4.5 Firewalls
1/10
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
11 Terms
Network-Based Firewalls
Sits inline within the network and filters traffic based on defined rules
Can allow or block traffic by analyzing port numbers (traditional firewalls)
Or by inspecting application data (next-generation firewalls).
Often include additional features like acting as a VPN endpoint or concentrator, allowing secure site-to-site or remote access connections.
Also capable of performing routing functions such as network address translation (NAT) and dynamic routing.
Are typically placed at the edge of the network, where the internal network connects to external networks like the internet.
Next-Generation Firewalls (NGFW)
Goes beyond traditional port-based filtering by analyzing traffic to identify the actual application in use.
Also known as application layer gateways, stateful multi-layer inspection devices, or deep packet inspection devices.
Examine traffic in detail, capturing and categorizing packets to determine what application is being used before deciding whether to allow or block it.
Requires more processing and analysis than traditional firewalls.
Ports & Protocols
Traditional firewalls made security decisions based solely on port numbers, without understanding the actual applications using those ports.
For example, they would allow traffic on TCP port 22 for SSH or TCP port 3389 for Microsoft Remote Desktop purely based on those numbers.
Next-generation firewalls (NGFWs), however, can identify and understand the actual applications—like SSH or RDP—regardless of what port they’re using.
NGFWs can still make decisions based on port numbers like traditional firewalls, they also offer the advantage of deeper traffic inspection to recognize applications directly.
Firewall Security Policies
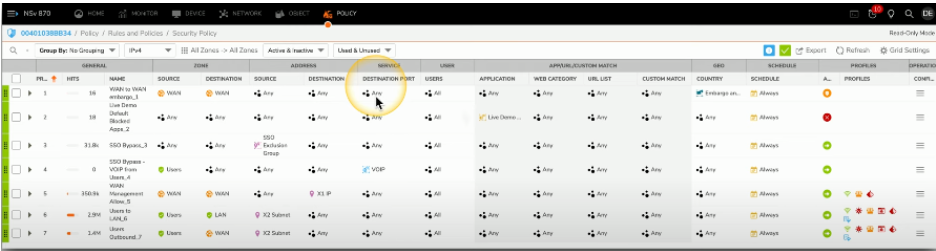
Here is a security policy from a next-generation firewall. And you can see that there are a number of different parameters that can be chosen.
For example, we can see the name that is associated with the rule, where the source of the traffic is coming from, where the destination is going to, and then you can specify information about IP addresses, services, which would be port numbers, the user that is associated with that traffic flow, and then, of course, the application, web category, URL list, or other matches that you can then add into that next-gen firewall rule.
Firewall Rules
Are typically processed from the top of the rule list downward, with each rule being evaluated in order.
More specific rules are placed at the top, while broader or general rules go lower.
Usually include an implicit deny rule at the bottom, meaning any traffic that doesn't match a listed rule is automatically blocked.
Access Control List (ACL) — Each rule can include criteria like source and destination IP addresses, port numbers, time of day, and even specific application names.
Web Server Firewall Ruleset
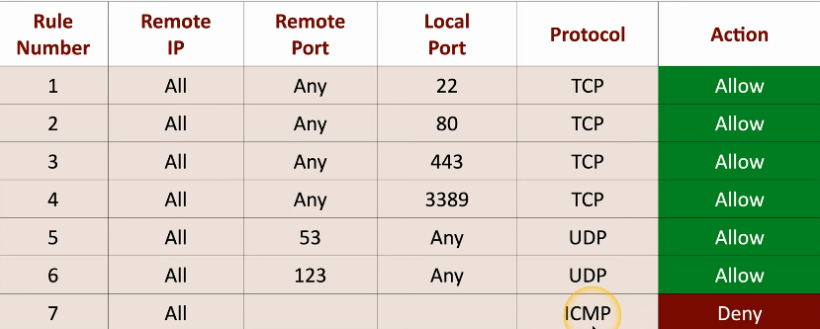
Let’s look at a list of firewall rules and understand what might be allowed or what might be blocked through this particular firewall.
The first rule that’s in our firewall will accept all traffic that is coming from a remote IP address and remote port number. And it’s looking for any traffic that may be destined for local port 22 using the TCP protocol. Knowing what we’ve already learned about protocols, we know that is SSH. And any SSH traffic inbound from a remote device to our local network is allowed through this firewall.
Lastly, we have a rule for any remote IP address. And this particular rule does not have a remote port number or local port number because the protocol that’s being used is ICMP which is commonly associated with a ping. And ICMP does not use UDP or TCP.
If there’s any inbound traffic over ICMP, that traffic is denied in the firewall.
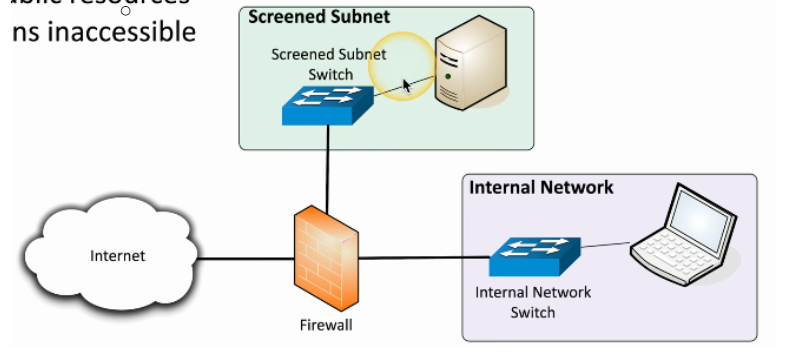
Screened Subnet
A network segment placed between the internet and an internal network, typically separated by a firewall.
Holds public-facing services (like web servers) that need to be accessed from the internet.
Helps protect the internal network from external access.
Also known as a DMZ
Intrusion Prevention Systems (IPS)
Like firewalls, uses rules—often signature-based—to identify known threats as traffic passes through.
Many next-generation firewalls include this
Some solutions detect threats by identifying anomalies, comparing current traffic to a baseline of normal activity (If abnormal behavior is detected, it can be blocked even without a known signature.)
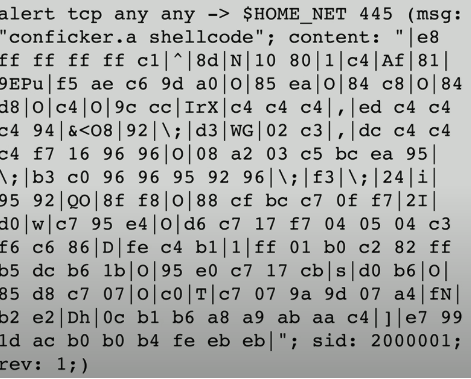
IPS Signature Example
This signature is looking for a very specific type of traffic to pass through the IPS.
And if that traffic matches the signature, the IPS can then react to that and make decisions on whether that traffic should be allowed or blocked.
This has been written for the Conficker worm.
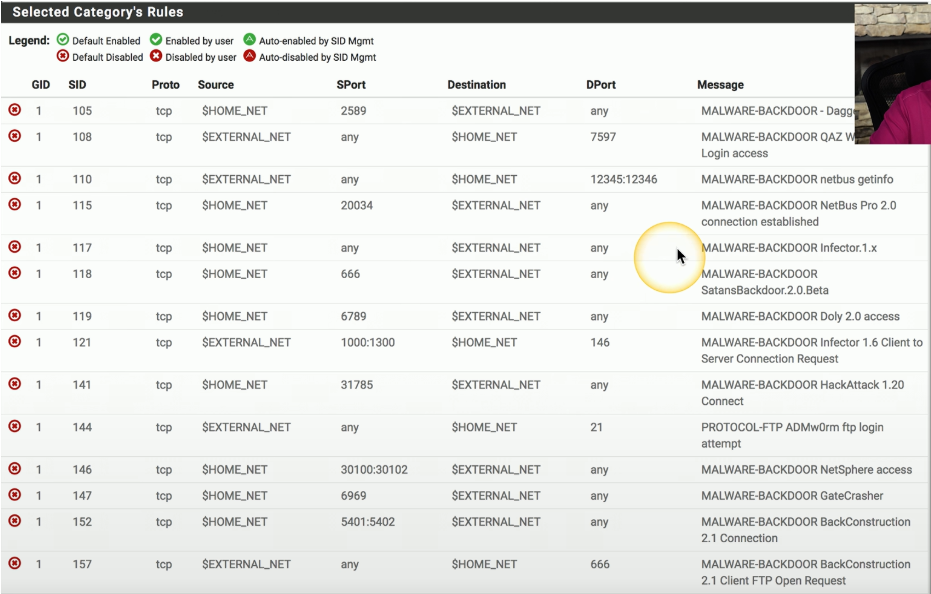
IPS Example:
Here’s an example of rules that you might find in an IPS. Many of these are based on malware.
You can see port numbers that might be used and the name of the malware that would be identified by the IPS.
This one is for an FTP protocol where there is a worm that can be identified as part of the FTP login process.
And you can configure your IPS to identify that worm logging in and block it before it gets inside of your network.
IPS Rules
Uses a large rule base, similar to a firewall, to determine whether to allow or block traffic based on known vulnerabilities.
These rules are built from thousands of signatures that identify specific threats
To manage the complexity, rules can be grouped (If any of the roles associated with a database injection are identified, block all of that traffic at the IPS)
Many IPS systems automatically create these groups, they can also be customized.
Due to the sheer number of rules, false positives can occur, so fine-tuning the IPS rules helps strike a balance between strong security and avoiding incorrect threat detection.