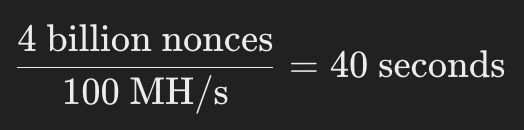blockchain
0.0(0)
Card Sorting
1/62
There's no tags or description
Looks like no tags are added yet.
Study Analytics
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
63 Terms
1
New cards
What is a Blockchain
A constantly growing ledger that keeps a permanent record of all transactions securely, chronologically, and immutably.
2
New cards
Blockchain Components
The five main components of blockchain are Hash Cryptography, Immutable Ledger, Distributed P2P Network, Consensus Protocol, and Mining.
3
New cards
Genesis Block
The first block in a blockchain, with a previous hash set to zeros because no blocks precede it.
4
New cards
Hash Cryptography
A technique ensuring data integrity by converting input data into a fixed-size hash.
5
New cards
SHA-256
A Secure Hash Algorithm developed by the NSA that generates a 256-bit hash.
6
New cards
Properties of Hash Functions
Hash functions must be One-Way, Deterministic, Fast Computation, exhibit the Avalanche Effect, and withstand collisions.
7
New cards
Immutable Ledger
A feature ensuring that once a transaction is recorded, it cannot be altered or deleted.
8
New cards
Distributed P2P Network
A decentralized system where all nodes maintain a copy of the blockchain, ensuring security and consensus.
9
New cards
Mining
The process of validating transactions and adding them to the blockchain by solving complex cryptographic puzzles.
10
New cards
Nonce
A number that miners adjust to find a valid block hash under the target threshold.
11
New cards
Proof of Work (PoW)
A consensus mechanism requiring miners to solve cryptographic puzzles to validate transactions and create new blocks.
12
New cards
Proof of Stake (PoS)
A consensus mechanism where validators are chosen based on the number of coins they stake.
13
New cards
Byzantine Generals’ Problem
A problem in distributed systems where actors must reach consensus despite potential traitors.
14
New cards
Byzantine Fault Tolerance (BFT)
The ability of a system to reach consensus even when some nodes act maliciously or fail.
15
New cards
51% Attack
A security risk where an entity controls more than 50% of the network’s mining power, allowing manipulation of the blockchain.
16
New cards
Competing Chains
Occurs when two miners solve a block simultaneously, requiring the network to adopt the longest chain.
17
New cards
Orphaned Blocks
Blocks that were valid but discarded because another chain became longer.
18
New cards
Merkle-Damgård Paradigm
A method of constructing a hash function for long messages from a collision-resistant function for short messages.
19
New cards
SHA-256 Hash Process
Involves padding the message, appending length, initializing hash buffer, processing message in 512-bit blocks, and producing a final 256-bit hash.
20
New cards
Compression Function in SHA-256
Uses chaining variables and message schedule arrays to iteratively transform data.
21
New cards
Security of SHA-256
Achieved through its deterministic nature, resistance to collisions, and unpredictable output.
22
New cards
Blockchain Use Cases
Applications include Supply Chain Management, Humanitarian Aid, Real Estate, Insurance, and Cryptocurrency.
23
New cards
Consensus Protocol
A mechanism ensuring agreement on the blockchain state among distributed network participants.
24
New cards
Mining Rewards
Miners receive newly minted cryptocurrency and transaction fees for successfully mining a block.
25
New cards
Attack Resistance
Blockchain security relies on cryptographic hashing, decentralization, and consensus mechanisms to prevent fraud.
26
New cards
Target Hash
The threshold below which a valid hash must fall for mining to be successful.
27
New cards
Proof of Work (PoW) Disadvantages
If one mining pool controls more than 51% of the total mining power, the entire blockchain security is at risk. A DDoS attack can put the network’s trustworthiness at risk.
28
New cards
PoW Profitability Issue
As mining difficulty increases, profits decrease, reducing the incentive to mine coins. Ethereum had to implement a "difficulty bomb" and transition to Proof of Stake (PoS) for scalability.
29
New cards
PoW Energy Consumption Issue
PoW is considered unsustainable due to high electricity consumption and slow transaction speeds compared to other consensus mechanisms.
30
New cards
51% Attack in PoW
A mining pool controlling 51% of hashing power can double-spend coins by removing transactions after spending.
31
New cards
Tragedy of Commons in Bitcoin
Fewer miners will remain as block rewards decrease, making the network vulnerable to 51% attacks.
32
New cards
Proof of Stake (PoS) Introduction
Created in 2012 as an alternative to PoW, PoS relies on staking coins rather than energy-intensive mining.
33
New cards
PoS Consensus Mechanism
Stakeholders are chosen to validate transactions based on the number of coins they stake, reducing energy costs.
34
New cards
PoS Security
A 51% attack in PoS requires an attacker to own 51% of the staked cryptocurrency, making attacks economically disadvantageous.
35
New cards
PoS vs. PoW
PoS achieves consensus with lower energy and cost than PoW, but DDoS attacks and fraud are still possible.
36
New cards
Delegated Proof of Stake (DPoS)
A democracy-based consensus mechanism where stakeholders vote for block producers instead of random selection.
37
New cards
Bitcoin Definition
A decentralized digital currency using blockchain technology to enable peer-to-peer transactions without intermediaries.
38
New cards
Bitcoin Layers
Bitcoin operates on three layers—technology (blockchain), protocol (Bitcoin network rules), and token (BTC currency).
39
New cards
Types of Tokens
Cryptocurrency tokens (BTC, ETH), utility tokens (BAT, FIL), security tokens (represent assets), stablecoins (USDT, DAI), governance tokens (UNI, MKR), and NFTs (CryptoPunks, BAYC).
40
New cards
Mining Difficulty in PoW
The target hash value defines mining difficulty, increasing as more leading zeros are required in the hash.
41
New cards
Probability of Finding a Golden Nonce
Extremely low; miners rely on massive computational power to generate valid hashes.
42
New cards
Mining Difficulty Adjustment
Adjusted every 2016 blocks (~2 weeks) to maintain a block creation time of ~10 minutes.
43
New cards
Mining Pools
Groups of miners combine their hashing power to increase their chances of finding a valid block and earning rewards.
44
New cards
Nonce Range
A 32-bit number (0 to ~4 billion) used in mining. When exhausted, timestamp changes allow a new nonce search.
45
New cards
Timestamp Role in Mining
Changes every second, enabling miners to restart nonce searches to find valid hashes.
46
New cards
MEMPOOL in Bitcoin
A temporary storage for unconfirmed transactions before they are added to a block.
47
New cards
Transaction Selection in Mining
Miners prioritize transactions with the highest fees to maximize earnings.
48
New cards
Mining Pool Algorithm
Distributes nonce values among miners, prevents duplicate work, and selects transactions efficiently.
49
New cards
Transaction Fees in Bitcoin
As block rewards decrease over time, transaction fees will replace them as miners' main income.
50
New cards
CPUs vs GPUs vs ASICs
Different types of mining hardware used to solve cryptographic hash puzzles.
51
New cards
CPU (Central Processing Unit)
General-purpose processor handling various tasks, capable of around 10 million hashes per second.
52
New cards
GPU (Graphical Processing Unit)
Specialized in parallel computations, more efficient than CPUs for hash calculations, capable of up to 1 billion hashes per second.
53
New cards
ASIC (Application-Specific Integrated Circuit)
Highly specialized for SHA-256 hashing, capable of over 1000 giga hashes per second.
54
New cards
Cloud Mining
Renting mining equipment remotely and paying a fee to use someone else's computing resources.
55
New cards
Mempool
Temporary storage for unconfirmed transactions in a peer-to-peer blockchain network.
56
New cards
How Mempools Work
Transactions are stored in mempools until they are added to a block by miners.
57
New cards
Orphaned Blocks
Valid blocks that are not part of the main blockchain due to competing chains.
58
New cards
51% Attack
Hypothetical scenario where a miner or group controls over 50% of network hash power to manipulate transactions.
59
New cards
Transaction Fees
The difference between input and output values goes to miners as a fee for transaction processing.
60
New cards
(eq.) Probability of Finding a Golden Nonce
represents the probability of randomly picking a nonce that results in a valid hash
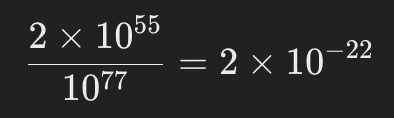
61
New cards
(eq.) Mining Difficulty Calculation
difficulty adjuests every 2016 blocks (~2 weeks) to maintain a blocktime of ~10 minutes
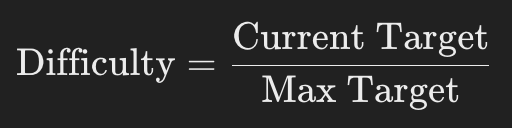
62
New cards
(eq.) Bitcoin Inflation Formula
coinbase (the amount of BTC released per block); as the block reqards decrease due to halving, Bitcoin experiences deflation
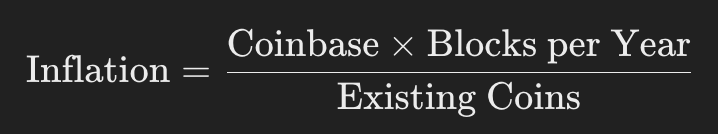
63
New cards
(eq.) Time Needed to Exhause Nonce Range for a Modest Miner
a modest miner can try 100 million hashes per second; it takes ~40 seconds to go through all possible nonce values