4.5 Secure Protocols
1/6
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
7 Terms
Unencrypted Network Data
Many common protocols like Telnet, FTP, SMTP, and IMAP transmit data in plaintext, making it vulnerable.
Network traffic—whether wired or wireless—should be encrypted to protect sensitive data.
Capturing packets on a network can reveal which protocols are unencrypted.
Unencrypted traffic will display readable data inside the packet.
Wall Of Sheep
If you use one of these insecure protocols and you happen to attend the DEFCON conference…
List of everyone at the conference who is using insecure protocols.
You could see that people were running IMAP, HTTP, POP3, and other insecure protocols.

Protocol Selection
Your goal should always be to use a secure protocol that uses encryption to protect all of this data sent across the network.
And if you’re not able to use one of these secure protocols, you would be better off not using that application at all.
Application | Insecure Protocol | Secure Protocol |
Remote Console | Telnet | SSH |
Web Browsing | HTTP | HTTPS |
Email Client Access | IMAP | IMAPS |
File Transfer | FTP | SFTP |
Port Selection
Some protocols use different port numbers to distinguish between secure and insecure versions.
For instance, HTTP typically uses port 80 (unencrypted), while HTTPS uses port 443 (encrypted).
However, port numbers alone don't guarantee encryption:
Verify the server’s settings and perform a packet capture to confirm whether the traffic is actually encrypted.
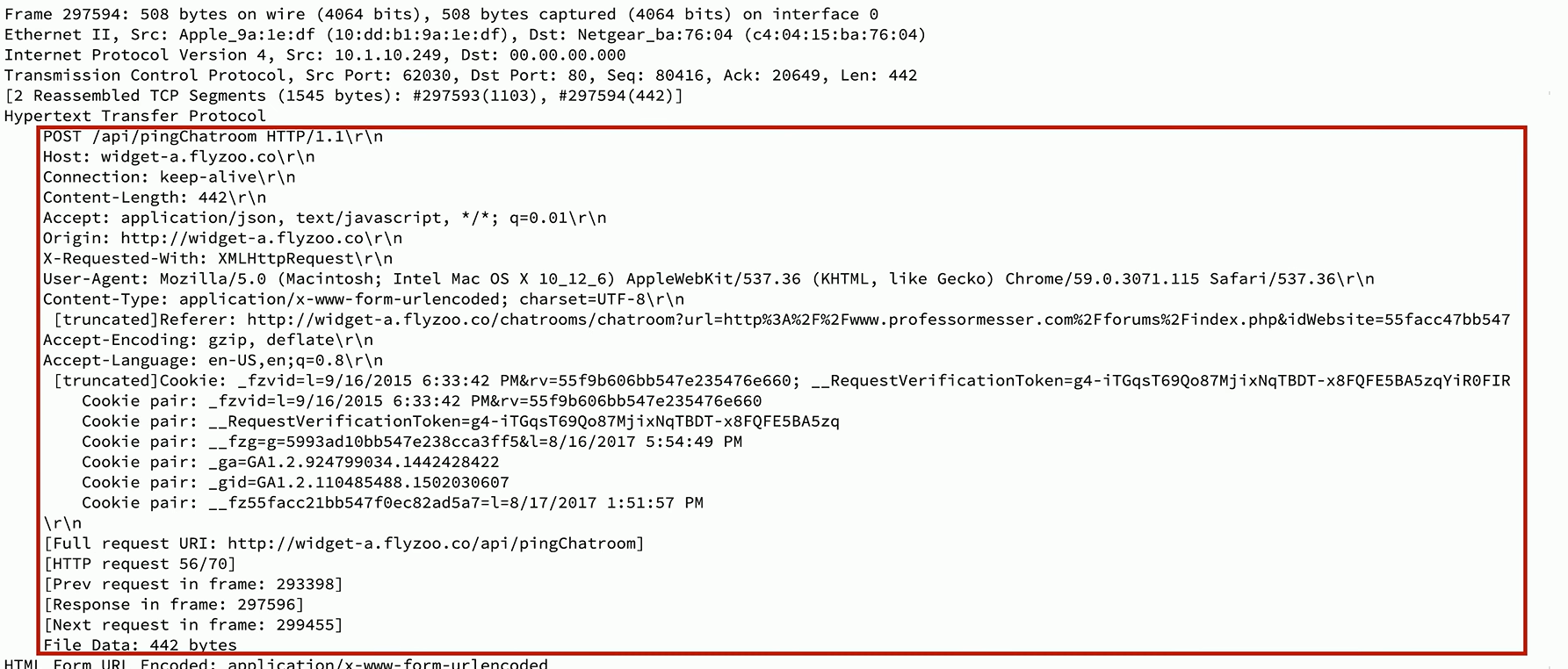
Packet Capture Example
In this example, the destination port for this website traffic is port 80, which by default would be HTTP.
And if we look at the packet capture itself, we can see that the hypertext transfer protocol itself is all in the clear and easily readable in the packet capture.
Transport Method
Ensure traffic is encrypted regardless of the application, you can use methods like WPA3 on wireless networks or VPNs.
WPA3 encrypts all wireless data at the access point level.
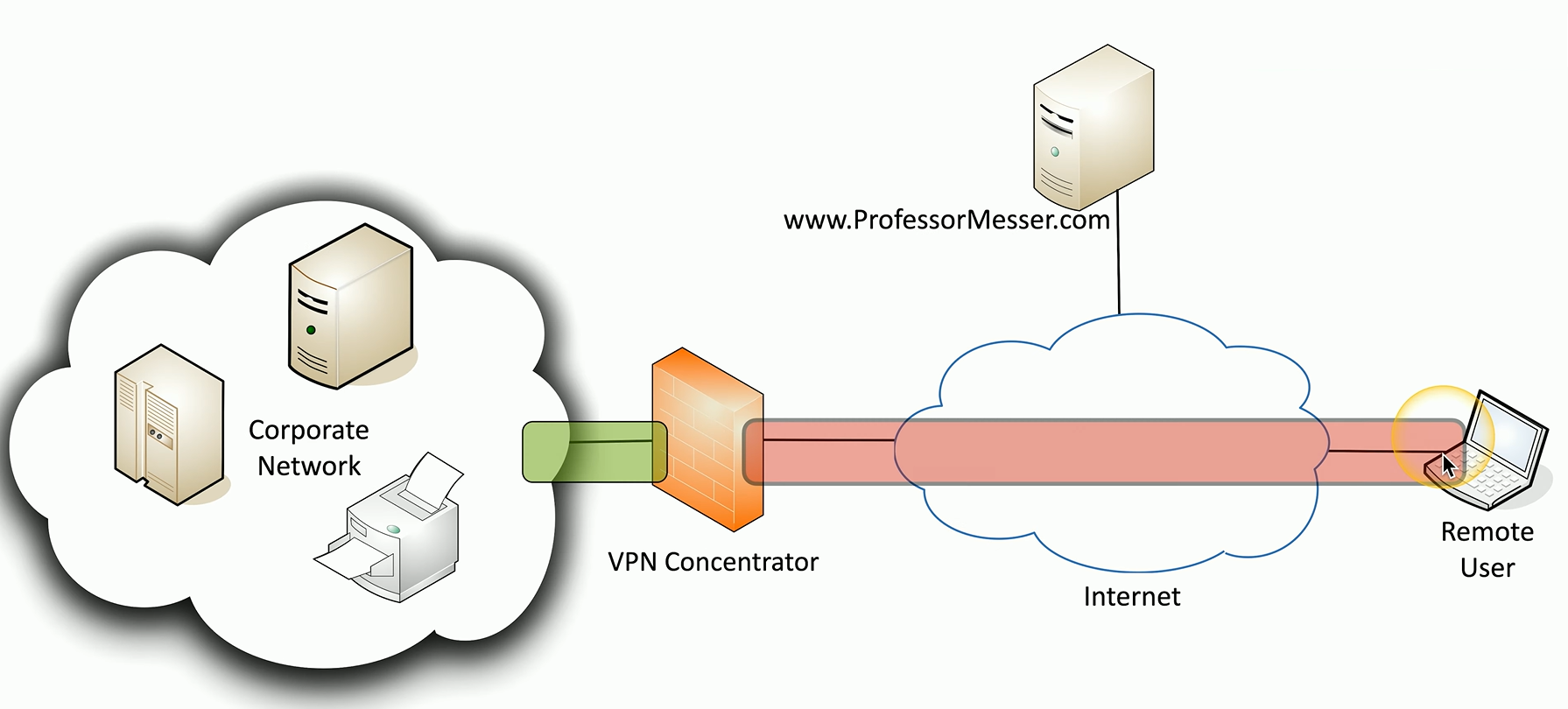
A VPN creates an encrypted tunnel between your device and a VPN concentrator, protecting all data in transit until it’s decrypted at the endpoint.
VPN Tunnel
Although this does provide an encrypted tunnel where all traffic sent over this link will be encrypted, it may require the installation of additional software on your device.
And you may need to install your own VPN concentrator or purchase access to a third-party VPN service.