1.3 Computer networks, connections and protocols
1/29
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
30 Terms
The characteristics of LANs and WANs and their characteristics
A LAN is a network that has computer systems located geographically close to each other for example within a building or site such as a school. LANs' network infrastructure (servers and routers) are usually owned and managed by the network owner. A WAN is a network that has computer systems located geographically distant from one another for example across a country or the world. WANs use third party communication channels from internet service providers like BT or Virgin Media.
The different factors that can affect network performance
The bandwidth (maximum amount of data that can be sent across a network at once) available
Number of users
Number of data collisions
Interference and physical obstructions such as thick walls
Distance to travel/signal strength
Amount of data to transfer
Wireless Access Point
Provides a link between wireless and wired networks allowing wireless devices to connect to a wired network by creating a wireless local network. WiFi or bluetooth hotspots like the WiFi in a café or airport that provides phones and laptops a connection to the internet. A WAP may be a separate device or built into another device such as a router.
Router
Routers are used to transfer data packets between networks. Routers receive data packets and use the IP address from the packet header to determine the best route to transmit the data. Data is transferred from router to router across the internet towards the destination. Routers store the IP address of each computer connected to it on the network and uses a list called a routing table to calculate the quickest and shortest route.
Switch
Switches connect devices together on a LAN by receiving data packets from a connected node, reading the destination address in the packet header and forwarding the data directly to its destination. Switches generate a list of the MAC addresses of all devices connected to it when it receives data, and must scan for a matching destination address before sending. An alternative to using a switch is a hub, but hubs are slower and less secure as they forward a copy of received data to all connected nodes.
Network Interface Controller/Card
An NIC is an internal piece of hardware that is required for the computer to connect to a network. The NIC includes a MAC address which is plugged into the network card to allow data to be exchanged between the device and a network. An NIC is embedded on the motherboard.
Transmission media
Although not technically a device, the communication channel along which data is transferred will affect performance. Three common types of transmission media include ethernet cables, fibre optic cables, and coaxial cables.
Ethernet cable
Ethernet cables are used typically on a LAN to transfer data between nodes and hardware such as switches. Examples include Cat5e and Cat6.
Fibre Optic cable
Fibre Optic cables very fast but more expensive and fragile cables typically used to send data quickly along a WAN. Data is sent as pulses of light.
Coaxial cables
Coaxial cables older, slower, copper cables that are not used as much in modern times as they can be affected by electromagnetic interference.
The internet
The internet is a global network of interconnected networks. The world wide web (WWW) is not the same as the internet. It is a way of accessing information, using protocols such as HTTPS to view web pages. Servers provide services on the internet, such as a web server which responds to the web browser (client) request to display a web page. The web server processes the client request to prepare the web page and return it so the web browser can display it to the user. A website must be hosted on a web server so that it can be accessed by others using the internet. A unique domain name must be registered with a domain registrar – this is a company that checks the name is valid and not already taken.
Domain Name Service
A DNS server stores a list of domain names and a list of corresponding IP addresses where the website is stored. Every webpage has a domain name which can be understood and typed by humans and a related, unique IP address. The role of a DNS is to convert the website's domain name into an IP address so the browser can make a request to the correct server hosting that webpage.
If the local DNS server doesn't hold the IP address the query is passed to another DNS server at a higher level until the IP address is resolved. If the IP address is found, the address is passed on to the DNS servers lower in the hierarchy until it is passed onto the local DNS server that couldn't find it and then the browser.
The steps to display a web page are;
A domain name is typed into the address bar of the browser
A query is sent to the local DNS server for the corresponding IP address
The local DNS server will check if it holds an IP address corresponding to that domain name and if it does it passes the IP address to the browser
The browser then connects to the IP address of the server and accesses the website
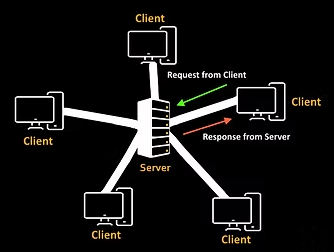
Client-server networks
In a client-server network, clients make requests to a server which manages that request and responds, for example if a user (client) made a request to access a website to a web server. Large services such as Amazon will require lots of powerful servers to handle the millions of requests per second. The client is completely dependent on the server to provide and manage the information. The server controls network security and backups and can be upgraded to manage higher demand.
The advantages of a C-S network are;
The network can be controlled centrally from the server to easily backup data and update software.
Hardware, software, and resources can be shared across the network, such as printers, applications and data files.
The network allows for improved scalability meaning more clients can be easily added to the central server.
The disadvantages of a C-S network are;
Large amounts of traffic congestion will cause the network to slow down.
If a fault occurs with the server then the whole network will fail.
IT technicians may be required to manage and maintain the network.
Malware, such as viruses, can spread quickly across the network.
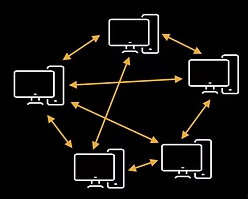
Peer-peer networks
For peer-peer networks, data is shared directly between systems without requiring a central server. Each computer is equally responsible for providing data. Peer-peer is optimal for sharing files that can then be downloaded.
The advantages of a P-P network are;
It is a simpler network than C-S to set up as no server is required.
Clients are not dependant on a server.
It is perfect for quickly sharing files between systems, such as downloading media files.
The disadvantages of a P-P network are;
Without a dedicated server, there is no central device to manage security or backups. Backups must be performed on each individual system.
Computer performance will decrease with more devices connected to the network, especially if other machines are slow.
The Cloud
The cloud is networks of servers accessed on the internet. Cloud computing is an example of remote service provision. Cloud servers can have different purposes such as running applications, remote processing and storing data. When data is stored in 'the cloud', using services such as Microsoft OneDrive data is stored on large servers owned by the hosting company. The hosting company is responsible for keeping the servers running and making the user's data accessible on the internet.
Advantages and disadvantages of the Cloud:
Cloud storage is very convenient as it allows people to work on a file at the same time and it can be accessed from different devices. It has a huge capacity and subscriptions can simply be upgraded if you want more storage. Cloud storage is typically free for a certain amount of storage so it is cheaper than regular storage.
Portability
Portability depends on internet connection. If the internet connection fails, or the servers are attacked then the data could become inaccessible.
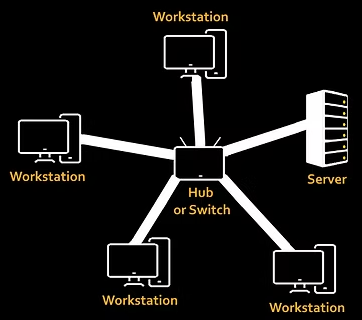
Star topology
In a star topology each computer system is connected to a central hub or switch.
How it works: each computer system is connected to the central hub or switch and transfers its data packets there. The hub or switch looks at the destination address in the header and transfers data packets directly to the intended computer.
The advantages of a star topology are;
A star topology has improved security because data packets are sent directly to and from the hub / switch in the centre and not necessarily all devices like in a bus or ring topology.
New systems can be attached directly to the central system so the network doesn't need to be shut down. System failures of attached computers won't usually cause complete network failure.
Transfer speeds are generally fast in a star topology as there are minimal network collisions.
The disadvantages of a star topology are;
Extra hardware (the hub or switch) is required to be purchased, installed and maintained.
If the central system (the hub or switch) fails then the whole network will be unusable until the error is fixed.
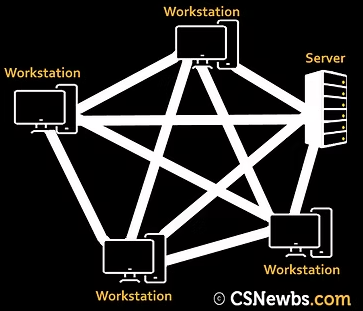
Mesh topology
In a full mesh network, each computer system is connected to every other computer system. There are also partial mesh networks where only some nodes (e.g. a printer) are connected to every other node.
How it works: Data packets are transferred to the destination address along the quickest path, travelling from node to node. If a pathway is broken, there are many alternative paths that the packets can take.
The advantages of a mesh topology are;
If one cable or system fails then data packets can take an alternative route and still reach the destination address.
Because of the large possible number of systems and connections, a mesh topology can usually withstand large amounts of data traffic.
New systems can be added to the network without disrupting the entire topology.
The disadvantages of a mesh topology are;
Because of the possibly large amount of cables required (especially in a full mesh topology) this network layout can be expensive to install and maintain.
Redundant cabling should be avoided - this is when cables are connected between systems that won't ever need to communicate.
Benefits and drawbacks of wired and wireless connection
Wired connections are physical cables such as copper or fibre optic wires, and require an NIC to connect to a network. Wired connections use a wired connection protocol, most commonly ethernet. Wired connections restrict movement but are faster and more secure than wireless networks and require an NIC.
Wireless connections such as WiFi or Bluetooth use no cables but require a wireless NIC (WNIC). Wireless connections can be affected by the device's distance from the wireless router and physical obstacles like walls or bad weather. Wireless connections provide a freedom of movement but are slower and less secure than wired networks and require a WNIC.
The principle of encryption to secure data across network connections.
Wireless connections are less secure and require encryption. Encryption is the process of scrambling data into an unreadable format so that attackers cannot understand it if intercepted during transmission.
The original data (known as plaintext) is converted to scrambled ciphertext using an encryption key. Only at the correct destination will the encryption key be used to convert the ciphertext back into plaintext to be understood by the receiving computer.
IP addressing and the format of an IP address (IPv4 and IPv6)
There are two versions of IP addressing currently used, IPv4 and IPv6.
IPv4 is a 32-bit address, represented in denary, that allows for over 4 billion unique addresses.
It has four 8-bit segments of denary values (from 0 to 255) separated by full stops.
IPv4 example:
145.13.218.102
IPv6 is a 128-bit address, represented in hexadecimal, that allows for an undecillion unique addresses.
It has eight 16-bit segments of four hexadecimal values (0000 - FFFF), separated by colons.
IPv6 example:
736E:1029:A4B3:902D:77B2:72FF:AE62:0912
A MAC address is assigned to devices; its use within a network; its format
A MAC address is a unique hexadecimal number assigned to each network interface card/controller inside a networked device such as a router or laptop.
A MAC address is a 48-bit address made up of six 8-bit pairs in hexadecimal, separated by dashes.
While an IP address may change, the MAC address can’t be changed. MAC stands for Media Access Control.
MAC example: 19-C2-D1-47-AA-38
Networking standards
Networking standards are rules that allow computer systems to communicate across networks. Standards have been created to ensure devices can exchange data and work together by interpreting signals in the same way, regardless of the manufacturer.
Transmission Control Protocol and Internet Protocol
Transmission Control Protocol / Internet Protocol or TCP / IP are actually two separate protocols that combine together. TCP is a protocol that allows packets to be sent and received between computer systems. It breaks the data into packets and reorders them back into the original data at the destination. IP is a protocol in charge of routing and addressing data packets. This ensures data packets are sent across networks to the correct destination. It is also an addressing system, every device on a network is given a unique IP address so data packets can be sent to the correct computer system.
Hyper Text Transfer Protocol
HTTP is used to transfer web pages over the Internet so that users can view them in a web browser. All URLs start with either HTTP or HTTPS. HTTPS is a more secure version of HTTP that works with another protocol called SSL (Secure Sockets Layer) to transfer encrypted data.
File Transfer Protocol
FTP is used to transfer files across a network. It is commonly used to upload or download files to/from a web server.
Simple Mail Transfer Protocol
SMTP is a protocol used to send emails to a mail server and between mail servers.
Post Office Protocol and Internet Message Access Protocol
POP and IMAP are both protocols for receiving and storing emails from a mail server. POP will delete an email from the email server once it has been downloaded to a device. IMAP syncs the message with an email server so it can be accessed by different devices.
How layers are used in protocols, and the benefits of using layers; for a teaching example, please refer to the 4-layer TCP/IP model
TCP/IP operate on different layers. A protocol layer is a division of network functionality with each layer providing a specific function to assist the transmission of the data. TCP/IP is split into four layers.
Protocol layers are used because;
Layers are self-contained, so they allow different developers to concentrate on one aspect of the network at a time. A layer can be taken out and edited without affecting other layers.
Protocol layers are used to visualise the different parts of a network, as each of the four layers of TCP/IP has a specific role and is associated with different protocols.
Protocols are broken down into well-defined, specific layers to simplify design, making it easier to identify errors (known as troubleshooting).
Each layer uses specific protocols, so layering ensures these protocols are applied in a specific order. This process uses abstraction and layers only communicate with adjacent layers for easy compatibility.