2.2 Common Threat Vectors
1/13
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
14 Terms
Threat Vectors
Or attack vector, is the method an attacker uses to break into a system. It’s the path they take to try and gain access.
Security professionals spend a lot of time studying these vectors—looking for weak spots, figuring out which ones are most vulnerable, and working to protect them.
Part of their job is also to identify new vectors before attackers can use them.
Message-Based Vectors
One of the most common and effective threat vectors. Since almost everyone uses some form of messaging.
Email, text messages (SMS), or instant messaging.
Might send malicious links or attachments that, when clicked or opened, lead to fake websites (like a fake bank login page) or install malware on your device. This is the basis of many phishing attacks.
Also use social engineering—pretending to be someone trustworthy. For example, they might email a fake invoice asking for payment or try to scam you into giving up cryptocurrency or access to your wallet.
Phishing Example
Sent from an onmicrosoft.com email address.
“You have a package that needs to be delivered, but it has been suspended due to an incorrect delivery address.”
Likely links to a fake U.S. Postal Service site or another malicious website that may try to install malware or steal your information.
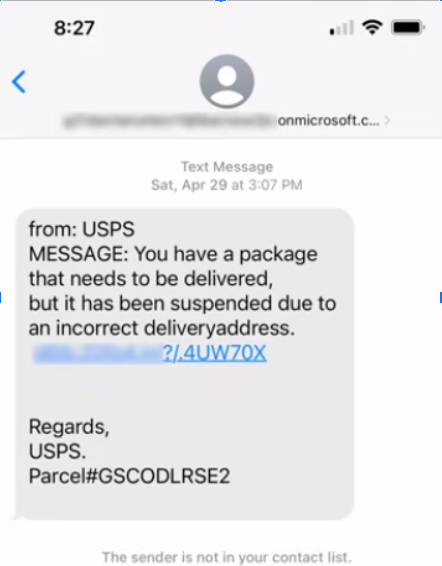
Image-Based Vectors
Are harder to identify compared to text-based ones
SVG (Scalable Vector Graphics) is a format that can pose a risk, as it is an XML file describing the image and can contain embedded data.
Attackers can inject malicious HTML or JavaScript into this XML description, which may execute when viewed in a browser.
Some browsers allow the disabling of specific image types or offer input validation for SVG files to help mitigate this risk.
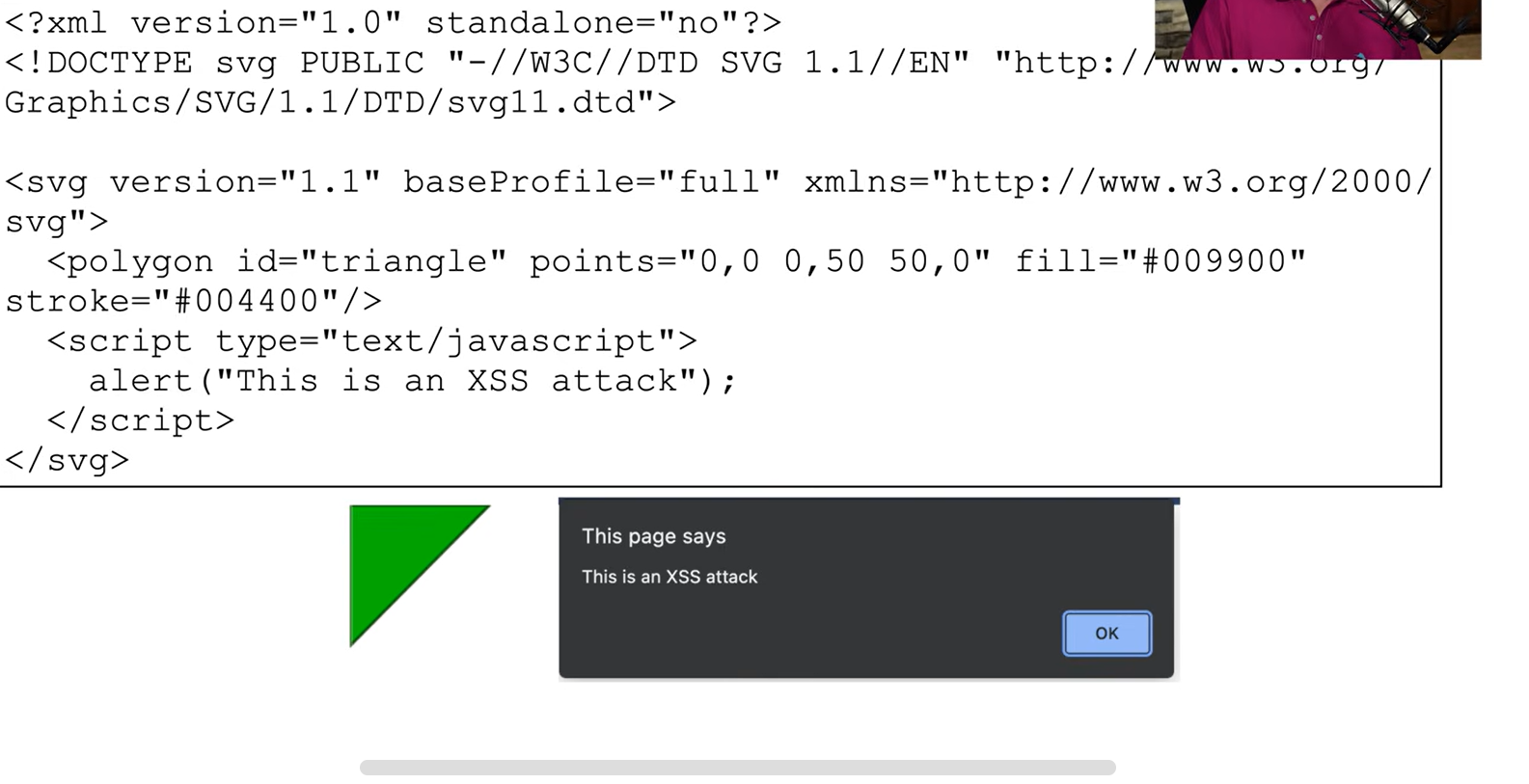
SVG / XML Example:
An SVG/XML file can display an image, like a triangle, while secretly running embedded JavaScript.
Most modern browsers prevent such scripts from executing, but if the browser has a vulnerability or the script isn't recognized as cross-site scripting, the malicious code could bypass the security and execute through the XML embedding.
In this example, the JavaScript simply displays a message saying, "This is a cross-site scripting attack."
File-Based Vectors
Malicious code can hide in many file types beyond just executables.
Adobe PDFs can contain scripts along with text and images, making them a potential attack vector.
ZIP or RAR files obfuscate malicious content by compressing it, potentially hiding harmful software within multiple files.
Microsoft Office documents with macros can be used to gather personal information and send it to attackers
Browser extensions or add-ins can also carry malicious software, putting your system at risk once added.
Voice-Based Vectors
Include vishing, where attackers use phone calls to trick individuals into revealing personal details like credit card information.
Spam over IP involves large-scale, automated phone calls or messages
War dialing; dialing many phone numbers to find open modems or internet-connected devices, and it still occurs today.
Call tampering involves disrupting or interfering with voice calls.
Removable Device Vectors
Attackers can bypass costly security systems with a simple USB drive.
By dropping infected USB drives in a company's parking lot, they hope someone will pick one up, plug it in, and infect the system.
These devices can be used to infect air-gapped networks, including industrial or high-security systems.
USB devices can also act as keyboards, allowing malicious software to automatically type commands on the system
Data exfiltration; terabytes of data walk out the door, zero bandwidth used.
Vulnerable Software Vectors
Include client-based and agentless systems.
Client-based software may have security flaws that need regular updates, as attackers can exploit known or unknown vulnerabilities to gain access.
Agentless systems don't require software to be installed on the client device; instead, users access the system through a browser/third party.
If an attacker compromises the central server, they can potentially infect all connecting clients.
Since the software runs on the server, it's easier for attackers to distribute malicious software, knowing each user runs a new instance daily.
Unsupported System Vectors
When a system is no longer supported by the manufacturer, it stops receiving essential security patches; pose a significant security risk.
Outdated operating systems may have unaddressed vulnerabilities that attackers can exploit.
Maintain an up-to-date inventory to identify unsupported systems in your network or data center.
Even a single unpatched system could become an entry point for attackers.
Unsecure Network Vectors
Allow attackers to move freely within your network by exploiting vulnerabilities in the infrastructure.
Without encryption, attackers can view all data transmitted.
For wireless networks, outdated security protocols like WEP, WPA, and WPA2 should be replaced with WPA3.
Open or rogue networks are also vulnerabilities.
Networks may lack security if there’s no 802.1X authentication for user access.
Bluetooth may have insufficient security, making it a potential entry point for attackers / can provide an attacker sight to where a particular system might be.
Open Service Ports
When ports are opened, they allow external access to the system, which is usually protected by security measures. However, if an attacker knows a vulnerability in the software using those ports, they can exploit it.
Misconfigurations in complex applications can also inadvertently expose a system.
The more services installed, the more open ports, increasing the system's attack surface.
To mitigate risks, port-based or application-aware firewalls can restrict external access to specific services, reducing potential attack vectors.
Default Credentials
If these are not changed, attackers can easily gain access to the system.
Are often publicly available and can be found on sites like routerpasswords.com
Update these credentials to prevent unauthorized access.
Supply Chain Vectors
Allow attackers to infiltrate your network through third-party vendors or contractors.
Can compromise infrastructure or manufacturing processes, gaining access through the systems or equipment you're installing.
If a Managed Service Provider (MSP) manages your network, they can also become a target. Once attackers gain access to the MSP, they can infiltrate your systems.
A notable example is the 2013 Target credit card breach, where attackers accessed Target’s network through an HVAC contractor.
Counterfeit networking equipment, like the 2020 fake Cisco Catalyst switches, can introduce backdoors and performance issues.