Formulas Spring 2025
1/143
Earn XP
Description and Tags
Formulas for all classes 2025
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
144 Terms
V=πr^2h
Cylinder Volume
l×w×h (length × width × height)
Rectangular Prism
V=4/3πr^3
Sphere
D=m/V
Density
sin of, 30 | 60 triangle
½ | √3/2
cos of 30 | 60 triangle
√3/2 | ½
tan of 30 | 60 triangle
√3/3 | √3
cotangent of a 30 | 60 triangle
√3 | √3/3
secent of the 30 | 60 triangle
2√3/3 and 2
secent
2√3/3 and 2
secent
2 and 2√3/3
sin of a 45 triangle
√2/2
cosine of a 45 triangle
√2/2
tan of a 45 triangle
1
cotangent of a 45 triangle
1
sec of a 45 triangle
√2
cosecant of a 45 triangle
√2
The number significant digits in the answer (math) should
be of the same as the lowest variable in the equation
significant digits is the
#of digits counted from the 1st non zero digits
complimentary angles are (alpha and beta)
angles that equal 90 degrees
the angle sum of a triangle is
180 degrees
The Pythagorem Theorem is
a2+b2=c2
A congruent triangle has
the same sides and angles
Similar triangles
have the same angle measures but different side lengths
A vertical angle would be
<1 and <4
An alternate interior angle would be
< 3 and <6
An alternate exterior angle example is
<1 and <8 or <2 and <7
Corresponding Angles exam
<1 = <5 and <2= <6
Interior angle on same side of the transversal
< 3 and < 5 =180s | < 4 and <6 = 180
The two special triangles are
45 triangle and 30,60 triangle
Servers are computers that provide information to
end device
Clients are computers that send requests to the servers to
retrieve information
Email server runs email server ________.
Clients use _____ software to access email.
software | client
Web server runs ___ _______ software.
Clients use ________ ________ to access web pages.
web server | browser software
File server stores _____ and user files.
The _____ devices access these files.
corporate | client
An end device is where a message
originates from or where it is received
Example of an intermediary device
switches, wireless access points, routers, and firewalls.
An Intermediary device manages
data as its moves through a network
Communication across a network is carried through a
medium which allows a message to travel from source to destination.
Medium Type examples include
Metal wires within cables
Glass or plastic fibers within cables (fiber-optic cable)
or Wireless transmission
Metal wires within cables use
electrical impulses
glass or plastic fibers within cables (fiber-optic cable) use
pulses of light
Wireless transmission use
modulation of specific frequencies of electromagnetic waves.
Topology diagrams, use ________ to represent devices within the network
symbols
Physical topology diagrams illustrate the ________ of intermediary devices and cable installation.
physical location
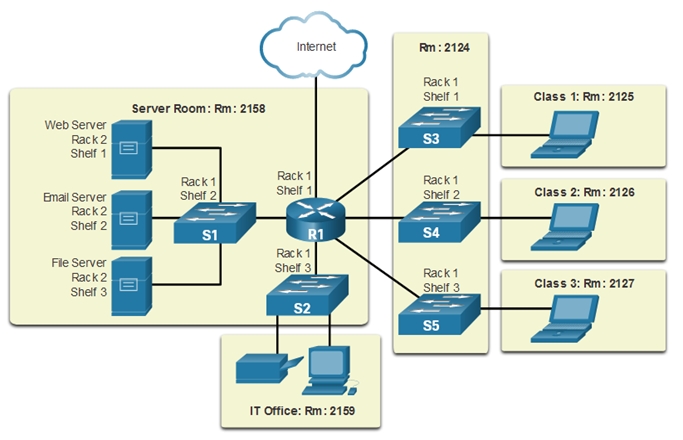
physical topology
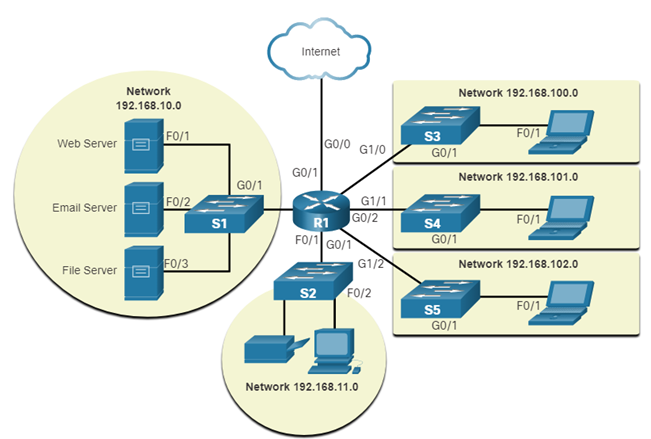
logical topoligy
Logical topology diagrams illustrate ______ _______ _________ of the network.
devices, ports, and the addressing scheme
Small Home Networks
•connect a few computers to each other and the Internet
Small Office/Home Office
•enables computer within a home or remote office to connect to a corporate network
Medium to Large Networks
many locations with hundreds or thousands of interconnected computers
World Wide Networks
connects hundreds of millions of computers world-wide – such as the internet
Two most common types of networks
Local Area Network (LAN)
Wide Area Network (WAN)
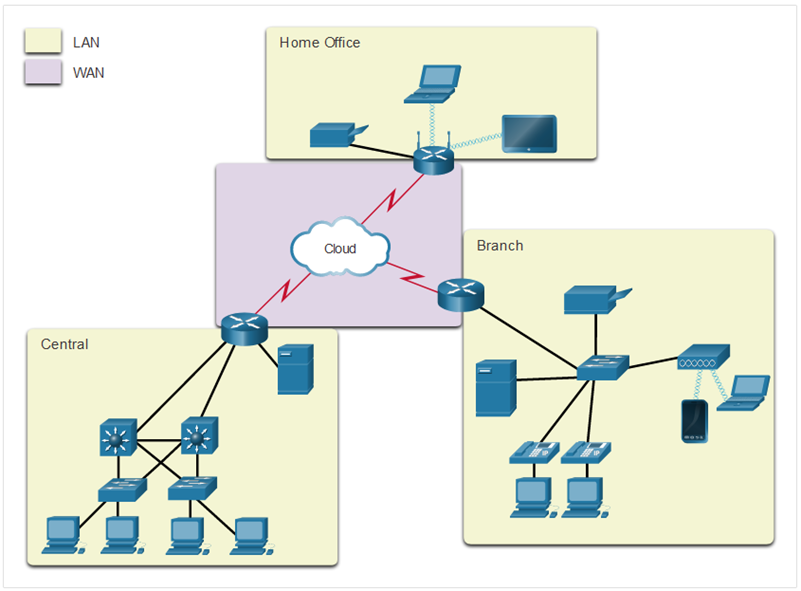
Visual Representation of a LAN | WAN network
LANs are connected to each other using
WANs
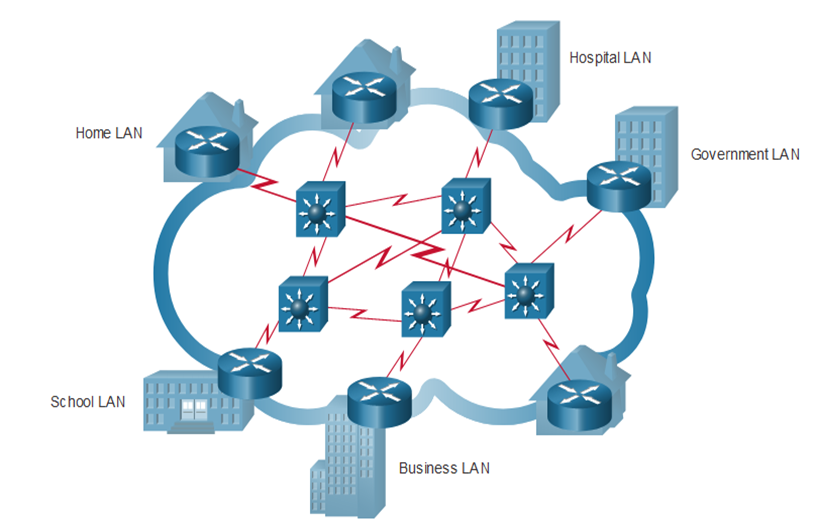
Visual Representation of LAN and WAN connection
The following groups were developed to help maintain structure on the internet
•IETF
•ICANN
•IAB
IETF (Internet Engineering Task Force)
Develops and maintains technical standards for the internet, such as communication protocols (e.g., TCP/IP, HTTP).
ICANN (Internet Corporation for Assigned Names and Numbers)
Manages domain names, IP addresses, and the DNS system to ensure unique and organized addressing.
IAB (Internet Architecture Board)
Oversees internet standards and protocols, providing guidance on overall internet architecture and policies.
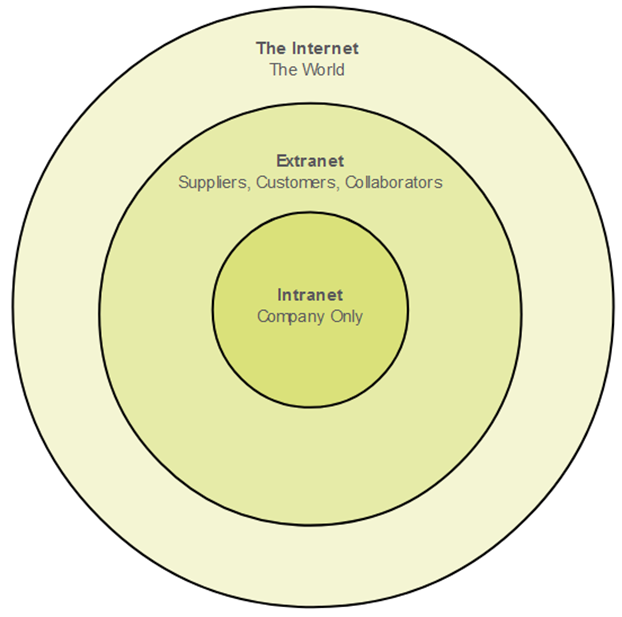
Visual Diagram of Intranet and Extranet
Popular services for home users and small offices include _________ ______, broadband digital subscriber line (DSL), _______ ___, and mobile services.
broadband cable | wireless WANs
•Organizations need faster connections to support __ ___________, ______ ____________, and data center storage.
IP phones, video conferencing
Home and Small Office Internet Connections consist of cable, ____, cellular, _______, and _______ _________
DSL | Satellite | Dial-Up Telephone
Cable connection offers _____ _________, always on, internet offered by cable television service providers
high bandwidth
A DSL connection offers high bandwidth, always on, internet connection that runs over a _______ _____.
telephone line
Corporate business connections consist of _________ ___, DSL, _________ ______ _____, and satellite
dedicated lease line, Ethernet WAN,
Dedicated lease line are
reserved circuits within the service provider’s network that connect distant offices with private voice and/or data networking.
Converged networks can deliver data, _____, and video over the same network infrastructure
voice
The converged network infrastructure uses the same
set of rules and standards.
Management Information Systems refer to
the ability to manage a collection of systems, which work together, allows a business to run smoothly and efficiently
Great management revolves around the ability to
communicate
John Locke is the father of _____ and developed the theory of ________
liberalism | property
Adam Smith is the father of ______ and develop the principles of _________ of labor and ______ enterprise
economics | division | free
The four basic characteristics that the underlying architectures need to address to meet user expectations are
Fault Tolerance | Scalability | Quality of Service (QoS) | Security
A fault tolerant network limits the impact of a failure by limiting
the number of affected devices
Reliable networks provide redundancy by implementing
a packet switched network
Packet switching splits ______ into packets that are ______ over a network
traffic | routed
A scalable network can expand quickly and easily to support new users and applications without
impacting the performance of services to existing users.
Quality of Service (QoS) is the primary mechanism used to ensure
reliable delivery of content for all users.
•With a QoS policy in place, the router can more easily ______ the flow of _____ ___ _____ traffic.
manage | data and voice
Network infrastructure security consist of _________ _________ of network devices and preventing __________ _________ to the devices
physical security | unauthorized access
Information Security is protection of the _________ or ____ transmitted over the network
information | data
The are two main types of network security that must be addressed are
Network Infrastructure Security and Information Security
Three goals of network security
CIA (Confidentiality, Integrity, Availibility)
Confidentiality
only intended recipients can read the data
Integrity
assurance that the data has not be altered with during transmission
Availability
assurance of timely and reliable access to data for authorized users
A NIC is a specialized port on a networking device that
connects to individual networks.
S1> is what mode
User Exec
Connect command in PKA terminal
opens a terminal connection
(Cisco) When part of a command is typed, the _____ key can be used to complete the partial command.
Tab
S1# is what mode
Privilleged Exec
S1 (config) #
global configuration mode.
S1# clock set 15:00:00 31 Jan 2035 does what
set clock to the date and time requested
enable command
turn on privilege exec
Switch# configure terminal
Switch(config)# hostname S1
S1(config)# exit
S1#
Assigning a name to a switch
configure terminal is what comand
to enter configuration mode
S1# config t
S1(config)# enable secret itsasecret
S1(config)# exit
S1#
enables an encrypted password that overwrites the enable password