Professor Messor 4.2 | Password Attacks
1/7
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
8 Terms
Plaintext / Unencrypted Passwords
Some applications store passwords in plaintext, meaning they are saved "in the clear" without any encryption. This practice is rare but poses a significant security risk. Anyone who gains access to the password file or database can easily read and misuse every stored credential.
To mitigate this risk, it's essential not to store passwords as plaintext. If you discover that your application saves passwords in this manner, the best course of action is to switch to a more secure application that properly encrypts passwords.
Hashing a Password
Is a process where data, such as a password, is transformed into a fixed-length string of text using a mathematical algorithm. This string, known as a hash, acts like a "fingerprint" of the data. Just as a fingerprint uniquely identifies a person without revealing their entire identity, a hash uniquely represents the original data without revealing it.
Is a one-way process, meaning it's impossible to recover the original password from its hash. Additionally, different inputs should produce unique hashes, minimizing the chance of two different inputs generating the same hash (known as a collision).
A common security practice because, even if someone gains access to the hashed password file, they cannot easily reverse-engineer the original passwords.
A Hash Example:
Consider plain text passwords like "123456" and "querty." These are easily readable, making them vulnerable if someone gains access to the password file. However, when these passwords are hashed, they transform into long, complex strings that are much harder to decipher.
For example, if you hash the password "123456" using the SHA-256 algorithm, you get a unique, long string. Changing just one character, as in "1234567," results in a completely different hash. This demonstrates the sensitivity of the hashing process to even minor changes in the input.
What's crucial is that these hashes cannot be reversed to retrieve the original passwords.
The password file
Different across operating systems and application; different hash algorithms.
Brute force hash example
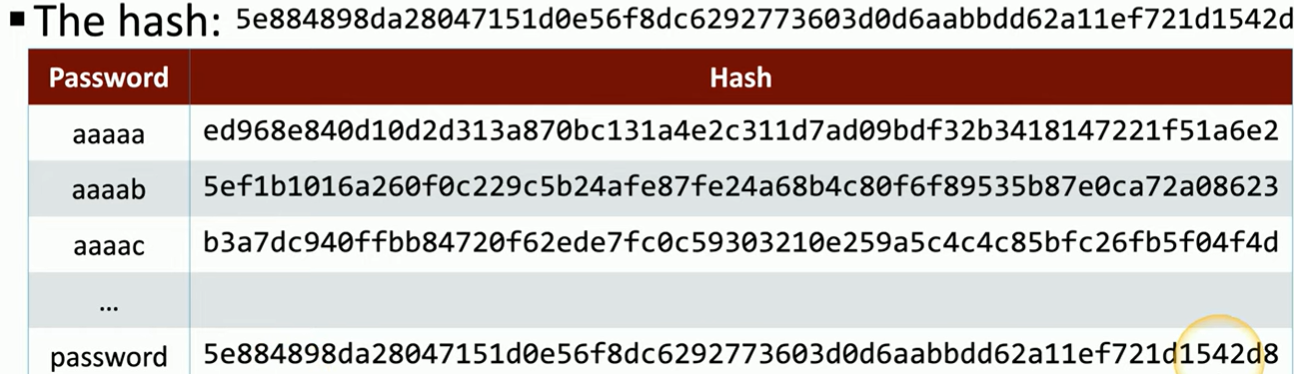
Imagine a hacker has obtained a hashed password file, with one hash ending in "428." The hacker starts by hashing simple passwords like "aaaaa" and comparing the results to the target hash. If "aaaaa" doesn't match, the hacker moves on to the next possible password.
This process continues until the hacker hashes the password "password." When they do, they find that the hash generated for "password" matches the hash in the file, revealing the original password.
Types of Brute Force Attacks
Online Brute Force:
In an online brute force attack, the attacker repeatedly tries to log in by guessing passwords directly through the login interface.
This method is slow because most systems have security measures like account lockouts after a certain number of failed attempts.
Offline Brute Force:
In an offline brute force attack, the attacker has already obtained a list of hashed passwords.
They can take their time calculating possible password hashes and comparing them to the stored hashes without worrying about account lockouts or rate limits.
This method requires significant computational resources, but it's more effective because the attacker can work at their own pace without triggering alarms.
Dictionary attacks:
Involve using a list of common words to guess passwords. Attackers generate hashes for each word in the dictionary and compare them with the hashed passwords they’re trying to crack. Since passwords are often human-created, many common wordlists are available online, with some tailored to specific languages or industries. For instance, a medical professional's wordlist may differ significantly from an IT-related one.
Attackers may also use letter substitutions, such as "p&ssw0rd" for "password," with software adjusting for these variations. Cracking can be sped up with distributed and GPU cracking methods, but it remains time-consuming.
Dictionary example:
Are going to go through the list of dictionary words, find the common names, and try to find matches in our file. So you may find that common words like ninja, dragon, football, let me in, or password are hashes that can be found relatively easily.