CCNA 3 Module (3-5) Part 4
1/10
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
11 Terms
Which set of access control entries would allow all users on the 192.168.10.0/24 network to access a web server that is located at 172.17.80.1, but would not allow them to use Telnet?
access-list 103 permit tcp 192.168.10.0 0.0.0.255 host 172.17.80.1 eq 80
access-list 103 deny tcp 192.168.10.0 0.0.0.255 any eq 23
What is the term used to describe a mechanism that takes advantage of a vulnerability?
exploit
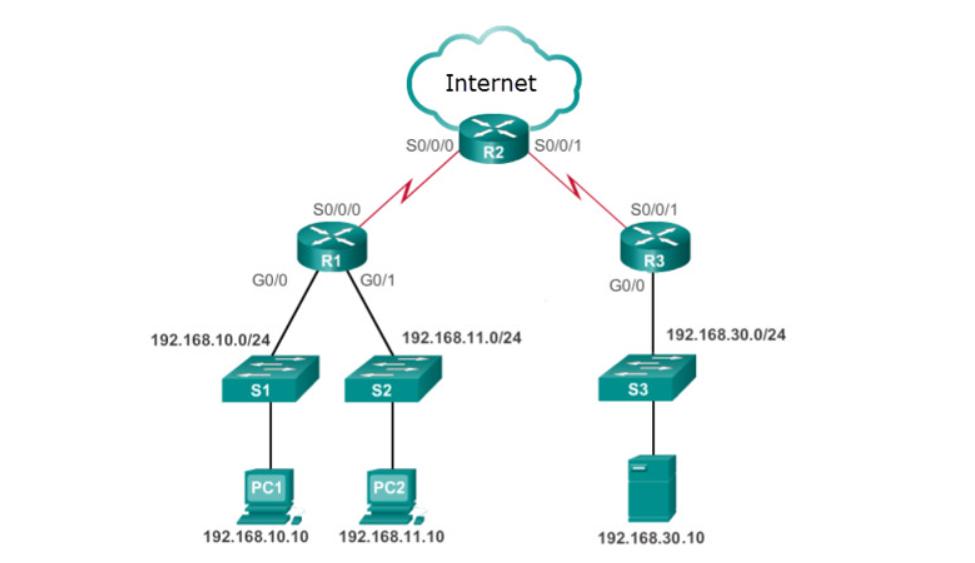
Refer to the exhibit. The network administrator has an IP address of 192.168.11.10 and needs access to manage R1. What is the best ACL type and placement to use in this situation?
standard ACL inbound on R1 vty lines
A technician is tasked with using ACLs to secure a router. When would the technician use the any configuration option or command?
to identify any IP address
Which statement accurately characterizes the evolution of threats to network security?
Internal threats can cause even greater damage than external threats.
A user receives a phone call from a person who claims to represent IT services and then asks that user for confirmation of username and password for auditing purposes. Which security threat does this phone call represent?
social engineering
In what way are zombies used in security attacks?
They are infected machines that carry out a DDoS attack.
Which attack involves threat actors positioning themselves between a source and destination with the intent of transparently monitoring, capturing, and controlling the communication?
man-in-the-middle attack
Which two keywords can be used in an access control list to replace a wildcard mask or address and wildcard mask pair? (Choose two.)
host
any
Which statement describes a difference between the operation of inbound and outbound ACLs?
Inbound ACLs are processed before the packets are routed while outbound ACLs are processed after the routing is completed.
What effect would the Router1(config-ext-nacl)# permit tcp 172.16.4.0 0.0.0.255 any eq www command have when implemented inbound on the f0/0 interface?
Traffic originating from 172.16.4.0/24 is permitted to all TCP port 80 destinations.