TOPCIT: Information Security
1/32
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
33 Terms
Which is NOT a requisite activity for the implementation of database access control?
Implement duplex functions to prepare for failures.
Implement authentication functions to identify users.
Define access methods and time to access information.
Identify users who are able to discern and access critical information.
Implement duplex functions to prepare for failures.
Which of the following is NOT a correct explanation about the security of Linux or Linux-like systems?
Delete unnecessary accounts using 'userdel' command.
'Write' permissions on /etc/profile files are removed except for the root user.
Use 'chmod' command to assign permissions to each user according to the access control policy.
Include users with access permissions to /etc/hosts. allow files and users without access permissions to /etc/hosts. deny files for access control.
Include users with access permissions to /etc/hosts. allow files and users without access permissions to /etc/hosts. deny files for access control.
Choose the correct explanation of the certification system for the Information Security Management System (ISMS).
The companies for profit only are subject to the certification.
There is no guarantee that the company with the certification is 100% safe from information security infringement incidents.
The initial certification is processed when the certification is acquired for the first time. The certification is valid for five years.
The scope of certification encompasses not only information and communication services but also the internal task procedures such as groupware and human resource systems which are not directly related to the information and communication services.
The initial certification is processed when the certification is acquired for the first time. The certification is valid for five years.
Which is the certification system described below?
Examines the adequacy of information protection systems, such as information protection management processes and security policies.
Examines the adequacy of the personal information protection management systems such as collection, use, and destruction policies of personal information.
ISMS-P(Personal Information & Information Security Management System)
ITSM(Information Technology Service Management)
PIMS(Personal Information Security Management System)
PIPL(Personal Information Protection Level)
ISMS-P(Personal Information & Information Security Management System)
Which of the following algorithms has NOT been applied for the right purpose?
The RSA-2048 algorithm has been applied to encrypt the encryption key.
The ECC algorithm has been applied to encrypt massive data at high speed.
The SEED algorithm has been applied to encrypt resident registration numbers.
The SHA:256 algorithm has been applied to verify the integrity of the data transmitted.
The ECC algorithm has been applied to encrypt massive data at high speed.
![<p><span style="background-color: transparent;"><span>Choose a Linux command to apply the [Improvement Plan] to the [Status of Access Right to Personal Information Files] below.</span></span></p><ul><li><p><span style="background-color: transparent;"><span>cat</span></span></p></li><li><p><span style="background-color: transparent;"><span>chown</span></span></p></li><li><p><span style="background-color: transparent;"><span>touch</span></span></p></li><li><p><span style="background-color: transparent;"><span>umask</span></span></p></li></ul><p></p>](https://knowt-user-attachments.s3.amazonaws.com/8e6d987b-9cd4-4d81-aeef-50c8cd543b2b.png)
Choose a Linux command to apply the [Improvement Plan] to the [Status of Access Right to Personal Information Files] below.
cat
chown
touch
umask
umask
Which description is NOT correct about Wireless LAN Security of IEEE 802.11?
Use 802.1x as the user authentication method.
4-way Handshake is used as the key exchange method.
Separate user authentication methods and the encryption function.
WEP (Wireless Equivalent Privacy) is used as the encryption algorithm
WEP (Wireless Equivalent Privacy) is used as the encryption algorithm
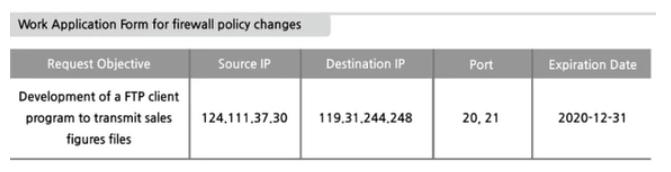
The example below is the summary of Work Application Form for the firewall of Company A. Which of the following interpretation is NOT a correct request for firewall policy changes?
The FTP client program is executed on a computer with the IP address 124:111.37.30.
The FTP server program is executed on a server with the IP address 119.31.244.248.
The request for firewall policy changes is to use port numbers 20 and 21 in the firewall.
The firewall policy manager must be set up to allow the in-bound port to source IPs.
The firewall policy manager must be set up to allow the in-bound port to source IPs.
Which of the following is NOT a correct explanation on the SSL(Secure Socket Layer)?
HTTPS protocol is SSL applied HTTP protocol.
In order to apply SSL, SSL certificate must be installed in a web server.
It runs in the Network Layer of the OSI(Open System Interconnection) 7 layer model.
Mutual authentication is carried out through the Handshake protocol between the client and the server.
It runs in the Network Layer of the OSI(Open System Interconnection) 7 layer model.
Choose the security threat against cloud computing described below:
The weaknesses found in the elementary technologies of cloud computing or in the hardware may be extended to the entire cloud computing environment.
The hacking of the hypervisor may affect all related operating system and result in the loss of control.
Virtualization vulnerabilities
Insufficient key management
Insecure API
Insufficient authentication and access management
Virtualization vulnerabilities
Choose the statement that is NOT correct about the vulnerabilities of Log4j.
Rated as Critical by the Common Vulnerability Scoring System (CVSS).
Log4j must be updated to the latest version according to the Java version.
Attacks such as DDoS and malware that make bad use of the Log4j vulnerabilities are possible.
Vulnerabilities occur because the return value is not verified after Lookup Method of JNDI is called.
Vulnerabilities occur because the return value is not verified after Lookup Method of JNDI is called.

Choose a method of IDS (Intrusion Detection System) that is appropriate to the description below.
Rule based
Pattern based
Behavior based
Signature based
Behavior based
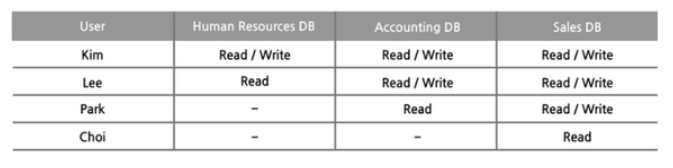
The Access Control Matrix in the example below defines the level of access to the data of Company A for each user. Choose the access control model used in the example.
Discretionary Access Control (DAC)
Mandatory Access Control (MAC)
Non-Discretionary Access Control (NDAC)
Role-Based Access Control (RBAC)
Discretionary Access Control (DAC)
Choose the incorrect management strategy of the database key encryption.
Use the secured random number generator when encryption keys are generated.
When the encryption keys are saved in file formats, they can be stored in plain text.
Encryption keys may be changed in 90, 180, or 365 days regularly according to the internal policy of the organization.
Encryption keys are managed by the database administrator and by the security manager, applying the principles of the minimum rights assignment and of the separation of duties.
When the encryption keys are saved in file formats, they can be stored in plain text.
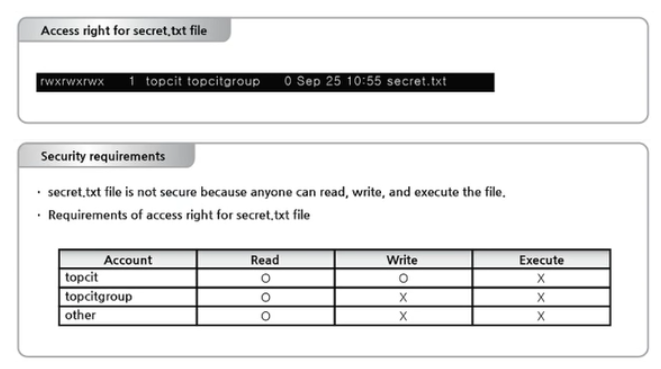
Choose the Linux command to apply the following security requirements.
chmod 022 secret.txt
chmod 644 secret txt
chmod 755 secret.txt
chmod 777 secret.txt
chmod 644 secret txt
Choose the most appropriate characteristic to the circumstance described below from the three goals of information security.
Company A operates two firewalls in the computer center.
Enables the smooth access to services by detouring the transmission traffic of the network information to other firewalls when anyone of the firewalls fails.
Availability
Confidentiality
Integrity
Controllability
Availability
Choose the term Q related to the personal information protection explained below.
Generalization
Obfuscation
Re-identification
Standardization
Re-identification
Which one of the following encryption technologies has the characteristics described below?
Different keys are used for encryption and decryption.
Processing speeds for both encryption and decryption are relatively slow.
Appropriate for encrypted communications with unknown persons.
Block Encryption
Public Key Encryption
Stream Encryption
Symmetric Key Encryption
Public Key Encryption
Which is NOT a requisite activity for Digital Signature described below?
Senders generate signatures using signature algorithms.
Receivers verify received messages and signatures using algorithms.
When verification results are true, received messages are determined as right.
Encryption
Integrity
Message Authentication
Non-Repudiation
Encryption
Choose the user authentication technology explained below.
Company A recently launched a web service, allowing users to access the service by utilizing their existing login information from google, facebook, etc. without a separate registration.
OAuth (Open Authorization)
OTP (One Time Password)
PKI (Public Key Infrastructure)
SSL (Secure Socket Layer)
OAuth (Open Authorization)
What is the type of network attack described below?
Forging a Media Access Control (MAC) address of a user PC with that of another user's PC.
Bypassing or avoiding the Access Control List (ACL) of the other party by forging or deceiving the attacker's own IP address.
Sending emails attached with malicious codes by forging the attacker's email address with that of the person the receiver trusts.
Smishing
Sniffing
Snooping
Spoofing
Spoofing
Which description is NOT correct about Wireless LAN Security of IEEE 802.11i?
Use 802.1x as the user authentication method.
4-way Handshake is used as the key exchange method.
Separate user authentication methods and the encryption function.
WEP (Wireless Equivalent Privacy) is used as the encryption algorithm
WEP (Wireless Equivalent Privacy) is used as the encryption algorithm.
Choose the statement that can NOT be inferred from the situation below.
Assistant Manager Park received a contract through the internet electronically signed by General Manager Lee who works for the partner company.
Assistant Manager Park confirmed that the hash function result of the received contract and the decryption result of the electronic signature are identical.
The received contract was not forged or altered.
The contract guarantees that the document was prepared by General Manager Lee.
The contract was not leaked externally in the process of sending or receiving.
A set of paired private and public keys was used.
The contract was not leaked externally in the process of sending or receiving.
Choose the setting which is NOT correct for the security of Windows system.
Delete unnecessary Guest accounts.
Block access to shared folders and remote registries.
Use " iptables" command to block the link of networks.
Stop unnecessary services applying terminal services, anonymous FTP, SNMP, etc.
Use " iptables" command to block the link of networks.
What is the type of security weakness described below?
Malicious scripts are inserted into a web page to be executed by a user's PC.
When an unverified external input is used to create a dynamic web page, it launches malicious behavior with the access privilege of the person browsing the page.
It leads to attacks such as leaks in browser cookies.
Web shell
SQL injection
Cross-site script
Memory Buffer Overflow
Cross-site script
Choose the next-generation cryptography technology explained below.
Cryptography technology using the minimum amount of physical entity.
"Superposition", "non-measurable", and "unclonable" characteristics of physical entities are applied.
It creates a one-time cryptographic key that is not decryptable between the sender and receiver to maintain confidentiality.
It is regarded as the most secure communication cryptography method among current security cryptography technologies.
Hash-based Cryptography
Quantum Cryptography
Steganography
Stream Cipher
Quantum Cryptography
Choose the database access control policy explained below.
Job functions are defined as developers, users, and database administrators (DBA).
The user, developer, and DBA functions are assigned to Assistant Manager Park, Manager Lee, and Director Jeong respectively, and only the minimum rights are permitted to perform their assigned functions as required.
The assignment and withdrawal of permissions can be done efficiently when assigned functions for staffs change frequently.
Discretionary Access Control
Hybrid Access Control
Mandatory Access Control
Role-Based Access Control
Role-Based Access Control
Choose which of the following statements is INCORRECT on the security of the mobile applications.
Mobile applications are developed so as not to operate the functions that are different from the purpose of application services.
Mobile applications are developed so as to operate even when the terminals are controlled by Rooting(Android) or Jailbreaking(iOS).
Mobile applications are developed so as to encrypt important information when they are stored inside the application or transmitted.
Source code obfuscation methods are applied to Android mobile applications so as to prevent easy analyses of source code through decompilation.
Mobile applications are developed so as to operate even when the terminals are controlled by Rooting(Android) or Jailbreaking(iOS).
Which of the following is NOT a correct description of a block cipher mode?
The DES and AES are typical algorithms of block ciphers.
A block cipher is faster than a stream cipher.
A block cipher encrypts by the unit of fixed-length group of bits called block.
When the size of the data to be encrypted is larger than the size of a block, a separate operation mode is required.
A block cipher is faster than a stream cipher.
The diagram below is a process of digital signature between senders and receivers.
Choose the correct set of key names for blanks and b.
(a) Public key of the sender (b) Private key of the sender
(a) Private key of the sender (b) Public key of the sender
(a) Public key of the receiver (b) Private key of the receiver
(a) Private key of the receiver (b) Public key of the receiver
(a) Private key of the sender (b) Public key of the sender
Choose the phase of the Secure SDLC (Software Development Life Cycle) that corresponds to the description below.
Threat modeling to identify security threats.
System structure modification to eliminate identified security threats.
Establishing security control criteria and activities suggested by the Secure Development Guidelines.
Design
Maintenance
Implementation
Requirements analysis
Design
Choose the INCORRECT method to apply encryption.
AES-128 encryption algorithm is used when the unique identification information is encrypted.
Passwords must be encrypted multiple times with a bi-directional encryption algorithm before they are stored.
The unique identification information stored in the DMZ (Demilitarized Zone), intermediate zone of Internet and Intranet, is encrypted.
API (Application Programming Interface) encryption is applied to transmit and receive encrypted data between application servers and database servers.
Passwords must be encrypted multiple times with a bi-directional encryption algorithm before they are stored.
Choose the activity performed during the implementation phase of the Secure SDLC (Secure Software Development Life Cycle).
Identification of security item requirements.
Threat modeling that identifies software security threats
Review of source code or diagnosis of source code security
Security vulnerability verification through dynamic analysis or Penetration Testing.
Review of source code or diagnosis of source code security