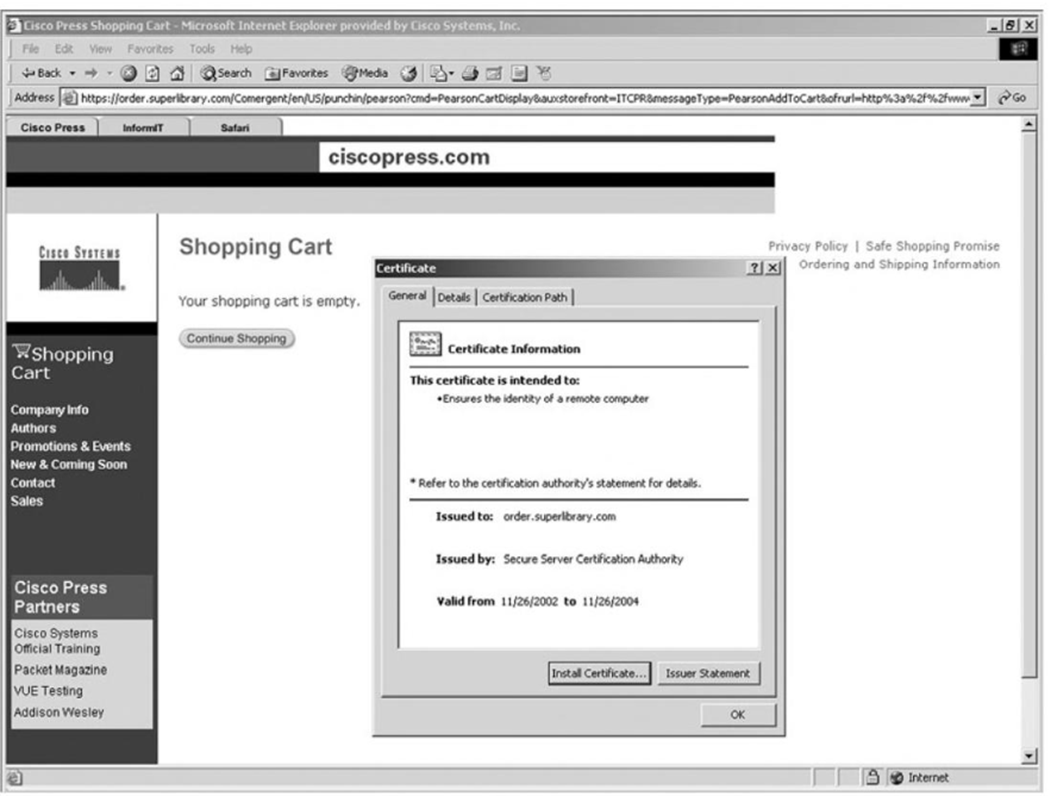
What is the Three types of Certificates available ?
Personal digital ID or personal certificate
Server digital ID or website certificate
Developers' digital ID
Software developers use developers' IDs. Internet Explorer and Netscape use only personal digital IDs and server digital IDs.
What’s the use of Personal certificate?
used for sending personal information over the Internet to a website, whereby the web server requires verification of the user's identity and most commonly used for the exchange of e-mails by individual users.
What’s the use of Website certificate?
enables and state that a specific web server is operating in a secure and authentic way. and a web server ID or certificate unambiguously identifies and authenticates the web server and guarantees the encryption of any information passed between the web server and the individual user.
What does IDS stand for?
Intrusion Detection System
What are the different components of IDS?
IDS sensors
IDS management
Misuse-Based IDS
Signature-Base IDS
Anomaly-Based IDS
IDS sensors
are software & hardware used to collect and analyze network traffic available in 2 types : 1) Network IDS 2) Host IDS
IDS Management:
Acts as the collection point for alerts and performs configuration and deployment services in the network.
Misuse-Based IDS:
relies on known patterns or signatures of known attacks. It compares network traffic or system behavior against a database of predefined attack signatures. When a match is found, it generates an alert.
Signature-Based IDS:
is highly effective at detecting well-known threats. However, it may struggle with "zero-day attacks," which are attacks that exploit vulnerabilities for which no known signature exists. Zero-day attacks can go undetected until a signature is created.
Anomaly-Based IDS:
Takes a different approach and it establishes a baseline of normal network or system behavior. It then flags deviations from this baseline as potential threats. Its particularly useful for detecting novel attacks or zero-day threats. However , one drawback is that it can generate higher rate of FP
What is Confusion Matrix performance?
True Positive ( correctly identifies an actual intrusion or malicious activity)
False Positive ( not dangerous false alarm)
True Negative ( identifies no intrusion or malicious activity present)
False Negative ( most negative , and IDS fails to detect an actual intrusion or malicious activity. This is a critical error b/c it means a security threat went undetected)
Explain Physical Security? how do we use it?
its the use of blueprints, standards, or models to protect networks and involves the identification and description of all the measures required to protect your facility.
Outside & External Security
When implementing physical security at a company level, the first consideration is the location of your site you need :
Electronic fence
Electromagnetic IDs
Camera systems
Entrance security (smart cards, PIN code)
Permanent guards
Internal Security
implementing internal physical security is similar to the approach to implementing external physical security . Camera systems can be installed all over a campus, with priority given to the entrances to mission-critical areas such as lab space, communication rooms, and server rooms.
Disaster-Recovery Plans
measures that limit losses that can be incurred by disaster such as hurricanes , floods, & electrical failure .
3 level disaster recovery plans are :
Hot Site : expensive type of data replication routine
Warm Site : data replication routine occur for once every 24hr to once a week
Cold Site: most cost effective b/c companies do not have to purchases duplicate machines
Encrypted Login
process of securely verifying the identity of a user attempting to access a system, service, or application
Kerberos Encrypted Login Sessions
provides an alternative approach to SSH-encrypted login, whereby a trusted third-party authentication mechanism verifies the identity of the users.
Secure Socket Layer : Difference Btwn HTTP & HTTPS
The main difference between HTTP and HTTPS is the presence of an SSL/TLS certificate in HTTPS. This certificate encrypts the data transmitted between the web server and the user's browser, ensuring secure communication. In contrast, HTTP does not provide encryption, making it vulnerable to eavesdropping and data tampering. Therefore, HTTPS is used for secure transactions, such as online banking or shopping, where data confidentiality is crucial
Firewalls
device that separates different functional areas of a network
CH.4:
Define Network Protocols
a set of rules and conventions that define how data should be formatted, transmitted, and received in computer networks.
Explain what is Role in Data Communications?
Creating a secure way to communicate and ensure that data is transmitted reliably
What is the Importance of Protocol Security?
ensures the confidentiality, integrity, and authenticity of data during network communication and by encrypting data it thwarts eavesdroppers and deters man in the middle attacks. It contributes to business continuity by minimizing the risk of breachers and disruptions, ensuring uninterrupted operations
Name the common protocol Based attacks
Eavesdropping or Sniffing Attacks.
Man-in-the-Middle (MitM) Attacks.
ARP Spoofing or Poisoning.
DNS Spoofing.
Denial of Service (DoS) Attacks - TCP/UDP-based DoS attack
SQL Injection.
SMTP Relay Attacks.
HTTP Request Smuggling.
Cross-site scripting (XSS).
Cross-Site Request Forgery (CSRF).
LDAP Injection.
What is DNS Spoofing attack?
Type of Cyberattack that manipulates the domain anme system (DNS) to redirect users to malicous websites or intercept their network traffic. Which is why DNS is responsible for translating user friendly domain names to ip address that computers can use to locate web servers on the internet
How does DNS Spoofing attack work?
1. Target Selection
2. DNS Cache Poisoning
3. Victim Queries
4. Redirection or Data Capture
Explain what is Mitigate DNS Spoofing Attack?
to protect against DNS Spoofing attacks , they are essential to implement security measures such as :
DNSSEC
DNS Caching
Use of Trusted DNS Servers
firewalls and IDS
Regular updates and patching
Define TCP/UDP-Based DoS Attack
Attacks targeting both TCP(transmission control protocol) and UDP(User Datagram protocol) which can disrupt network services and make resources unavailable to legitimate users
What is the 3 way handshake?
is a TCP/IP network connection mechanism that connects the server and client. Before the real data communication process begins, both the client and server must exchange synchronization and acknowledgment packets.
How is the 3 way Handshake designed?
mechanism is designed to allow both communicating ends to initiate and negotiate the network TCP socket connection parameters at the same time before data is transmitted. It allows you to transfer numerous TCP socket connections in both directions simultaneously.
Explain the TCP 3-way Handshake process?
process is used for establishing and terminating the connection between the client and server.
(further explanation is from your own understanding)
Define TCP SYN Flood Attack
A type of DDoS attack that exploits the TCP 3 way Handshake to consume resources in the targeted server and render it unresponsive . It Becomes TCP SYN Flood b/c of how the offenders sends TCP connection requests faster that the targeted machine can process them , causing network saturation
Tell me what are the common techniques of Mitigating SYN Flood Attack?
number of common techniques to mitigate SYN flood attacks, including:
1.Micro Blocks: micro records in the server memory for each incoming SYN requests instead off a complete connection object
2.SYN Cookies: Using Cryptographic hashing
3. RST Cookies : For the first request from given client, the server intentionally sends an invalid SYN-ACK
4.Strack Twerking: Administrators can twerk TCP Stacks if Mitigate the effect of SYN Floods
What are the 3 Types of UDP-Based Dos Attacks?
UDP Flood Attack : ¤flood a target server with a massive number of UDP packets , and UDP is connectionless and doesn't require a handshake
DNS Amplification Attack: Exploit vulnerable open DNS resolvers by sending small DNS query requests with a forged source IP address and the server responds with a much larger DNS response to the victim's address, amplifying the attack.
NTP Amplification Attack: UDP Fragmentation Attack: When attackers send fragmented UDP packets to a target exploiting the servers needs to reassemble these fragments
mention the 11 different types of Mitigating UDP-Based DoS attacks?
1.Firewalls and IDS/IPS.
2.Rate Limiting and Traffic Shaping:
3.Access Control Lists (ACLs)
4.Content Delivery Networks (CDNs).
5.Anti-Spoofing Measures.
6.Monitoring and Anomaly Detection.
7.Load Balancers and Redundancy.
8.DNS Security Extensions (DNSSEC).
9.Application-Layer Protection.
10.Regular Patching and Updates.
11.Incident Response Plan
What is SQL injection?
is a code-based vulnerability that allows an attacker to read and access sensitive data from the database.
Types of SQL Injection
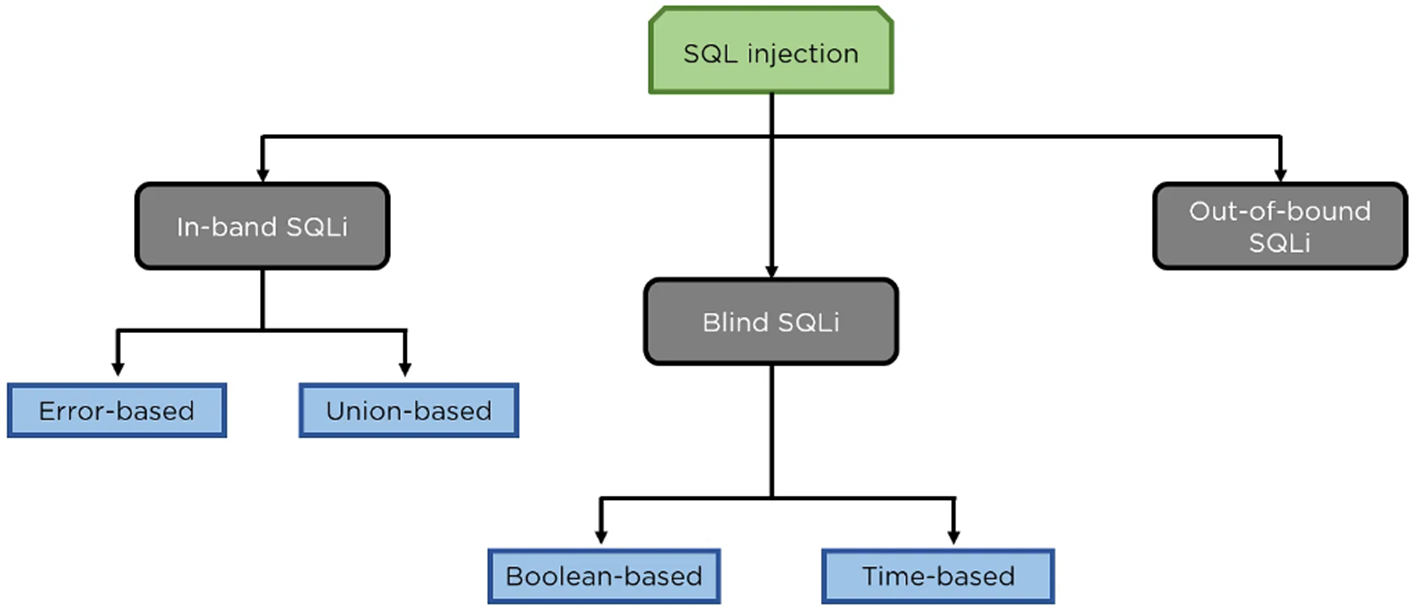
How do you Prevent SQL Injection from happening?
Use prepared statments and parameterized queries such as : Object relational mapping and Escaping inputs
there are other measures such as :
¤ Password hashing
Third-party authentication
Web application firewall
Purchase better software
Always update and use patches
Continuously monitor SQL statements and database
CH.7:
What’s a Basic Router Configuration?
its to perform basic router config tasks , accessing via a console port is required and its labeled as CON/AUX → in cisco router router 819 series + console in cisco 1841 router

How do you Connect Laptop to Router Console Port:
you must have one or a combination of these cables to do this and you take a RJ-45 console cable that’s for windows type computer or take a USB o serial DB-9 adapter if only your laptop does not have a serial port or a RJ-45 console cable to USB , and a USB-C to RJ-45 console cable for newer laptops
How to Locate the correct COM port?
your right click on windows start icon and select “Device Manager” and open “Ports(COM &LPT)” section and locate which COM port is using
How do we open a Console Session?
By using “PuTTY or other terminal emulator , select “Serial” as the connection type and change the “Serial Line” to match the COM port noted earlier . The serial console speed is typically 9600 . Then click “Open” to connect to the console
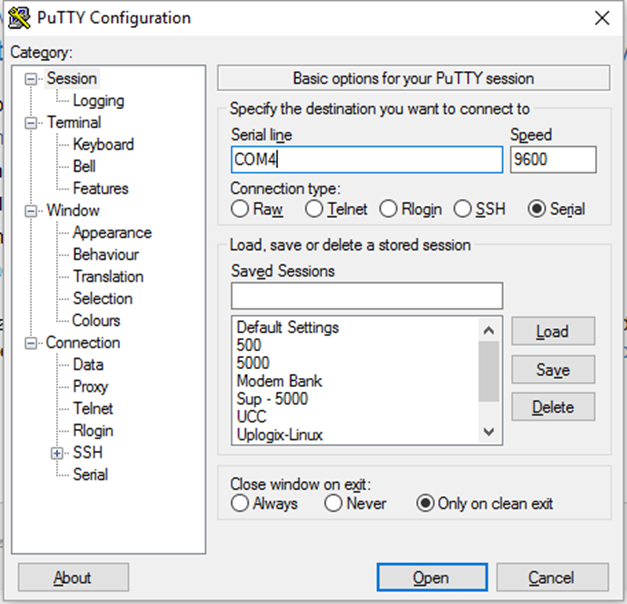
How do you Enable a Password and what does it do ?
so to configure a password we write ( enable password) and write the password in a network device it wont be that secure
How do you Enable Secret and what does it do?
following the command enables secret password of pw1 → enable secret pw1
and by doing so its encrypting a password and it skips users into making the passwords that way it’ll be more secure than enable password
Difference btwn Enable password vs Enable secret
difference between enable password and enable secret
The main difference between an "enable password" and an "enable secret" is the level of security they provide. The enable password is a legacy method that stores the password in plain text, making it less secure. On the other hand, the enable secret uses encryption with a cryptographic hash function, making it a more secure option for protecting privileged access on Cisco devices. In summary, the enable secret provides stronger security by encrypting the password, while the enable password is less secure as it is stored in plain text.
What is VTY?
short for Virtual Terminal lines and are used for accessing the router remotely through telnet by using these virtual router interfaces.
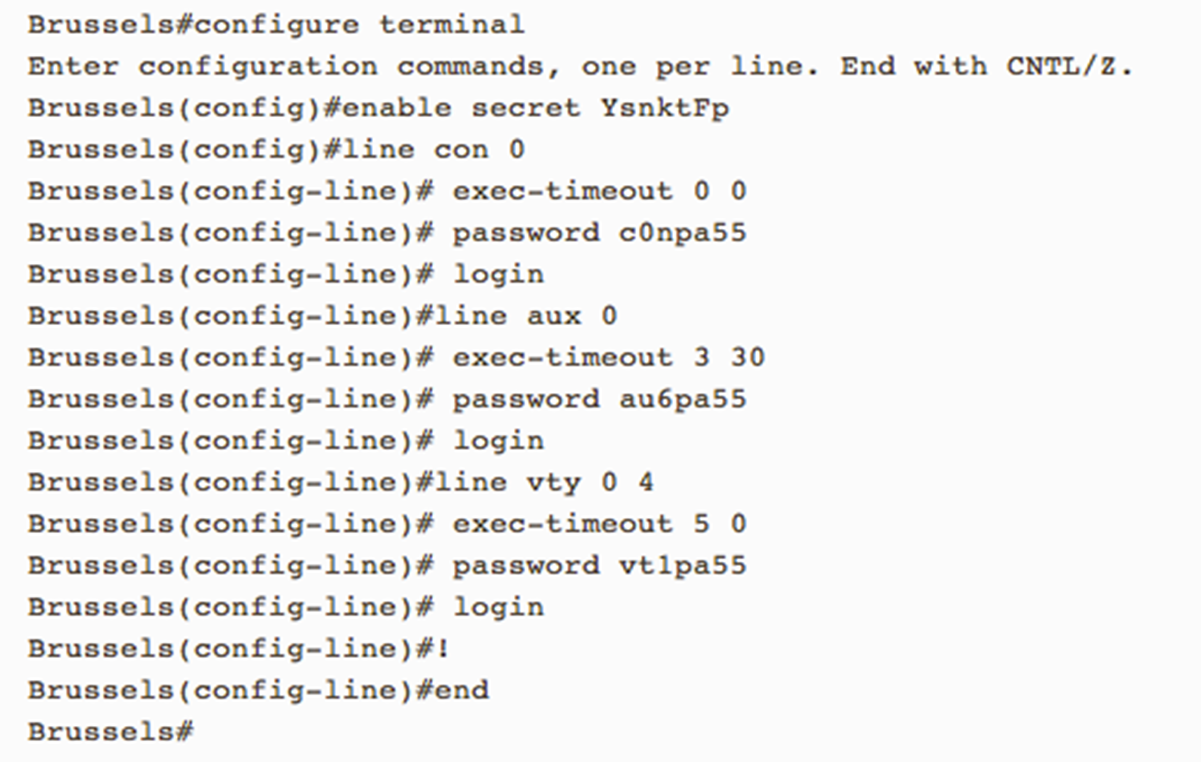
how to configure of all passwords
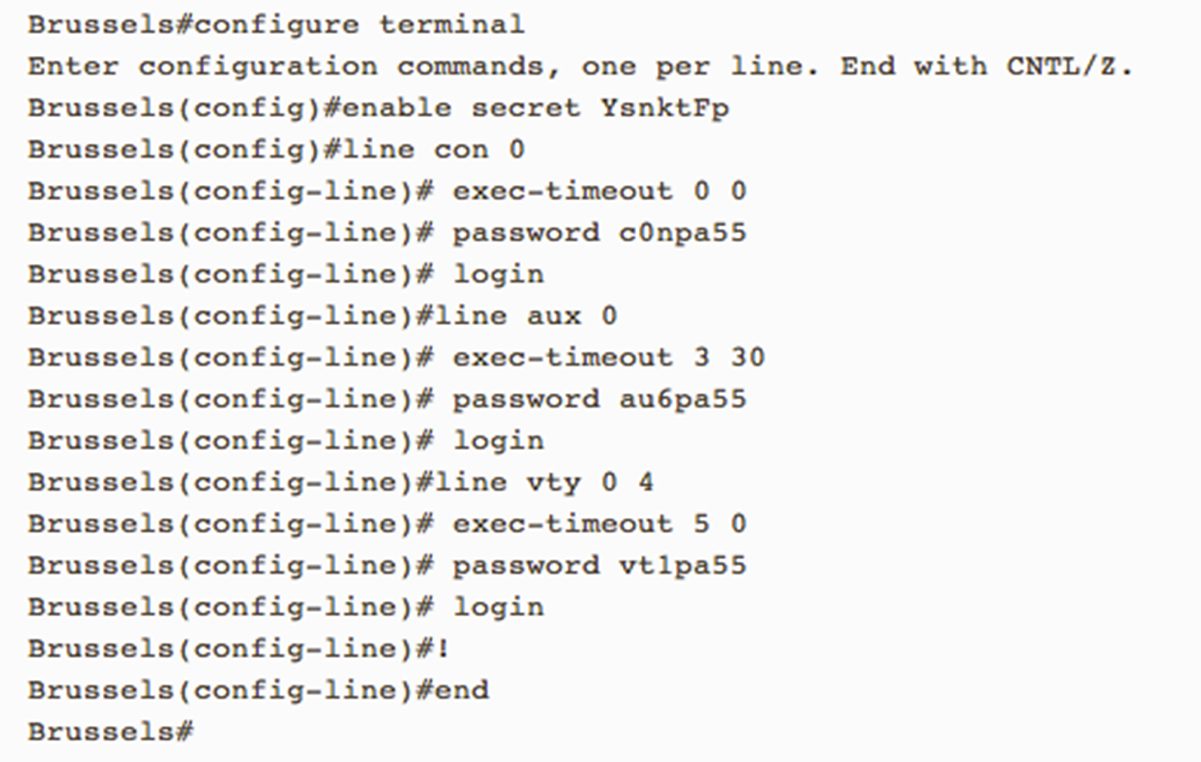
How to enable password encryption on the Router?
When password encryption is enabled, the encrypted form of the passwords is displayed when a more [system:running-config] command is entered. This requires passwords to be encrypted in the configuration file to prevent unauthorized users from learning the passwords just by reading the configuration. When not enabled, many of the device's passwords will be rendered in plain text in the configuration file. This service ensures passwords are rendered as encrypted strings preventing an attacker from easily determining the configured value.
what to do Configure Banner in Cisco devices do?
refers to setting up banner messages that are displayed to users when they access the device via a terminal session, console port or other means of remote access and are typically used for legal , security, or informational purposes served to notify users , security warning , policy communication
Why Disable Unwanted Services?
by Disabling services that may or may not be required certain networks & network security could greatly improve by turning them off or at least restricting access to them like:
Cisco Discovery Protocol(CDP) → no cdp run | no cdp enable
HTTP server → no ip http server
BOOTP server → no ip bootp server
IP redirect → no ip redirects
DNS lookups → no ip domain-lookup