CCNA 3 Module (3-5)
1/10
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
11 Terms
The IT department is reporting that a company web server is receiving an abnormally high number of web page requests from different locations simultaneously. Which type of security attack is occurring?
DDoS
What causes a buffer overflow?
attempting to write more data to a memory location than that location can hold
Which objective of secure communications is achieved by encrypting data?
confidentiality
What type of malware has the primary objective of spreading across the network?
worm
What commonly motivates cybercriminals to attack networks as compared to hactivists or state-sponsored hackers?
financial gain
Which type of hacker is motivated to protest against political and social issues?
hacktivist
What is a ping sweep?
a network scanning technique that indicates the live hosts in a range of IP addresses.
In what type of attack is a cybercriminal attempting to prevent legitimate users from accessing network services?
DoS
Which requirement of secure communications is ensured by the implementation of MD5 or SHA hash generating algorithms?
integrity
If an asymmetric algorithm uses a public key to encrypt data, what is used to decrypt it?
a private key
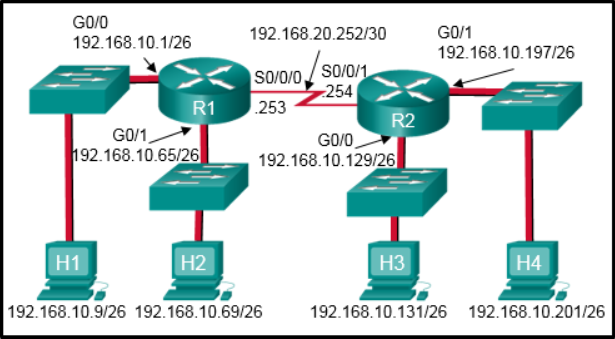
Refer to the exhibit. Which two ACLs would permit only the two LAN networks attached to R1 to access the network that connects to R2 G0/1 interface? (Choose two.)
access-list 1 permit 192.168.10.0 0.0.0.127
access-list 5 permit 192.168.10.0 0.0.0.63
access-list 5 permit 192.168.10.64 0.0.0.63