K201 lecture exam 1
1/65
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
66 Terms
According to your textbook, in the five-component framework of an information system, which is the most important?
People
Each information system is comprised of five components. Match the component with the order in which is appears (left to right) in the Five-Component Model.
Hardware, software, data, procedures, people
The number of components in the Five-Component Model increases in proportion to an information system's complexity and/or size
False
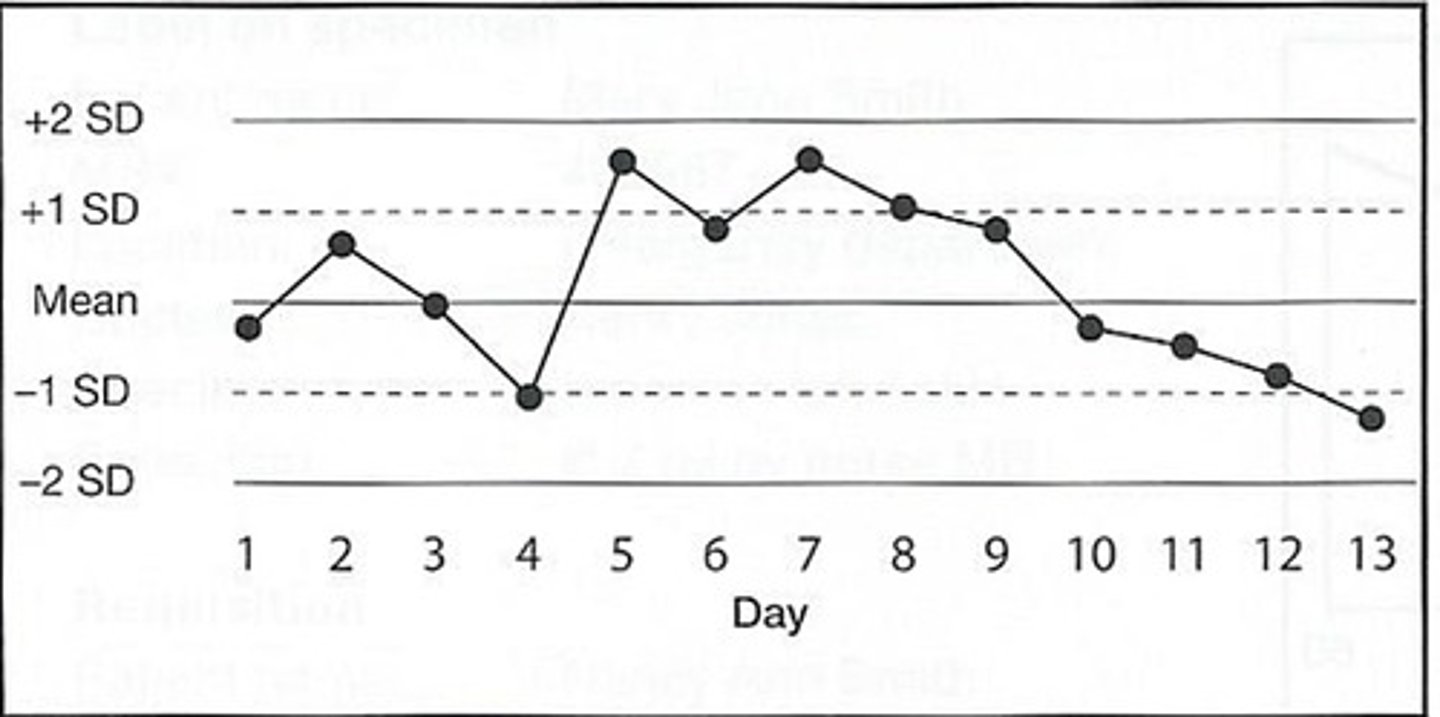
Which of the following does the chart represent?
Data
In order for data to be considered timely is must be delivered in real time.
False
Good data is always worth the cost, no matter how expensive.
False
Keeping track of data involving multiple themes such as employees, transactions, customers, supplies, etc. should be done with what?
a relational database
The data displayed in Design view of a table in an access database is an example of _____
Metadata
A database is simply a group of tables or files.
False
Match the data elements below with the term in which they are often referred to:
fields:
bytes:
table:
records:
columns
characters
file
row
How many primary functions does a database management system (DBMS) have?
3 primary functions
Which of the following is an international standard language for processing a database?
SQL
The lost-update problem can be resolved by implementing multi-user database processing.
False
Microsoft access belongs to which DBMS category
Personal DBMS
A ______ describes the data and relationships that will be stored in a database
Data model
Which of the following relationship types is described when there are crow feet connecting the tables?
N:M many to many
A table containing normalized data should have 3 or fewer themes.
False, one have one theme
Which phase of the SDLC is the most important phase?
Determine Requirements
If a defined project is determined to be feasible in the SDLC, the immediate next step is to ________.
Form the project team
The situation that occurs when adding more resources creates inefficiencies is known as _______.
Diseconomies of scale
Information systems that process operational, social, and other data to ID patterns, trends, and relationships for use by business professionals are known as _______.
Business Intelligence Systems
The patterns, trends, and relationships produced by these information systems are referred to as _______.
Business Intelligence
An inventory report set to run automatically when an item reaches a critical low point is an example of pull publishing.
False, that would be considered push publishing
What is the first primary activity in the BI process?
Acquire data
One of the main benefits of a BI analysis is that there are no discrepancies in the data acquired from multiple sources.
False
______ is the application of statistical techniques to find patterns and relationships among data for classification and prediction.
Data mining
True or false of unsupervised data mining, Analysts do not create a model or hypothesis before running the analysis.
True
With _______, data miners develop a model prior to the analysis and apply statistical techniques to data to estimate parameters of the model.
Supervised data mining
A common business application of decision trees is to classify loans by likelihood of default.
True
The process by which Netflix recommends movies and TV shows that you may like is an example of business intelligence systems being utilized in the entertainment industry.
True
A ______ is a person or organization that seeks to obtain or alter data or other IS assets illegally, without the owner's permission and often without the owner's knowledge.
Threat
An employee inadvertently installing an old database on top of the current one is an example of a threat caused by human error.
True
In the context of security threats, pretexting, sniffing, spoofing, and phishing are all examples of _______.
Unauthorized data disclosure
In order to access your student records, you must authenticate with your IU username and passphrase. This is an example of which type of safeguard?
Technical safeguard
Encryption, the process of transforming clear text into coded, unintelligible text for secure communication is a type of data safeguard.
False
Nonword passwords are vulnerable to a _________ attack in which the password cracker tries every possible combination of characters.
Brute force
When transferring funds online through the website of a reputed bank, what should be displayed in the address bar of the browser that will let you know that the bank is using the Secure Sockets Layer (SSL) protocol?
https
_______ refers to an organization-wide function that is in charge of developing data policies and enforcing data standards.
Data administration
________ protect databases and other organizational data.
data safeguards
True or false about human safeguards: user accounts should be defined to give users the least possible privilege needed to perform their jobs.
True
A student team, which is assigned a term project, meets and divides the work into a section and then the team members work independently on their individual pieces. An hour before the project is due the team members meet again to assemble their independent pieces into a whole. What is LACKING in this activity?
Collaboration
What is a key difference between collaboration and cooperation?
Unlike cooperation, collaboration gives importance to iteration and feedback
What is the primary purpose of collaboration?
Being informed
Kyra, a plant supervisor, orders 500 units of Type-2 steel beams for the coming month. In doing so, she has made a(n) __________ decision.
Operational
Project leaders have to make decisions on the allocation and utilization of materials and labor. Such decisions are called _________ decisions.
Managerial
An organization uses a formula to compute the reorder quantity of an item in inventory, This is an example of a(n) __________ decision process.
Structured
What question is best answered through unstructured decision making?
Should we continue to outsource our bookkeeping processes?
The need for collaboration is greatest for _______ decisions.
Strategic
Margaret finds that calling all her senior supervisors and quality managers for a face-to-face meeting is not feasible. She arranges for a multiparty text chatting sessions involving all of them. This is an example of asynchronous communication.
False
Version-management systems ___________.
Track changes to shared documents.
Businesses often purchase information systems to increase efficiency of their business process.
False, can only purchase Information Technology
In pre-lab, you created a relationship between the Employee table and the Employee_Training table. Both tables contain an employee ID field. What type of key is the Employee ID field in the Employee_Training table?
Foreign key
Is microsoft access considered a database?
No, its a database management system
The forked lines on the right side of a line on an E-R diagram that indicates a 1:N relationship between 2 entities is referred to as a _________.
Crows Feet
Which type of relationship would be between a student table and a classes table?
N:M (many to many)
Aldi utilizes a database that enables them to report back to their suppliers and concerns they may have about the quality of food. In this database what type of relationship would be between a supplier table and a food item?
1:M (one to many)
Are any parts of is IS components not part of a Business Intelligence Information System
No, BI information systems contain all 5 components (hardware, software, data, procedures, people)
What is the software component of a BI system called?
BI application
One benefit from effective supervised data mining techniques is to determine sales patterns which can result in increased sales through cross-selling.
False, cross-selling comes from market-basket analysis (unsupervised)
Regression analysis, which is a statistical method of measuring the effects of a set of variables on another variable is an example of a supervised data mining technique.
True
Email spoofing is a synonym for phishing.
True
True/False about managing risk in information security: organizations should implement safeguards that balance the tradeoff between risk and cost.
True
A ______ is a type of virus that self propagates using the internet or other computer network
a worm
________ involve the people and procedure component of information systems.
Human Safeguards
A team of Aldi district managers working together to increase the overall Quarter 3 sales in the U.S is an example of _______.
cooperation because they are doing the same type of work to accomplish task and meet a goal
Version management tool limit, and sometimes even direct user activity control workflow.
false, not about control