CCNA 3 Module (3-5) Part 3
1/10
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
11 Terms
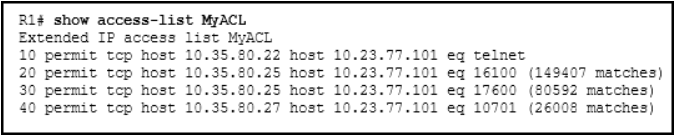
Refer to the exhibit. What can be determined from this output?
The router has not had any Telnet packets from 10.35.80.22 that are destined for 10.23.77.101.
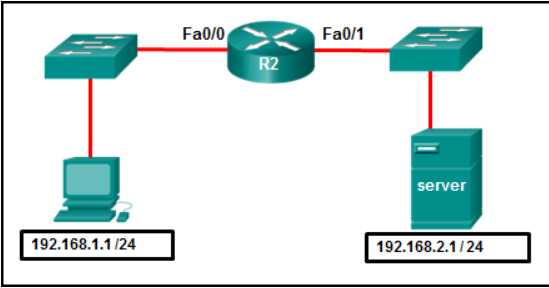
Refer to the exhibit. A network administrator wants to permit only host 192.168.1.1 /24 to be able to access the server 192.168.2.1 /24. Which three commands will achieve this using best ACL placement practices? (Choose three.)
R2(config-if)# ip access-group 101 in
R2(config)# interface fastethernet 0/0
R2(config)# access-list 101 permit ip host 192.168.1.1 host 192.168.2.1
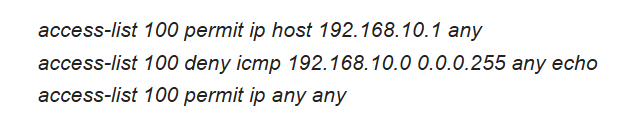
Consider the following access list. Which two actions are taken if the access list is placed inbound on a router Gigabit Ethernet port that has the IP address 192.168.10.254 assigned? (Choose two.)
A Telnet or SSH session is allowed from any device on the 192.168.10.0 into the router with this access list assigned.
Devices on the 192.168.10.0/24 network are allowed to reply to any ping requests.
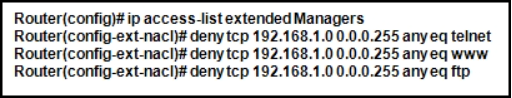
Refer to the exhibit. The named ACL “Managers” already exists on the router. What will happen when the network administrator issues the commands that are shown in the exhibit?
The commands are added at the end of the existing Managers ACL.
In which TCP attack is the cybercriminal attempting to overwhelm a target host with half-open TCP connections?
SYN flood attack
Which protocol is attacked when a cybercriminal provides an invalid gateway in order to create a man-in-the-middle attack?
DHCP
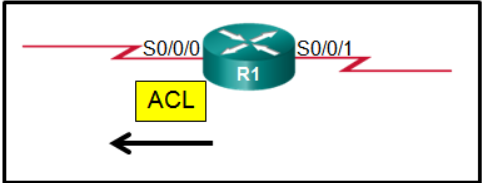
Refer to the exhibit. An administrator has configured a standard ACL on R1 and applied it to interface serial 0/0/0 in the outbound direction. What happens to traffic leaving interface serial 0/0/0 that does not match the configured ACL statements?
The traffic is dropped.
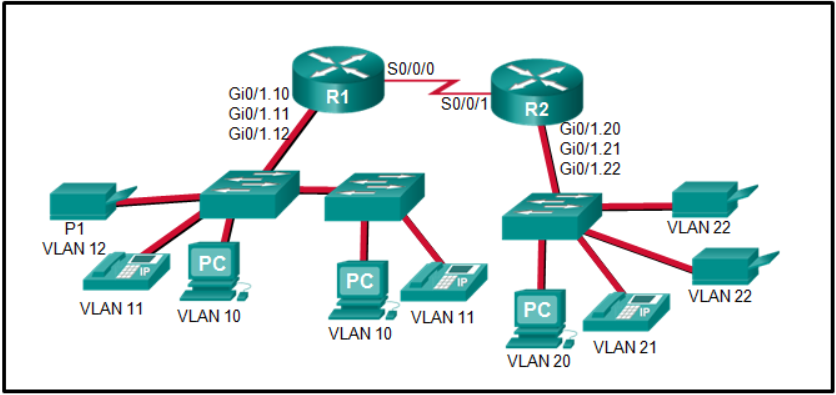
Refer to the exhibit. The Gigabit interfaces on both routers have been configured with subinterface numbers that match the VLAN numbers connected to them. PCs on VLAN 10 should be able to print to the P1 printer on VLAN 12. PCs on VLAN 20 should print to the printers on VLAN 22. What interface and in what direction should you place a standard ACL that allows printing to P1 from data VLAN 10, but stops the PCs on VLAN 20 from using the P1 printer? (Choose two.)
R1 Gi0/1.12
outbound
Which statement describes a characteristic of standard IPv4 ACLs?
They filter traffic based on source IP addresses only.
What is considered a best practice when configuring ACLs on vty lines?
Place identical restrictions on all vty lines.
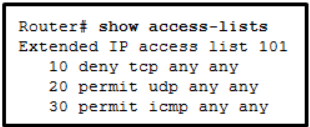
Refer to the exhibit. An administrator first configured an extended ACL as shown by the output of the show access-lists command. The administrator then edited this access-list by issuing the commands below.
Router(config)# ip access-list extended 101
Router(config-ext-nacl)# no 20
Router(config-ext-nacl)# 5 permit tcp any any eq 22
Router(config-ext-nacl)# 20 deny udp any anyWhich two conclusions can be drawn from this new configuration? (Choose two.)
Ping packets will be permitted.
SSH packets will be permitted.