Denial of Service Attacks and Defense
1/22
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
23 Terms
A network DoS aims to take out a site with little computing work. This is done through amplification (small number of packets → big effect)
What are the two types of amplification attacks?
DoS bug
Design flaw allowing one machine to disrupt a service
DoS flood
Command bot-net to generate flood of requests
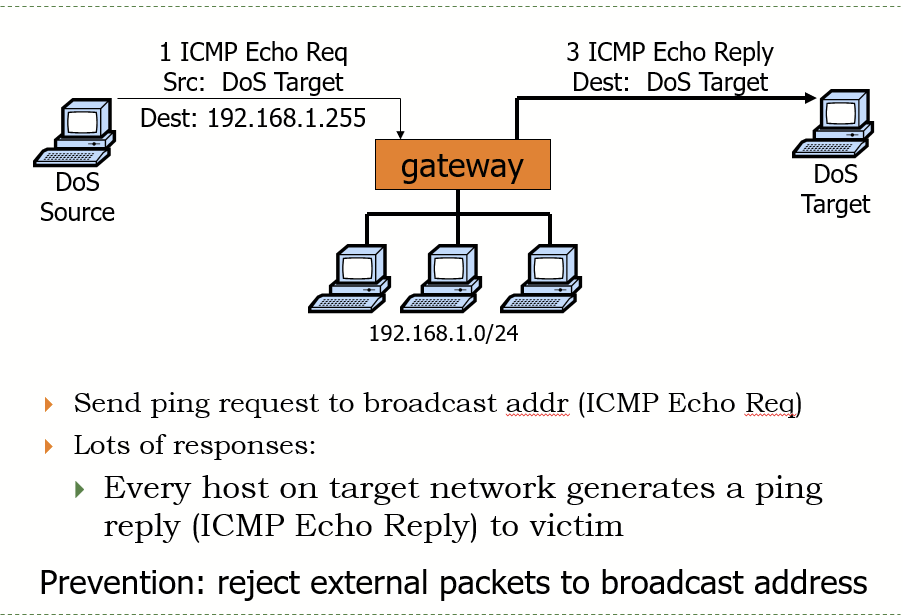
Smurf Attack
Amplification DoS Attack
Send ping request to broadcast address (ICMP requests), resulting in a bunch of echo replies to the victim
Prevention:
reject external packets to broadcast address
DNS Based Amplificiation DoS Attack
Recursion makes it ouchie
Prevention
reject DNS queries from external addresses
SYN Flood Defenses
Not an actual solution
increasing backlog queue size or decreasing timeout
Correct solution
SYN cookies: remove state from server
Small performance overhead
What is a SYNcookie?
Eliminates SYN state from server by having the server reply to SYN requests with crafted SYN-ACKS without creating a new Transmission Control Block (contains all TCP sessions)
TCB only created once client responds to cookie with a valid answer
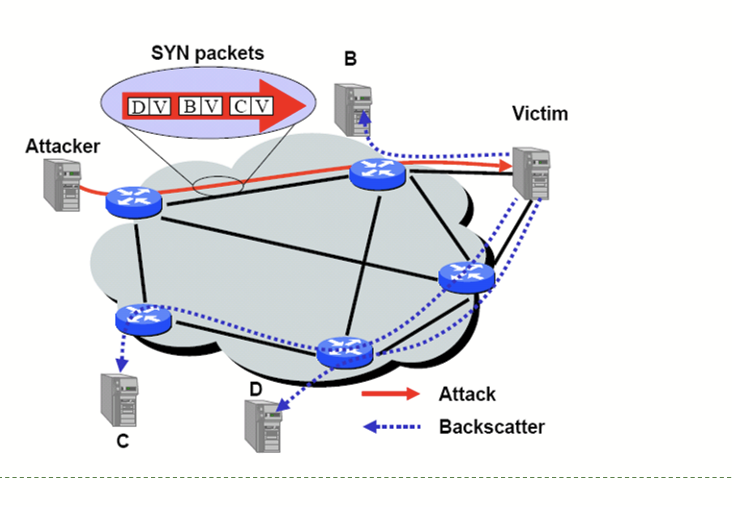
SYN floods: backscatter
SYN with forged source IP → SYN/ACK to random host
Prevent against SYN Floods (Massive Scale) with…
Google PRoject SHield and Akamai
Google Project Shield & Prolexic (Akamai)
What does it do normally?
What if we want the bot army to complete the TCP connection and send short requests?
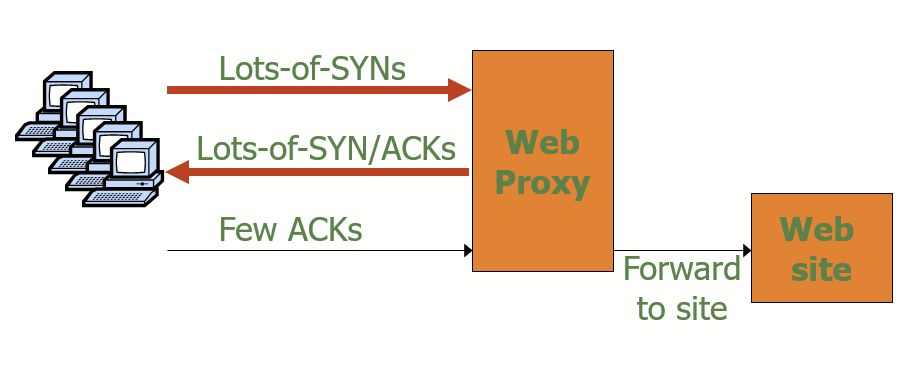
Make website accessible only via web proxy and only forward established TCP Connections to the site
In the case that the bot army completes teh TCP connection, it’ll bypass the proxy server, BUT it reveals the location of the bot zombies and the proxy can block/rate-limit bots
Con: can’t tell if it’s a bot or legitimate client
SSL/TLS Handshake
DoS Mitigation
List the Strategies
Client Puzzles
CAPTCHA
Source Identification to Block attack at source
Ingress Filtering
Traceback
DoS Mitigation: Client Puzzles
Describe its goal and its operation
Benefits and Cons as well
Goal: slow down attacker by giving it a challenge
Checking the puzzle solution should be easy
During a DoS Attack everyone must submit puzzle solution with requests (not during no attack time)
Cons
Hardness of challenge decided based on DoS attack volume
requires changes to both clients and server
hurts low CPU power legitimate clients during attack
that’s why switch to solutions that require main memory access (significantly faster)
DoS Mitigation: CAPTCHA
Describe its goal and its operation
What type of DDOS attack does it apply to?
Goal: verify connection is human
Applies to application layer DDOS
Generate CAPTCHA during attacks only
one CAPTCHA per source IP address
How does Ingress Filtering prevent spoofed IPs from making attacks?
What are some implementation issues?
ISP only forwards packets with legitimate source IPs
Implementation Issues
ALL ISPs must do this
requires global trust
Non Solution
enforce source IP at peer AS BUT transit AS can’t validate packet source IP
Describe Traceback goal, method, and assumptions
Goal
given set of attack packets, determine path to the source
How/Method
make routers record info in packets
Each router adds its own IP address to the packet and the victim reads path from packet
Problem
space in packet!
Long paths?
No extra fields in current IP format
Assumes
most routers uncompromised
attacker sends many packets
route from attacker to victim remains relatively stable
What would be a better approach to recording info in packets for traceback?
Storing one node/edge in each packet b/c usually in a DOS attack many packets are on the same path
Each router stores own address
Fixed space regardless of path length
Describe Edge Sampling (how it works)
Data fields are written to packet
Edge:
start and end IP addresses
Distance
number of hops since edge stored
Marking probability.
Write router into start address and write 0 into distance field BUT if distance == 0, write R int oend field and increment distance field
Extract info from atttack packets and build the graph rooted at the victim
Each start, end, distance tuple provides an edge
There is a number of packets you need to construct a path that you may no always meet
Edge sampling kind of takes up a lot of space, so we can reduce the size via XOR edge IP address
Store edge as start XOR end and work backwards (start XOR end) XOR end = start
When router decides to mark packet, it writes its address ‘a’ into the packet
the following router notices the distance field is zero, reads ‘a’ form the packet and XORs the value with its own address and writes teh resulting value aXORb into the packet
Bad in case of multiple attacks al mismo which is why encode parts of fragments into it as a hash me thinks
Describe Node Sampling
Less data from edge sampling and each router writes own address with probability p
Infer order by # of packets
Problems
need many packets to infer path order
Doesn’t work well if a lot of paths
No bueno if multiple attacks
most likely won’t get nodes close to attacker if it takes a long path
Where to store edge?
Store in identification field used for fragmentation b/c fragmentation rare
Break it into chunks and store start XOR end
Hash-based IP Traceback Concept
Main idea: store path state on router
router logs forwarded packets for a period of time
Store packet digest in a table
Digest table uses bloom filter or something?
Reconstruct path by querying routers in reverse path flooding manner
Pro:
trace single packet
Con:
storage and access time overheads
Tf is a Bloom FIlter?
Technique that stores digests
For each packet arrived
use K different function to compute k independent n bit digests
Set corresponding bits in the bits digest table
If bit= 0, packet not stored in the table
if all bits are 1 → likely packet was stored or other insertions caused bits to be set
Restriction
can only store limited number of digests
Saturated filters can be swapped out for a new, empty filter
Change to a new filer → lose previous digest info
IP traceback limitations
Not effective against reflector attacks
Reflector
network component that responds to packets
response sent to victim (spoofed source IP)
Capability based defense
Concept:
receiver can specify what packets they want
How:
sender requests capability in SYN packet
Receiver responds with capability
Sender includes capability in all future packets
So Routers would only forward request packets _ packets with valid capability
capability can be revoked in case of attack
AKAMAI Web Caching Service
Uses IP tunnels to connect
If client has a lot of static content on their site, AKAMAI will stash the content at various locations and through a DNS trick, when yo uwant to connect to the web service, DNS will get the AKAMAI DNS server and look at the source IP of the query
For ex:
attacker will get redirected to AKAMAI caches when they request the website and b/c there are multiple caches, it’s not that bad
the only way to bring the website down is to bring down all of the caches
Overlay based defense mechanism
If the attacker learns the IP of the actual website, it’s still whatever b/c the caches could still be up
Downsides to AKAMAI
cost b/c outsourcing
only static content