FBLA - Digital Citizenship
1/53
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|

54 Terms
Anti-virus software
Used to block malicious (bad) programs, such as viruses or malware, from harming your computer.

Avatar
A graphic (picture or image) that you use to represent yourself on the internet.

Boundaries
Physical, emotional and mental limits we set to protect ourselves from being manipulated, used, or harmed by others.

Bully
Someone who acts in an aggressive, hostile or hurtful way towards others.

Bystander
A person who witness the actions of a bully and the reaction of the victim(s), without taking action.

Citation
Listing the source of specific information you have used for a project or writing assignment.
Citizenship
Being a member of and supporting your community and country. This comes with both rights and responsibilities.

Copyright
A owner's legal protection to anything they create.

Creative Commons
A license that allows you to decide how other may use your work. You keep your copyright, but allow others to copy and distribute your work provided they give you credit and only follow the conditions you specify.

Cyberbullying
Using digital media tools such as the Internet and cell phones to deliberately and repeatedly hurt, harass or embarrass someone else.

Digital Footprint
A trail of data you (unintentionally) create while using the Internet. In includes the websites you visit, emails you send, and information you submit to online services...etc. It cannot be edited or deleted. All of the information online about a person either posted by that person or others, intentionally or unintentionally.

Downloading
The process of transferring files from a website/Internet location to your personal computer/device.

Emoticon or Emoji
A simple face or image, sometimes animated, that expresses an emotion.
Empathy
Being aware of, sensitive to, and understanding what someone else is feeling or experiencing.

Fair Use
The idea that copyright material may be quoted without the need for permission from or payment to the original source, provided that a citation is clearly given and the material quoted is reasonably brief.

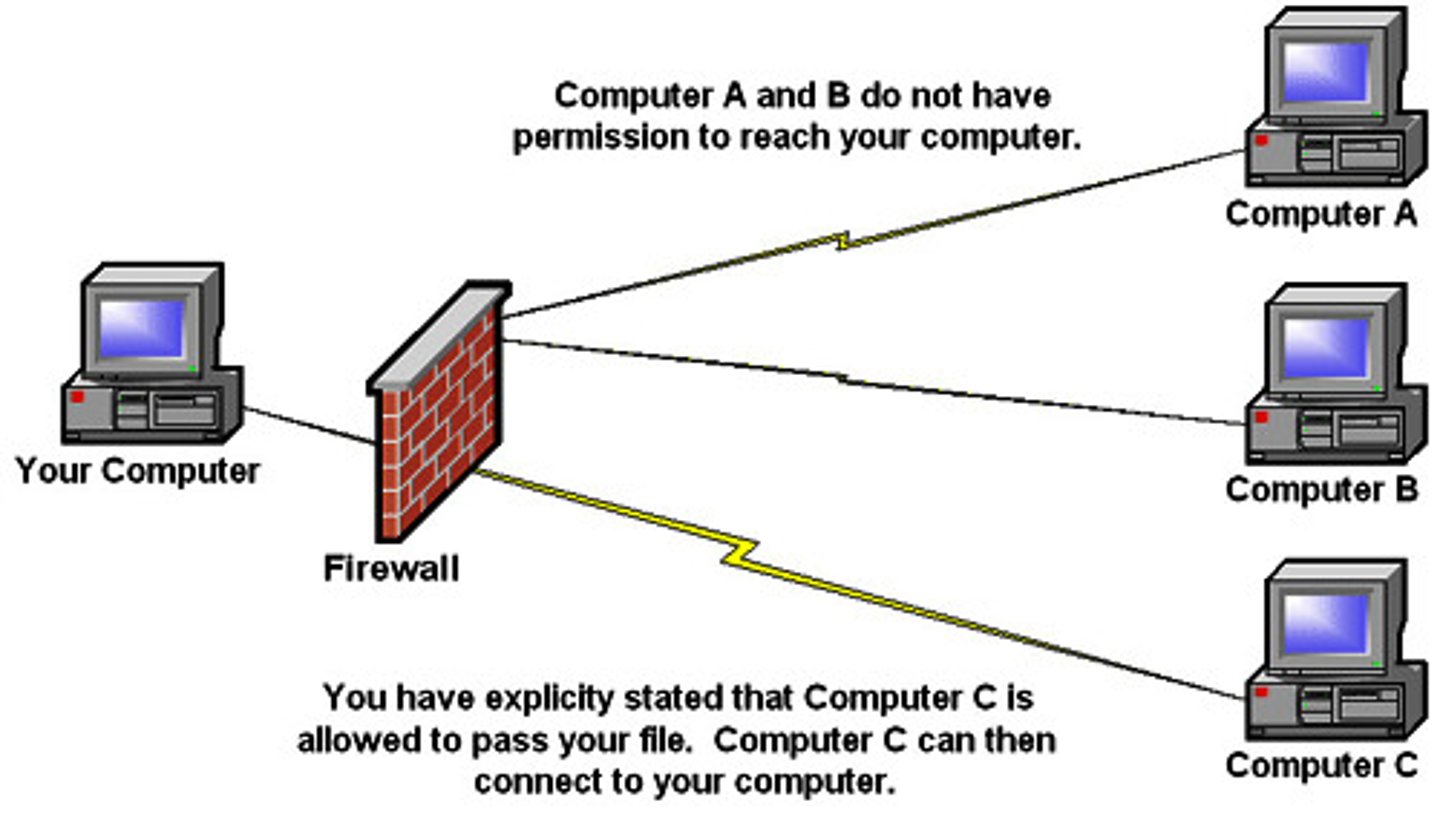
Firewall
Hardware or software that blocks or filters certain types of network traffic from reaching your computer/device.
Flaming
A mean spirited message sent to others on the Internet

Grooming
Techniques used by predators to try to gain your trust.

Hacker
A person who accesses computer information without permission.

Harassment
To annoy someone repeatedly.

Hardware
A term for the actual computer equipment and computer parts.
Identity Theft
A crime that happens when someone gets the personal information (credit card, social security number, bank account) of another person, usually to steal money.

Intellectual Property
Art, books, inventions, magazines, movies, music, performances, reports, software, stories created by you or by others.

Jeopardize or Jeopardizing
To put something at risk, such as your reputation or digital footprint.

Keyword
A word you use when looking for information on a search engine (Google, Yahoo, etc.)

Malicious
Means to cause harm to someone or something on purpose.

Malware
Malicious software or code (trojan horses, worms, spyware, adware, etc.) that is design to damage a computer/device or collect information.

Media Literacy
The ability to access, analyze, evaluate and create media in a variety of forms.

Netiquette
Courtesy, honesty and polite behavior while on the Internet

Open Source
Programming code with limited or no copyright restrictions, allowing you legally modify and share the software program.

Password
The secret word or combination of letters, numbers and symbols you use to sign in to the Internet or an online service to help confirm your identity.

Phishing
Techniques that scammers use to collect personal information from unsuspecting users. They may use false emails or websites where you have to enter information, that look real.

Piracy, Pirating
Theft of intellectual property. In other words, stealing what does not belong to you. Usually, refers to music and videos.

Plagiarism
Using someone else's words or ideas and passing them off as your own.

Predator
One who stalks or uses lies, secrecy, or stealth, to get close enough to another person in order to easily hurt or harm them.

Privacy
Your right to determine what information you would like others to know about you.

Search Engine
A program that searches information on the Internet by looking for specific keywords.

Software Patch
An upgrade, bug fix, a new hardware driver or update to fix new issues such as security or stability problems.
Spyware
Software that goes on your computer/device without your knowledge and steals private information.

Tolerance
Respecting those that are different from you.

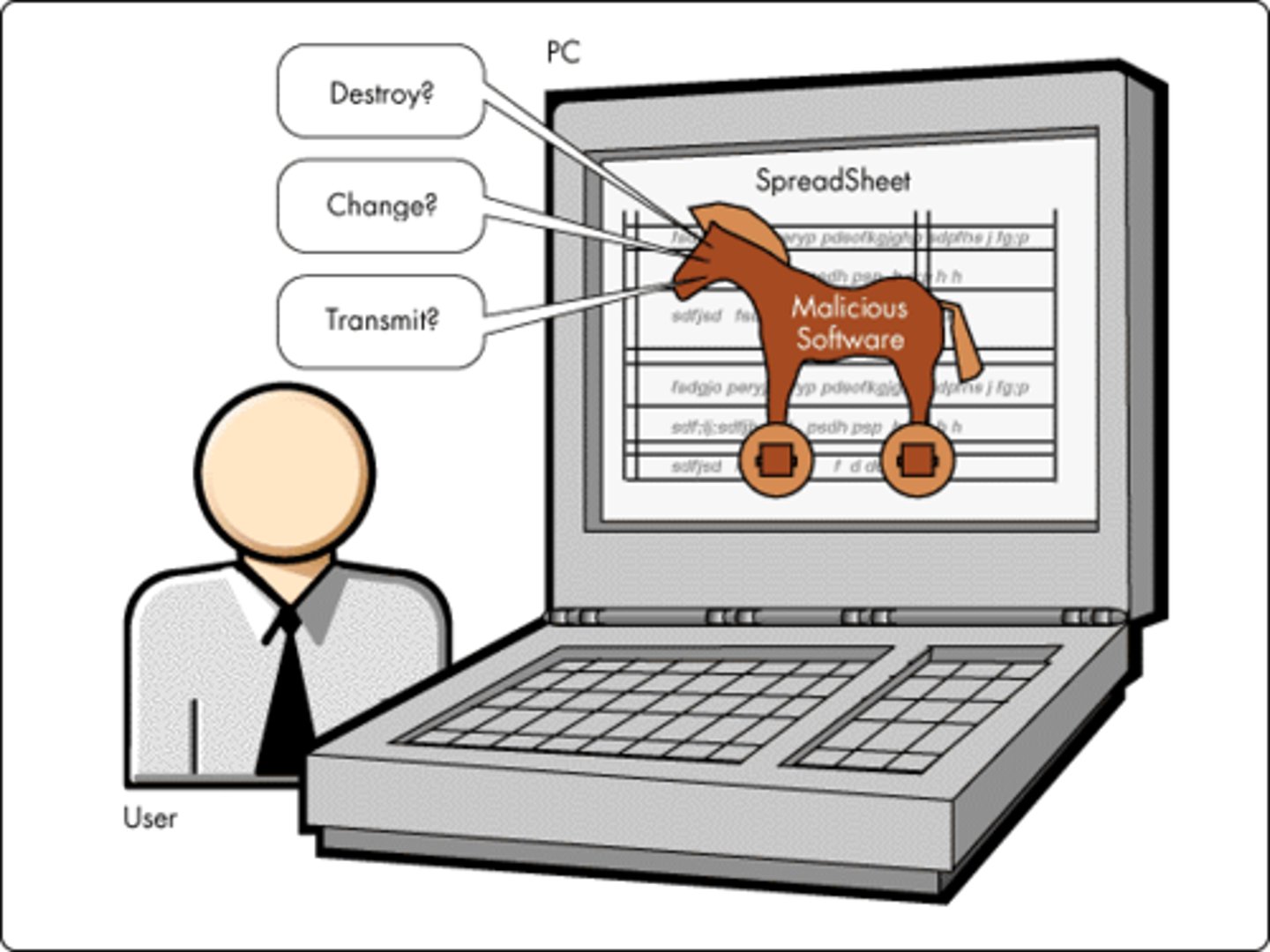
Trojan Horse
Software programs that hide inside regular programs, such as games or utilities. If run, these programs can do great harm to your computer/device. Compared to an event in Greek mythology.
Upload
The process by which an individual can send or post a file to the internet.

Upstander
Someone who takes action to stop bullying behavior or other inappropriate behavior.

Victim
Someone who is harmed by another person or persons.

Virus
A program that duplicates itself and spreads throughout your computer/device destroying files, changing data and hogging all your memory. They damage software, not hardware (your computer/device).

Worm
A virus that replicates itself, but does not change any files on your computer/device. They can multiple may times and take up all the available memory on your computer/device.

Reasonable Expectation of Privacy
Related to the Fourth Amendment which protects citizens' privacy in places such as: Places of residence, Restrooms, Changing rooms...etc
Cyber Attack
These can range from installing spyware on a personal computer to attempts to destroy the infrastructure of entire nations.
Hate Speech
This attacks a person or group on the basis of attributes such as race, religion, ethnic origin, sexual orientation, disability, or gender. ... In some countries, a victim may seek redress under civil law, criminal law, or both.
Digital Reputation
Defined by your behaviors in the online environment and by the content you post about yourself and others. Tagged photos, blog posts and social networking interactions will all shape how you are perceived by others online and offline, both now and in the future.
Shoulder Surfing
The practice of spying on the user of an ATM, computer, or other electronic device in order to obtain their personal access information. Recently it is used during job interviews to view your digital reputation.
Distracted Driving Law
The law forbids virtually all use of handheld gadgets such as phones, tablets, laptop computers and gaming devices while driving. Fines start at $136 for the first offense and $234 for the second, and will be reported to the driver's insurance company (increa$e) and will appear on the driver's record.
Cyber Sickness
Also known as "digital motion sickness," symptoms that range from headaches to woozy feelings can occur when you quickly scroll on your smart phone or watch action-packed video on your screen. The sensation results from a mismatch between sensory inputs.
Text Neck
Discomfort in the neck and spine from spending long periods of time looking down at your smartphone. The angle at which our big heads look down forces our spine to bear the weight of approximately 60 pounds. The habit may lead to people requiring medical spine care at a younger age. Being mindful of how far your neck bends when you're on your phone — and bending it back to an upright position — can help reduce the risk of text neck.