Week 2 - Basic Notations and Methods
1/26
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
27 Terms
What is an asset in cybersecurity?
An object of value that needs to be protected.
What is a threat?
A potential violation of a security property.
An action which causes harm.
What is a vulnerability?
Weaknesses in a system that can be exploited by threats to cause harm.
What are security controls?
Measures put in place to mitigate risk.
What is a risk?
Likelihood of a threat exploiting a vulnerability.
Value
Importance of the asset
What is a security requirement?
A formal statement defining how a system should be protected.
Standards of security that need to be adhered to.
what are security measures?
Measures/actions taken to protect against threats
what are the core security properties?
confidentiality
privacy
integrity
availability
access control
authentication
authorization
Confidentiality
preventing unauthorised disclosure of info
Privacy
protection of personal data
integrity
preventing unauthorised modification of data or services
availability
prevent unorthorised withholding of info
Access control
preventing unauthorised users from accessing resources
authentication
verifying the identity of a user
authorization
prevent users violating their privileges
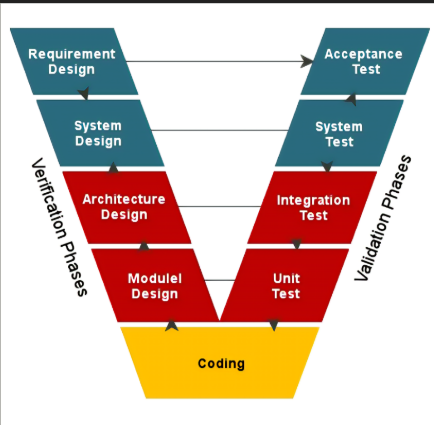
what is the V-Model?
a development model showing progression from specification to validation and verification
describe the 5 phases in V model
What does CyBoK say about modern cybercrime?
it is a commoditized ecosystem with specialized actors.
quote
what is an attack tree
a structured diagram used to model how a system can be attacked.
Root node: The attacker’s main goal (e.g., "Steal user data").
Branches and leaf nodes: Steps or sub-goals needed to achieve the main goal.
Logic: Uses AND/OR relationships to show how combinations of actions lead to the attack.
It helps identify potential vulnerabilities and guide security testing or threat mitigation.
security through the development cycle
requirements and use cases
design
test plans
code
test results
field feedback
how is security tested at the ‘requirements and use cases’ stage
abuse cases
security requirements
risk analysis
how is security tested at the ‘design’ stage
risk analysis
external review
how is security tested at the ‘test plan’ stage
risk-based security tests
how is security tested at the ‘code’ stage
static analysis
how is security tested at the ‘test results’ stage
risk analysis
penetration testing
how is security tested at the ‘field feedback’ stage
security breaks