CCNA Module (3-5) Part 6
1/10
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
11 Terms
What does the CLI prompt change to after entering the command ip access-list standard aaa from global configuration mode?
Router(config-std-nacl)#
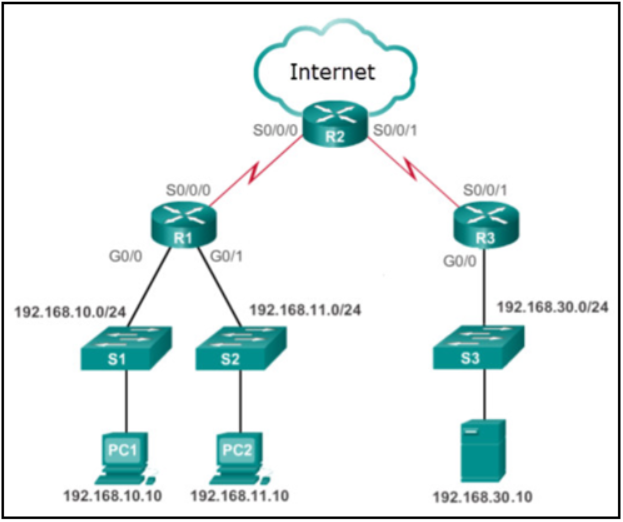
Refer to the exhibit. Many employees are wasting company time accessing social media on their work computers. The company wants to stop this access. What is the best ACL type and placement to use in this situation?
extended ACLs inbound on R1 G0/0 and G0/1
A technician is tasked with using ACLs to secure a router. When would the technician use the 40 deny host 192.168.23.8 configuration option or command?
to create an entry in a numbered ACL
What is the best description of Trojan horse malware?
It appears as useful software but hides malicious code.
What wild card mask will match networks 172.16.0.0 through 172.19.0.0?
0.3.255.255
What is the term used to describe gray hat hackers who publicly protest organizations or governments by posting articles, videos, leaking sensitive information, and performing network attacks?
hacktivists
A technician is tasked with using ACLs to secure a router. When would the technician use the no ip access-list 101 configuration option or command?
to remove a configured ACL
What is the term used to describe unethical criminals who compromise computer and network security for personal gain, or for malicious reasons?
black hat hackers
What is the term used to describe a guarantee that the message is not a forgery and does actually come from whom it states?
origin authentication
A technician is tasked with using ACLs to secure a router. When would the technician use the ip access-group 101 in configuration option or command?
to apply an extended ACL to an interface
A technician is tasked with using ACLs to secure a router. When would the technician use the remark configuration option or command?
to add a text entry for documentation purposes