Advanced Computer Networks - Chapter 2
1/40
Earn XP
Description and Tags
Requirements and Technology
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
41 Terms
(3P) What is Elastic Traffic?
It (traffic that) can adjust, over wide ranges, to changes in delay and throughput across an internet and still meet the needs of its applications.
It is the traditional type of traffic supported on TCP/IP based internets.
It is the type of traffic for which internets were designed.
Applications that generate such traffic typically use Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) as a transport protocol.
These last 3 points are kinda the same. Maybe something like this would be easier to remember? It is the traditional type of traffic supported on TCP/IP based internets and is the type of traffic for which the internets were originally designed for. As such, applications that generate such traffic usually use TCP or UDP as a transport protocol.
TCP: Use the capacity up to maximum rate to accept data. (considers network capacity)
UDP: Use the available capacity up to the rate to generate data. (sends at rate decided by application disregarding network capacity)
(4P) Discuss the differences between TCP and UDP
ROFU
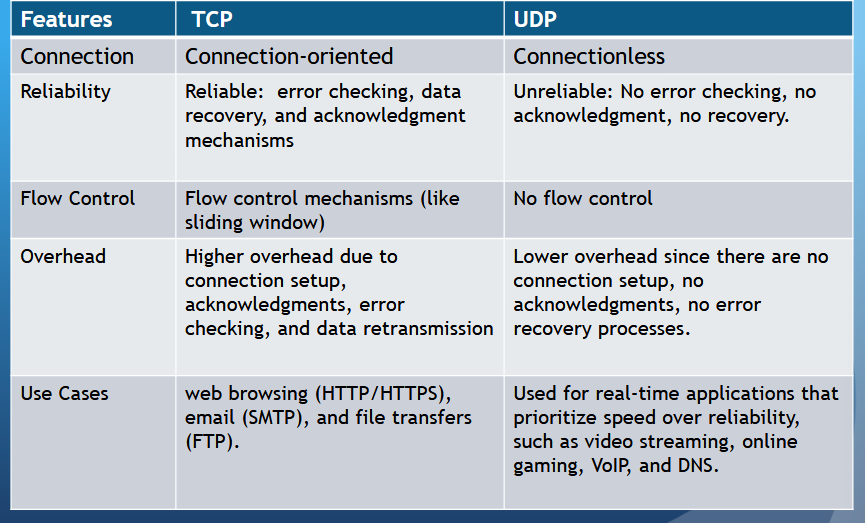
(3P) Cite the Sliding Window Protocols. What is ARQ?
ARQ = Automatic Repeat Query/Request: Error-control method for data transmission that uses acknowledgements and timeouts.
Stop-and-wait ARQ
Go-Back-N ARQ
Selective Repeat ARQ
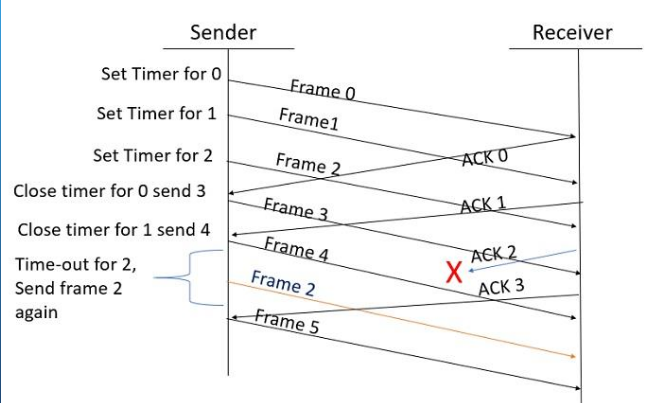
(3P) Why is stop-and-wait ARQ considered sliding-window? Also, understand this img
In networking textbooks (especially ones like Tanenbaum, Kurose & Ross, or Forouzan), the header “Sliding Window Protocols” is often used to describe a family of data link layer protocols that use:
Acknowledgments (ACKs)
Timers (timeouts)
Sequence numbers
Windows (to manage how many frames can be sent before waiting for ACKs)
Even Stop-and-Wait fits this general framework — it’s just the simplest form of it.
So:
Stop-and-Wait = Sliding Window with window size = 1
Go-Back-N = Sliding Window with cumulative ACKs
Selective Repeat = Sliding Window with per-frame ACKs
Image clarification:
Imagine the sender transmits Frame 0, but the ACK gets lost.
The sender times out and retransmits Frame 0.
Without alternating numbers:
The receiver might confuse this retransmission with a new frame and deliver it twice to the application layer.
By alternating between 0 and 1:
The receiver can easily detect duplicates — if it receives another Frame 0 when it’s expecting Frame 1, it knows it’s a retransmission and discards it.
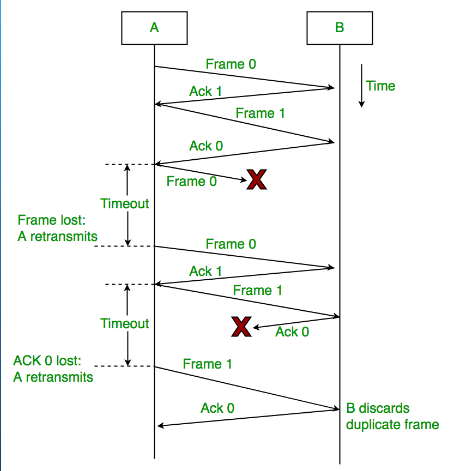
(3P) Understand Go-Back-N ARQ
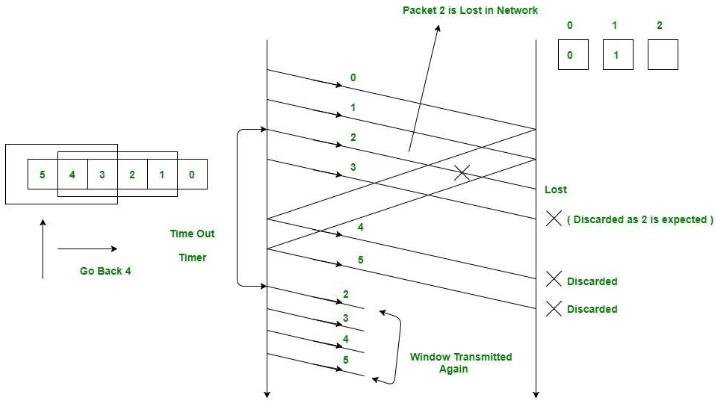
(3P) Understand Selective Repeat ARQ
Unlike Go-Back-N, sender has a buffer and can store the out-of-order packets. That way, even if a packet is lost, the packets that were received after do not have to be discarded.
(3P) Mention protocols that operate through TCP and UDP // (1P) Choose whether these protocols operate over TCP or UDP
File Transfer Protocol (FTP) / Secure FTP (SFTP) → TCP
Simple mail transport protocol (SMTP) (Electronc mail) → TCP
Telnet, Secure Shell (SSH) (remote login) → TCP
Simple network management protocol (typo: SNTP, actually: SNMP) → UDP
Hypertext Transfer Protocol (HTTP) / HTTP Secure (HTTPS) (Web access) → Traditionally TCP, but HTTP/3 (newest version) uses UDP + QUIC
(3P) What is Inelastic Traffic? (Note: The requirements mentioned here for inelastic traffic were asked by Prof. in a general context as well, as in; what are the requirements of Internet Traffic?)
(Traffic that) Cannot easily adjust, or may not adjust at all, to changes in delay and data speed on the internet.
Examples of inelastic traffic include: multimedia transmission such as voice and video, and high-volume interactive traffic.
Requirements may include:
Throughput: A minimum throughput value may be required.
Delay: Also called latency.
Delay jitter: The amount of delay variation is a key factor for real-time applications.
Packet loss: Real-time applications differ in how much packet loss they can tolerate, if any.
(2P) Here are some service class characteristics, along with their tolerance to loss, delay, and jitter. If you consider Very Low → Low, then this isn’t too difficult to memorize. Please dedicate some time to this. You should be able to memorize all of this in 10 min using paper & pen.
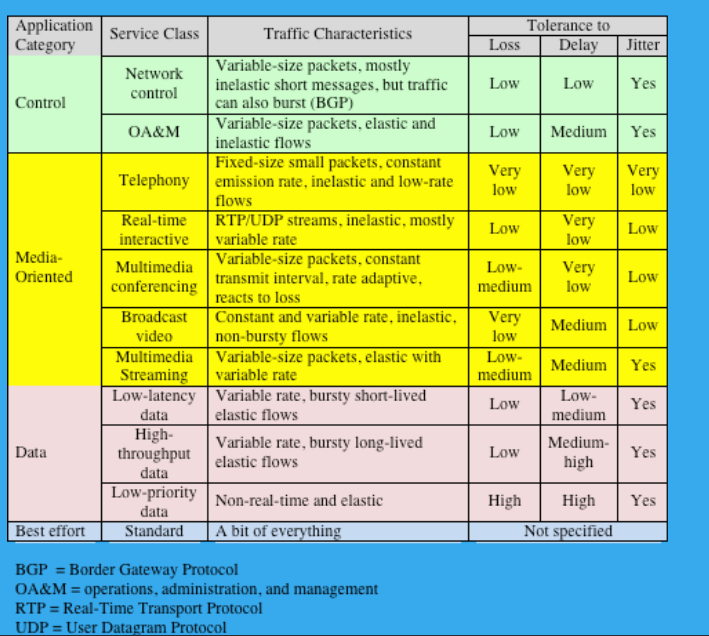
(1P) What are the QoS requirements of these Application Classes? (Voice, Broadcast Video, Real-time interactive video, Multimedia conferencing, Multimedia streaming) (Also easy to memorize with pen & paper, Real-time interactive video → Multimedia Conferencing → Multimedia streaming)
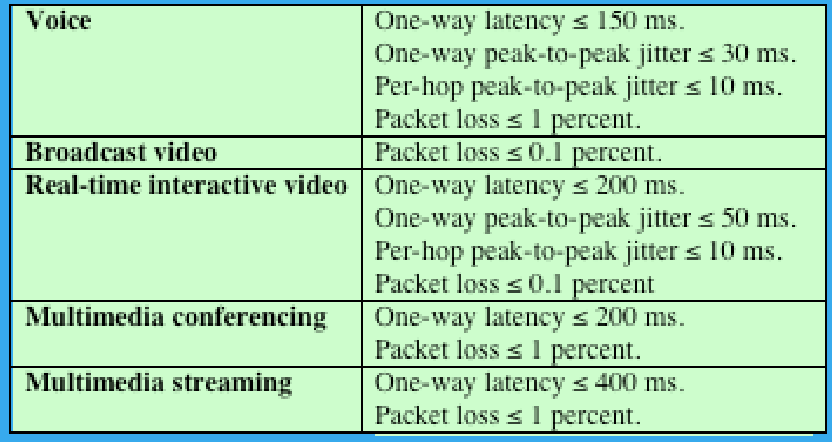
(3P) Discuss Real-Time Traffic and its characteristics
Real time: As fast as required. A real-time system must respond to a signal, event, or request fast enough to satisfy some requirement.
Real-time traffic: A data flow that must meet real-time requirements, such as low jitter and low delay.
It is an example of inelastic traffic.
It is concerned with timing issues as well as packet loss.
In most cases, there is a requirement that data be delivered at a constant rate equal to the sending rate.
In other cases a deadline is associated with each block of data, such that the data are not usable after the deadline has expired.
(By the way, a really nice example relevant to the image: If your device gets a sound packet 2 seconds late, you can’t “insert it” into the music anymore — that moment’s gone, you may as well just consider that packet as ‘lost’ or ‘dropped’.)
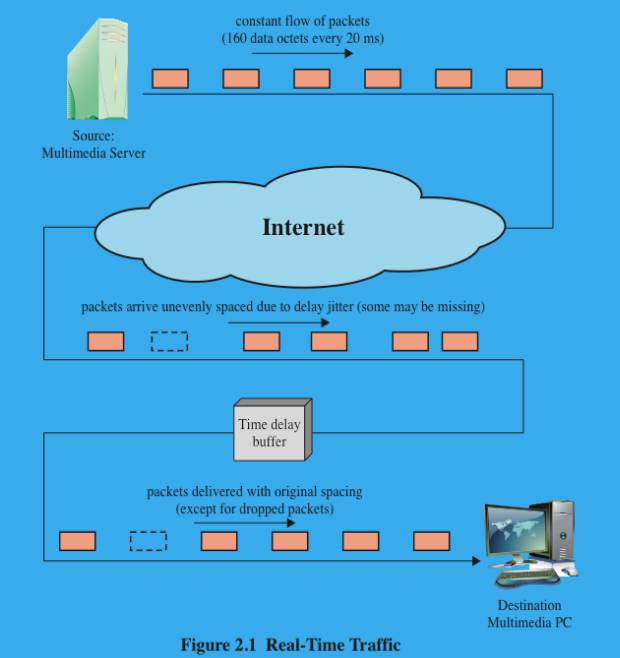
(3P) Which are the data generation types?
Continuous data source:
Fixed size packets are generated at fixed intervals.
Air traffic control radar, Real-time simulation
ON/OFF source:
The source switches between times when it send fixed-size packets at regular intervals and times when it stays idle.
Telephony, audio conference.
Variable packet size:
Source generate variable length packets at fixed intervals
Digitized video
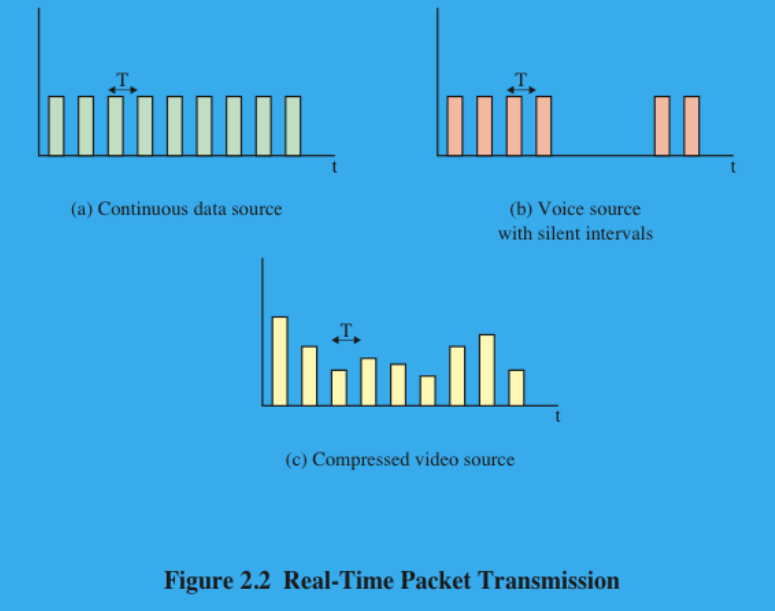
(3P) Demands — Which are the major contributors to traffic presented in the Internet and IP-networks?
Big data
Cloud computing
Mobile traffic
(3P) Discuss Big Data
Big data is data so large in scale that traditional analysis and management tools cannot handle it effectively.
Big data refers to the volume, variety, and velocity of structured and unstructured data that move quickly through networks into storage and processing systems, where they can be analyzed and turned into useful insights for businesses.
Infrastructure:
Relational database management systems (RDBMS)
Network-attached storage (NAS) (HUH)
Storage area networks (SANs) (HUH2?? same shit??)
Data warehouses (DWs)
Business intelligence (BI) analytics
Analytics: Analysis of massive amount of data, particularly with a focus on decision making.
(3P) What are the key elements of a Big Data networking system?
Data warehouse: Integrated data from multiple sources.
Data management servers: Run data analysis applications such as data integration tools and analytics tools.
Workstations/data processing systems: Use big data applications to generate big data warehouses.
Network management server: Network management, control, and monitoring
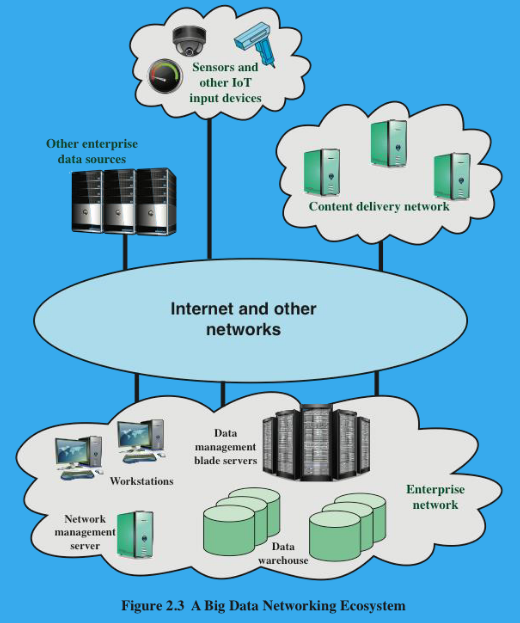
(3P) What are the three V’s that drive the impact of big data on an enterprise’s networking infrastructure?
Volume: Growing amounts of data
Velocity: Increasing speed in storing and reading data
Variability: Growing number of data type and sources
These are the same three V’s mentioned in the definition. Note that.
(0P) Here are some other V’s if you have free time.
(3P) What are the Areas of concern regarding big data?
Network Capacity: Running big data analytics requires a lot of capacity on its own. The issue is magnified when big data and day-to-day application traffic are combined over an enterprise network.
Latency: The real or near-real-time nature of big data demands a network architecture with consistent low latency to achieve optimal performance.
Storage Capacity: Massive amounts of highly scalable storage are required to address the insatiable appetite of big data. Yet these resources must be flexible enough to handle many different data formats and traffic loads.
Processing: Big data can add significant pressure on computational memory and storage systems. If not properly addressed, can negatively impact operational efficiency.
Secure Data Access: Big data projects combine sensitive information from many sources like customer transactions, GPS coordinates, video streams, etc. These must be protected from unauthorized access.
(3P) Discuss the Cloud Network Model
Intra-cloud, inter-cloud, core, together with the OSS components, are the foundation of cloud services composition and delivery. (The cloud network is made up of internal, external, and backbone connections, plus the management systems (OSS) that keep everything configured and running — and together, they make it possible for cloud services (like AWS, Gmail, or Netflix) to actually work and be delivered to users.)
VM: One instance of an OS along with one or more applications running in an isolated paritition within the computer.
Operating Support System (OSS)
→ Network OSS:
Traditional OSS is a system dedicated to providers for telecom service.
They provide serivce management, maintenance, configuration, fault management.
→ Cloud OSS:
OSS of cloud infrastructure is the system dedicated to provide cloud computing service.
They provide maintenance, monitoring, configuration.
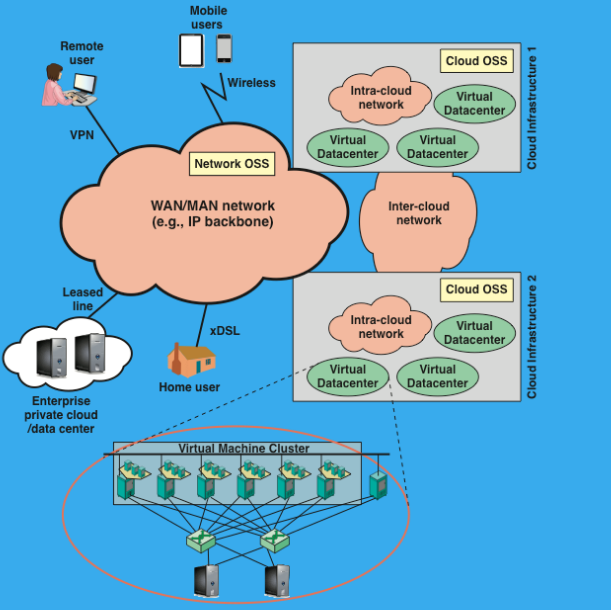
(3P) What are the functional requirements for the network capability of Cloud Computing? (What features or abilities the cloud network must have to properly support cloud computing)
Functional requirements for this network capability:
Scalability: Networks must be able to scale easily to meet the demands of moving from current cloud infrastructures of hundreds or a few thousand of servers to networks of tens or even hundreds of thousands of servers. (The network should “grow with the cloud” — adding servers, data centers, or users should be straightforward and not cause performance drops or reconfiguration chaos.)
Performance: Traffic in both big data installations and cloud provider networks is unpredictable and quite variable.
Agility and flexibility: The cloud-based data center needs to be able to respond and manage the highly dynamic nature of cloud resource utilization.
(2P, QUESTIONABLE SLIDE) What are the types of enterprise traffic?
Mobile data traffic: All enterprise traffic that crosses a mobile access point.
Managed IP traffic: All enterprise traffic that is transported over IP but remain within the corporate WAN.
Internet Traffic: All enterprise traffic that crosses the public internet.
I have no clue why the header is Mobile Traffic honestly.

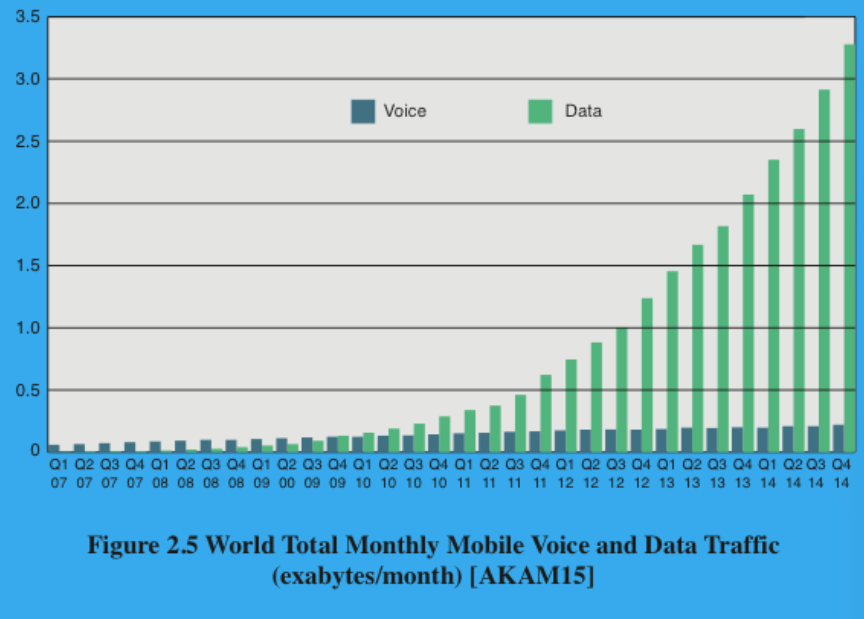
(0.5P) How has the World Total Monthly Mobile Voice and Data Traffic data changed over the years?
Immense growth, especially on the data department.
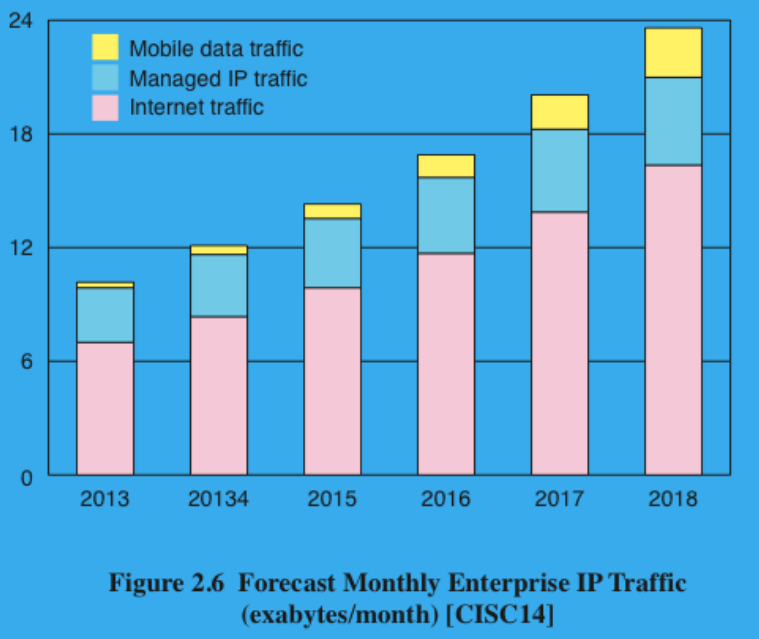
(1P) Rank the sources of traffic in an enterprise from largest to smallest. What percentage has each traffic source increased between 2013-2018?
Internet traffic
Managed IP traffic
Mobile data traffic
Internet Traffic: 18%
Managed IP traffic: 10%
Mobile Data Traffic: 55%
Total Traffic: 18%
(4P) What is Quality of Service (QoS)?
The measurable performance of a network service from start to finish, which can be guaranteed by an agreement between a user and a provider to meet specific customer needs.
This agreement is called service level agreement (SLA) between a user and a service provider.
Commonly specified properties include:
Throughput
Delay
Packet jitter
Error rate
Packet loss
Priority
Availability
Security
(4P) What is Quality of Experience (QoE)?
A subjective measure of performance as reported by the user; relies on human opinion.
It is particularly important when dealing with multimedia applications and multimedia content delivery.
QoS processes by themselves are not sufficient in that do not take into account the user’s perception of network performance and service quality.
Categories of factors and features that can be included in QoE are:
Perceptual: Quality of sensory of user Experience. Ex: Video sharpness, brightness, contrast, etc.
Psychological: User’s feeling. Easy of use, joy of use, usefulness, etc.
Interactive: Interaction between user and application or device. Responsiveness, communication efficiency.
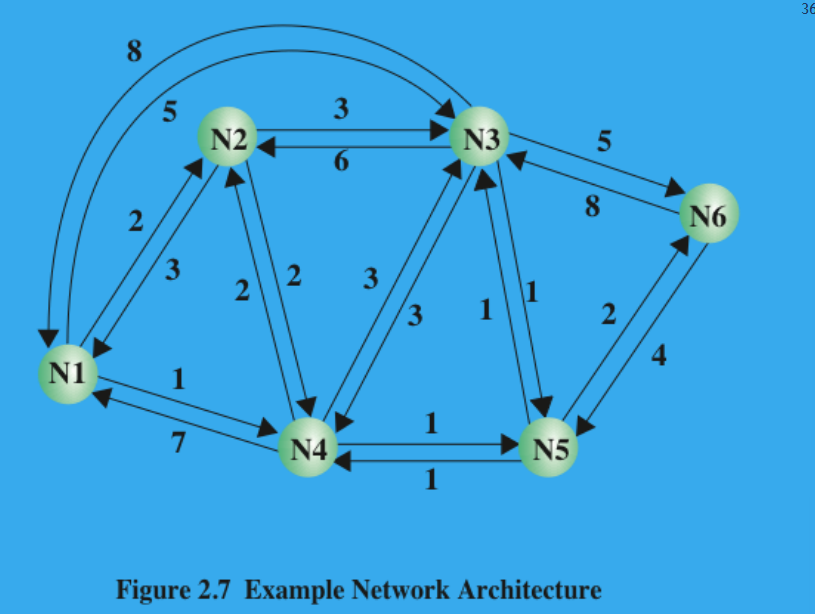
(2P) Discuss routing. Why must a routing function be performed? On what is the selection of the route based on?
The primary function of the internet is to accept packets from a source station and deliver them to a destination station.
To accomplish this, a path or route through the network must be determined.
Generally, more than one route is possible; therefore, a routing function must be performed.
Selection of a route is generally based on some performance criterion.
The simplest criterion is to choose the minimum-hop route (one that passes through the least number nodes) through the network.
A generalization of the minimum-hop criterion is the least-cost routing; in this case, a cost is associated with each link, and, for any pair of attached stations, the route through the network that accumulates the least cost is sought.
(2P) What information is used for forwarding decision? What factors affect routing?
There are various information used for forwarding decision:
Destination address
Source address
Packet flow identifier
Security
etc
Key factors that affect routing DYNAMICALLY(?):
Failure: When a node or link fails.
Congestion: When a particular portion of the network is heavily congested.
Topology change: Insertion of new link or node
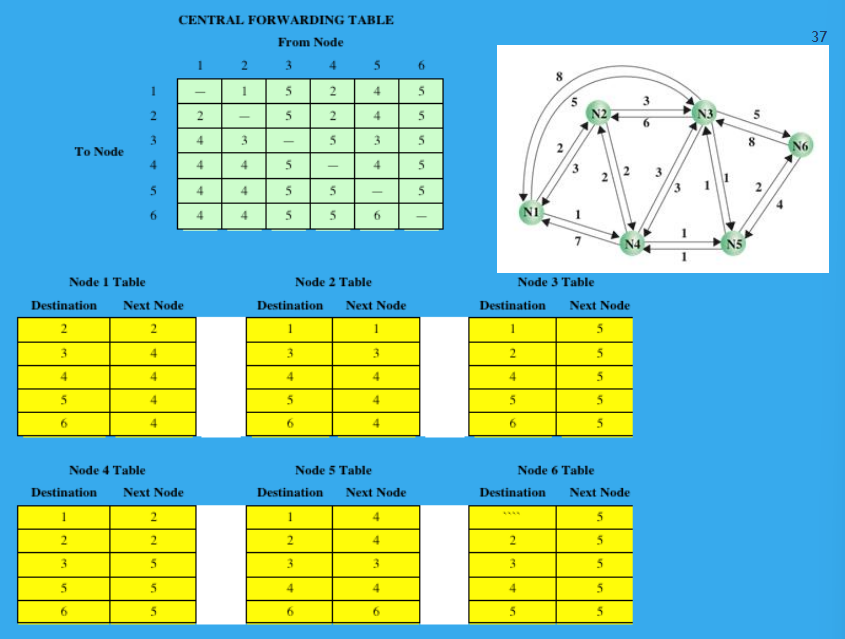
(1P) Here’s a forwarding table example. Understand the tables and you’ll do fine.
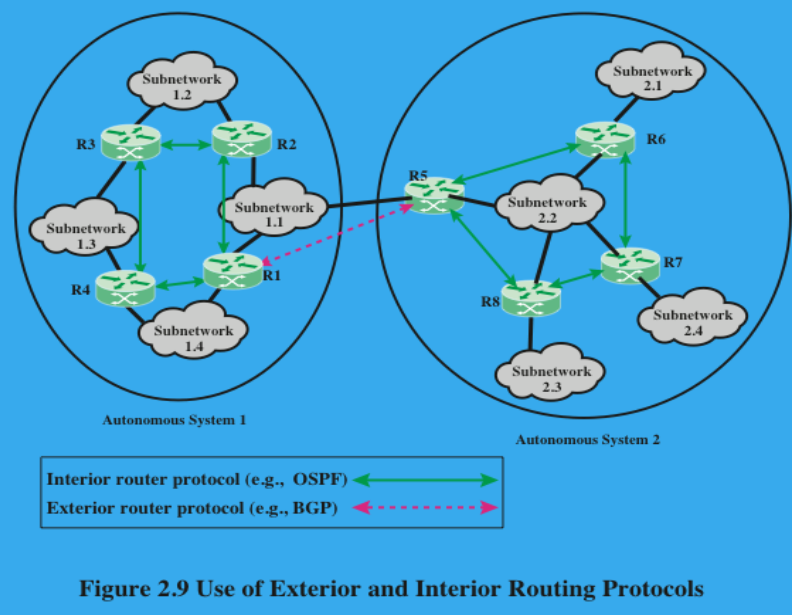
(2P) Discuss Routing Protocols. What are AS? What characteristics do they exhibit?
Routers are responsible for receiving and forwarding packets through the interconnected set of networks.
Each router makes routing decisions based on knowledge of the topology and traffic/delay conditions on the internet.
A degree of dynamic cooperation is needed among the routers.
The router must avoid portions of the network that have failed and should avoid portions of the network that are congested.
There are essentially two categories of routing protocols which are based on the concept of an autonomous system (AS).
An AS exhibits the following characteristics:
An AS is a set of routers and networks managed by a single organization.
An AS consists of a group of routers exchanging information via a common routing protocol.
Except in times of failure, an AS is connected (in a graph-theoretic sense).
An interior router protocol (IRP) is a shared routing protocol that passes routing information between routers within an AS. (Example: OSPF).
An exterior router protocol (ERP) is a routing protocol that passes information between routers in separate AS.
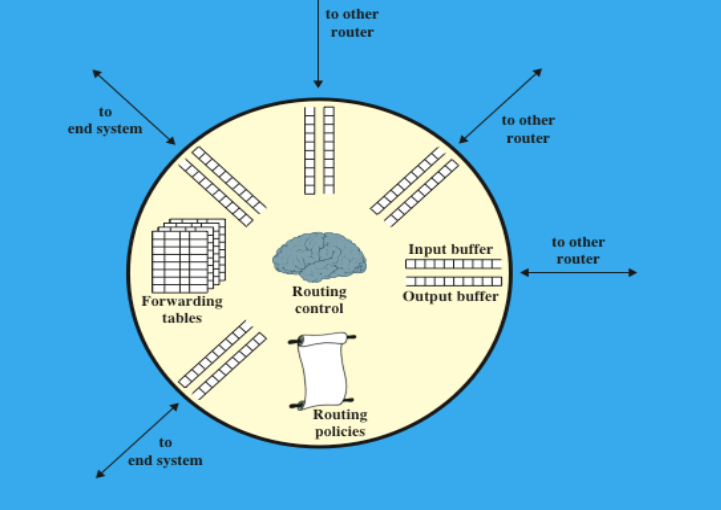
(1.5P) Note some router elements
Input & Output buffers
Routing Policies
Forwarding Tables
Routing Control
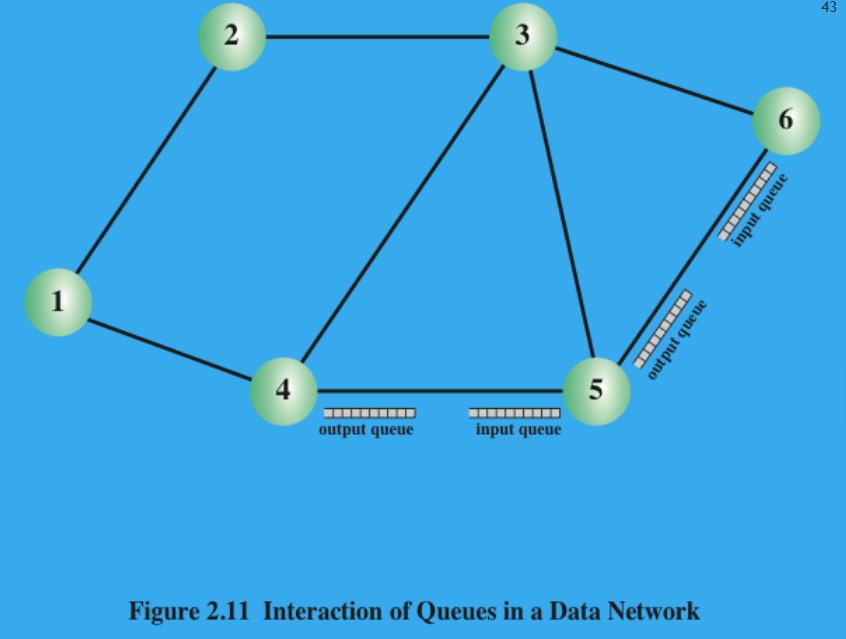
(3P) Discuss Congestion and the strategies that can be deployed to combat its effects.
Congestion: If traffic demand exceeds capacity, Internet does not manage the traffic. (In better terms: When traffic demand exceeds the available network capacity, packets may be delayed or dropped, since the Internet does not centrally manage or control overall traffic flow.)
Effect of Congestion: When packets arrive too fast for a router to process them. Two strategies can be adopted:
Discard any incoming packets for which there is no available buffer space.
Exercise some flow control over to neighboring nodes.
(By the way, both of definitions are kinda the same thing, just different views: Congestion occurs when overall traffic demand exceeds the available capacity, which causes routers to receive packets faster than they can process or forward them.)
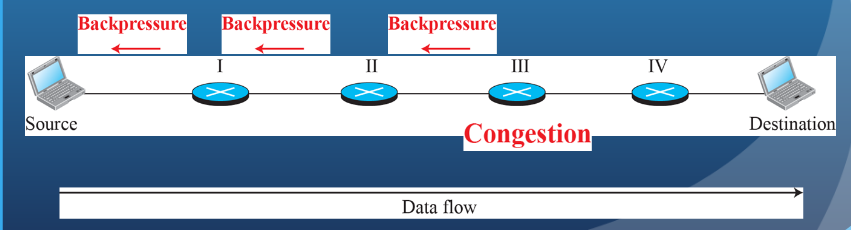
(1P) What are some congestion control techniques/mechanisms?
Discarding
Backpressure
Choke packet
(3P) Discuss Backpressure
Can be exerted on the basis of links or logical connections.
Flow restriction propagates backward( against the flow of traffic) to sources, which are restricted in the flow of new packets into the network.
Backpressure is automatically triggered by flow control mechanisms at the data link layer for traffic on a specific link.
Backpressure can also be selectively applied to logical connections so that the flow from one node to the next is only restricted or halted on some connections, generally the ones with the most traffic.
⚙ How it works
Each node (router or switch) monitors its output queues.
If a queue becomes full or nearly full, the node restricts the flow of new packets coming from the previous node.
That upstream node may, in turn, have to slow down the node before it — creating a chain reaction of flow restriction upstream.
As a result, packet injection into the network decreases, giving the congested area time to clear.
(3P) Discuss Choke Packets
A control packet generated at a congested node and transmitted back to a source node to restrict traffic flow.
Either a router or a destination end system may send this message to a source end system.
On receipt of a choke packet the source host should cut back the rate at which it is sending traffic to the specified destination until it no longer receives choke packets.
The choke packet can be used by a router or host that must discard IP datagrams because of a full buffer.
The router will issue a choke packet for every packet that it discards.
A system may anticipate congestion and issue choke packets when its buffers approach capacity.
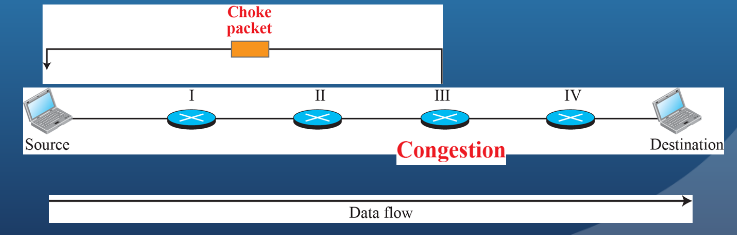
(3P) Explain Implicit Congestion Signaling
When network congestion occurs, two things may happen:
The transmission delay for an individual packet from source to destination increases, so that it is noticeably longer than the fixed propagation delay.
Packets are discarded
In implicit signaling, there is no communication between the congested nodes and the source. The source guesses that there is congestion in a network.
For example, when the sender sends several packets, and there is no acknowledgment for a while, one assumption is that there is a congestion.
Congestion control based on implicit signaling is the responsibility of end systems and does not require action on the part of network nodes.
(3P) Explain Explicit Congestion Signaling. Note the difference between it and choke packets.
In explicit signaling, if a node experiences congestion, it can explicitly send a packet to the source or destination to inform about congestion.
The difference between choke packet and explicit signaling is that the signal is included in the packets that carry data (marking) rather than creating a different packet as in the case of choke packet technique.
Explicit congestion signaling approaches can work in one of two directions:
Backward:
In backwards signaling, a signal is sent in the opposite direction of the congestion.
The source is warned about congestion and it needs to slow down.
Forward:
In forward signaling, a signal is sent in the direction of the congestion.
The destination is warned about congestion.
The receiver in this case adopts policies to prevent further congestion.
(2P) What are the categories of explicit congestion signaling approaches?
Binary:
A bit is set in a data packet as it is forwarded by the congested node.
When a source receives a binary indication of congestion on a logical connection, it may reduce its traffic flow.
Credit based:
These schemes are based on providing an explicit credit to a source over a logical connection.
The credit indicates how many octets or how many packets the source may transmit.
Common for end-to-end flow control, in which a destination system uses credit to prevent the source from overflowing the destination buffers.
Rate based:
These schemes are based on providing an explicit data rate limit to the source over a logical connection.
The source may transmit data at a rate up to the set limit.
To control congestion, any node along the path of the connection can reduce the data rate limit in a control message to the source.
Read addendum 4.
(1P/5P) Discuss Software-Defined Networking (SDN)
An approach to designing, building, and operating large-scale networks based on programming the forwarding decisions in routers and switches via software from a central controller/server.
SDN differs from traditional networking, which requires configuring each device separately and which relies on protocols that can not be altered.
The two elements involved in forwarding packets through routers are:
Control function, which decides the route the traffic takes and the relative priority of traffic.
Data function, which forwards data based on control-function policy.
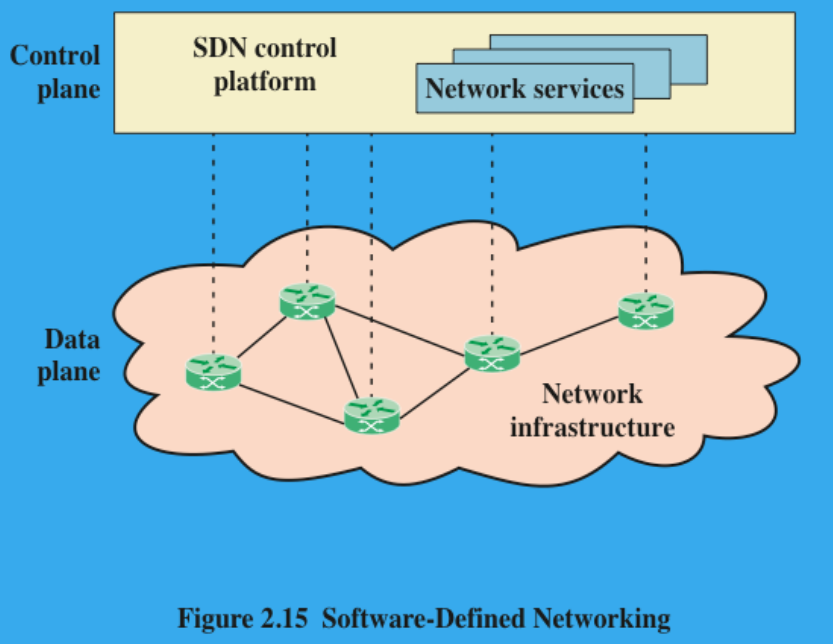
(0.5P) Explain Network Function Virtualization
Virtualization of network functions by implementing these functions in software (rather than hardware) and running them on virtual machines.
NFV has a number of features in common with SDN. They share the following objectives:
Move functionality to software.
Use commodity hardware platforms instead of proprietary platforms.
Use standardized or open APIs.
Support more efficient evolution, deployment, and repositioning of Network Functions.
NFV and SDN are independent but complementary schemes.
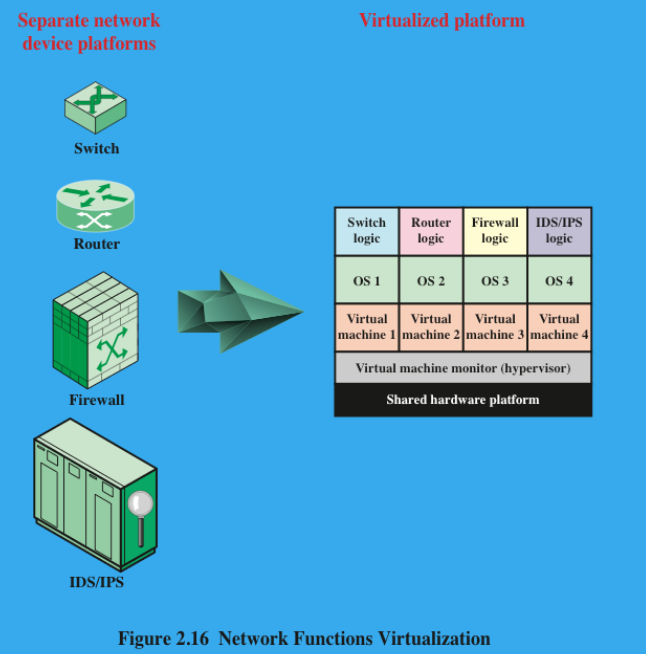
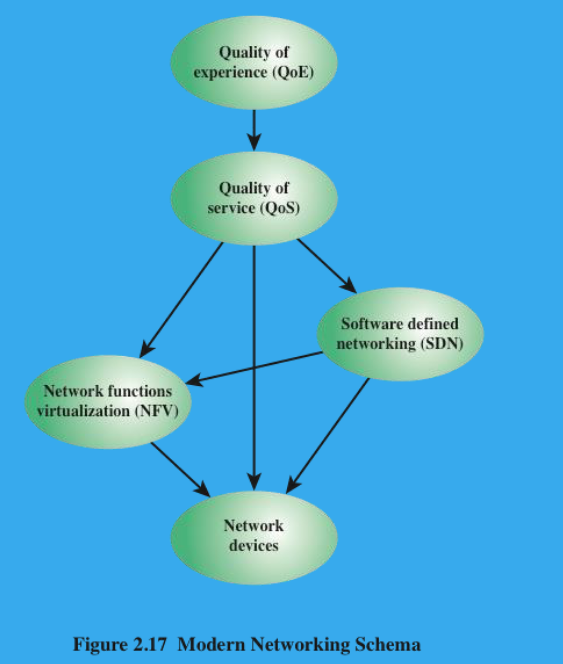
(1P) Draw the Modern Networking Schema