Chapter 9: Internal control
1/18
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
19 Terms
Components of a system of internal control CRIME
Control activities
Risk assessment
The information system and communication
The entity's process to monitor the system of internal control
Control environment
Internal controls in smaller entities
Smaller entities are likely to have less segregation of duties due to limited numbers of staff.
Management override of controls is likely to be an increased risk as a result of the close involvement of directors/owners.
Inherent limitations of internal control systems
Deliberate circumvention of processes by employees
Management override of controls
Unforeseen circumstances where no control exists
Cost of control > benefit
Human error
Use of systems of internal control by auditors
Assess the adequacy of the accounting system as a basis for preparing the accounts
Identify the types of potential misstatements that could occur in the accounts
Consider factors that affect the risk of misstatements
Design appropriate audit procedures
Techniques
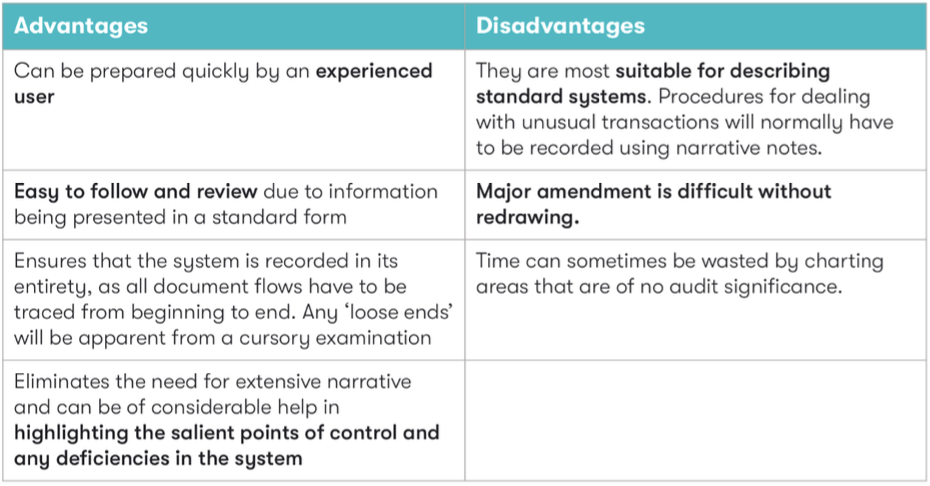
Flowcharts
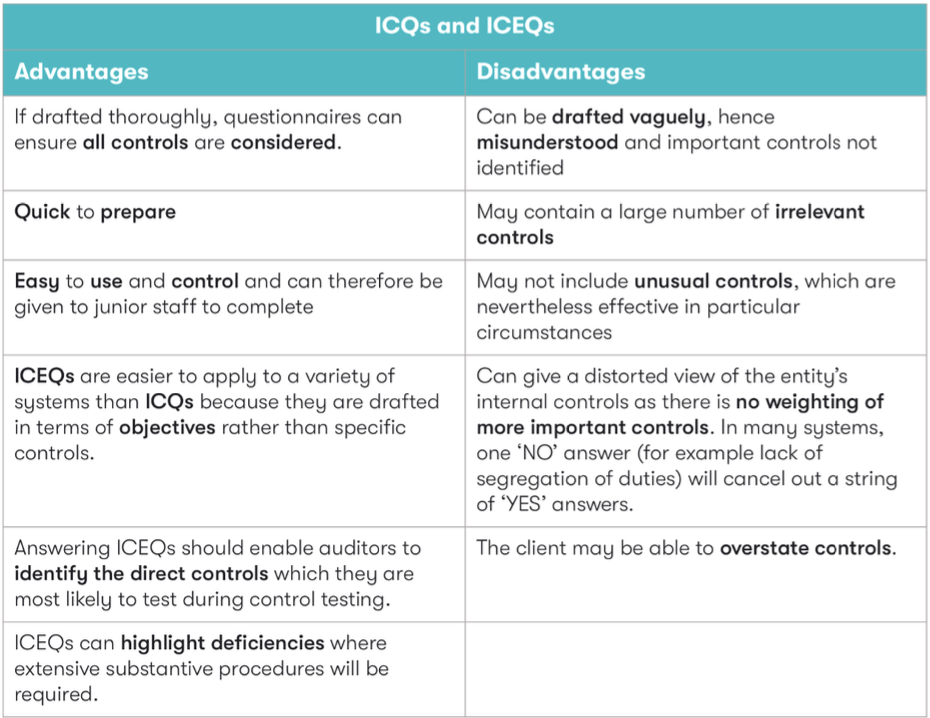
Internal control questionnaires (ICQs)
Narrative notes
Internal control evaluation questionnaires (ICEQs)
Narrative notes
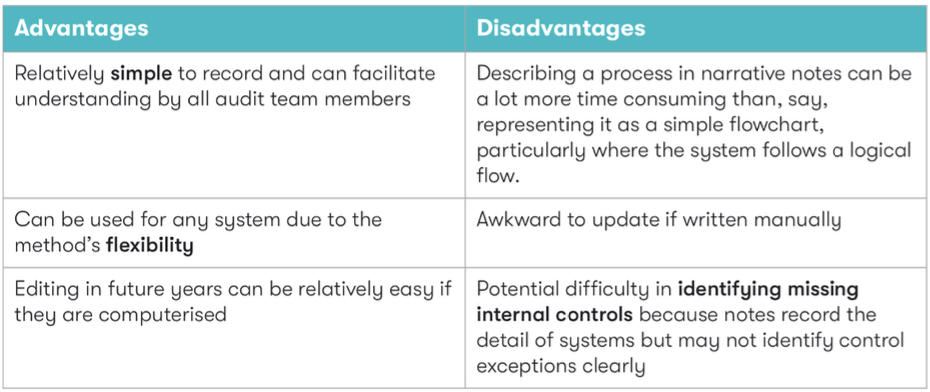
Flowcharts
Internal control questionnaires (ICQs)
(a) They comprise a list of questions designed to determine whether desirable controls are present for each major transaction cycle (for example. sales, purchases).
(b) They are formulated so that there is one list of questions to cover each of the major transaction cycles.
Internal control evaluation questionnaires (ICEQs)
Internal control evaluation questionnaires (ICEQs) are slightly more robust in that they ask questions that concentrate on the significant errors or omissions that could occur at each phase of the appropriate cycle if controls are weak. This, in turn, enables the auditor to elicit the controls which exist.
ICQs and ICEQs
Control activities
• The policies and procedures that help ensure that management directives are carried out
The categories most relevant ot an audit are:
• Performance reviews (đơn hàng không được chấp nhận trừ khi được xem trươcs điểm tín dụng)
• Information processing (mọi chứng từ hoá đơn đều được hỗ trợ và có thể tham chiếu đến nhau)
• Physical controls
• Segregation of duties (việc xử lý đơn hàng, ghi nhận doanh thu có được thực hiện bởi nhiều người khác nhau không)
athorization (đơn hàng được lập theo danh sách giá và điều khoản hợp đồng đã được phê duyệt)
Test of control
Inspection of the document (pick a random sample to test)
Inquiry (interview)
Observation
Reperformance (reconciliation)
Examination of evidence of management views
Testing on a computerized system
Control environment
• Governance and management functions
• Attitudes, awareness and actions of management
• Sets the tone by creating a culture of honest and ethical behaviour
• Provides an appropriate foundation for the other components of internal control
The entity's risk assessment process
• How management identifies risks and decides upon actions to manage them
The entity's process to monitor the system of internal control
• Assess the design and operation of controls over time
• Ongoing monitoring is part of regular management activity
• Separate monitoring may be performed by the internal audit function
The information system and communication
• Consists of infrastructure, software, people, procedures and data
• The related accounting records, supporting information and specific accounts in the financial statements that are used to record, process and report transactions
Internal controls in the IT environment
• General TI controls
• Information processing controls
General IT controls
Development of computer applications
Examples
• Standards over systems design, programming and documentation
• Full testing procedures using test data
• Approval by computer users and management
• Segregation of duties so that those responsible for design are not responsible for testing
• Installation procedures so that data is not corrupted in transition
• Training of staff in new procedures and availability of adequate documentation
Prevention or detection of unauthorised changes to programs
• Segregation of duties
• Full records of program changes
• Password protection of programs so that access is limited to computer operations staff
• Restricted access to central computer by locked doors, keypads
• Maintenance of programs logs
• Virus checks on software: use of anti-virus software and policy prohibiting use of non- authorised programs or files
• Back-up copies of programs being taken a n d stored in other locations
• Control copies of programs being preserved and regularly compared with actual programs
• Stricter controls over certain programs (utility programs) by use of read-only memory
Testing and documentation of program changes
• Documentation standards
• Approval of changes by computer users and management
• Training of staff using programs
Controls to prevent wrong programs or files being used
• Operation controls over programs
• Libraries of programs
• Proper job scheduling
Controls to prevent unauthorised amendments to data files
• Password protection
• Restricted access to authorised users only
Controls to ensure continuity of operation
• Storing extra copies of programs and data files off-site
• Protection of equipment against fire and other hazards
• Back-up power sources
• Disaster recovery procedures eg availability of back-up computer facilities
• Maintenance agreements and insurance
Information processing controls
Controls over input: completeness
• Manual or programmed agreement of control totals
• Document counts
• One-for-one checking of processed output to source documents
• Programmed matching of input to an expected input control file
• Procedures over resubmission of rejected controls
Controls over input: accuracy
Programs to check data fields (for example value, reference number, date) on input transactions for plausibility:
• Digit verification (eg reference numbers are as expected)
• Reasonableness test (eg sales tax to total value)
• Existence checks (eg customer name)
• Character checks (no unexpected characters used in reference)
• Necessary information (no transaction passed with gaps)
• Permitted range (no transaction processed over a certain value)
Manual scrutiny of output and reconciliation to source
Agreement of control totals (manual/programmed)
Controls over input: authorisation
Manual checks to ensure information input was:
• Authorised
• Input by authorised personnel
Controls over processing
• Similar controls to input must be in place when input is completed, for example batch reconciliations
• Screen warnings can prevent people logging out before processing is complete
Controls over master files and standing data
• One-for-one checking
• Cyclical reviews of all master files and standing data
• Record counts (number of documents processed) and hash totals (for example, the total of all the payroll numbers) used when master files are used to ensure no deletions
• Controls over the deletion of accounts that have no current balance