CCNA 3 Module (3-5) Part 5
1/10
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
11 Terms
Which ACE will permit a packet that originates from any network and is destined for a web server at 192.168.1.1?
access-list 101 permit tcp any host 192.168.1.1 eq 80
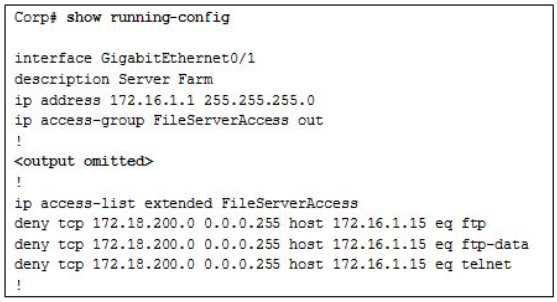
Refer to the exhibit. A new network policy requires an ACL denying FTP and Telnet access to a Corp file server from all interns. The address of the file server is 172.16.1.15 and all interns are assigned addresses in the 172.18.200.0/24 network. After implementing the ACL, no one in the Corp network can access any of the servers. What is the problem?
The ACL is implicitly denying access to all the servers.
A technician is tasked with using ACLs to secure a router. When would the technician use the access-class 20 in configuration option or command?
to secure administrative access to the router
What is the term used to describe the same pre-shared key or secret key, known by both the sender and receiver to encrypt and decrypt data?
symmetric encryption algorithm
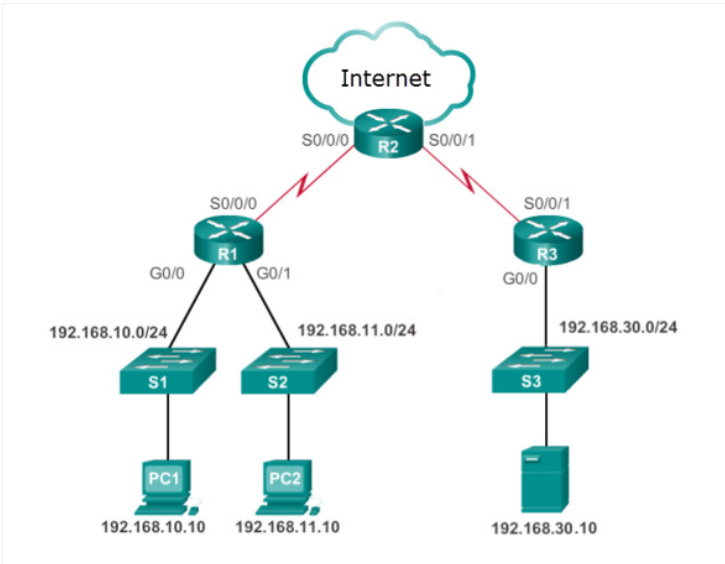
Refer to the exhibit. Internet privileges for an employee have been revoked because of abuse but the employee still needs access to company resources. What is the best ACL type and placement to use in this situation?
standard ACL outbound on R2 WAN interface towards the internet
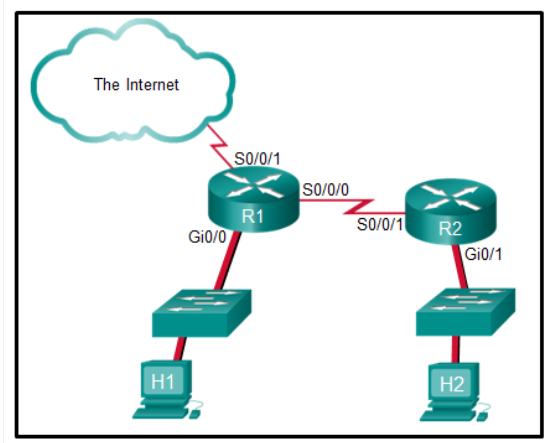
Refer to the exhibit. The student on the H1 computer continues to launch an extended ping with expanded packets at the student on the H2 computer. The school network administrator wants to stop this behavior, but still allow both students access to web-based computer assignments. What would be the best plan for the network administrator?
Apply an inbound extended ACL on R1 Gi0/0.
A technician is tasked with using ACLs to secure a router. When would the technician use the ‘ip access-group 101 in’ configuration option or command?
to apply an extended ACL to an interface
In which type of attack is falsified information used to redirect users to malicious Internet sites?
DNS cache poisoning
What is a feature of an IPS?
It can stop malicious packets.
What is the term used to describe a potential danger to a company’s assets, data, or network functionality?
threat
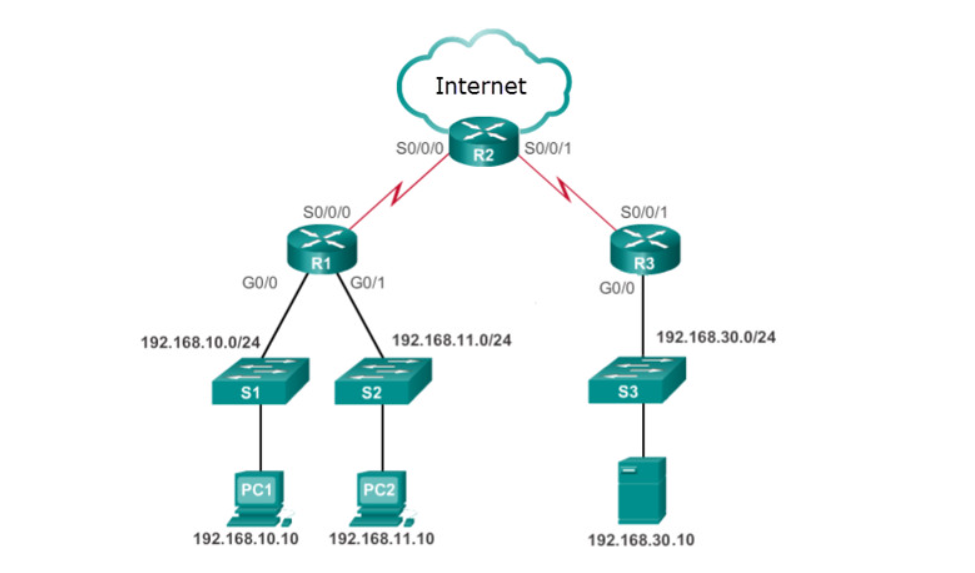
Refer to the exhibit. Network 192.168.30.0/24 contains all of the company servers. Policy dictates that traffic from the servers to both networks 192.168.10.0 and 192.168.11.0 be limited to replies for original requests. What is the best ACL type and placement to use in this situation?
extended ACL inbound on R3 G0/0