4.5 Email Security
1/8
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
9 Terms
Email Security Challenges
Email protocols lack built-in security, making it easy for attackers to spoof sender addresses.
To counter this, organizations now use additional DNS-based security features that help verify whether a message truly came from an authorized source.
A message may appear to come from someone familiar, like a friend or james@professormesser.com, even if it didn’t.
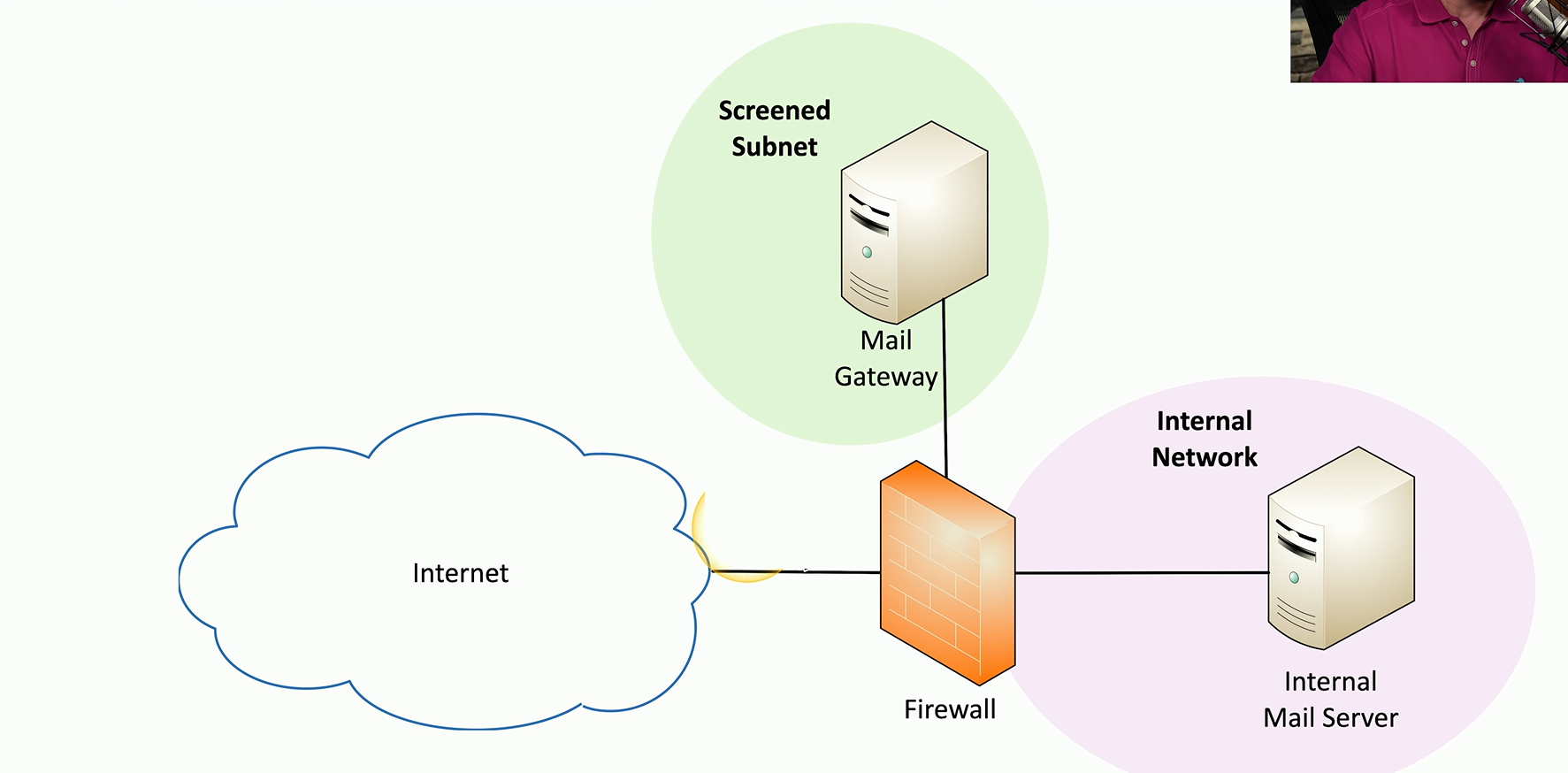
Mail Gateway
Acts as the gatekeeper for all incoming email to an organization.
Checks each message from external servers to verify legitimacy before delivering it to users' inboxes
If the message appears suspicious or invalid, it's discarded or sent to the spam folder.
Can be located on-premises, usually in a screened subnet for internet communication.
Or hosted in the cloud via third-party services.
Multiple may be used for larger environments
Sender Policy Framework (SPF)
An email validation protocol that helps prevent spoofing by specifying which mail servers are authorized to send emails on behalf of a domain.
The domain owner adds an this record as a TXT entry in their DNS.
When a recipient’s mail gateway gets an email, it checks the sender’s DNS for the this record. I
If the sending server matches an authorized server listed—like mailgun.org for professormesser.com—the message is considered valid.

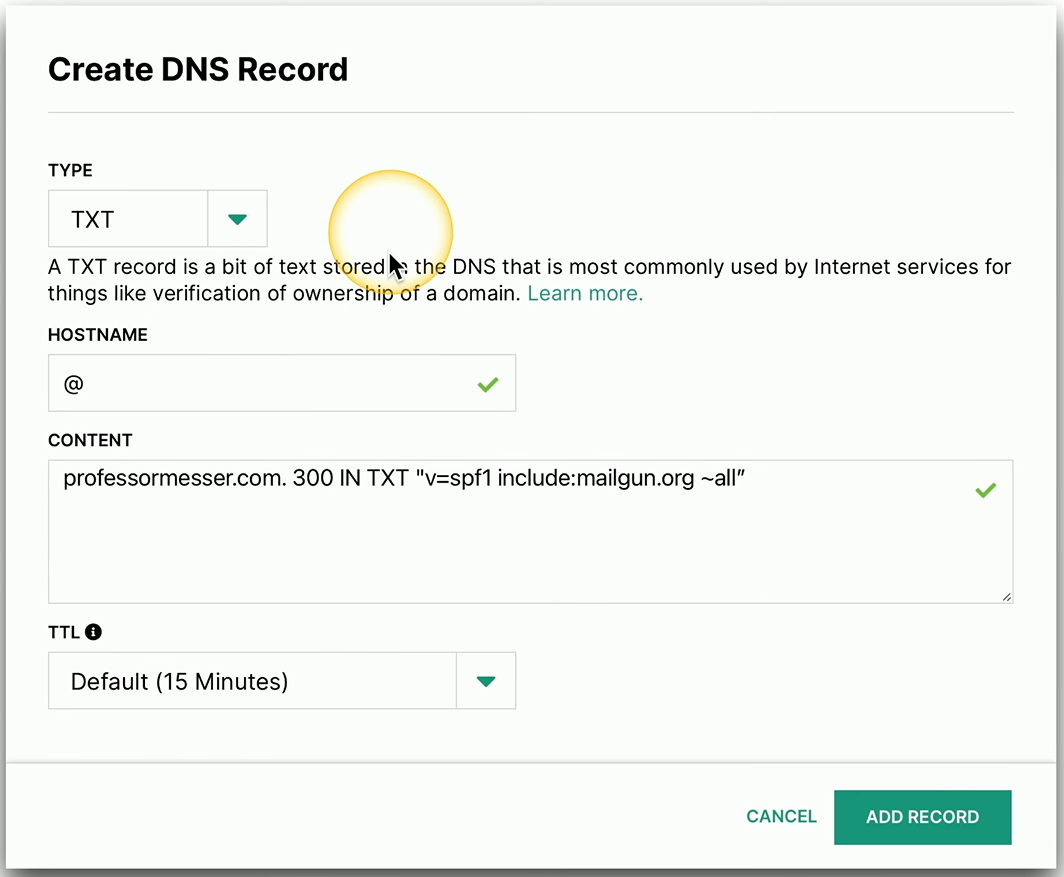
SPF TXT Example
If you have a web-based front end to your DNS, you can add this information very easily.
This is a text record that I’m adding.
This is the content of the text record that says, for professormesser.com, we’re going to include mailgun.org as one of the authorized servers.
Domain Keys Identified Mail (DKIM)
Adds a digital signature to outgoing emails to verify that the message hasn’t been altered and that it came from an authorized server.
Process happens behind the scenes during transport and is not usually visible in the email body—only in the headers.
Mail server signs each message using a private key.
The recipient’s server checks the email header for the this signature, then queries the sender’s DNS for a public key (stored as a TXT record).
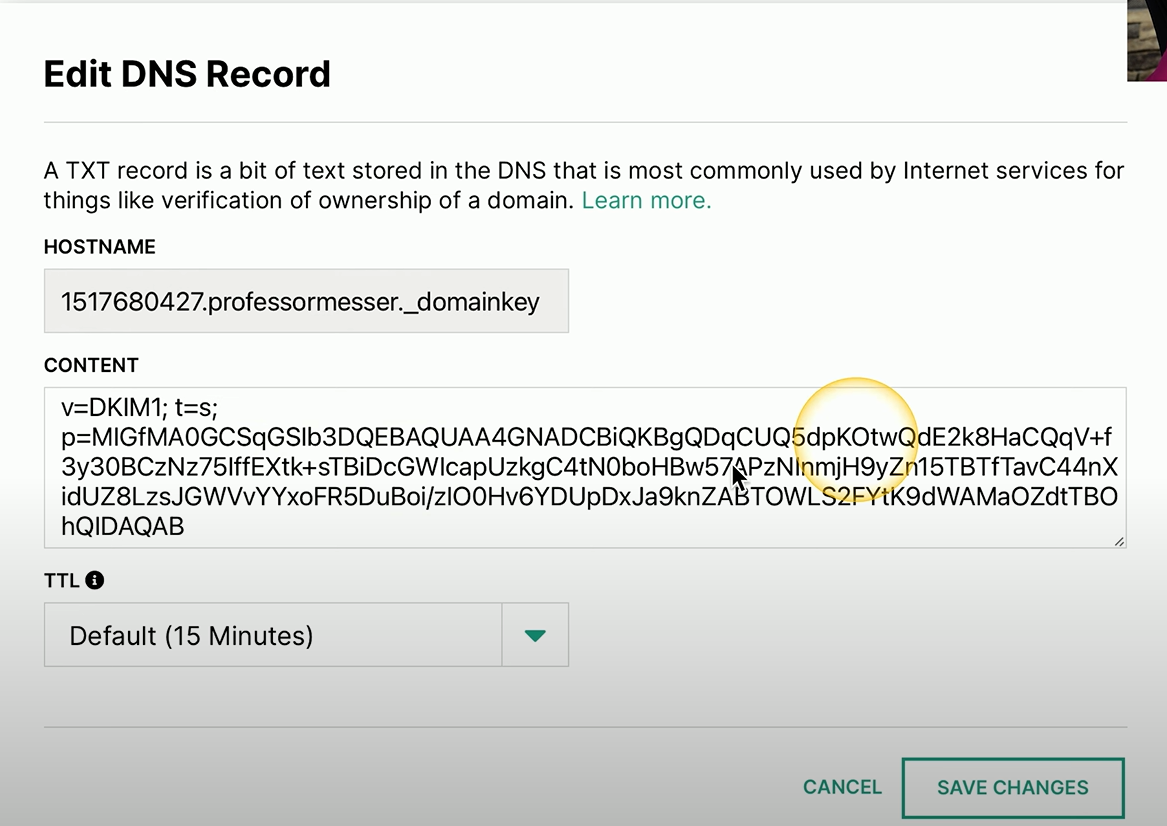
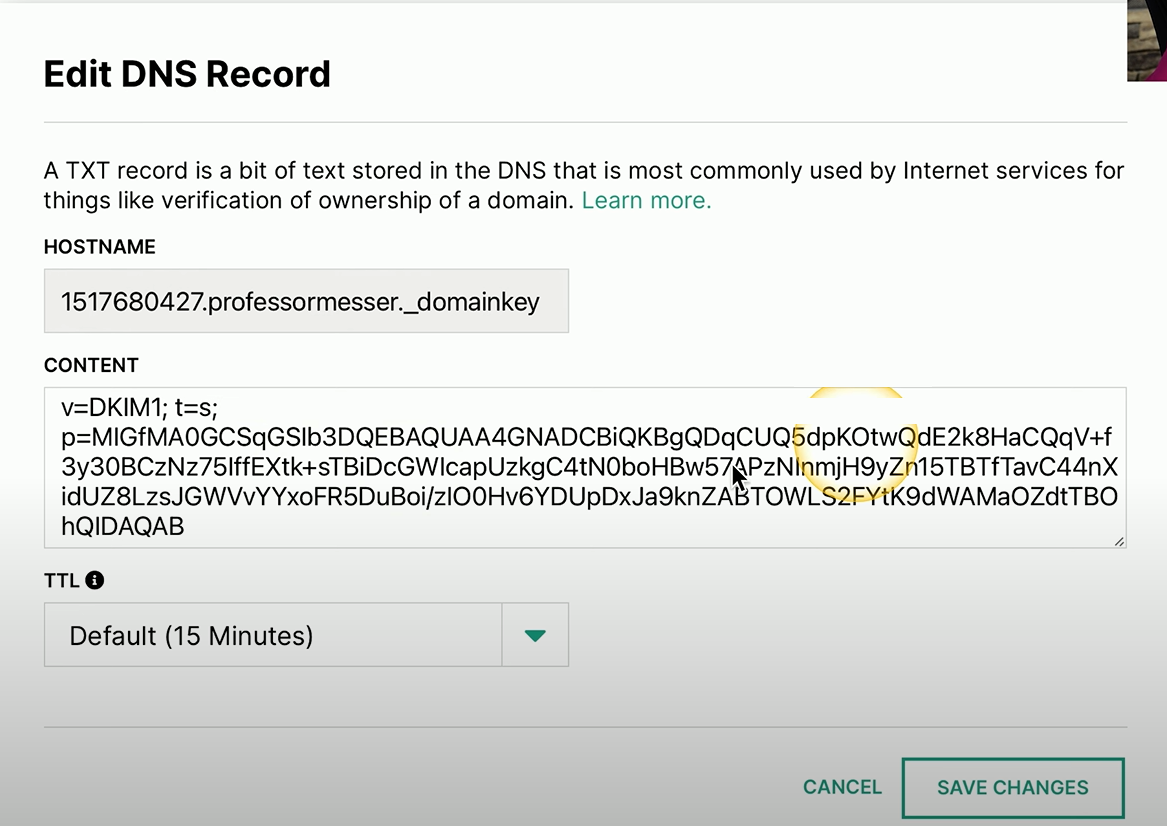
DKIM TXT Record Example
Because the DKIM information is also added to a DNS text record, it’s the same process as adding an SPF record.
You can see that we’re putting in hostname information.
There is the content, which is the public key for this record. And then we can save the changes into our DNS.
Domain-based Message Authentication, Reporting, and Conformance (DMARC)
Builds on SPF and DKIM to tell receiving mail servers what to do if an email fails authentication.
It's published as a TXT record in your DNS and gives instructions like “accept,” “quarantine,” or “reject” for failed messages.
Also includes a reporting feature so domain owners can track how many messages are passing or failing authentication, helping to detect spoofing or unauthorized email use.
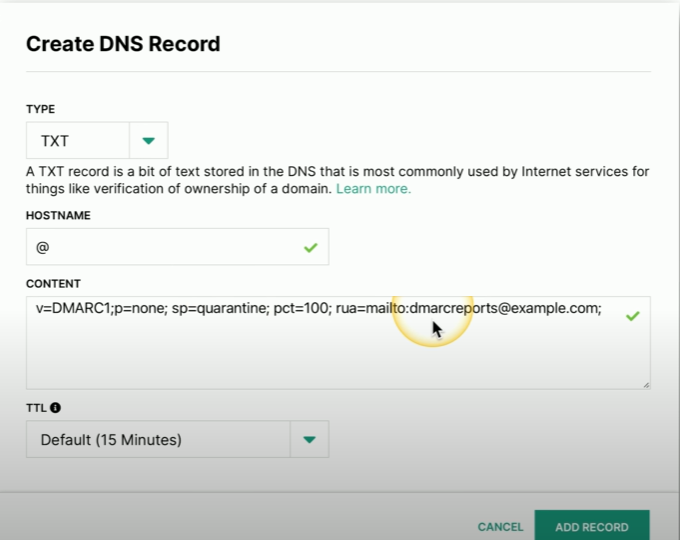
DMARC TXT Example
Here’s a DMARC record, and it is added to the DNS server as a TXT or a text record. You can see that it’s designated as DMARC1.
Set emails to be put into quarantine if they’re not properly validated
And all of the statistics surrounding the receiving of these email messages is sent to one central DMARC reporting engine.
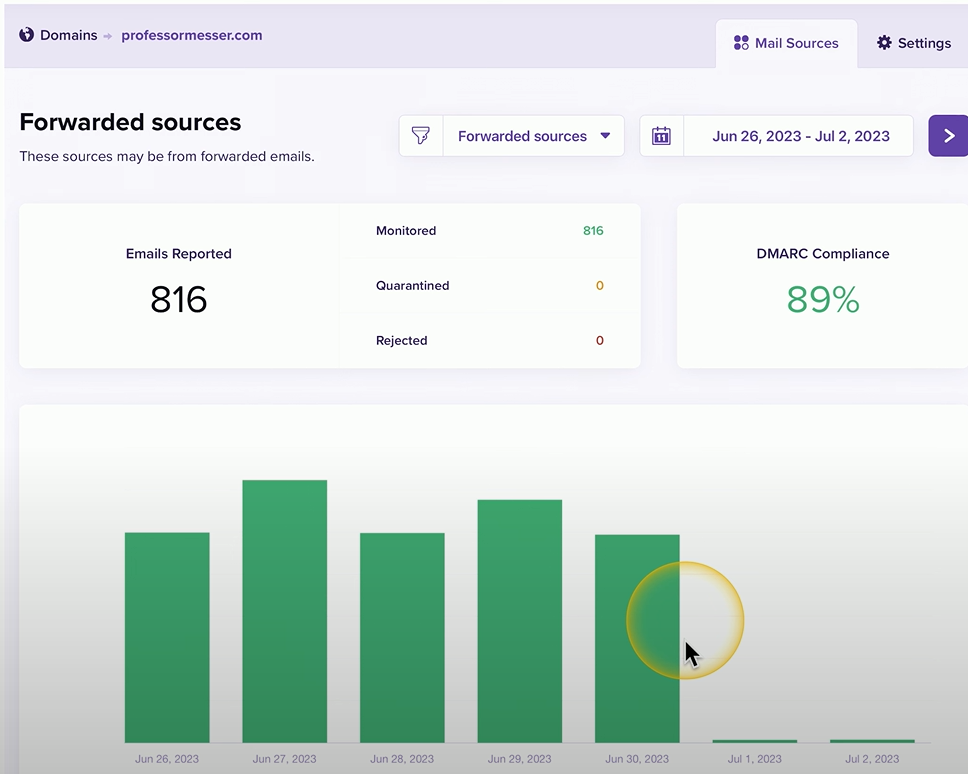
DMARC Reports
The domain owner can go to this reporting engine and get an idea of how many emails are being received properly by the end users and how many emails may be spoofed by a third party and what the disposition of those emails might be.