Comp sci unit 3 terms
1/114
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
115 Terms
TCP
Transmission control protocol
Communication standard that enables application programs and computing devices to successfully exchange data packets over networks
For email/messaging, file transfers, web browsing
TCP connections:
Requires an established connection before transmitting data
Can sequence data
Can retransmit data if packets fail to arrive
Uses error-checking to guarantee that data arrives in intended state
Don’t support delivering continuous data
Can be slower than UDP
UDP
User datagram protocol
“Connectionless” communications standard that enables application programs and computing devices to exchange packets of data over networks
For: live streaming, online gaming, video chat
UDP connections:
Require no connection to start and end a data transfer
Cannot sequence or arrange data
Cannot retransmit data if packets fail to arrive
Use minimal error-checking that may not prevent all errors
Support delivering continuous data
Can be faster than TCP
IP address
Internet protocol address
Numerical label assigned to identify a device
Divided into network and host portion
Class A
Mask - 255.0.0.0
Addresses - 16,777,216
First octet - 0-127
/8
Class B
Mask - 255.0.0.0
Addresses - 65,536
First octet - 128-191
/16
Class C
Mask - 255.255.255.0
Addresses - 256
First octet - 192-223
/24
Subnet mask addresses
For each subnet mask, usable host IP addresses is less by 2
First address for network
Last address for broadcast (used to send data to all other hosts on subnet)
IPv4
uses 32-bit addresses
Represented by four 8-bit fields (octets)
Separated by periods
IPv6
Uses 128-bit addresses
Represented by eight 16-bit hexadecimal fields
Separated by colons
Public IP
Identifies you to the wider internet so that all the info you’re searching for can find you
Private IP
Used within a private network to connect securely to other devices within the same network
MAC address
Media access control address
Unique identifier assigned to a network interface controller to identify physical hardware in a network
MAC vs IP
MAC: designates the physical location of a device
IP: signifies the device’s global or internet-accessible identity
Subnet
Network inside a network
Makes networks more efficient
Data can travel a shorter distance without passing through unnecessary routers
Subnet mask
Like an IP address, but only for internal usage within a network
Used by routers to route data packets to the right place
Not indicated within data packets traversing the internet
Collision domain
Section of a network where packet collisions can occur
Collisions occur when 2 or more data packets try to occupy the same network channel at the same time, which can lead to packet loss
Problem when using hubs instead of switches
Network segmentation
Used to compartmentalise subnets to deliver unique security controls and services to each subnet
Hub
Like a router but doesn’t route frames intelligently
When it receives a signal, it will repeat it out on all connections except the one where it received the signal from
Physical (OSI) layer
Switch
Prevent collision by buffering Ethernet frames
Receives incoming data packets and redirect them to the destination on a LAN
Operates using MAC addresses to switch data on the ethernet layer
Internet (DoD) and data link (OSI) layer
Port number
Way to direct TCP/UDP connection to a specific process
Serve to identify the purpose of a connection
Come after an IP address, separated by a colon
OSI model layers
physical
data link
network
transport
session
presentation
application
Physical layer
Responsible for the physical cable or wireless connection between network nodes
Protocols: Ethernet, DSL, fibre optic
Data link layer
Establishes and terminates a connection between two physically connected nodes on a network
Protocols: LCP, NCP
LLC
Logical link control
Identifies network protocols, performs error checking and synchronises frames
MAC
Uses MAC addresses to connect devices and define permissions to transmit and receive data
Network layer
Breaks up segments into network packets and reassembles them on the receiving end
Routes packets by discovering the best path across a physical network
Uses network addresses (IP) to route packets to a destination node
Layer 3 routing
Use IP address to decide where to forward packets through a hardware switch
Switch/router accepts a packet, looks at its destination address and makes a routing decision
Transport layer
Takes data transferred in the session layer and breaks it into ‘segments’ on the transmitting end
Responsible for reassembling the segments on the receiving end, turning it back into data that can be used
Transport layer carries out…
Flow control - sending data at a rate that matches the connection speed of the receiving device
Error control - checking if data was received correctly and if not, requesting it again
Session layer
Creates communication channels (sessions) between devices
Responsible for opening sessions, ensuring they remain open and functional while data is being transferred
Responsible for closing them when communication ends
Session layer checkpoints
Allows devices to resume data transfer from the last checkpoint if session is interrupted
Presentation layer
Prepares data for the application layer
Defines how 2 devices should encode, encrypt and compress data so it’s received correctly
Takes data transmitted by the application layer and prepares it for transmission over the session layer
Protocols: TLS, SSL
Application layer
Used by end-user software
Provides protocols that allow software to send and receive info and present meaningful data to users
Protocols: HTTP, FTP, SMTP
OSI model
Open systems interconnection model
Based on the concept of splitting up a communication system into 7 abstract layers, with each layer dependent upon the last
Data passes through each layer in sequence
DoD TCP/IP model
Department of defence transmission control protocol/internet protocol model
Condensed version of OSI model
Basis for the current internet
Packets
Basic unit of communication between source and destination in a network
Data sent through the network is broken into packets that are recombined by the destination devices
Dividing data allows the network to easily transmit, route, keep track of and retransmit lost or corrupted data
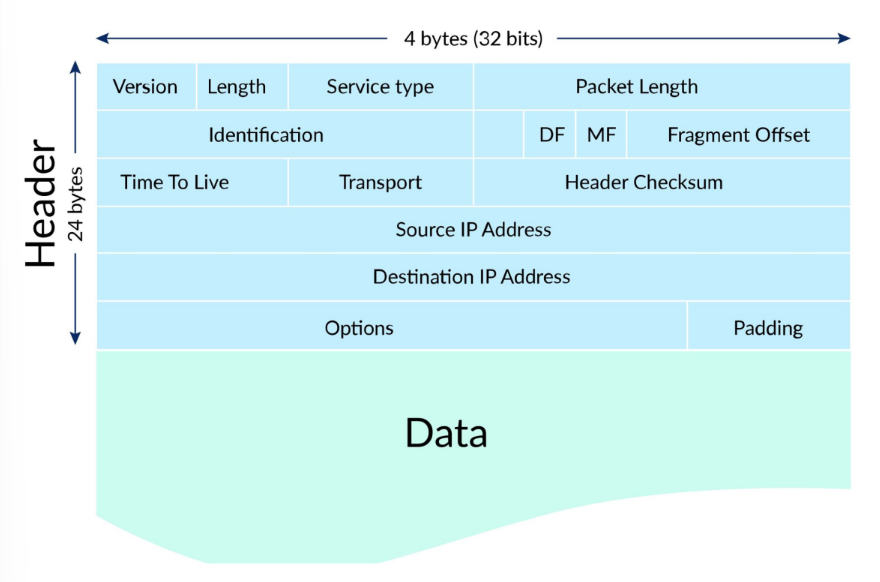
IPv4 packets
Contains header (20/24 bytes long) and data (variable length)
Header - IP addresses of source and destination, other fields that help route the packet
Data - actual content (e.g., string of letters, part of webpage)
Data at TCP/IP model
Encapsulates/modifies data according to a 4 layer procedure
Data is sent out through the layers, converted into packets and routed to their destination
Packets are received and reassembled by the destination device into data usable by apps
Data at application layer
Unencapsulated, not modified
Sends data to the transport layer
Encapsulation details are mostly hidden from the user, process and software developer through abstraction
Segments at transport layer
Protocols start the process
Data is wrapped with a header which contains a source and destination port, checksum and session establishment
TCP - segment
UDP - datagram
Checksum
Value that represents the number of bits in the segment
Used to detect data corruption
Packets at internet layer
Data wrapped in ‘IP envelope’ which contains source and destination IP addresses, info on protocol type (TCP) and version (v4/v6) and time to live (TTL)
TTL
Time to live
Amount of time (hops) that a packet is set to exist inside a network before being discarded by a router
Frames at network layer
Packet wrapped in ethernet frame which contains info on source and destination MAC addresses, Frame Check Sequence (FCS) for error correction and header and footer that mark the start and end of frame
Data at different layers of OSI
Encapsulated as data -> segments -> packets -> frames
Physical layer: data is known as bits - the raw ‘bit stream’ of 1s and 0s over the network, transmitted as electrical or wireless signals
DoD application protocols
SMTP, FTP, HTTP, HTTPS, DHCP, DNS, PING
DoD transport protocols
TCP, UDP
DoD internet protocols
IPv4, IPv6, ARP
DoD network protocols
Ethernet (802.3), Wi-Fi (802.11)
Transmission media
Provides a physical path between a transmitter and receiver
Channel through which data is sent from one place to another
Network (DoD) and physical (OSI) layer
LAN
Local area network
Collection of devices connected together in one physical location
WLAN
Wireless local area network
Group of co-located devices that form a network based on radio transmissions
WAN
Wide area network
Collection of LANs or other networks that communicate with each other
Problems from unauthorised network access
Data breaches, which can also lead to ransomware.
Identity theft - access to one’s personal details through their personal network can give hackers substantial content to steal the identity of the person whose info they are accessing
Disruptions - shutting down systems or making it more difficult to access data
Firewall
Acts as a gatekeeper for network traffic, filtering and controlling access to prevent unauthorised access and protect against cyberattacks
Examines incoming and outgoing data based on predefined security rules, allowing legit traffic while blocking malicious or unwanted connections
Transport or internet (DoD) and network or transport (OSI) layer
Packet filtering
Involves inspecting incoming and outgoing data packets based on rules
Can be based on IP addresses, port numbers, and protocols
Can block traffic that doesn't match the established rules, preventing unauthorised access
Stateful inspection
Enhances packet filtering by keeping track of active connections and the state of the packets within a session
Allows the firewall to make more informed decisions about which packets to allow or block based on the context of the connection
Proxy services
Act as intermediaries between the client and the destination, inspecting the content before it's allowed onto the network
Can help prevent malicious content from entering the network
OSI vs TCP/IP model
Similarities - describe how info is transmitted between 2 devices, use encapsulation where data is packaged into headers and trailers that contain info about the data and how it should be handled
OSI - delivery is guaranteed
TCP/IP - more reliable
DoD layers
Application
Transport
Internet
Network
Application layer role (DoD)
Provides network services directly to user applications
Transport layer role (DoD)
Ensures reliable data transfer between devices, manages error detection and correction, flow control
Internet layer role (DoD)
Determines the best path for data to travel across networks, handles logical addressing and routing
Network layer role (DoD)
Manages the physical transmission of data over network media
Router
Determines the best path for data packets to travel across an internetwork
Utilises routing tables and protocols to make routing decisions
Internet (DoD) and network (OSI) layer
WAP
Wireless Access Point
Allows wireless devices to connect to a wired network
Acts as a bridge between the wired network and wireless clients
Network (DoD) and physical and data link (OSI) layer
Bandwidth
The maximum rate at which data can be transferred through a network
Layer 2 switching
Uses MAC address table that identifies the MAC address of the connected device and port number
Enables the switch to direct frames towards the correct destination
TCP vs UDP
TCP - reliable, provides extensive error-checking mechanisms, sequencing to ensure packets arrive in order
UDP - no acknowledgement segment, faster, simpler, more efficient, no retransmission of lost packets
TCP packet architecture
20-60 byte variable length header
Heavy-weight
Byte stream connection type
Low overhead (higher than UDP)
UDP packet architecture
8 byte fixed length header
Lightweight
Message stream connection type
Very low overhead
Subnetting
Process of dividing a large network into smaller networks
Saves IP addresses, keeps networks faster and protects sensitive data
Contains broadcast domains to minimise bandwidth consumption
Default gateway
Node that forwards the packet to other networks when there’s no routing info about the destination
DNS
Domain name system
Translates human-readable domain names into machine-readable IP addresses, enabling internet connection
Gateway
Connects 2 networks with different transmission protocols
Physical network gateway includes network interface cards (NICs), inputs and outputs and software for translating protocols
Internet (DoD) and network (OSI) layer
Network topology
Arrangement of different elements in a computer network
e.g., bus, ring, star, point to point
Network design
Efficient designs reduce the number of hops and bottlenecks, improving data flow across the network
Ping
Helps check the reachability of a server/IP address
Measures the round-trip time for messages sent from computer to destination and back
Verifies whether a device/server is active and responsive
Traceroute
Traces the path that packets take from computer to a remote server/host
Provides a detailed map of the route the data packets follow across the network
Shows how long it takes to travel from one hop (router/intermediary device) to the next
Malware
Any type of malicious software designed to harm or exploit any programmable device, service or network
Malware effects
Costs people and businesses money and can lead to data loss, identity theft and other serious problems
Ransomware
Locks up or encrypts files so user can’t access them, requiring a ransom to restore access to the files
Virus
Programs or code that self-replicates or copies itself in order to spread to other devices or areas of the network
Rootkit
Tool or set of tools used by an attacker in order to compromise a system, gain the highest level of privilege, and then hide their activity
Spyware
Enters a user’s computer, gathers data from the device and user and sends it to third parties without their consent
Backdoors
Any method by which authorised and unauthorised users are able to get around normal security measures and gain high level user access on a computer system, network or software application
Phishing
Way attackers trick users into giving them personal info, usually through fraudulent emails or text messages pretending to be from a large, trusted and known org
Reliance on software
Software systems, the algorithms that drive them and the the hardware devices they operates on are more powerful and capable than ever
Social networking
Computer networks have been used to socialise, chat and share information
Cyber safety
Refers to the ways we protect ourselves, data and others in the digital world
Cyber safety importance
Proliferation of cyber crime, ease of accessing people’s private data and overreach of governments
Internet information
Large volumes of info (which may be unsupported, unverifiable, misleading or incorrect) available through the internet
Class
Blueprint for an object
Object
New instance of a class
Attributes
Data contained within an object
Methods
Functions callable on an object or attribute
Instantiation
To create an “instance” of a class (an instance is called an object)
Using methods
Method or operation is a function that can only act on a specific class/object. Use dot notation to access an object’s methods or attributes.