IT Fundamentals: Big Buffies
1/43
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
44 Terms
The World Wide Web
An information system that enables content sharing over the Internet through user-friendly ways, it allows documents and other web resources to be accessed over the Internet according to specific rules of the Hypertext Transfer Protocol (HTTP)
PHP Processor
The software component responsible for executing PHP scripts on a web server (PHP: collects form data, generates dynamic page content, or sends and receives cookies)
Router
A network device that directs data between different networks (The internet -> Huge network, home's private network), choosing the best path for each packet to travel; It connects to local devices to the Internet, assigns them IP addresses, and manages traffic so everything flows smoothly without collisions (essentially acting as a traffic controller for digital communication)
Packet
A small, structured chunk of data sent across a network.
Instead of sending an entire file or message as one big piece, computers break it into packets so they:
can travel efficiently
take different paths if needed
be reassembled at the destination.
Modem
The device that talks directly to your ISP (Internet Service Provider) and converts their signal (from either a coaxial or fiber-optic cable) into standard digital internet data
Converts ISP signals
Gives your router a single IP address
Acts as the gateway between the ISP and your home network
Cable Internet
Uses a coax cable (the same one used for a TV) that sends electrical signals through copper wiring
Fast, but slower than fiber at the high end
Extremely common because it piggybacks on the same coaxial cable systems used for TV
(Examples: Comcast Xfinity, Optimum)
Fiber Internet
Uses thin glass strands called fiber optic cables that send light pulses instead of electricity
Upload and download speeds are equal (called symmetrical speeds)
Doesn't slow down from electrical interference
Handles huge amounts of data without congestion
(Examples: Verizon Fios, Google Fiber, AT&T Fiber)
Network
Just two or more devices connected so they can send data to each other.
OSI Model
Otherwise known as the Open Systems Interconnection Model, this describes how data moves from one device to another over a network. It has seven layers, from the closest to the user (Layer 7) to the closest to the hardware (Layer 1).
Physical Layer
Layer 1 —> Transmits raw bits over physical media (the actual wires and signals carrying data)
Examples: Cables (Ethernet, fiber), Wi-Fi signals, Network interface cards
Application
Presentation
Session
Transport
Network
Data Link
Physical
“All People Should Take Noble Data Processing”
Data Link Layer
Layer 2 → Handles node-to-node data transfer over a single physical network link and handles error detection/correction, using MAC addresses and frames; In other words, it makes sure data can move correctly between two directly connected devices (like your computer to your router)
How does the Data Link Layer do this?
Breaks the raw bits from the Physical Layer into frames (structured chunks of data)
Adds headers and trailers so the device knows when a frame starts and ends
MAC addresses are used to identify source and destination devices
(Local street delivery between nearby houses)
Includes the Ethernet (for LAN), and Point-to-Point Protocol (for direct connections between two network nodes)
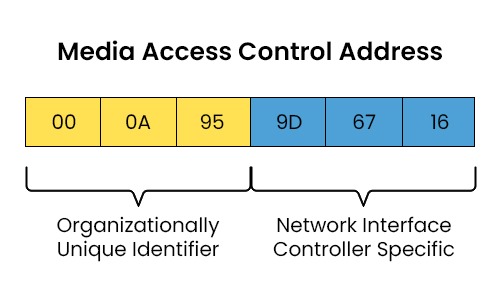
MAC Addresses
Media Access Control address that is assigned to a network interface controller (NIC); it is a 12-digit hexadecimal number that serves as the physical hardware address for devices on a network —> allowing them to communicate with one another on a local network segment
Network
Layer 3 —> Determines how data gets from one network to another through routing and logical addressing
IP addresses, routers, ICMP
Determines the best physical path for data to reach its destination based on network conditions, the priority of service, and other factors
Headers and Trailers
Control data added to the beginning (header) and end (trailer) of a data block for management, routing, and error checking
Transport
Layer 4 —> Ensures complete data transfer, error recovery, and flow control between hosts. This layer segments and reassembles data for efficient transmission and provides reliability with an error detection and correction mechanism
Session
Layer 5 —> Manages and controls the connections between computers. It establishes, maintains, and terminates connections, ensuring that data exchanges occur efficiently and in an organized manner.
Presentation
Layer 6 —> Responsible for translating data between the application layer and the network format. Ensures data is in a usable format for the Application layer, focused on data translation, encryption and decryption, and both compression and decompression
Application
Layer 7 —> Serves as the interface between the end-user applications and the underlying network services, providing network services directly to end-user applications. (examples: web browsers, emails)
Network Protocol
Provides the rules by which the layers of a network communicate with each other.
This, in turn, provides rules by which different networks can communicate with each other.
This also informs network programmers and administrators how to implement, manage, and maintain a network.
TCP/IP
The most commonly used Internet protocol sets the requirements of all computers that communicate over the Internet. Thus, every computer may run other network protocols, but it is a requirement that they run TCP/IP (Transmission Control Protocol/Internet Protocol)
What are some rules of TCP/IP?
Each device on a TCP/IP network must be uniquely identifiable
Large data is split into small packets before transmission.
IPv4
Version of the Internet Protocol (IP), where their main job is to identify devices on a network and route data to the correct destination.; simple and remains widely used today
This version is the older and original IP addressing system, introduced in the early 1980s, where the address format is written as four numbers separated by dots.
About how many unique addresses? 4.3 billion
Checksum
A simple piece of data that, with high probability, tells you whether a message was received correctly; they are often used to verify data integrity but are not relied upon to verify data authenticity
Ping Program
A network diagnostic program that is used to determine whether another computer, or device, is available and reachable over a network.
Sends a small message called an ICMP Echo Request to a target device
Waits for an ICMP Echo Reply
Modulo
OLAP Model
Stands for Online Analytical Processing, a category of software tools used to analyze large volumes of data from multiple perspectives.
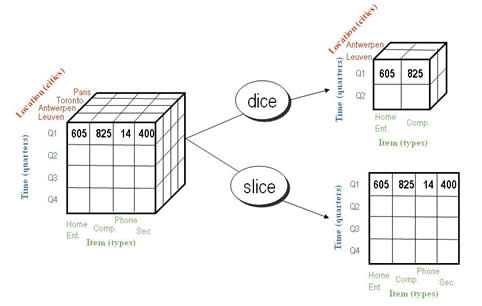
Slicing
Part of OLAP operations, involves creating a subset of the data by reducing the data from multiple dimensions to one dimension.
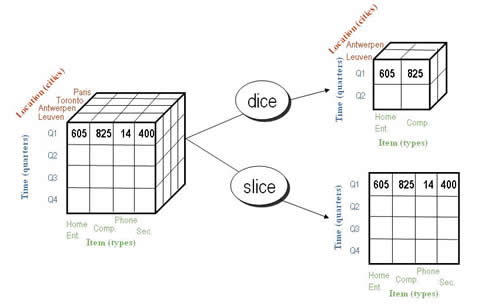
Dicing
Part of OLAP operations; Same as slicing except that the result can be in multiple dimensions, but still obtaining a subset of the data.
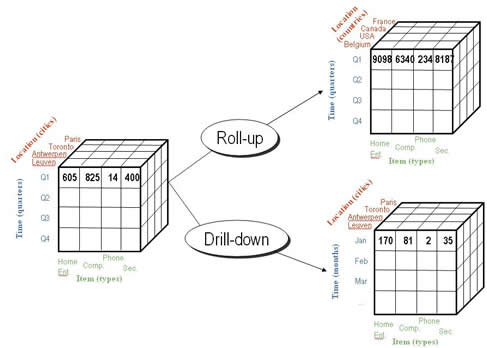
Drilling Up / Down
Part of OLAP operations; exclusively only shifts the view of the data
______ Down: Provides more detail
_______ Up: Provides summarized data
Rolling Up: Provides summarized data but also collapses the data from multiple items into a single value
RAID
Redundant Array of Independent (or Inexpensive) Disks; a data storage technology that combines multiple physical hard drives into one logical unit to improve performance, fault tolerance, or both.
Pivoting
Part of OLAP operations, lets you swap rows and columns (or dimensions) to analyze the same data in a new way.
Example: Rows = Years, Columns = Regions --> Rows = Regions, Columns = Years
Domain Name System
Translates human-friendly website names into IP addresses that computers use to find each other on a network.
Network Port
A logical communication endpoint identified by a number (0-65535) that tells a computer which application or service should receive incoming network data
They work with the IP address, the IP address identifies the device, and the port number identifies the application on that device
Three-Way Network Handshake
A core process that TCP/IP uses to establish a reliable connection between two devices before any data is sent, where it 1)
Radio signals are transmitted through radio towers, cell phone towers, and microwave towers.
For long distances, cable is too expensive, and so radio signals are sent via…
Packet-Switching
The message’s pathway is created only as it is sent, most computer networks are ____-switched (the Internet)
Network Hub
Merely a device that connects multiple computers together.
When there are multiple computers connected to a ____, a message received by the ___ is made available to all connected computers!

Router
A device that connects multiple networks, typically used in specific locations in a network so that messages can be routed to other networks.
Creates a local network (LAN) by directing data traffic
Has decision-making capabilities
If message traffic exceeds its capacity, the router may have to drop messages purposefully

Network Gateway
A router that connects networks of different types..
If two networks use different protocols, this tool is capable of handling the differences in the messages themselves because of different protocols
Ethernet
A standard technology for wired networking that connects devices in a Local Area Network (LAN) or larger networks

WPA2
Otherwise known as Wi-Fi Protected Access 2, it is a wireless security standard that is used to protect Wi-Fi networks by encrypting data sent between devices and the wireless access point.
Protocol Attack
A type of cyberattack that exploits weaknesses in the design or implementation of a communication protocol (the rules that govern how data is transmitted between devices), rather than attacking a specific application or user directly.
Relational Database
Collection of data, organized to support access that models some aspect of reality
Relation: A set of tuples that have the same attributes.