This is all what you need to learn governance and regulations
1/164
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
165 Terms
Why does the EU want to regulate data (EU Commission vision)?
Make the EU the world’s most attractive, data-driven economy.
Europe lags behind the USA and China in tech innovation.
Personal and non-personal data aren’t fully used.
What does the EU believe about data?
Data changes how we live and work.
Data is vital for the economy and sustainability.
Small businesses benefit from data.
AI needs data to learn.
Data should benefit everyone.
What is the goal of the European Data Space?
One big, safe European market for high-quality data to grow businesses and help the environment.
What is the goal of the EU Data Strategy?
Create a European market for personal and non-personal data.
Build common data spaces: smart devices, wind farms, transport, business data.
What are the main challenges in the EU Data Strategy?
DIIT
Individuals first: Protect rights, laws, European values.
Innovation & privacy: Balance free data flow with privacy.
Data, tech & skills: Ensure data quality, security, digital skills.
Trust in data sharing: Fair rules and trustworthy systems.
What are the pillars of the EU Data Strategy?
Governance framework: Simple rules; sector-specific laws if needed.
Enablers: Invest in data, skills, infrastructure; best practices for personal data.
Competences: Improve tech skills; empower people to control their data.
Common European Data Spaces: Make data widely available across sectors.
What is the EU’s cross-sectoral data framework about?
Data Governace act + data act
Data Governance Act: Safe sharing of public and sensitive data via neutral intermediaries; data sharing for good causes.
Data Act: Rules for sharing, accessing, and using data from IoT devices.
What are the main criticisms of the EU Data Strategy?
Over-regulation (AI Act, Data Act, GDPR, etc.)
Terms not fully aligned
Unclear if laws ease data sharing
Tension between data sharing and data minimization
What are other concerns about the EU Data Strategy?
Datafication: everything becomes data
Who benefits from data value?
Is a single EU data space feasible now?
What is a European Data Space?
A system enabling trusted data sharing between participants
What are Common European Data Spaces?
Data spaces for key economic sectors and public areas.
Sector-specific ecosystems for new products and services.
Sharing organizations gain more data, insights, services, or fees.
Question: do citizens/patients benefit?
European Health Data Space (EHDS)
Make health data easier to use.
Uses: research, innovation, public health, policy, personalized medicine.
Problem: lots of data, poorly used.
Health Data Space – Data Protection Rules
Only for purposes that help people/society
Keep identity hidden
Use secure environments
Health Data Uses:
Primary: Help doctors access data → continuity of care
Secondary: Help policymakers, researchers, innovators; remove access obstacles
Goal: to foster a genuine single market for electronic health record systems.
EHDS – Patient Consent & Data Rules
Opt-out: data used by default unless opted out
Respect patient wishes while enabling public interest
Re-identification forbidden
HDS – Data for Secondary Use
HRs, health factors, genetic data, wellness apps, registries, clinical trials, medical device data
EHDS – Secondary Use Prohibited
No harmful or discriminatory decisions (job loss, insurance exclusion, loans)
No commercial exploitation (marketing)
No harmful products or services
No ethical or legal conflicts
EHDS – Who Benefits?
Patients (main)
Medical practitioners
Governments & policymakers
Researchers & scientists
Pharma & tech/AI health innovators
Big tech
Minister of Health NL
Data remains confidential, is shared by default (opt-out), patients can set limits, and existing safeguards stay in place.
What did Bart Jacobs say about IoT systems and processing?
IoT systems (like smart meters) must choose between central or local processing. This choice affects power and society, so it should be decided by politicians.
What does Lawrence Lessig say about politics and disagreement?
Politics is about disagreements on how to live, who gets what, and who decides. People argue about power, money, cooperation vs. conflict, and influence.
Opposing frames in technology debates?
RFID Platform: promotes RFID tech
Fellowship of the Chip: favors barcodes on everything

What did Kevin Ashton say about computers that know everything?
If computers knew everything through data, we could track all items, reduce waste and costs, and know when things need fixing or replacing.
What did Mark Weiser say about ubiquitous computing?
The best technologies fade into daily life. But too many sensors can hurt privacy and make people feel constantly watched.
IoT Action Plan – what drives social acceptance?
Respect for privacy and protection of personal data
Why is seclusion important biologically?
Privacy is a biological need; social stimulation alone isn’t enough
What happens when privacy is removed?
Totalitarian control → peer pressure, loss of personal voice, and no room for reason (think of nazi regime)
What can happen when you guard your boundaries?
People may guilt-trip you or dismiss your need for privacy.
What is the role of privacy in society?
Privacy is a counterbalance between the private and public sphere, protecting individuals from powerful societal actors (like the state or industry). It’s rooted in liberal political theory.
What did Edward Snowden say about “nothing to hide” and privacy?
Saying you don’t care about privacy because you have nothing to hide is like saying you don’t care about free speech because you have nothing to say.
CHARTER OF FUNDAMENTAL RIGHTS EU
Art. 7:
Everyone has the right to privacy — in their personal and family life, home, and communications.
Art. 52(1):
Limits on rights are only allowed if they are legal, necessary, reasonable, and protect the public interest or others’ rights.
What determines the effectiveness of fundamental rights?
Fundamental Rights Impact Assessment
Legislative Proposal
Request & Review work of European Standardisation Organisations
Roles of the European Commission
Policy-making
Legislative process
Executive / Pseudo-legislation
The European Commission is involved in shaping policies, proposing legislation, and executing or enforcing EU rules.
Article 290 TFEU – Delegated Acts
The Commission can make rules to add or change parts of a law.
Only for non-essential parts.
The goals, content, scope, and time limit must be clearly stated in the law.
Essential parts stay with the legislator.
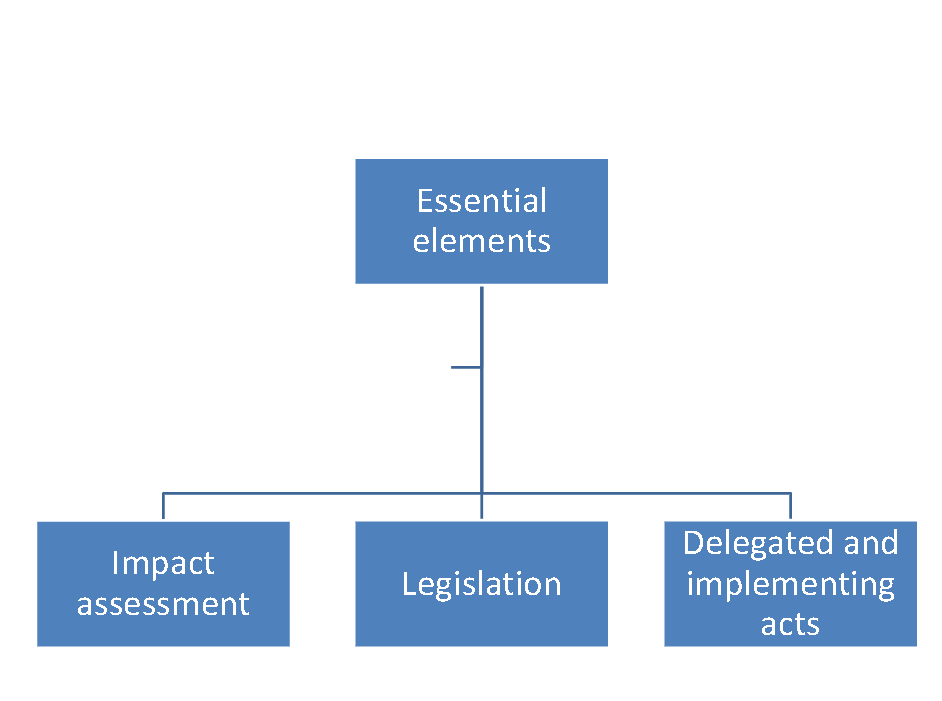
Essential Elements of an Area
Politically sensitive or controversial issues.
When fundamental rights might be seriously affected, needing EU legislature intervention.
Legislation Against Function Creep
The “less restrictive means test” helps reveal hidden motives behind laws.
It makes sure systems (like IoT) are used only for their stated purpose.
This helps prevent abuse and protect privacy in the future.
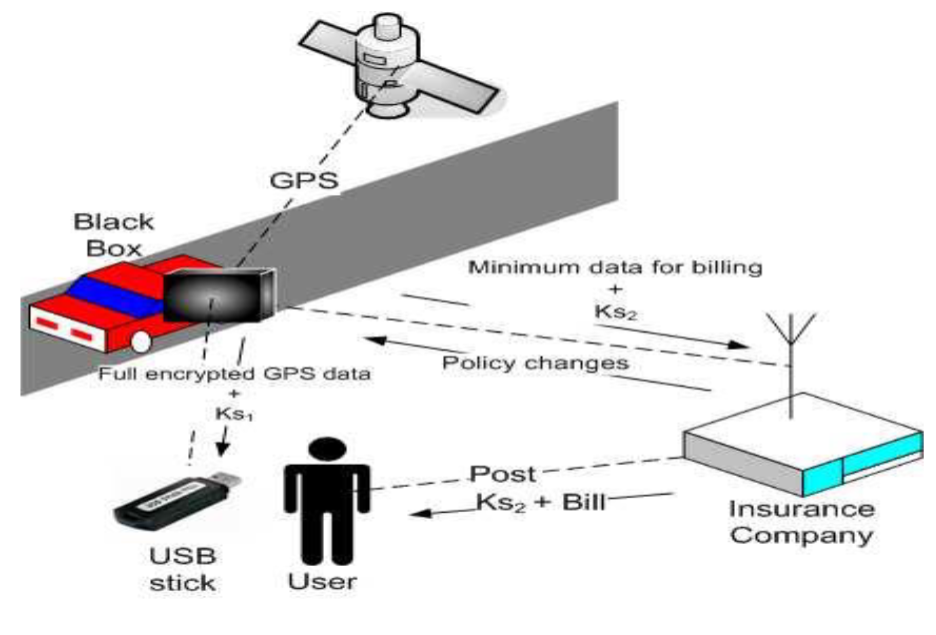
Privacy & Data Protection in the Regulation
Must follow data protection directives (95/46/EC & 2002/58/EC)
Data can’t be traceable during normal use
Manufacturers must inform users in the manual
Design must stop public & private systems from communicating
Must follow Privacy-by-Design principle
Regulation 2015/758 – eCall Regulation (Art. 15)
Cars must have a 112-based eCall system.
Extra services (by manufacturers or others) are allowed, but:
Must not distract drivers or affect eCall performance.
No personal data can be shared between eCall and private systems.
Must follow safety, security & data protection laws.
Must stay optional for consumers.
Future Group – European Justice Policy
Focus: Public security, privacy & technology.
Idea: Every action or object creates digital data, useful for security, but also raises privacy concerns.
What are the three layers in the Hourglass Model and their functions?
Application Layer: Applications use IP for connectivity.
Network Access Layer: Components deliver IP connectivity.
IP Layer: Provides a coherent mapping between the layers (IP = Internet Protocol).

Who are the players at the Application Layer and what do they do?
Application Layer = the apps you use on the internet.
Give services to Internet users
Can be client and provider (thanks to IP)
Work independent from ISPs (Internet Service Providers)
What does Unlimited Possibilities mean in the Application Layer?
Unlimited possibilities (Application Layer)
New apps appear all the time, like TikTok or Zoom.
Anyone can make an app.
Apps can be open for everyone or owned by companies.
Many types exist: websites, video, AI, smart devices.
👉 In short: There’s no limit — anyone can create something new on the internet.
What is the Network Access Layer?
75k+ autonomous networks
Each makes its own choices
Each serves a different market
Who are the players at the Network Layer and what do they do?
Moves IP packets — small pieces of data.
Sends them through radio, fiber, or cables.
Works for many users: homes, companies, governments.
Can be worldwide or local networks.
(Note: Moves IP packets around → an IP packet = a unit of information)
How do independent networks form the Internet?
How networks make the Internet
Many networks connect to each other.
They share data using IP packets.
They agree on how to send data.
Not all are directly connected.
👉 Together, they form the Internet — a big network of networks.
Why does the Internet work?
Apps:
Send data using IP
Internet looks like one cloud
Other app gets the data
Network:
Handles IP
Doesn’t care about apps
Works with new apps without changes
Can use different technologies
Why does collaboration matter for the Internet?
SORR
Standards organizations
Resource allocation and assignment
Registry maintenance
Open and bottom-up approach
explanation (Dutch):
Deze regels en organisaties zorgen ervoor dat het Internet overal hetzelfde werkt en dat iedereen nieuwe toepassingen kan toevoegen zonder het netwerk te breken.
What’s the difference between HTTP and HTTPS?
HTTP = not encrypted, anyone can see data
HTTPS = encrypted, only sender & receiver can read data
Stel je voor dat je een brief naar iemand stuurt. HTTP is alsof je de brief in een open envelop stopt: iedereen die langsloopt kan lezen wat erin staat. Dat is handig, maar niet veilig.
HTTPS daarentegen is alsof je de brief in een kluisje stopt dat alleen de ontvanger kan openen. Dit doet HTTPS door je gegevens te versleutelen met speciale sleutels (SSL/TLS-certificaten). Zo kan niemand stiekem meekijken tussen jouw computer en de website waar je mee communiceert.
Kortom: HTTP = open envelop, HTTPS = beveiligde kluis.
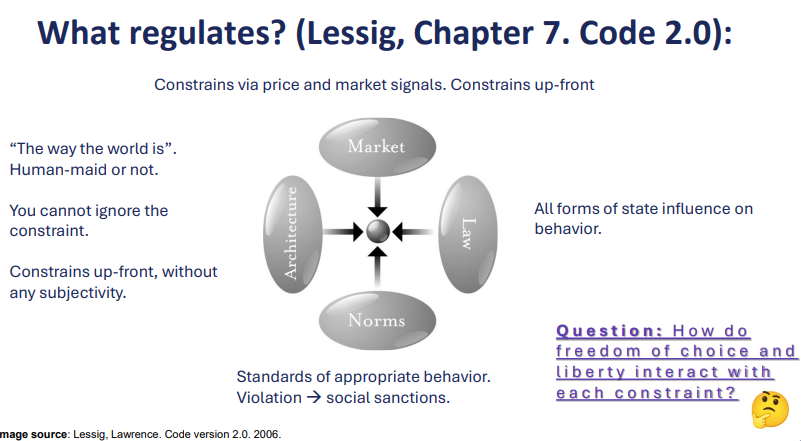
What is Lessig’s “Pathetic Dot” and what constraints shape it?
The pathetic dot = the individual, whose behavior is shaped by 4 constraints:
Law – rules enforced by government (e.g., copyright, privacy law).
Social Norms – community expectations (e.g., stigma, culture).
Market – prices & economic forces (e.g., paywalls, costs).
Architecture/Code – the environment or technology design (e.g., fences, software restrictions).
💡 Called “pathetic” because the individual is acted upon by all four forces.
How does law regulate the digital realm?
Law plays a major role online.
It regulates:
e-commerce
data protection
intellectual property (IP)
disinformation
freedom of expression
But remember: social norms, market, and code also shape the digital realm.
Example: Reducing car’s speed
Solution 1 (Law):
Command-and-control → rules, fines, cameras, police.Solution 2 (Architecture):
Speed bump → physical constraint, you must slow down or you’ll fly.

What is regulation through architecture/code in Lessig’s model?
A locked door ≠ command → it’s a physical constraint.
Architecture is a kind of law: it decides what people can or cannot do.
In the digital world → software + hardware shape behavior.
Examples: passwords, encryption.
What is techno-regulation in Lessig’s model?
Regulating behavior with technology.
A type of architecture regulation.
Made by governments or companies.
Examples:
End-to-end encryption
Infinite scrolling (Instagram, TikTok)
Paywalls
Multi-factor authentication
Geo-fencing (location boundaries)
Loot boxes
What are the problems of indirection in Lessig’s model?
Law works in two ways:
Direct regulation → government law directly controls behavior.
Indirect regulation → government uses other modalities (norms, market, architecture).
Problem: indirection by government can blur/misdirect responsibility and accountability.
What are the two domains in Law & Technology studies (Berg, 2011)?
Regulation of technologies → how law regulates tech.
Regulation through technologies → how tech itself regulates behavior.
What is the power of default settings (Kesan)?
Defaults = preselected options by software makers.
People usually stick with defaults (cognitive bias).
Can protect users or cause harm.
Examples: cookies, privacy settings, autoplay.
What is Privacy/Data protection by design?
Built into systems from the start (GDPR Art. 25).
Prevent problems instead of fixing later.
Works through the whole lifecycle.
Balanced with security + transparency.
Example: Signal → little data + end-to-end encryption.
What does “artifacts have politics” mean? (Winner / Yeung & Ranchordas)
Techno-regulation ≠ always good.
Technologies embed political decisions.
Shaped by the social/economic system.
Bias is often unintentional but built-in.
Myth of neutrality (Kranzberg): tech is not good, not bad, and not neutral.
What do Lessig and B. Jacobs mean by the power of code and coders?
Code shapes our daily lives.
Code reflects values, not just tech.
Controlling code = having power → "Code is law".
Coders are becoming like lawmakers.
IT rules affect privacy, access, control, freedom.
What does “Architecture is politics” and “embedded values” in technology mean?
Technology can contain values, power, and behaviors of people or groups.
These values can be embedded intentionally or unintentionally (Surden, 2017).
Can regulation be unintentional? (yes)
Regulation can happen as a side-effect of technology design.
Technology can steer people in subtle, implicit ways.
It can have unexpected consequences (Berg).
What are the advantages of technoregulation?
Efficient
Cheap
Strongly enforceable
Little flexibility
What are the disadvantages of technoregulation?
Not legitimate
Not accountable / lacks human interaction
Responsibility is unclear
Not transparent
Ignores differences
Limits freedom of choice
Why is techno-regulation a problem?
Tech lets governments and companies control people more.
Raises issues of responsibility and accountability (e.g., CSAM vs. encryption).
Examples: social media, video games.
What is tech ?
Technology = material & immaterial artefacts and processes
Includes: tools, machines, products, processes
Created through mental and physical effort
Purpose: solve problems or improve the status quo
Technology & Novelty
Tech change = hope, fear, or arrogance
1st Machine Age: Industrial Revolution → job loss, power shifts
2nd Machine Age: Digital networks, automation, platform economy
Characteristics of the Second Machine Age
Includes: networked computers, sensors, big data, algorithms, platforms
Core: data processing
Concerns: unemployment (automation), surveillance, deskilling (loss of knowledge, loss of privacy
Key atributes of emerging technologies 5
Radical novelty – something new & different
Fast growth – spreads quickly
Coherence – stays relevant over time
Impact – strong effect on society/economy
Uncertainty – outcomes not fully known
Gartner Hype cycle for emerging tech (just for illustration)
Gartner hype cycle is not important
1 innovation trigger : promosis what the tech could do
2 peak of inflated expectations : the promosise are made go into action
3 Trough of dissilusionment : the negative and difficulties
4 Slope of enlighenmet : people that use will use for other purposis
5 plateau of productivity : the people use it as intented to
Fjader (2020) : almost all tech are more likely to crash and burn without making a lasting impact on our lives (this is maybe important)
Non-state actors & their influence on technology
Non-state regulators (zoals adviesbureaus, bedrijven, organisaties) sturen technologie via hun normen & visies.
Voorbeelden
PwC noemt 8 grote technologische doorbraken die elk businessmodel beïnvloeden → organisaties moeten zich aanpassen.
Mandel (2009): technologieën zullen de samenleving hervormen op manieren die we nog niet volledig begrijpen.
Uitdaging = kracht benutten maar ook risico’s beheersen.
Stakeholder ( just know what it is)
anyone affected by or interested in a policy/decision
Government vs. Governance
Government = alleen state actors
Governance = state + non-state actors
Key takeaway about governance decision-making
Decision-making should involve relevant stakeholders
Sectors using governance approaches
Health
Environment
Internet
AI
Main goal of technology governance (OECD)
Implement shared values
Protect human rights
Elements of technology governance
SAIV
Stakeholder engagement
Assessing regulation
International cooperation
values & fundamental rights in the innovation process
Tools of technology governance (OECD)
PARCTD
Principles
Codes of practice
Regulation
Democratic participation
Technology assessment
Narrow approach to regulation
State influence by imposing & enforcing legal rules
Rule backed with legal consequence
Broad approach to regulation
All state actions to influence behavior
Examples: taxes, subsidies, resources, info, nudging, certifications, education campaigns
Broadest approach to regulation
All forms of influence on behavior (state & non-state actors)
Examples: corporations, communities, self-regulatory bodies, trade associations
The definition of regulation
Regulation is the control of risk or behavior by authority to solve problems or address collective tensions. usually through rules, monitoring, and influence.
Regulation: Characteristics MEFF
MEFF
Multi-disciplinary
Focus on risks
Embedded in politics (tensions, power)
Foundational role of law (policies, institutions, norms, practices)
Who regulates?
States (governments)
Communities / societal groups
Private sector: trade associations, companies, self-regulatory bodies
Why regulate?
Economic reasons: fix market failures (monopolies, public goods, info asymmetry, externalities) + foster innovation
Legal/societal reasons: protect human & fundamental rights
Risk management
Dominant framework for regulation (Yeung & Ranchordas)
Risk (focus shifted from law/economics to risk)
Aim of interventions in risk regulation
Reduce or control risk
Definition of risk
Probability/likelihood of harm, injury, or adversity
Formula for risk
Likelihood (or Probability %) x Impact (or Consequence)
Example of risk-based regulation
AI Act: risk-based AI classification system
Positive aspects of state regulation
BEPPP
Protects fundamental rights & freedoms
Provides legal certainty
Builds trust (esp. in tech)
Promotes social values
Enables/facilitates economic activities
Negative aspects of over-regulation
BIEF
Blocks innovation
Inflexible & complex rules
Focus on compliance over goals (following rules ipv doelen)
Enforcement is burdensome
Pros of Self-regulation
Expertise
Lower / No cost external enforcement
avoid reputaional damage
Setting your own norms can lead to better compliance
Cons of Self-regulation
Rule-making AND enforcement
Enforcement may be weak
Focus only on business interests rather than consumer/citizen interest
What is the impact of technological change on society and power?
Technological change doesn’t work in a straight line. Sometimes it brings good effects, sometimes bad. It’s unpredictable: new inventions can have unintended consequences. They change who has power and how it is used. Some groups or countries gain, others lose. Those who lose may resist the technology, while those who gain embrace it.
Digital Colonialism (Couldry & Mejias; Yeung & Ranchordas)
Colonialism: domination (legal, cultural, economic)
Data colonialism: global data extraction, with or without consent
Driven by US & Chinese tech giants (e.g., Google, Tencent) → profit from user data
Europe’s role: AI AND DATA PROTECTION (Europe risk of becomming a colonie)
What is the capacity for surveillance, control, and exploitation?
Granular legibility: highly detailed data enables new forms of control
Lives become ‘datafied’: Big Data → algorithmic control
Opacity: “A one-way mirror that allows those on top to surveil those below, but they cannot understand the algorithmic black boxes regulating daily life” (Yeung, 2018, p. 13)
What is the platform economy?
Platforms act as modern middlemen connecting users, producers, and services.
What powers platforms?
Devices (smartphones, computers)
Algorithms (match users, recommend content)
Cloud computing (store & process data)
Massive user networks (scale and reach)
How does the platform economy blur roles?
It blurs lines between:
Consumer ↔ owner-producer
Employee ↔ employer