A+ 1102 combined set (abridged)
1/95
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
96 Terms
exFAT
- Microsoft flash drive file system
- files can be larger than 4 GB
- compatible across many operating systems (Windows, Linux, Mac OS)
NTFS
- provides extensive improvements over FAT32
- quotas, file compression, symbolic links, encryption, large file support, etc.
- not very compatible across operating systems
- many will read NTFS, but not write (or will have limited writing functionality)
Finder
- the central OS file manager
- provides integrated access to other devices
Remote Disc
- use an optical drive from another computer
- designed for copying data files
- set up in System Preferences, under Sharing
Force Quit
- press cmd-option-esc to bring up the menu
- or, hold down the option key when right clicking the application icon in the dock
Accessability
- allow applications to use system input
- can be used to further secure a system
"sdelete" (command)
- file level overwriting
Access Control Lists (acronym)
ACL
ACL
- used to allow or deny traffic
- also used by operating systems
- commonly used on the ingress or egress of a routing interface
Non-Persistent (Reflected) Cross-Site Scripting Attacks (steps)
1. the website allows scripts to run inside of user input prompts and text boxes
2. to utilize this design flaw, the attacker emails a link
3. this link runs a script that sends credentials, session IDs, and cookies to the attacker
4. simultaneously, the script embedded in the URL executes in the victim's browser
Persistent (Stored) Cross-Site Scripting Attacks
- malicious code is placed on a centralized server, such as a social media website
- inside of a comment, for example
- everybody who visits the page or who views the comment gets attacked
- no specific target
Standard Operating Environments
- a set of tested and approved hardware/software systems
- often a standalone OS image
Patch Management (steps)
1. test
2. prioritize
3. deploy
EOSL
- similar to EOD, but support is no longer available
- a costly, premium support option may exist, though
Windows Firewall Exception Rule Types (list)
- program
- port
- predefined
- custom
NTFS Permissions
- apply from local and network connections
- inherited from the parent
Share Permissions
- only apply to connections over the network
- the most restrictive setting wins
User Account Control (acronym)
UAC
User Account Control
- pop-up approval screen
- limits user capabilities
- secure desktop
Verifying Certificate Details (list)
verify
- not expired
- domain name
- properly signed
- date and time
Unable to Access The Network (Troubleshooting)
- may be due to malware
- symptoms:
- slow performance and lock up
- internet connectivity issues
- OS update failures
- use malware cleaner or reload from a known good backup
Altered System or Personal Files (Troubleshooting)
- indicates malware
- remove or reload from a known good backup
Browser Redirection (Troubleshooting)
- malware is the most common cause
- best practice is to restore from a known good backup
App Issues (Troubleshooting)
- restart the device
- stop the app and restart
- or update the application
App Fails to Update (Troubleshooting)
- manually update
- restart the device
OS Fails to Update (Troubleshooting)
- check available storage
- check available bandwidth
- connect to wifi
- try a different network connection
- reboot
Battery Life Issues (Troubleshooting)
- caused by bad reception or an aging battery
- disable unnecessary features
- check application battery usage
Random Reboots (Troubleshooting)
- check the OS and application versions
- perform a hardware check
- check the battery health
- contact tech support for options
- crash logs should be on the device
No Wifi Connectivity (Troubleshooting)
- check/enable Wifi
- check security key configuration
- hard reset your device
"pwd" (command)
- prints the working directory's name (path)
Linux File System Mode Cheat Sheet (image)
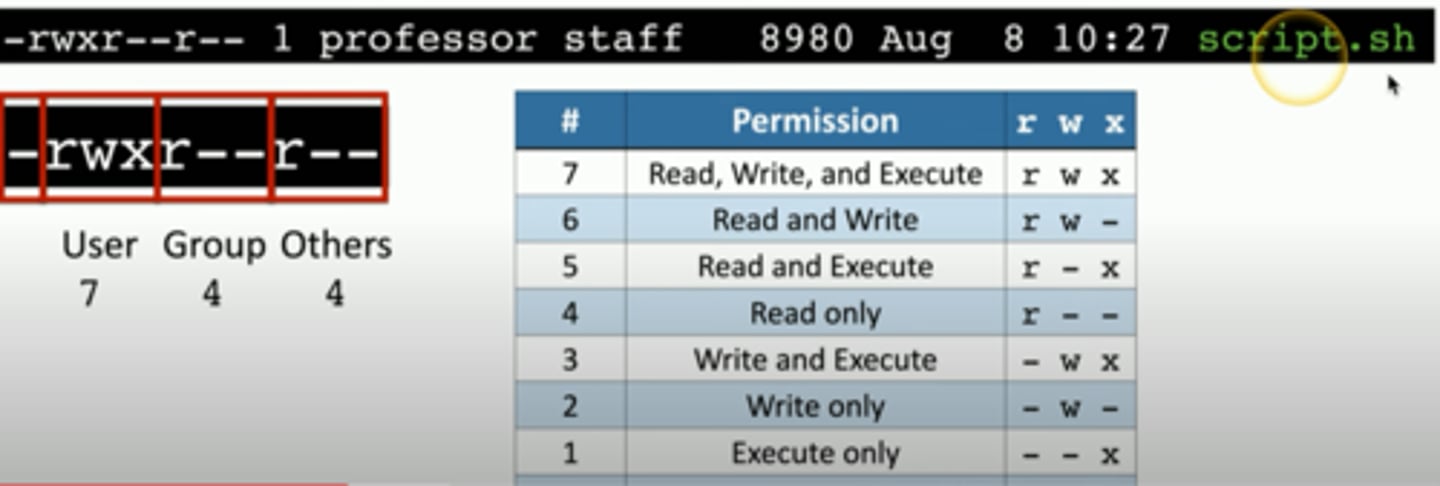
Commonly Used "ip" Commands (list)
- "ip address"
- "ip route"
"df" (command)
- view file systems and free space
- presented in blocks
- use "df -h" to view in human-readable sizes
"top" (command)
- view resource utilization
- includes a summary of the overall load
- presented in one, five, and fifteen minute intervals
"cat" (command)
- concatenate files
- "cat [first file and extension] [second file and extension]"
- copies a file or files to another file
"rsync" (command)
- provides a utility for syncing files between storage devices
- can be instant or scheduled
Software Center
Linux's version of the Mac OS App Store
"samba"
- file server utility
- often used to add SMB (Server Message Block) to Linux systems
- implement file and printer sharing
- integrate with Active Directory
- integrates Linux into a Windows environment
Starting the Windows Recovery Environment
- hold shift while clicking the restart button
- or, boot from installation media
- or, restart into advanced startup
- recovery > troubleshoot > advanced options > command prompt
Malware Removal Process (steps)
1. verify malware symptoms
2. quarantine infected
3. disable system restore
4. remediate : update anti-virus
5. remediate : scan and remove
6. schedule scans and run updates
7. enable system protection
8. educate the end user
4. Remediate : Update Anti-Virus (Malware Removal Process)
- the malware may prevent the update process
- copy updated signatures onto your computer
5. Remediate : Scan and Remove (Malware Removal Process)
use tools or run in Safe Mode or in WinPE
Galois Message Authentication Code (acronym)
GCMP with GMAC
Counter Mode with Cipher Block Chaining
Message Authentication Code Protocol (acronym)
CCMP with CBC-MAC
Simultaneous Authentication of Equals (acronym)
SAE
WPA2
- uses CCMP block cipher mode
- provides data confidentiality using AES encryption
- adds a MIC with CBC-MAC (compared to WPA)
WPA3
- introduced in 2018
- uses GCMP block cipher mode
- a stronger encryption method than WPA2
- provides data confidentiality with AES
- includes MIC with GMAC
TACACS
- remote authentication protocol
- created to control access to dial-up lines to ARPANET
TACACS+
- the latest version of TACACS
- provides more authentication requests and response codes
- released as an open standard in 1993
- commonly associated with Cisco devices, though
Kerberos
- network authentication protocol
- supports SSO
- provides mutual authentication between the client and the server
- prevents against on-path or replay attacks
- standard since the 1980s
- used for Windows Domain authentication
Acceptable Use Policy (acronym)
AUP
Differential Backup
subsequent backups contain data changed since the last full backup
Incremental Backup
- subsequent backups contain data changed since the last full backup and the last incremental backup
- a restoration requires the last full backup and all of the incremental backups
Synthetic Backup
- the first full backup copies every file
- subsequent full backups are created from previous backups
Uninterruptible Power Supply (UPS) Types (term-5list)
- standby UPS
- line-interactive UPS
- on-line UPS
Surge Suppressor Specifications (list)
- joule ratings
- surge absorption
- look for 600+ joules of protection
- surge amp ratings
- UL 1449 voltage let-through ratings
- ratings at 500, 400, and 300
- lower is better
Incident Response : Chain of Custody
- control evidence and maintain integrity
- documents everybody who comes into contact with the evidence
- avoid tampering
- use hashes
- label and catalog everything
- use digital signatures
Incident Response : First Response (steps)
1. identify the issue
- logs, monitoring data
2. report to proper channels
3. collect and protect evidence
PHI
regulated with HIPAA
RDP (Microsoft Remote Desktop Protocol)
- clients for MacOS, Linux, etc.
- remotely connect to a Windows device
Remote Frame Buffer Protocol (acronym)
RFB
VNC
- uses RFB protocol
- clients for many operating systems
Maximum Supported RAM for x64 (64-bit) Windows 10 Operating System Versions (list)
- Windows 10 Home: 128 GB
- Windows 10 Pro: 2 TB
- Windows 10 Pro for Workstations: 6 TB
- Windows 10 Enterprise: 6 TB
Group Policy Editor
- centrally manage users and systems
- commonly associated with Active Directory
- though, policies can be part of a local system
Local Group Policy (command)
"gpedit.msc"
Group Policy Management Console
integrated with Active Directory
Group Policy Management Console (command)
"gpmc.msc"
In-Place Upgrade Paths to Windows 10 (list)
- Windows 7
- Windows 8.1
- not Windows 8.0
Roll Back a Windows Upgrade (instructions)
start > settings > system > recovery > go back
Organizational Units (acronym)
OU
Group Policy Updates
- manage the computer or users with group policies, using the group policy management front-end and editor
- a central console
- update a client with the "gpupdate" utility
- applies policy changes
- "gpupdate /force" will update all of the group policies
Assigning a Home Folder to a Network Folder
- allows you to manage and backup files from the network
- when added to a user profile, the directories are automatically created, with proper permissions assigned
Folder Redirection
- redirects folders to a network share
- user configuration > policies > windows settings > folder redirection
- often paired with the Offline Files feature
Built-In Windows Groups (list)
- users, guests
- remote management users
- event log readers
Microsoft Management Console
- build your own management consoles
- add snap-ins to customize
- mmc.exe
Power Options (Control Panel)
- configure how Windows uses power
- options to choose what closing the lid on a laptop does
- options for USB selective suspend
- used to disable individual USB devices
- enable or disable fast startup
modes:
- hibernate
- open documents and applications are saved to the disk
- used by Fast Startup
- sleep (standby)
- open files and applications are stored in memory
- save power and startup quickly
- switches to hibernate if power is low
Blue Screens and Frequent Shutdowns
- might be linked to bad hardware, bad drivers, or a bad application
- use last known good, system restore, or rollback drivers to troubleshoot a possible software problem
- or try safe mode
- if potentially hardware related, remove or reseat the hardware
- run hardware diagnostics
Sluggish Performance
- check task manager for high CPU and I/O utilization
- update Windows
- check for available disk space and defrag
- verify power-saving mode is turned off (laptops)
- run an anti-virus scan and an anti-malware scan
Windows Boot Configuration (acronym)
BCD
Windows Boot Configuration
"bootrec /rebuildbdcd" in the recovery console
Boot Errors
- may be caused by a boot loader replacement or changes
try:
- checking boot drives
- remove any removable media
- using startup repair
- modifying BCD
Startup Repair
- useful in missing NTLDR troubleshooting
- the main Windows boot loader is missing
- run Startup Repair or replace manually and reboot
- disconnect any removable media
- also useful with missing OS errors
- boot configuration data may be incorrect
- settings > system > recovery
- or run from advanced boot options
Starting The System Troubleshooting
- if Windows is starting, but a device is not, check device manager and event viewer
- often due to a bad driver
- remove or replace
- the "one or more services failed to start" error is due to bad/incorrect drivers or bad hardware
- try starting manually
- check account permissions
- check service dependencies
- check system files (Windows Service)
- reinstall application (application service)
Application Crashing
- check the event log and/or the reliability monitor
- reinstall the application
- contact application support
System Instability
- general system failures
troubleshooting:
- run a full diagnostic (first)
- check the OS
- run SFC
- perform an anti-malware scan
System File Checker
- verifies the integrity of the OS
- "sfc /scannow"
Deleting a Windows Profile (steps)
1. login to the computer with domain administrator rights
2. rename the \users\name folder
3. backup the user's registry
- HKLM\software\microsoft\windows nt\currentversion\profilelist
- right click and export
4. delete the registry entry
Recreating a Windows Profile (steps)
1. login to the computer with the user account
- the profile will be rebuilt
2. login as the domain administrator and copy any important files from the old profile, to the new profile
GPT Partition Style
- the latest partition format standard
- requires a UEFI BIOS
- can have up to 128 partitions
- maximum partition size is over 9 billion TB
- no need for extended partitions or logical drives
MBR Partition Style
- maximum partition size of 2 TB
- includes primary and extended partitions
primary partitions:
- bootable
- maximum of four per hard disk
- one can be marked as active
extended partitions:
- used for extending the maximum number of partitions
- one per hard disk (though optional)
- contains additional logical partitions
- not bootable
Shared Resources
- make a folder or printer available on the network
- share by mapping a drive letter to a share
- shares ending with a $ are hidden
- view shares in Administrative Tools/Computer Management
Mapping Drives
- needed to access a share on a remote device
- associates a drive letter with a share name
- view network shares in "This PC"
- create using "map network drive"
- or by using "net use [drive letter]: \\[server]\[name]" in command prompt
- disconnect a share in the toolbar or by right-clicking the drive
Sharing a Printer
- access the share function in printer properties, file explorer, or the settings application
- manage printer access under the security tab
Accessing a Shared Printer
add the printer to your system from file explorer or from the settings application
Windows Firewall Configuration Options (list)
- block all incoming connections
- ignores your exceptions
- the most secure option
- modify notifications
- app blocking
Allowing an Application or Feature Through Windows Firewall Options (list)
- block or allow by port number
- use predefined exceptions
- set custom rules