CSCI 180 - Introduction & Security Principles
1/50
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
51 Terms
Vulnerability
A weakness in the system, for example, in procedures, design, or implementation, that could be exploited to cause loss or harm
Threat
Any circumstances / event with the potential to cause loss or harm / potential violation of security policy
Attack
An action taken against a target with the intention of doing harm
How can we deal with harm?
- Prevent it
- Deter it
- Deflect it
- Mitigate it
- Detect it
- Recover it
Prevent Harm
Blocking the attack or closing the vulnerability
Deter Harm
Prevent harm by making the attack harder
Deflect Harm
Redirecting the attack or making another target more attractive
Mitigate Harm
Make its impact less severe
Detect Harm
Detect the attack either as it happens or some time after the fact
Recover Harm
Recovery from its effects
Many breaches begin by _______________________ a vulnerability.
exploiting
A ___________________________ is a security-relevant software defect that can be exploited to effect an undesired behavior.
vulnerability
Defect
Occur in the software's design and its implementation
Flaw
A defect in the design
Bug
A defect in the implementation
Why do companies not fix all bugs?
Would be too expensive to fix all bugs before deploying, so companies only fix the ones most likely to affect normal users
Adversary
Not a normal user, and will actively attempt to find defects in rare feature interactions and edge cases and will try to find a bug and exploit it to achieve his goal
CIA Triad
Confidentiality, integrity, and availability
Confidentiality
The avoidance of the unauthorized disclosure of information involving the protection of data, providing access for those who are allowed to see it while disallowing others from learning anything about its content.
Integrity
The property that information has not been altered in an unauthorized way involving maintaining the consistency, accuracy, and trustworthiness of data over its entire life cycle
Modifying information or misusing the systems functionality is violation of __________________________ .
integrity
Availability
The property that information is accessible and modifiable in a timely fashion by those authorized to do so, applying to both data and services
What are the tools for confidentiality?
Encryption, access control, authentication, authorization, and physical security
What are the tools for integrity?
Cryptographic tools, backups, checksums (for detection), and data correcting codes
Data and services are thought to be available if:
1. There is a timely response to our request
2. Resources are allocated fairly so that some requests are not favored over others
3. Concurrency is controlled, that is simultaneous access, deadlock management, and exclusive access are supported as required
Encryption
The transformation of information using a secret, called a key, so that the transformed information can only be read by someone who has the key
Access Control
Rules and policies that limit access to confidential information. Who can have access is determined by identity
Authentication
Determining the identity or role that someone has, usually based on a combination of
1. Something the person has (like a smart card or a radio key fob storing)
2. Something the person knows (like a password, secret keys)
3. Something the person is (like a human with a fingerprint)
Authorization
Determining if a person or system is allowed access, based on an access control policy. Such authorizations should prevent an attacker from tricking the system into letting him have access to protected resources
Physical Security
The establishment of physical barriers to limit access to protected computational resources
Backups
The periodic archiving of data
Checksums
The computation of a function that maps the contents of a file to a numerical value, depending on the entire contents of a file and is designed in a way that even a small change to the input file is highly likely to result in a different output value
Data Correcting Codes
Methods for storing data in such away that small changes can be easily detected and automatically corrected
Nonrepudiation
Prevents either sender or receiver from denying a transmitted message. When a message is sent, the receiver can prove that the alleged sender in fact sent the message When a message is received, the sender can prove that the alleged receiver in fact received the message
Security Principles
Set of general principles that help design more secure systems
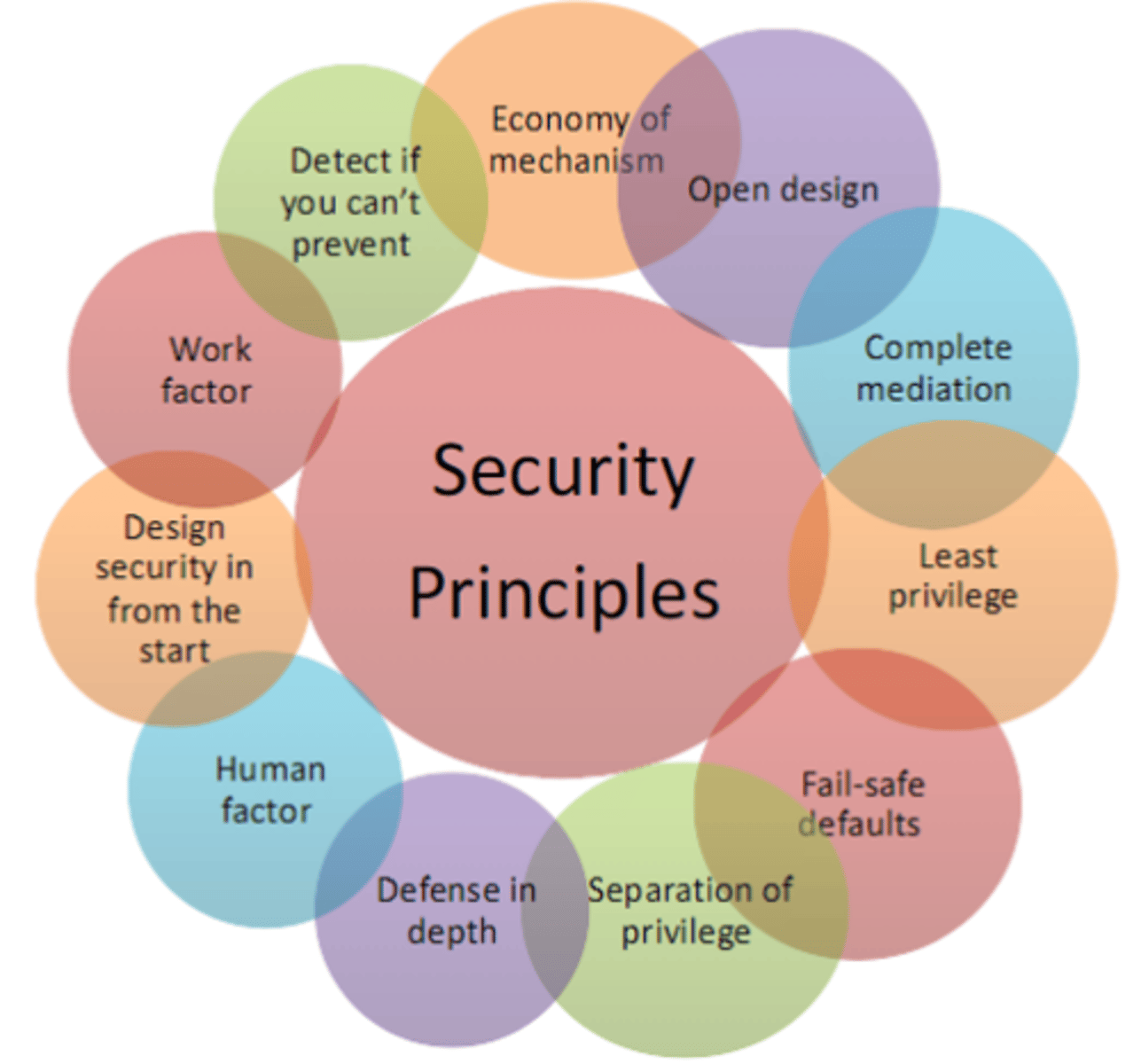
Economy of Mechanism
The design of security measures should be as simple and small as possible. If a design and implementation are simple, fewer possibilities exist for errors. The checking and testing process is easier, because fewer components and cases need to be tested. With a complex design, there are many more opportunities for an adversary to discover subtle weaknesses to exploit that may be difficult to spot ahead of time
Open Design
The design of a security mechanism should be open rather than secret. Don't rely on security through obscurity
Shannon's Maxim
"The enemy knows the system", where attackers can obtain access to a copy of a given system to measure and/or determine how it work.
Attackers can get these information: OS types, software versions, usernames, server ports, IP addresses, usual patterns of activity, administrative procedures.
Kerchoff's Principle
"The only part of a cryptographic system unknown to the adversary is the cryptographic keys" Although encryption keys must be secret, encryption algorithms should be open to public scrutiny
Ensure Complete Mediation
Ensure that every access point is monitored and protected. Every access must be checked against the access control mechanism. Systems should not rely on access decisions retrieved from a cache
Reference Monitor
Single point through which all access must occur (ex. network firewall, airport security, the doors to the dorms)
Least Privilege
Every process and every user of the system should operate using the least set of privileges necessary to perform the task. The less privilege a program has the less harm it can do if it is compromised. If a specific action requires that a subject's access rights be augmented, those extra rights should be relinquished immediately on completion of the action
Work Factor
Cost/benefit analysis, the worth of what we are protecting vs. the cost of securing it. The cost of bypassing a security mechanism should be compared with the resources of an attacker when designing a security scheme.
You should focus your energy on securing the ________________________. A system is only as secure as the weakest link. Attackers will attack the system at its weakest point.
weakest links
Use Fail-Safe Defaults
The default is lack of access, and the protection scheme identifies conditions under which access is permitted
Separation of Privilege
Split up privilege so no one person/system has complete power. Require multiple parties to approve before access is granted
Defense in Depth
If you use multiple redundant protections, then all of them would need to be breached before the system's security will be endangered.
However, remember: Work factor! Defenses are not free
Consider Human Factor
User interfaces should be well designed and intuitive, and all security-related settings should adhere to what an ordinary user might expect. Security systems should be user-friendly, designed to be intuitive and easily understandable by the average person.
The security mechanism may add some extra burden, but that burden must be both minimal and reasonable. Users like convenience. Will users abide a security mechanism that makes their job hard, or decide to subvert it?
Detect if You Can't Prevent
If you can't stop the attack from happening, you should at least be able to know that the attack has happened. Save audit logs so that you can detect and analyze break-ins
Design Security in from the Start
Trying to add security to an existing application after it has been designed and implemented is usually a very difficult task. A lot of systems today were not designed with security from the start, resulting in patches that don't fully fix the problem
Common Assumptions About Attackers
1. Attackers can interact with our systems without particular notice
2. Attackers can often find clever ways to automate
3. Many times attacks happen when attackers become lucky. Attackers use automation and with automation/repetition their chances increase