CCNA 3 Moadule (3-5) Part 7
1/7
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
8 Terms
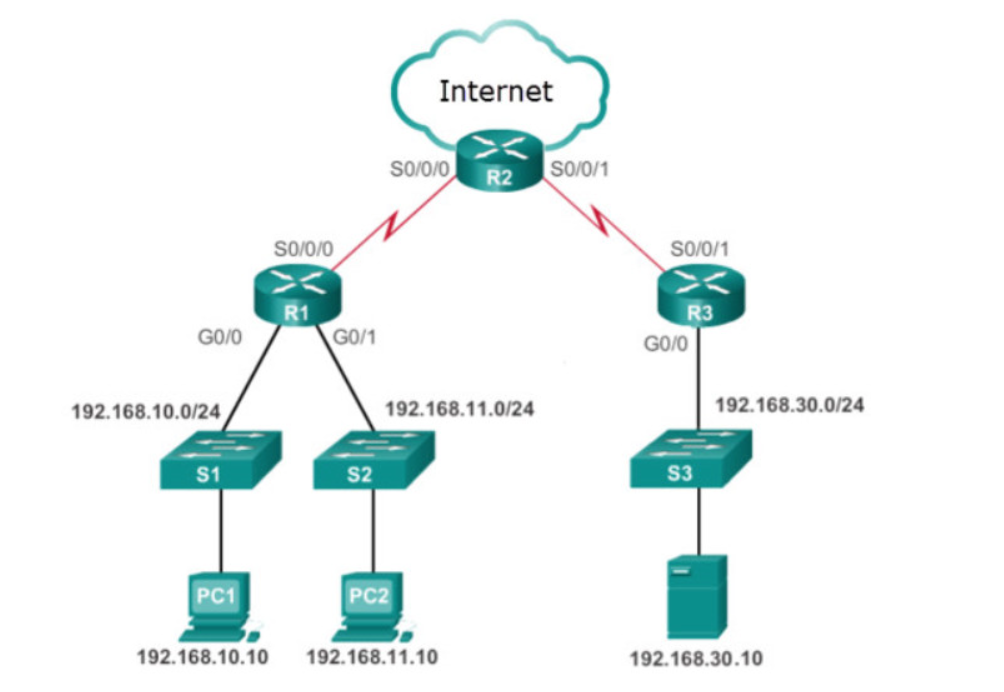
Refer to the exhibit. The company CEO demands that one ACL be created to permit email traffic to the internet and deny FTP access. What is the best ACL type and placement to use in this situation?
extended ACL outbound on R2 WAN interface towards the internet
A technician is tasked with using ACLs to secure a router. When would the technician use the established configuration option or command?
to allow returning reply traffic to enter the internal network
A technician is tasked with using ACLs to secure a router. When would the technician use the deny configuration option or command?
to restrict specific traffic access through an interface
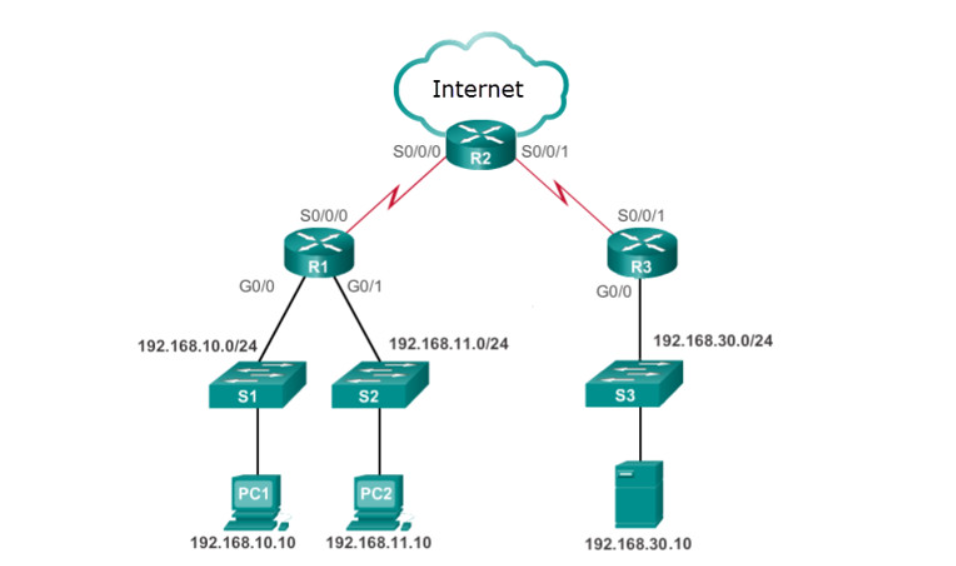
Refer to the exhibit. Only authorized remote users are allowed remote access to the company server 192.168.30.10. What is the best ACL type and placement to use in this situation?
extended ACL inbound on R2 WAN interface connected to the internet
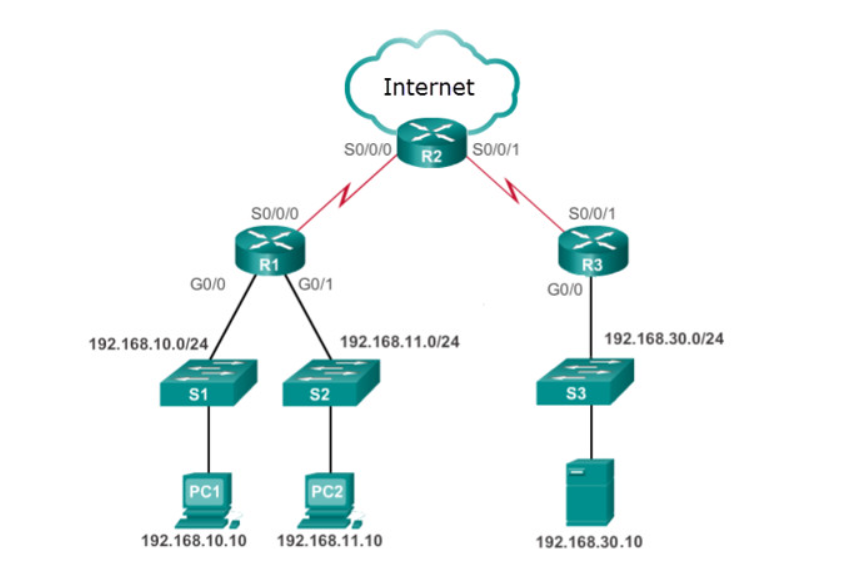
Refer to the exhibit. Employees on 192.168.11.0/24 work on critically sensitive information and are not allowed access off their network. What is the best ACL type and placement to use in this situation?
standard ACL inbound on R1 G0/1
A technician is tasked with using ACLs to secure a router. When would the technician use the host configuration option or command?
to identify one specific IP address
What commonly motivates cybercriminals to attack networks as compared to hacktivists or state-sponsored hackers?
financial gain
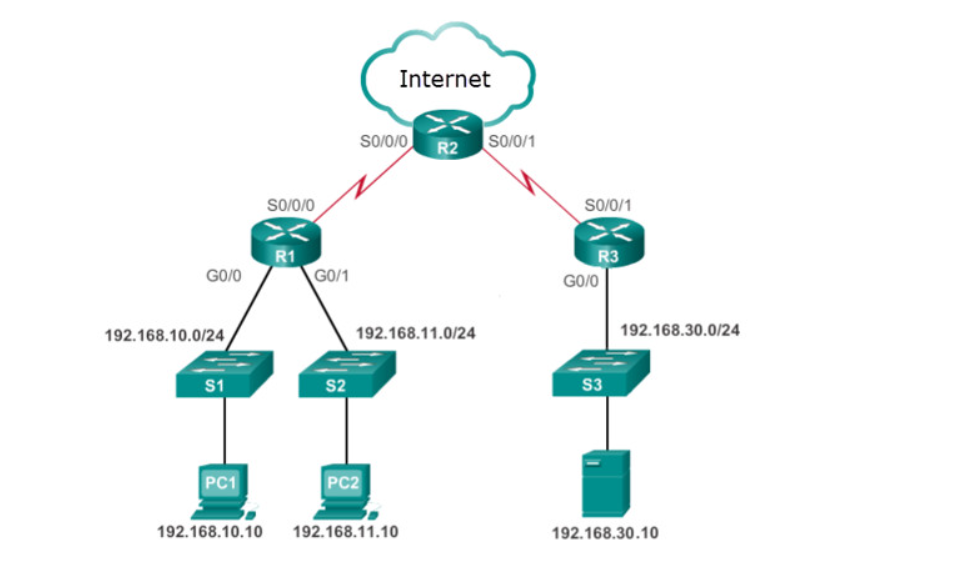
Refer to the exhibit. The company has provided IP phones to employees on the 192.168.10.0/24 network and the voice traffic will need priority over data traffic. What is the best ACL type and placement to use in this situation?
extended ACL inbound on R1 G0/0