L16 - T16A - S6 - Password Attacks
1/9
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
10 Terms
Password Attack
Any attack where the attacker tries to gain unauthorized access to and use of passwords – (A+)
Plaintext Password weakness
A [partial answer/clue] can be captured by obtaining a password file or by sniffing unencrypted traffic on the network.
If the protocol does not use encryption, then the threat actor can simply read the password string from the captured frames
Password
Typically stored and transmitted securely by making a cryptographic hash of the string entered by the user
Cryptographic Hash
Produces a fixed-length string from a variable-length string using a one-way function
In theory, no one except the user (not even the system administrator) knows the password, because the plaintext should not be recoverable from the [answer]
True
This is not the same as cryptographic hashing.
The password value can easily be derived from the Base64 string
True or False: A password might be sent in an encoded form, such as Base64, which is simply an ASCII representation of binary data
Common password hash files and databases
%SystemRoot%\System32\config\SAM%SystemRoot%\NTDS\NTDS.DIT(the Active Directory credential store)/etc/shadow
False
This is definitely a possibility
True or False: A threat actor cannot use an on-path attack to capture a password hash transmitted during user authentication
Password-cracking software
Software which can be used to try to identify the password from the cryptographic hash
Uses 2 basic techniques
Dictionary
The software matches the hash to those produced by ordinary words found in a dictionary
Brute Force
Software tries to match the hash against one of every possible combination it could be
Dictionary Technique (password cracking software)
Type of password attack that compares encrypted passwords against a predetermined list of possible password values – (A+)
The software matches the hash to those produced by ordinary words found in a [answer]
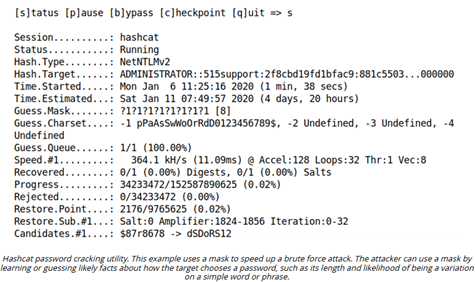
Brute Force Technique (password cracking software)
Type of password attack where an attacker uses an application to exhaustively try every possible alphanumeric combination to crack encrypted passwords – (A+)
A password might be cracked in minutes if
The password is short (under eight characters)
Noncomplex (using only lower-case letters, for instance),