IST 220 Final Exam
1/57
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
58 Terms
End systems are connected by a network of:
Transmission rates and packet switches
All activity in the Internet that involves two or more communicating remote entities is governed by a protocol. True or False?
True
Every router has a _______________ that maps destination addresses (or portions of the destination addresses) to that router's outbound links.
Forwarding table
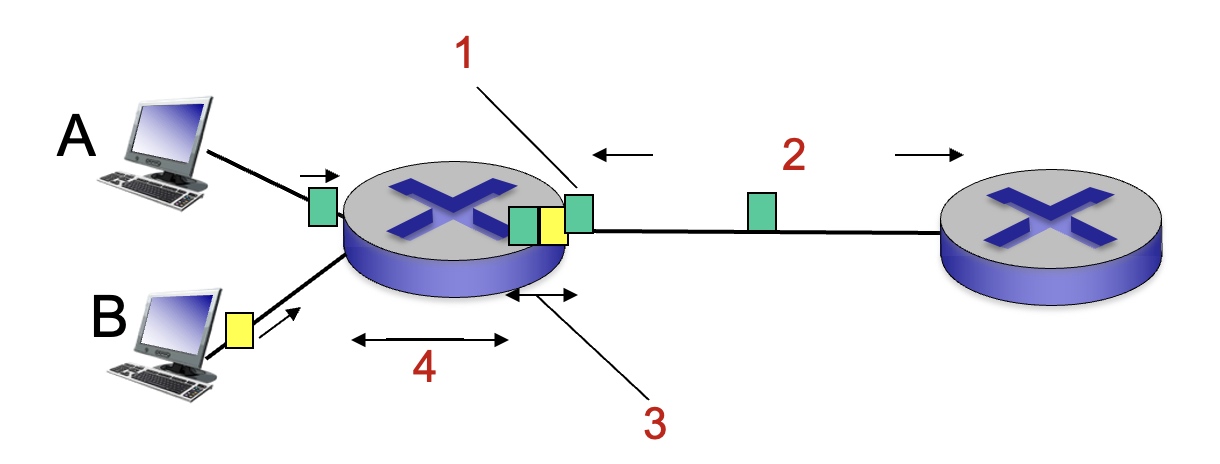
For the figure below, what is the source of packet delay most associated with number 1?
Transmission delay
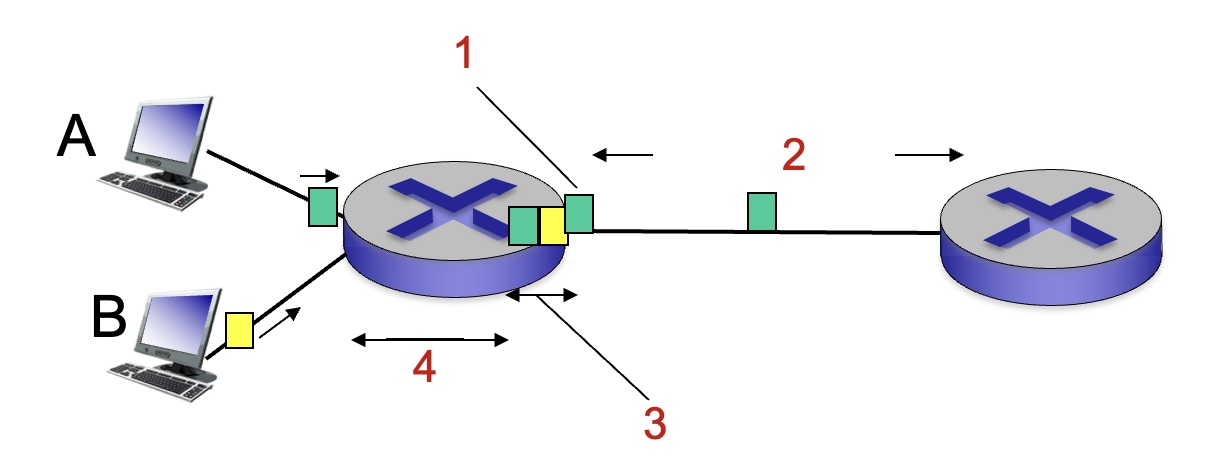
For the figure below, what is the source of packet delay most associated with number 2?
Propagation delay
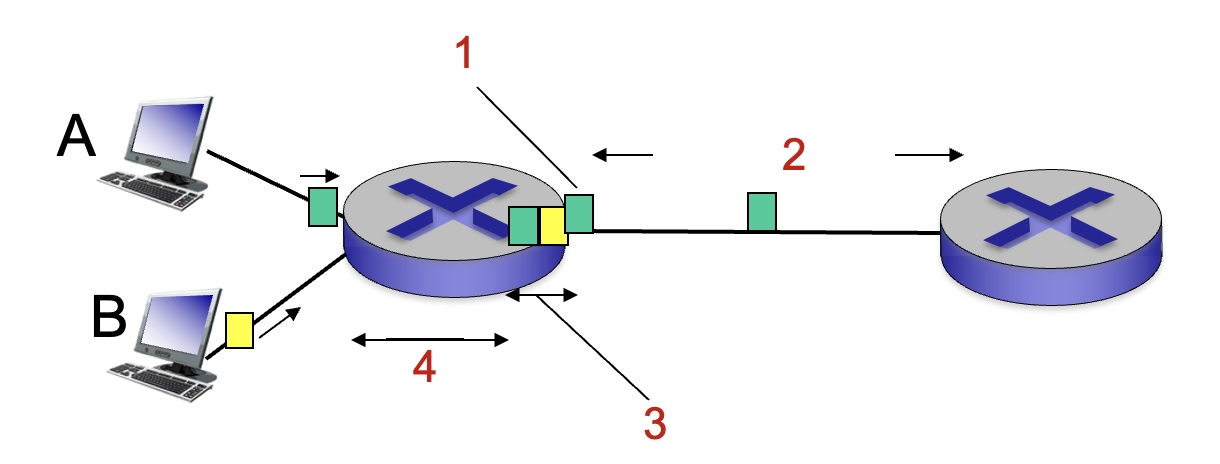
For the figure below, what is the source of packet delay most associated with number 3?
Queuing delay
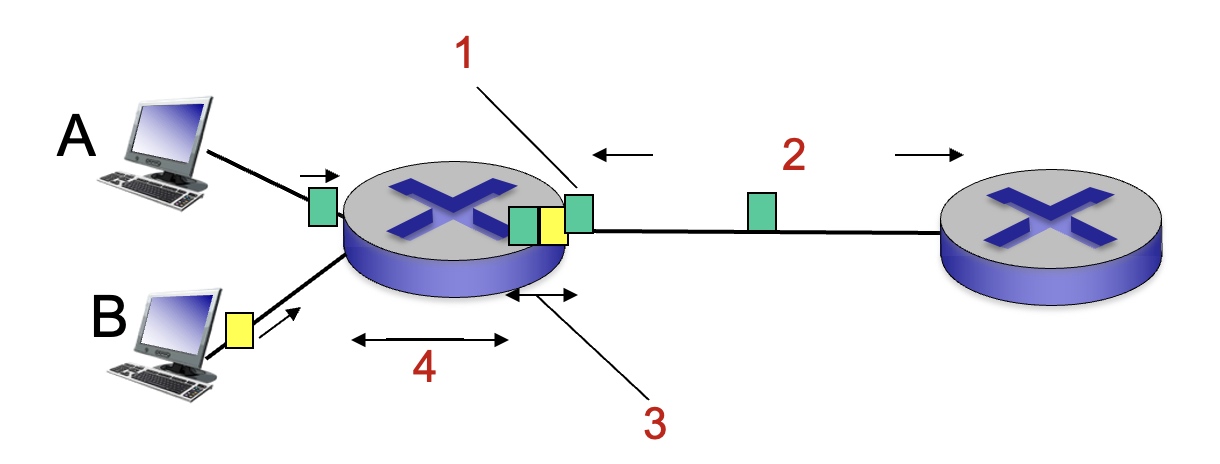
For the figure below, what is the source of packet delay most associated with number 4?
Nodal processing
Packet switching pre-allocates use of the transmission link regardless of demand, with allocated but unneeded link time going unused. True or False?
False
The Internet protocol stack consists of six layers. True or False?
False
Describe the meaning of the phrase encapsulation as used in the context of protocol layers and their service models.
Encapsulation is the process of creating a packet which includes two fields: header fields and a payload field. The payload field is typically a packet from the layer above.
In topic 1.6, "Networks Under Attack," you learned about four categories of attacks that "the bad guys" can launch across the Internet, and saw several examples of each. In a few sentences, describe one of those examples.
The bad guys can put malware in your host via the internet
Malware: self-replicating or not
Viruses
Worms
The bad guys can attack servers and network infrastructure
Denial-of-service (DoS) attacks
Distributed DoS (DDoS)
The bad guys can sniff packets
Packet sniffer - passive receiver that records a copy of every packet that flies by
The bad guys can masquerade as someone you trust
IP spoofing
Which of the following is not an example of an object, as we have used that term in this course?
HTTP socket
Web servers implement the server side of HTTP. True or False?
True
Suppose the URL that a user requests is http://220.m84.us/http_object_demo/index.html. Which path will be included in the request?
/http_object_demo/index.html
The first line of an HTTP request message is called the request line. True or False?
True
An HTTP server is stateless. True or False?
True
In a few sentences, describe what a proxy server is.
A proxy server, also known as a Web cache, is a network entity that satisfies HTTP requests on the behalf of an origin Web server. A user's browser can be configured so that all of the user's HTTP requests are first directed to the Web cache. This can substantially reduce the response time for a client request, and can substantially reduce traffic on an institution's access link to the Internet.
The HTTP mechanism which allows a cache to verify that its objects are up to date is called the:
conditional GET
HTTP/1.1 uses UDP connections. True or False?
False
The three major components of e-mail are user agents, mail servers, and the Simple Mail Transfer Protocol (SMTP). True or False?
True
SMTP uses UDP for ultra-reliable delivery from the sender's mail server to the recipient's mail server. True or False?
False
Much like HTTP, SMTP uses a command-response interaction. True or False?
True
SMTP is primarily a pull protocol—it is used to load information at the client's convenience. True or False?
False
Because POP3 is an extremely simple mail access protocol, it doesn't require authorization (i.e., a username and password). True or False?
False
What does the term "logical communication" mean, in the context of a transport-layer protocol?
Logical communication means that, from an application's perspective, it is as if the hosts running the processes were directly connected.
How many timers does the TCP Sender use in order to decide when to retransmit a packet?
One: for the oldest unacknowledged packet
The sequence number for a segment is the byte-stream number of the first byte in the segment. True or False?
True
Which action should the TCP receiver take in response to the following event: "Arrival of out-of-order segment with higher-than-expected sequence number. Gap detected."?
Immediately send duplicate ACK, indicating sequence number of next expected byte.
Assume a TCP connection exists between Host A and Host B. True or false: The acknowledgement number that Host A puts in its segment is the sequence number of the last byte Host A received from Host B. True or False?
False
Congestion can manifest both long delays (queueing in router buffers) and packet loss (buffer overflow at routers). True or False?
True
Describe the difference between forwarding and routing.
Forwarding refers to the router-local action of transferring a packet from an input link interface to the appropriate output link interface. Routing refers to the network-wide process that determines the end-to-end paths that packets take from source to destination.
What is defined as the area or component which connects a router's input ports to its output ports?
Switching fabric
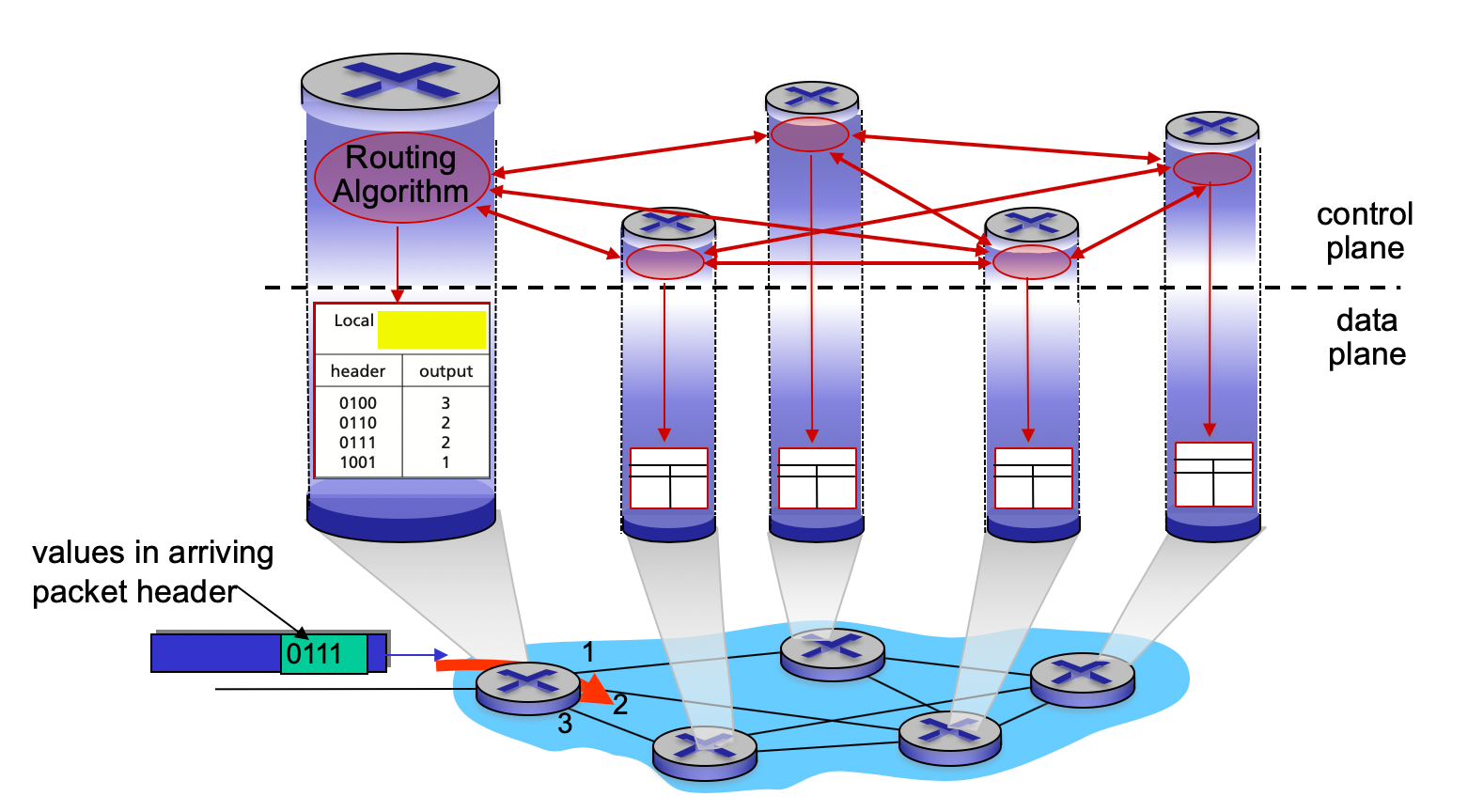
In the figure below, what would be the most appropriate words to put in place of the yellow box? In other words, what does the routing algorithm generate?
forwarding table
The boundary between the host and the physical link—which boundary must be associated with an IP address—is called:
an interface
What does the sending host do to help the destination host be absolutely sure it has received the last fragment of the original datagram?
Sets the flag bit of the last fragment to 0
Network Address Translation (NAT) lets us use just one IP address as far as the outside world is concerned, while still being able to provide private IP addresses for many device interfaces within the local network. True or False?
True
Link-layer protocols run at which numbered network layer?
Layer 3
Which term may be used synonymously with "network adapter"?
Network interface card
Assume we are using a one-bit even parity scheme. True or false: When an even number of bit errors occurs, the result is an undetected error.
True
The link layer is a combination of hardware, software, and firmware. True or False?
False
SMTP is a protocol that you can use to access your e-mail. True or False?
False
If a file consists of F bits and the transfer takes T seconds for the receiver to receive all of the bits, what is the average throughput?
F/T
What is the standard port number for SMTP?
25
In order to transmit data over a network, an application process creates a:
socket
In the application layer protocol stack, which statement is true about user applications?
They run only on end systems
What is the purpose of the conditional GET in HTTP?
To reduce response time and link utilization
What information is needed to identify a process for receiving messages over a network?
Both IP address and port number
Which of the following network applications typically runs over UDP?
DNS
What do we call the tool that can intercept and log traffic passing over a digital network or part of a network?
Packet sniffer
The Internet's network core contains packet switches. True or False?
True
What is the purpose of cookies in web applications?
To maintain state
Circuit switching pre-allocates use of the transmission link regardless of demand, with allocated but unneeded link resources going unused. True or False?
True
What is the main difference between POP3 and IMAP?
IMAP keeps messages on the server while POP3 typically downloads and deletes them
Which term is synonymous with “host”?
End System
Which transport layer protocol provides reliable data transfer and flow control?
TCP
The most popular mail access protocols are POP3, IMAP, and HTTP. True or False?
True
In the following URL, what is the hostname?
What is the purpose of TTL in DNS records?
To specify how long a cached entry remains valid