4.5 Identity and Access Management
1/15
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
16 Terms
Identity & Access Management (IAM)
Ensures that the right users have appropriate access to applications and data across various systems and locations.
Applications may run on desktops, laptops, or mobile devices
Data can reside locally, in data centers, or in the cloud.
Different types of users—employees, vendors, contractors, or customers—require different permissions.
Manages these permissions securely, granting access only when and where it’s needed.
IAM Start
Starts when a user requests access and ends when that access is revoked, such as during onboarding and offboarding.
Permissions adjusted as needed over time.
Handles access control through authentication and authorization, typically using usernames, passwords, or other factors.
Also involves logging and monitoring all access for identity governance, which is essential both for security best practices and regulatory compliance.
Provisioning/De-Provisioning User Accounts
A core IAM process that begins with creating a user account and ends with its deactivation, typically during onboarding and offboarding.
Also applies when users change roles or departments.
User information includes names, attributes, group permissions, and application access rights.
Proper provisioning ensures users receive only the permissions necessary for their roles, preventing excessive access ( administrator rights)
Permission Assignments
A key goal of IAM is to assign users only the permissions necessary for their job and no more.
Many organizations use mandatory access control, where users gain permissions by belonging to specific groups, like an email group for email access.
Documents and files a user creates are private to them, preventing others who use the same device from accessing them
Users also have limited access to the device’s core operating system, protecting it from unauthorized changes by users or malware.
Identity Proofing
A crucial part of IAM that verifies a user’s true identity before granting access.
This process, called resolution (verify that a user really is who they say they are), ensures that permissions aren’t assigned to unauthorized individuals.
Users must provide something only they know, like a password, or answer security questions.
Attestation involves further verification, sometimes requiring government-issued documents or an in-person meeting.
Automated methods may also check credit reports or ask questions about personal history to confirm identity.
Gaining Access
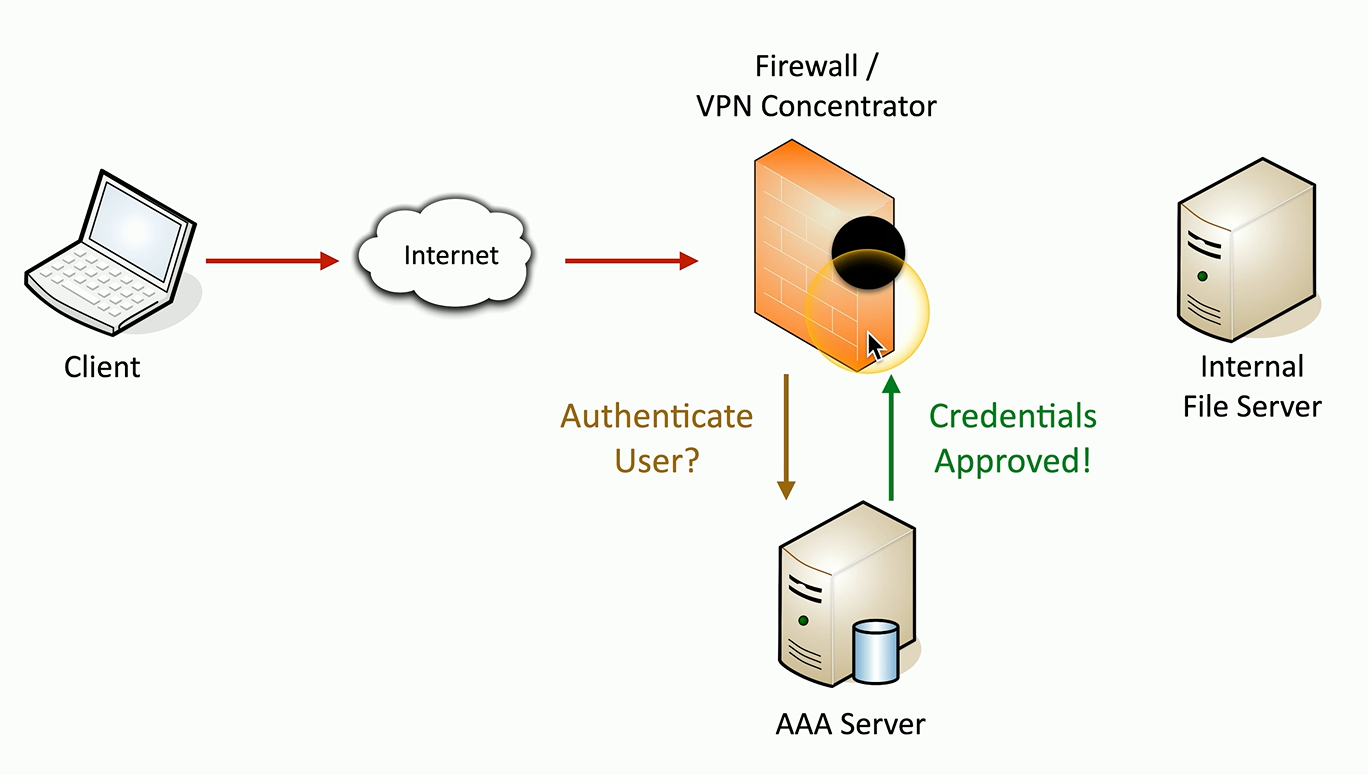
When a user needs to gain access to a resource on the network, they need to provide some type of authentication.
This usually begins with the client sending information into a central point that can be used for authentication.
This might be on a VPN concentrator or logging into an Active Directory infrastructure.
The user will provide authentication details, such as a username and password
And there’s usually a centralized authentication server that will be used to validate that information.
If that login information is correct, the authentication server will send back a notice saying that those credentials have been approved, and the user is then able to gain access to that resource.
Single Sign-on (SSO)
Allows a user to log in once and gain access to all needed resources across the network.
Access typically lasts for a set period, such as 24 hours, after which the user must authenticate again for continued access
The authorization system must support this unified authentication process.
Lightweight Directory Access Protocol (LDAP)
A standardized protocol used to access and manage large directories of data on a network.
Based on the X.500 specification developed by the International Telecommunications Union (ITU).
Evolved from the original Directory Access Protocol (DAP), which operated over the OSI protocol, to a lighter protocol compatible with various operating systems.
Commonly used to query and update directory services like Windows Active Directory, Apple OpenDirectory, and Novell eDirectory.
X.500
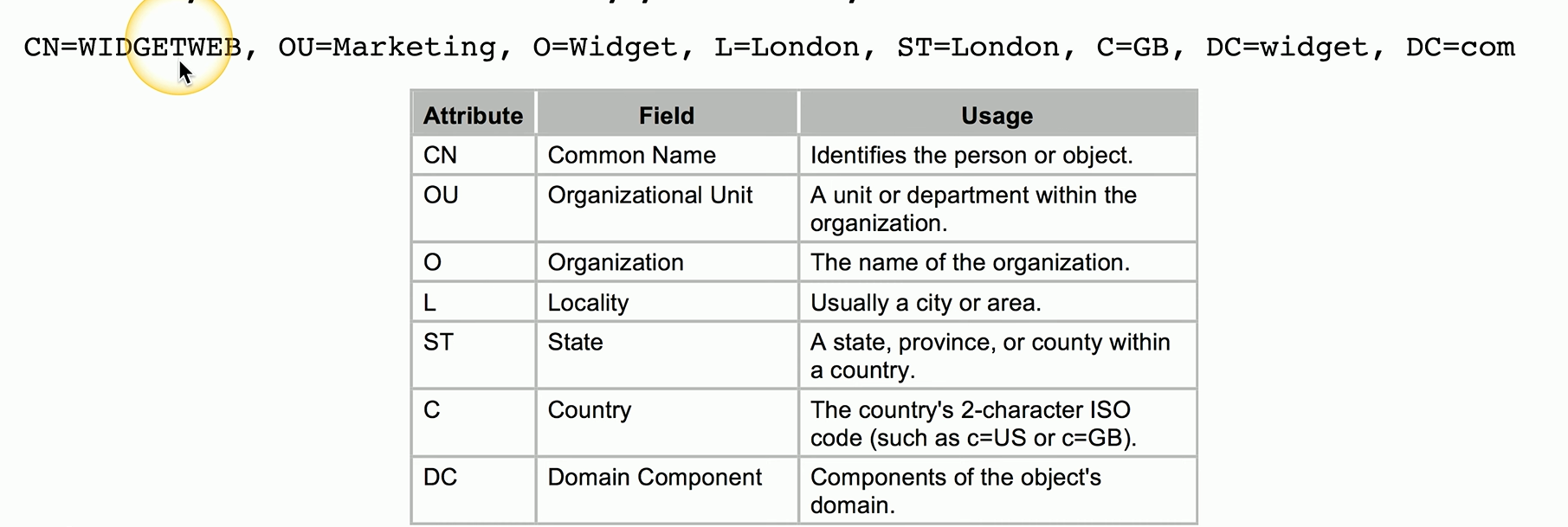
If you ever work with LDAP, you’ll see a very standard format for listing out what’s called distinguished names in X.500.
And it starts with an attribute, an equal sign, and the value of that attribute.
Most specific attribute is listed first
This may be similar to the way you already think
For example, CN, which stands for Common Name, refers to an individual device.
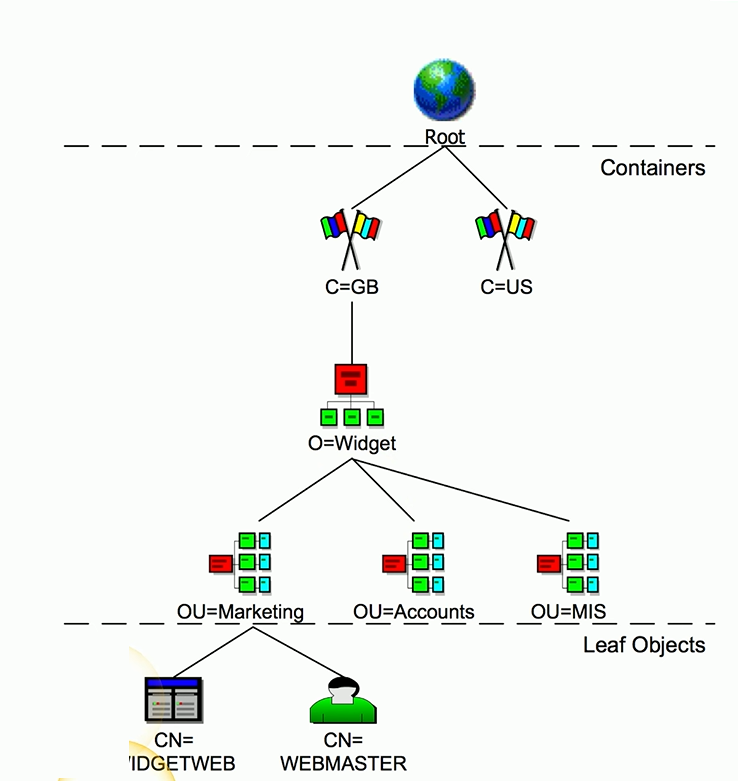
X.500 Directory Information Tree
Allows you to build a tree where you can organize all of the different devices, users, and other components on your network.
These container objects could be
The country where these objects are located, an organization within that country, different organizational units or departments, and even individual devices within that department.
Each of these individual components in the tree are referred to as leaf objects.
Users, computers, printers, files
Security Assertion Markup Language (SAML)
A standard protocol for authentication and authorization that lets users authenticate through a third-party database instead of maintaining their own user database.
Was not originally designed for mobile devices, which presents challenges today as people frequently use multiple mobile devices simultaneously.
SAML Authentication Flow
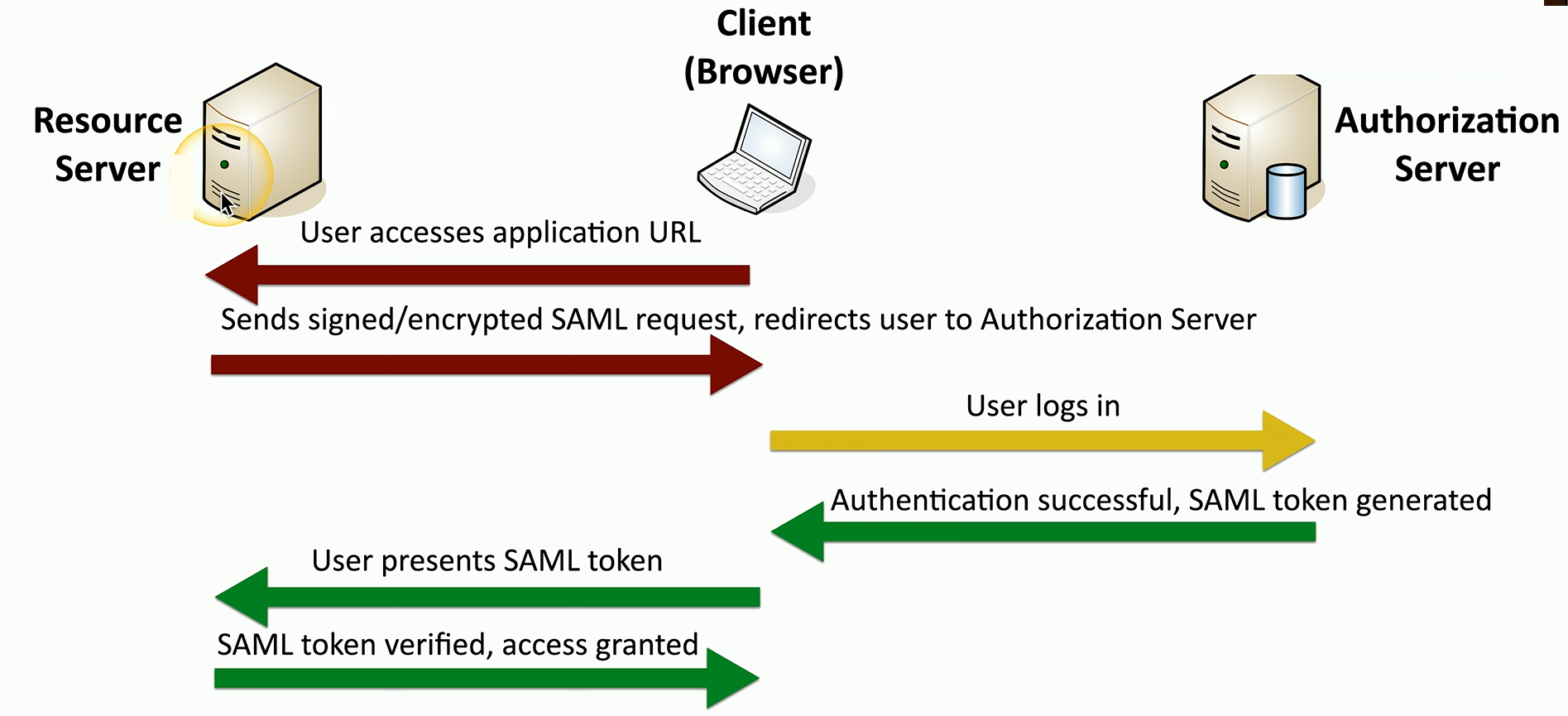
A basic SAML process involves three different devices.
One would be the device you’re using
There’s your resource server on the network.
Authorization server.
This process starts on the client where the client wants to access a URL on the resource server.
Since this user is not logged in, the resource server sends an encrypted SAML request and redirects that to the authorization server.
The user then provides user credentials to be able to gain access to that resource, and the authorization server checks those credentials, approves that the credentials were correct, and creates a SAML token.
The client now has a copy of this token that was generated by the authorization server
Now they only need to present the SAML token to the resource server to then gain access to the resource and the application that they want to use.
OAuth
An authorization framework designed for modern, mobile systems.
Allows users to log in to one system using credentials from another, like using Google or Apple login to access a smartphone game.
Developed by major tech companies, enables seamless access across different platforms and devices.
Handles authorization but not authentication, it’s often paired with OpenID to provide both authentication and authorization together.
OAuth Example
Say, you want to visit a site like eBay. Because this website allows financial transactions, the owners want you to create an account.
You can make an account on their system, but this forces you to provide your billing information, remember yet another password and other such annoyances.
Instead, you can log on using your Google account.
When prompted to authenticate, you input your credentials in a pop-up from a server owned by Google, not eBay.
Google sends you an "OAuth-token": a cookie containing an encrypted message saying that Google is SURE you are who you say you are.
The pop-up closes and the eBay-website collects the token, checks it and provides access.
At the same time, through a separate channel, Google provides access to your billing information (if you opted-in, of course).
Federation
Enables users to access resources across different systems or organizations using a single set of credentials.
The level of trust between parties is carefully defined to securely share access across these networks.
Interoperability
Can work together effectively.
Sometimes this decision depends on existing resources—for example, a VPN concentrator that supports LDAP authentication pairs well with an existing Active Directory server.