2-3 cisco quizzes
1/82
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
83 Terms
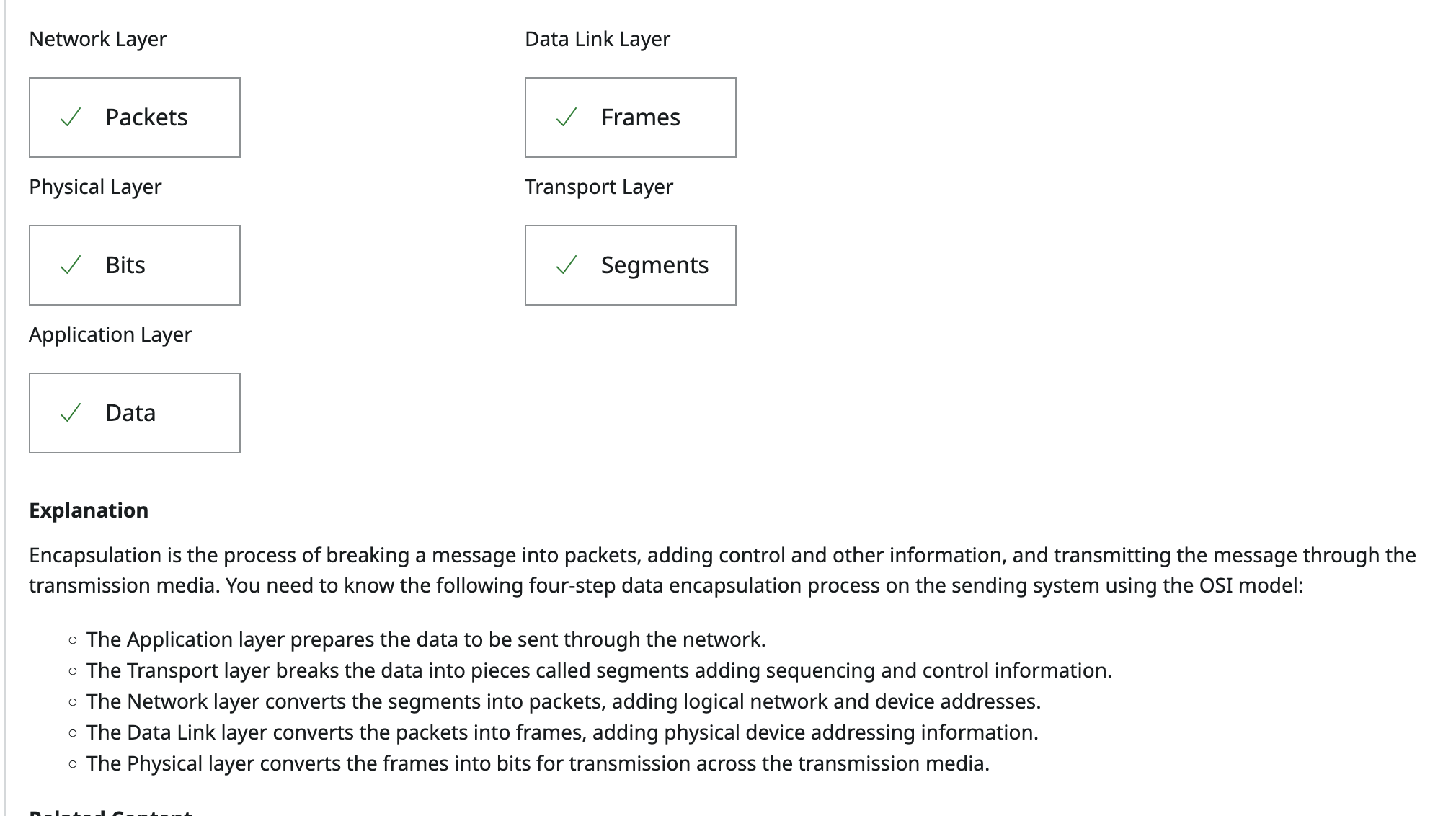
Drag the information type on the left to the appropriate layer of the OSI model that it is associated with on the right.
Network Layer
Data Link Layer
Physical Layer
Transport Layer
Transport Layer
Application Layer
Packets
Frames
Bits
Segments
Data
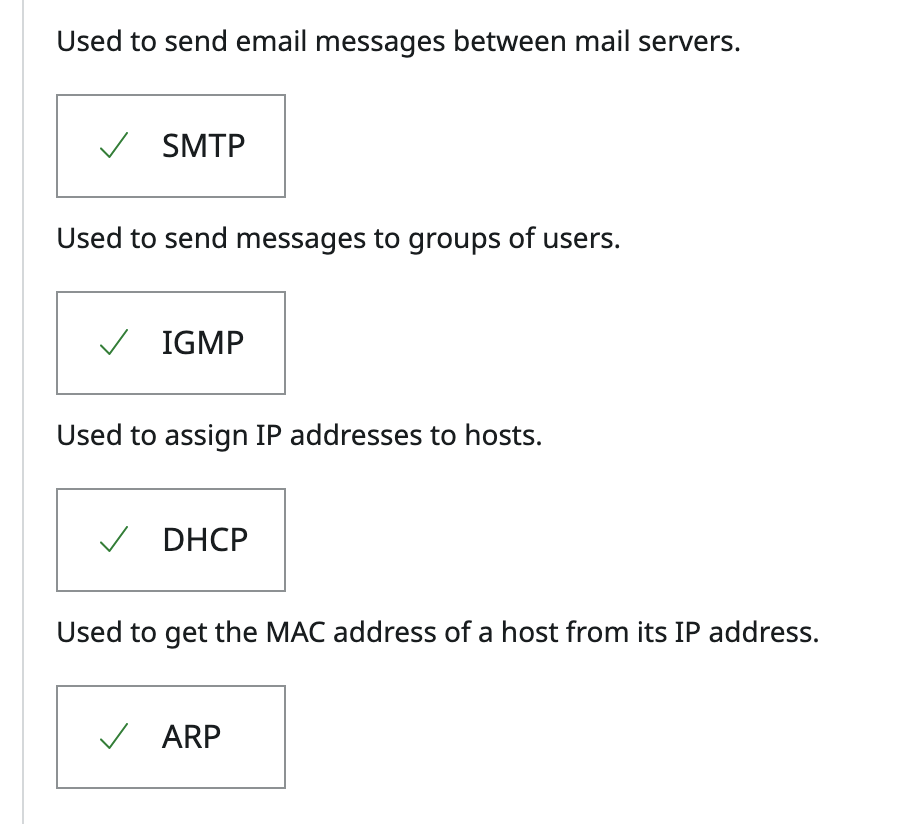
Match the TCP/IP protocols with their sunctions.
Used to send emails messages between mail servers
Used to send messages to groups of users
Used to assign IP addresses to Hosts
Used to get the MAC address of a host from its IP Address
SMTP
IGMP
DHCP
ARP
The following items describe the functions performed at various OSI model layers:
Logical topology, hardware addresses, media access, framing
Logical device identification, path identification, and selection
Flow control, reliable data transfer, windowing, segmentation, and sequencing
Converting data to 0s and 1s, bit signaling, and synchronization
Which of the following correctly identifies, in order, the layers that perform each of the functions listed here?
Dara LInk, Network, Transport, Physical

Which two of the following functions are performed by IP? (Select two.)
creating multicast groups
routing datagrams to their destination
Delivering IP addresses to host
Identifying host with the IP address
routing datagrams to their destination
Identifying host with the IP address
IP is responsible for moving data through the network. It identifies devices by their IP addresses and routes datagrams based on this address. The other functions listed here are performed by other protocols in the TCP/IP suite.
Put the OSI layer is order
7
6
5
4
3
2
1
7 - Application
6- Presentation
5 - Session
4- Transport
3 - Network
2 - Data Link
1 - Physical
A client computer starts to download some files from an FTP server named FTPsvr1. While the first download is in progress, the user opens a second instance of the FTP program and initiates a second download.
What do the server and the client use to keep each download separate?
Session ID
Which of the following are limitations of the OSI model? (Select two.)
OSI layers are not theoretical and actually perform real functions.
Requires specialization of features at different levels.
OSI layers are theoretical and do not actually perform real functions.
A particular protocol implementation may not represent every OSI layer.
OSI layers are theoretical and do not actually perform real functions.
A particular protocol implementation may not represent every OSI layer.
The following are limitations of the OSI model:
OSI layers are theoretical and do not actually perform real functions.
Industry implementations rarely have a layer-to-layer correspondence with the OSI
layers.
Different protocols within the stack perform different functions that help send or
receive the overall message.
A particular protocol implementation may not represent every OSI layer (or may
spread across multiple layers).
What is the purpose of the CRC in network communications?
Detect data errors
Match the TCP/IP protocols with their functions.
Used to get the IP address of a host from a known MAC address.
Used to Transfer Files
Used to Identify routes through an internetwork
BOOTP
OSPF
RARP
RIP
FTP
TFTP
Used to get the IP address of a host from a known MAC address.
BOOTP
RARP
Used to Transfer Files
FTP
TFTP
Used to Identify routes through an internetwork
OSPF
RIP
Which of the following are functions of the MAC sublayer in the OSI model? (Select two.)
Letting devices on the network have access to the LAN.
Defining a unique hardware address for each device on the network.
An internet server has a single network interface that has been assigned an IP address. The server is running both the FTP and HTTP services. A client computer initiates a session with the HTTP server.
How is the HTTP request from the client routed to the correct service running on the server?
Port or socket number
Port or socket numbers are used to identify a service running on the server. For example, FTP uses ports 20 and 21 to send communications to the FTP service running on the server, while port number 80 is used for HTTP.
What is the purpose of a network model?
Standardize processes at each layer.
Match each tcp and / or UDP ports to the service that uses it
Dynamic Host Configuration Protocol (DHCP)
Network News Transport Protocol (NNTP)
Simple Network Management Protocol (SNMP)
Domain Name System
TEL NET
TFTP
TCP and UDP use port 23 for Telnet
TCP and UDP use port 53 for Domain Name System (DNS)
UDP uses ports 67 and 68 for Dynamic Host Configuration Protocol (DHCP)
UDP uses port 69 for Trivial File Transfer Protocol (TFTP)
TCP uses port 119 for Network News Transport Protocol (NNTP)
UDP uses ports 161 and 162 usually for Simple Network Management Protocol (SNMP)
Which of the following lists accurately describes TCP and UDP? (Select two.)
TCP: connection-oriented, reliable, sequenced, high overhead
UDP: connectionless, unreliable, unsequenced, low overhead
UDP: connection-oriented, reliable, sequenced, high overhead
TCP: connection-oriented, reliable, unsequenced, lov overhead
TCP: connection-oriented, reliable, sequenced, high overhead
UDP: connectionless, unreliable, unsequenced, low overhead
TCP characteristics include:
• Connection-oriented
• Reliable
• Sequenced
• High overhead
UDP characteristics include:
• Connectionless
• Unreliable
• Unsequenced
• Low overhead
Match each layer of the TCP/IP model to its functions. (Each layer matches with two functions.)
Is responsible for how messages are electrically transmitted.
Is responsible for forwarding packets through multiple networks.
Is responsible for describing the physical layout of the network.
Is responsible for error checking and reliable delivery.
Is not concerned with reliable delivery of information.
Integrates network functionality into the host operating system.
Provides the capability for services to operate on the network.
Uses ports to enable application-to-application communications between hosts.
Is responsible for how messages are electrically transmitted.
LINK
Is responsible for forwarding packets through multiple networks.
INTERNET
Is responsible for describing the physical layout of the network.
LINK
Is responsible for error checking and reliable delivery.
TRANSPORT
Is not concerned with reliable delivery of information.
INTERNET
Integrates network functionality into the host operating system.
APPLICATION
Provides the capability for services to operate on the network.
APPLICATION
Uses ports to enable application-to-application communications between hosts.
TRANSPORT
Which of the following are limitations of the TCP/IP model? (Select two.)
Divides networking tasks into logical layers.
TCP/IP layers are theoretical and do not actually perform real functions.
Forces modularity in networking features.
A particular protocol implementation may not represent every layer.
Does not aid in troubleshooting.
TCP/IP layers are theoretical and do not actually perform real functions.
A particular protocol implementation may not represent every layer.
The TCP/IP protocol stack uses port numbers to determine protocol use. Port usage is regulated by the Internet Corporation for Assigning Names and Numbers (ICANN). Which of the following are characteristics of registered ports? (Select two.)
Has port numbers ranging from 0 to 1023.
Has port numbers ranging from 1024 to 49151.
Is assigned by ICANN for a network service.
Has port numbers ranging from 49152 to 65535.
Has port numbers ranging from 1024 to 49151.
Is assigned by ICANN for a network service.
Which of the following methods helps to detect lost packets? (Select two.)
Acknowledgements
Sequencing
Flow control
CRC
Acknowledgements
Sequencing
How does TCP handle data sequencing ?
TCP breaks user data into segments, numbers each segment, places them in the correct sequence, and sends each one in order, waiting for an acknowledgement before sending the / Correct next segment.
You need to connect several network devices together using twisted pair Ethernet cables. Assuming Auto-MDIX is not enabled on these devices, drag the appropriate type of cabling on the left to each connection type on the right.
WORKSTATION TO SWITCH
ROUTER TO SWITCH
SWITCH TO SWITCH
WORKSTATION TO ROUTER
ROUTER TO ROUTER
If Auto-MDI/MDIX is not enabled, then you must use a crossover Ethernet cable when connecting the following devices:
Switch to switch
Switch to hub
Hub to hub
Workstation to router
Workstation to workstation
Router to router
Use a straight-through Ethernet cable to connect the following devices:
Workstation to hub
Workstation to switch
Router to hub
Router to switch
You want to implement an Ethernet network using the 1000BaseT standard using the minimum hardware specifications possible. Which of the following should you include in your plan? (Select two.)
Cat4 twisted pair cable
Cat5 twisted pair cable
Cat5e twisted pair cable
RJ-45 connectors
Cat5e twisted pair cable
RJ-45 connectors
You have a small network with two switches, SwitchA and SwitchB. MDI-X is not enabled on either switch. Each switch has three client computers connected. IP addresses have been assigned to various devices as follows:
WrkA_1, WrkA_2, and WrkA_3 are connected to SwitchA, while WrkB_4, WrkB_5, and WrkB_6 are connected to SwitchB. All of the devices are configured to operate within the same subnet.
You need to connect SwitchA and SwitchB so that workstations connected to SwitchA can communicate with workstations connected to SwitchB. What should you do?
Connect SwitchA and SwitchB using a crossover cable
Match each characteristic on the left with the appropriate fiber optic connector on the right.
Metal guide pins for alignment
Half the size of other connectors
V Bayonet-type connector
Push-on, pull-off connector
MT-RJ
Metal guide pins for alignment
LC
Half the size of other connectors
ST
V Bayonet-type connector
SC
Push-on, pull-off connector
Question 6
Which of the following are features of multimode fiber cable? (Select three.)
Transfers data through the core using a single light ray
Supports cable lengths that extend a great distance
Has a core diameter around 10 microns
Supports only limited distance cable lengths
Typically used for connecting networks between buildings
Has a core diameter around 50 to 100 microns
Transfers data through the core using multiple light rays
Has a core diameter around 50 to 100 microns
Transfers data through the core using multiple light rays
Supports only limited distance cable lengths
Which fiber optic cable requires the exposed fiber tip to be polished as part of the assembly process?
Only plastic core fiber connectors
Field terminated epoxy connectors
Pre-polished connectors
RJ-45 connectors
Field terminated epoxy connectors
You want to implement an Ethernet network using the 100Base-FX standard and the minimum hardware specifications possible. You need to support distances of up to 1,000 meters without repeaters.
Which of the following should you include in your plan? (Select two.)
Multi-mode fiber optic cable
RJ-45 connectors
Cat4 twisted pair cable
Cat5 twisted pair cable
SC connectors
Single-mode fiber optic cable
SC connectors
Single-mode fiber optic cable
Which pins are used in a Cat 5 Ethernet (100BASE-T) UTP cable?
2, 5, 6, and 9
1, 2, 3, and 6
1, 3, 4, and 7
4, 5, 7, and 8
1, 2, 3, and 6
You are deploying a new 10GB Ethernet network using Cat 6 cabling.
Which of the following are true concerning this media? (Select two.)
It uses twisted 18- or 16-gauge copper wiring.
It is completely immune to EMI.
It supports multi-mode transmissions.
It supports 10 GB Ethernet connections.
PVC insulation surrounds each copper wire.
It supports 10 GB Ethernet connections.
PVC insulation surrounds each copper wire.
What is the purpose of a frame check sequence (FCS) footer?
Contains logical network addresses
Checksum error detection
Holds segment data
Control information
Checksum error detection
What role does ARP play in the routing process?
ARP does not play any role in the routing process. Switches use ARP to map IP addresses to MAC addresses in collision domains.
If a router does not know a destination device's IP address, it sends an ARP broadcast containing the destination device's MAC address and requesting its IP address.
If a router knows the MAC and IP address of a destination host, it sends an ARP request to update the other routers' route tables.
If a router does not know a destination device's MAC address, it sends an ARP broadcast containing the destination device's IP address and requesting its MAC address.
If a router does not know a destination device's MAC address, it sends an ARP broadcast containing the destination device's IP address and requesting its MAC address.
Routing data between computers on a network requires several mappings between different addresses. Which of the following statements is true?
IMP lets routers bypass the general network broadcast by providing a dynamic table of IP-to-MAC address mappings.
Routers use DNS to resolve MAC addresses of diskless workstations into IP addresses based on the information contained in other routers' route tables.
Diskless workstations use ARP to ask a server for an IP address.
Routers use ARP to resolve known IP addresses into MAC addresses.
Routers use ARP to resolve known IP addresses into MAC addresses.
What term does the OSI model use that is different from the TCP/IP model uses to refer to frame, packet, and segment?
Protocol data unit (PDU)
IEEE Ethernet standard
Presentation
Session
Protocol data unit (PDU)
During network transmission, data is transferred to various routers, which forward the data to the appropriate network. If the source and destination network addresses reside on the same network, which protocol is used to determine the MAC address of the destination IP address?
UDP
TCP
HTTP get
ARP
ARP
The process of breaking a message into packets, adding control information and other information, and then transmitting the message through the transmission medium is known as
Sequencing
Segmentation
Transformation
Encapsulation
Encapsulation
Drag the information type on the left to the appropriate layer of the TCP/IP model it is associated with on the right.
Transport Layer
Link Layer
Application Layer
Internet Layer
Frames
Data
Packets
Segments
Transport Layer- segments
Link Layer - frames
Application Layer - data
Internet Layer- packets
What is the first thing that happens when a collision occurs on an Ethernet network?
All devices that were sending data transmit a clear to send (CTS) message.
The device that detected the collision transmits a jam signal.
All devices wait a random amount of time before trying to retransmit.
The device that detected the collision transmits a jam signal.
Which two of the following statements accurately describe half-duplex Ethernet? (Select two.)
It uses direct point-to-point connections between the sender and receiver.
It lets you use 100% of the available bandwidth for data transmission.
It uses collision detection and recovery.
It sends both signals along the same wire.
It uses collision detection and recovery.
It sends both signals along the same wire.
Which of the following is true of CSMA/CD? (Select two.)
If collisions are detected, an interrupt jam signal is broadcast to stop all transmissions.
Only devices with information to send have access to the transmission media.
Two devices can transmit at the same time without collisions occurring.
After a collision, sending devices run the same algorithm before sending their messages again.
A device with data to send first listens to the transmission medium to determine whether is free
Only devices with information to send have access to the transmission media.
A device with data to send first listens to the transmission medium to determine whether is free
Which two of the following statements accurately describe full-duplex Ethernet? (Select two.)
It uses built-in loopback and collision detection.
It uses 75% of the available bandwidth for actual signal transmission.
It is collision-free.
It multiplexes signals along the same wire for higher transmission speeds.
It uses direct point-to-point connections between the sender and receiver.
It is collision-free.
It uses direct point-to-point connections between the sender and receiver.
As specified in the Ethernet standards, what is the maximum number of hosts supported on a single subnet?
1024
Which of the following are true about Gigabit Ethernet? (Select two.)
Uses CSMA/CD
Requires fiber optic
Uses CSMA/CA
Can use both copper and fiber optic
Uses CSMA/CD
Can use both copper and fiber optic
What is the maximum cable length for UTP Ethernet T implementations?
100meters
What is the backoff on an Ethernet network?
The random amount of time a device waits before retransmitting after a collision.
Which of the following mechanisms are used on Ethernet networks to control access to the transmission medium? (Select two.)
Collision detection
Token
Request to send/clear to send (RTS/CTS)
Backoff
Collision detection
Backoff
Why is a DNS server essential in a network environment?.
It translates human-readable domain names into IP addresses.
How does Linux differ from Windows Server in managing server roles?
Linux uses configuration files and CLI, while Windows uses GUI tools like Server Manager.
Which of the following are general advantages of using routers on your network? (Select three.)
Routers provide multiple links between devices to support load balancing.
Routers provide more features, such as flow control, error detection, and congestion control, than switches or bridges.
Routers support multiple routing protocols for better flexibility.
Which is the primary role of a firewall?
To protect networks and workstations by allowing or denying network traffic. The firewall does this using a configured set of rules.
You have been put in charge of connecting two company networks that were previously separated.
You need to connect a 100BaseTx Ethernet network with an older token ring network. Most traffic will be localized within each network, with only a little traffic crossing between networks. Both networks are using the TCP/IP protocol suite.
Which connectivity device would be the best choice in this situation?
Router
Which of the following describes the function of a dedicated wireless access point on a network?
On a network, a wireless access point only acts as a bridge between the wireless segment and the wired segment on the same subnet.
What’s is the primary function of a dhcp sever in a network?
Automatically assign IP addresses to devices
Which of the following is a key feature of windows server for managing server roles?
Server manager
Which of the following statements are true about bridges? (Select two.)
Bridges connect two networks that use different protocols.
Bridges connect two network segments with the same network address.
Bridges convert one type of transmission medium into another.
Bridges connect two network segments with the same network address.
Bridges convert one type of transmission medium into another.
At which layer of the OSI model do network switches operate that do not support routing ?
Data link
You want to make a console connection to a router using the serial port on a PC. Select the necessary components to make the console connection. Select only the necessary components.
Components
Terminal emulation program
Rollover cable
Console port
Put the boot sequence process items in order
1
Power-on self-test checks hardware.
2
Boot loader software is loaded.
3
IOS is loaded.
4
Startup-config is loaded.
You are a network administrator configuring a new switch in your organization's network. The switch supports both Telnet and SSH for remote management.
To ensure secure access, you decide to enable SSH.
Which of the following actions should you take to properly implement SSH on the switch?
Configure a strong username and password, and disable Telnet on the switch.
Match the defition
RAM
FLASH
ROM
NVRAM
RAM stores the running-configuration file, routing tables, and ARP tables.
FLASH stores the Cisco IOS software.
ROM stores POST and the boot loader software.
NVRAM stores the startup-configuration file.
You have issued the following command and received the response as shown.
Router#sh start
%%Non-volatile configuration memory has not been set up or has bad checksum
Which of the following is a reason for this response?
No configuration file has been saved to NVRAM.
You are a network administrator tasked with configuring a legacy router in a small office network. The router only supports Telnet for remote access, and you need to make some urgent configuration changes.
Which of the following actions should you take to minimize security risks while using Telnet?
Use Telnet over a secure VPN connection to access the router.
You are troubleshooting a network switch that has lost remote connectivity due to a misconfiguration. Remote access methods such as SSH and HTTPS are no longer functional.
Which of the following actions should you take to regain access to the switch and resolve the issue?
Connect a console cable to the switch and access it through a terminal application on your computer.
You are managing a wireless controller for your organization's network. The controller supports both HTTP and HTTPS for web-based management.
To ensure secure access, you decide to configure HTTPS.
Which of the following actions should you take to properly implement HTTPS on the wireless controller?
Install a valid SSL/TLS certificate on the wireless controller and disable HTTP access.
Which of the following measures can you implement to help secure access to a router?
Keep the router in a locked room.
Set a password and use the login command.
You are a field technician for a large company. You have been sent to a remote site to troubleshoot a downed router. When you arrive at the remote site, how will you connect your laptop to the router?
Connect the laptop's COM/USB port to the router's console port using a rollover cable.
While working at the console of a Cisco device, you need to view a list of the commands that are currently stored in the history buffer of the s)
Which command should you use?
Show history
While working at the console of a Cisco device, you need to view a list of the commands that are available in the current mode.
Which command should you use?
?
You want to save the configuration file in NVRAM to a TFTP server with address 192.168.1.10 to be used as a backup. Which command would you use?
• copy start tftp
You need to back up the current IOS image on your router to the TFTP server. The TFTP server's IP address is 192.56.145.23. Which of the following commands do you use?
Copy flash tftp
You want to look at the size of the configuration files. Which command would you use?
Show flash
Match each command to its corresponding operation.
Save the current configuration to NVRAM.
copy run start
Load the current configuration saved in NVRAM into memory.
copy start run
Save the current configuration to a network server.
copy run tftp
Copy a configuration file from a network server into NVRAM.
copy tftp start
While working at the console of a Cisco device, you need to use the same command repeatedly.
Given that the command is quite long, what can you do to avoid having to retype it over and over?
Press the Up arrow key.
Which command would you use to remove the contents of NVRAM?
Erase NVRAM
Which of the following configuration register values tells the router to use configuration information from NVRAM?
0×2102
Which of the following commands configures a password to switch to privileged EXEC mode and saves the password using MD5 hashing?
Enable secret
What is the main security weakness associated with the service password-encryption command?
Passwords are easily broken
Which of the following is the most important thing to do to prevent console access to the router?
Keep the router in a locked room.
Router (config)#enable password cisco
Router (config)#enable secret highway
Router (config)#username admin password television
Router (config)#line con 0
Router (config-line)#password airplane
Router (config-line)#login
Router (config-line)#line vty 0 4
Router (config-lide)#password garage
Router (config-line)#login
Which password would you use to open telnet session to the router?
Garage
You want users to enter a password before being able to access the router through a Telnet session. You use the following commands: router#config t router (config)#line vty 0 4 router (config-line)#password cisco router (config-line)#exit router (config) #exit
You open a Telnet session with the router and discover that the session starts without being prompted for a password. What should you do?
In line configuration mode, add the login parameter
You are at a customer site and need to access their router. The previous administrator left the company and did not document the password to the device.
Which of the following would you access to start the password recovery process?
ROMmon
One of the steps in the password recovery process for a router is to access the ROM monitor. Which of the following methods will accomplish this? (Select two.)
Use a break sequence during the boot process.
Remove the external flash memory while the device is powered off and then boot.
After configuring a router to ignore the startup configuration when the device boots, what command would you use to tell the device to load the startup configuration upon boot?
confreg 0x2102
As part of the password recovery process on a router, you want the device to ignore the startup config file when the device is rebooted. Which of the following commands would you use to do this?
Confreg 0×2142
You want to prevent users from accessing a router through a telnet session. What should you do?
For the vty lines, add the login parameter and remove any passwords