AP CSP Exam Terms
DNS (Domain Name System)
is a fundamental internet service that translates human-readable domain names, such as "example.com," into their corresponding IP addresses, like "192.168.0.1." This process facilitates user-friendly browsing by allowing people to easily remember and enter website names rather than numeric IP addresses.
Citizen Science
Citizen science is scientific research conducted in whole or part by distributed individuals, many of whom may not be scientists, who contribute relevant data to research using their own computing devices. “This project would benefit from using a citizen science model for gathering photographs of birds from amateur photographers around the world.”
1/67
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
68 Terms
DNS (Domain Name System)
is a fundamental internet service that translates human-readable domain names, such as "example.com," into their corresponding IP addresses, like "192.168.0.1." This process facilitates user-friendly browsing by allowing people to easily remember and enter website names rather than numeric IP addresses.
Citizen Science
Citizen science is scientific research conducted in whole or part by distributed individuals, many of whom may not be scientists, who contribute relevant data to research using their own computing devices. “This project would benefit from using a citizen science model for gathering photographs of birds from amateur photographers around the world.”
Internet Engineering Task Force
an open standards organization, which develops and promotes voluntary Internet standards, in particular the standards that comprise the Internet protocol suite. It has no formal membership roster or membership requirements
Digital Divide
the gulf between those who have ready access to computers and the internet, and those who do not. (Low income, rural areas, disabled people all have less access)
Creative Commons License
Creative Commons licenses can be used by creators of digital music to specify how the samples can be used by others. A no-rights-reserved license allows others to freely make use of the samples.
Floating point imprecision
stems from the problem of trying to store values less than 1 like 1/10 or (. 10) in a computer with a binary number system with a finite amount of numbers.
Open Protocol
An open (nonproprietary) protocol is one that is not owned by any particular company and not limited to a particular company's products. The protocols in the Internet stack are open so that any computing device can follow the protocol to join the global network.
Reasonable Run Time
If n represents the size of the data that you are dealing with, anything less than n^n or n! is considered reasonable run time. So, for example linear search (checking every single item in a list to find something) is considered n run time because the maximum or worst case number of steps required would be n or checking every single element in the list. n^2 is considered reasonable. As is n^6, etc… For our purposes, I think you can consider anything less than n^n as reasonable run time…
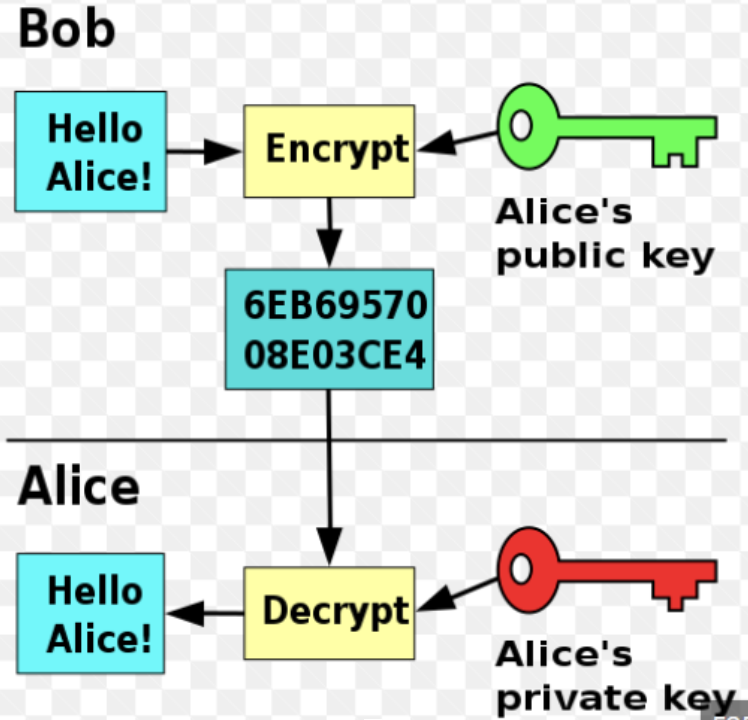
Public Key/Private Key
Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys (which may be known to others), and private keys (which may never be known by any except the owner). The generation of such key pairs depends on cryptographic algorithms which are based on mathematical problems termed one-way functions. Effective security requires keeping the private key private; the public key can be openly distributed without compromising security.
Symmetric encryption
uses a single key for both encryption and decryption of data. Since the key can be used to unlock the data, it should be kept secret.
Linear Search v. Binary Search
Linear search is checking every single item in a list or data structure to find something. The items do not have to be sorted. Binary Search is when you have a SORTED list and you check the middle to see if the value is there, then make another guess depending on whether the value you are looking for is higher or lower than that value. Binary Search is considered to have a log(n) run time which is better than the n run time of linear search, BUT you do have to SORT the elements in the list first to run a binary search…
Symmetric Key Cryptography
also known as Symmetric Encryption is when a secret key is leveraged for both encryption and decryption functions. This method is the opposite of Asymmetric Encryption (Public Key/Private Key) where one key is used to encrypt and another is used to decrypt. (The Caesar cipher is an example of symmetric encryption)
Machine learning
is the study of computer algorithms that improve automatically through experience and by the use of data. It is seen as a part of artificial intelligence. (It would involve computers making better and better predictions of outcomes based on data, algorithms, etc..>)
Crowdsourcing
the practice of obtaining information or input into a task or project by enlisting the services of a large number of people, either paid or unpaid, typically via the internet.
Abstraction
Hiding or suppressing detail. The MORE detail which is suppressed the HIGHER LEVEL of abstraction. In the case of Animal - Person - Student - You. Animal is the highest level of abstraction and You are the lowest level… (In coding, we often use functions/procedures to achieve abstraction in our programs. Among other things, it helps to make the program more readable…)
Cloud Computing
the practice of using a network of remote servers hosted on the internet to store, manage, and process data, rather than a local server or a personal computer. (ie, storing documents on Google Drive, etc…)
Turing Complete
Turing Complete refers to the ability of a computer or system to run any algorithm or solve any computational problem, provided it is given the necessary instructions, time, and memory. Most modern programming languages are Turing Complete, such as C++, Python, and JavaScript.
Phishing
An email attack where the attackers are trying to access private/sensitive information… Phishing is a technique that attempts to trick a user into providing personal information. (Apparently it doesn't have to be an email attack, but it is typically used in this context…)
DDOS (Dedicated Denial of Service) Attack
this means that hackers have attempted to make a website or computer unavailable by flooding or crashing the website with too much traffic.
A rogue access point
is a wireless access point that gives unauthorized access to secure networks. Data sent over public networks can be intercepted, analyzed, and modified. One way that this can happen is through a rogue access point.
Internet Packets (TCP)
Data transmitted on the Internet is broken into packets and then reassembled upon arrival. Packets may travel along different paths, arriving at the destination in order, out of order, or not at all (the server will send a request for the missing packets).
heuristic approach
a problem-solving technique that uses practical methods, shortcuts, or educated guesses to find approximate solutions to complex problems more efficiently. While not always providing an optimal or exact solution, heuristic strategies prioritize speed and simplicity, making them suitable for tackling problems where a timely, reasonably accurate solution is preferred over an exhaustive search for the perfect answer. In computer science, heuristics are commonly used in areas such as artificial intelligence, optimization algorithms, and search algorithms, where quick decision-making or resource allocation is crucial.
(Audio) Analog signals
sampled digitally at discrete intervals over time. These samples, like all digital data, are represented at the lowest level as a sequence of bits
The Internet and The World Wide Web
the global system of interconnected computer networks that uses open protocols to connect devices worldwide. The World Wide Web is an information system (of pages, programs, and files) that is accessible over the Internet.
bandwidth
a computer network is the maximum amount of data that can be sent in a fixed amount of time. With limited bandwidth, guest users will be restricted in the amount of data transmitted per second. Bandwidth is the amount of data that can be transferred over a period of time (usually one second). If you think about your internet connection as a water pipe, bandwidth is all the water that can travel through the pipe in a second. The bigger the pipe is, the more water that can be transferred over a set period of time. Typically, internet bandwidth is measured in megabytes per second, or Mbps. In general, high bandwidth means faster internet, as less time is needed for all the data to be transferred.
Latency or ping
the time between you sending a request for data (like opening a web page), and that data getting back to you (that page starts to load on your browser). Again, think of your internet connection as a water pipe, and also think of your computer or phone as a hose connected to that water pipe. Latency would be the time it takes for you to start seeing water come out of that hose after you turn the water on. Unlike bandwidth, with latency, you’re looking for the smallest number possible. Latency is usually measured in milliseconds.
Parallel computing
a type of computation in which many calculations or processes are carried out simultaneously. Large problems can often be divided into smaller ones, which can then be solved at the same time. There are several different forms of parallel computing: bit-level, instruction-level, data, and task parallelism. The efficiency of a parallel computing solution is limited by the sequential portion of the solution. If each step is dependent on the preceding step, then each step must wait for the previous step to complete before executing. Therefore, if the solution is completely sequential it does not benefit from parallel computing.
Keylogging
Keylogging is the use of a program to record every keystroke made by a computer to gain fraudulent access to passwords and other confidential information.
algorithm
a step-by-step, structured set of instructions or procedures designed to solve a specific problem or accomplish a task. In computer science, algorithms serve as the foundation for programming, as they outline how a computer should process data and perform calculations to reach a desired outcome.
Bit
shorthand for binary digit and is either 0 or 1 (smallest piece of memory in a computer) 4 bits can store 16 values (0-15). If you tried storing a larger value it would cause an overflow error.
byte
A byte is 8 bits. Max value is 255.
Abstraction
the process of reducing complexity by focusing on the main idea. By hiding details irrelevant to the question at hand and bringing together related and useful details, abstraction reduces complexity and allows one to focus on the idea.
Data compression
can reduce the size (number of bits) transmitted or stored data.
Lossless
Lossless data compression algorithms can usually reduce the number of bits stored or transmitted while guaranteeing the complete reconstruction of the original data.
Lossy
data compression algorithms can significantly reduce the number of bits stored or transmitted but only allow reconstruction of an approximation of the original data.
Metadata
Metadata are data about data. For example, the piece of data may be an image, while metadata may include the date of creation or the file size image. For example, the author and publisher of a book.
Cleaning data
a process that makes the data uniform without changing their meaning. (e.g., replacing all equivalent abbreviations, spellings, and capitalizations with the same word.)
computing system
a group of computing devices and programs working together for a common purpose
computer network
a group of interconnected computing devices capable of sending and receiving data. (A computer network is a type of computer system.)
Path
A sequence of directly connected computing devices from a sender to a receiver is a path
Routing
Routing is the process of finding a path from sender to receiver.
Bandwidth
Bandwidth of a computer network is the maximum amount of data that can be sent in a given amount of time. (Usually measured in bits per second or bps)
Protocol
Protocol is an agreed set of rules that specify the behavior of a system. (Internet protocols are open, IP, TCP, and UDP are common protocols used on the Internet.)
Scalability
Scalability is the capacity of a system to change in size and scale to meet demands.
Packets
Packets are small amounts of data sent over the Internet. They contain data and metadata including the sources and destinations of as well as data needed for reassembly.
World Wide Web
System of linked pages, programs, and files. HTTP is a protocol used by the WWW. WWW uses the Internet.
Sequential Computing
Sequential Computing is a computational model in which operations are performed in order one at a time. (Time takes as long as the sum of all its steps)
Parallel Computing
Parallel Computing is a computational model where the program is broken into multiple smaller sequential computing operations some of which are performed simultaneously. (Time takes as long as it's sequential tasks plus the longest of its parallel tasks)x
Distributed computing
Distributed computing is a computational model in which multiple devices are used to run a program
computing innovation
A computing innovation includes a program as an integral part of its function. A computing innovation can be a physical, non physical computing software, or a non physical computing concept.
program
a program is a collection of program statements that performs a specific task when run by a computer a program is often referred to as software
code segment
A code segment is a collection of program statements that is part of a program
Program documentation
written description of the function of a code segment, event, procedure, or program and how it was developed
comments
a form of program documentation written into the program to be read by people and do not affect how a program runs
logic error
a mistake in the algorithm or program that causes it to behave incorrectly or unexpectedly
syntax error
a mistake in the program where the rules of the programming language are not followed
runtime error
a mistake in the program that occurs during the execution of a program. Programming languages define their own runtime errors
overflow error
an error that occurs when a computer attempts to handle a number that is outside of the defined range of values
Redundancy
the inclusion of extra components that can be used to mitigate failure of a system if other components fail
fault tolerant
a system is fault tolerant when it can support failures and still continue to function
digital divide
The digital divide refers to differing access to computing devices and the Internet, based on socioeconomic, geographic, or demographic characteristics
citizen science
scientific research conducted in whole or part by distributed individuals, many of whom may or may not be scientists, who contribute relevant data to research using their own computing devices
crowdsourcing
the practice of obtaining input or information from a large number of people via the Internet
Phishing
a technique that attempts to trick a user into providing personal information. That personal information can then be used to access sensitive online resources, such as bank accounts and emails
keylogging
the use of a program to record every keystroke made by a computer user in order to gain fraudulent access to passwords and other confidential information
rogue access point
a wireless access point that gives unauthorized access to secure networks
Linear search
sequential search algorithms check each element of a list, in order, until the desired value is found or all elements in the list have been checked. One advantage of a linear search is that the items do not need to be in order or sorted before the search
binary search
a binary search algorithm starts at the middle of a sorted data set of numbers and eliminates half of the data this process repeats until the desired value is found or all elements have been eliminated. A binary search can be much faster than a linear search, but it requires that all the elements are sorted before the search