Module 4: Cryptographic algorithms: Symmetric and Asymmetric
1/15
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
16 Terms
How does Symmetric Cryptography (AES) work?
Advanced Encryption Standard (AES) became a standard in 2002 when it replaced DES and 3DES
Block and key length are respectively 128, 192 or 256 bits
So far, AES has shown to be resistant to all known cryptoanalysis methods
It is simple, fast and easy to implement in hardware and/or software
AES (Advanced Encryption Standard) is a block cipher, meaning it encrypts fixed-size blocks of data
This is the process for each block:
AddRoundKey: Each byte in the table is combined with a “round key”, which is derived from the key
SubBytes: Each byte in the table is replaced with another based on a lookup table
ShiftRows: Each row in the table is shiftet cyclically by a certain number of steps
MixColumns: An invertible linear transformation is performed on each column in the table
What are Block Ciphers?
Block cipher: encrypt blocks of data with a fixed length/size.
Divides data into blocks that are x number of bits and encrypts them to blocks that also have x number of bits.
Block sizes vary depending on the algorithm (56 to 256 bits)
Symmetric encryption using the Block cipher method are: DES, 3DES, AES, RC6, Blowfish, Twofish, Serpent and IDEA
What are Stream Ciphers?
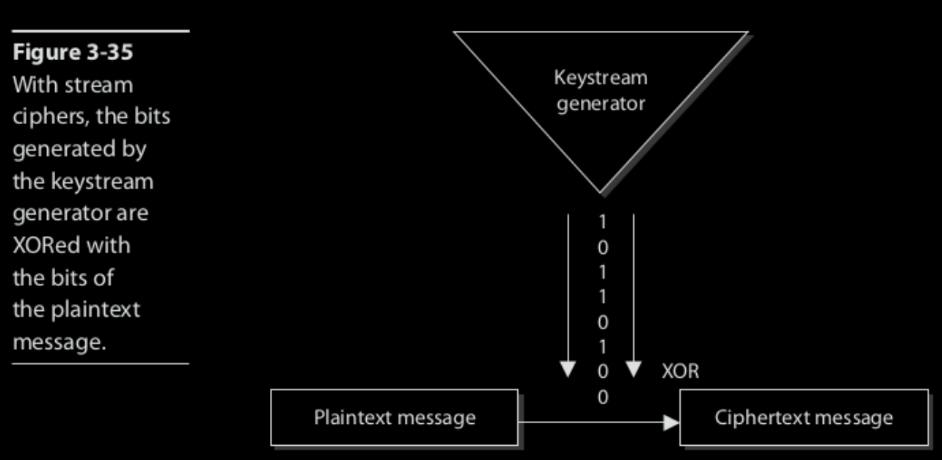
A stream cipher is a type of symmetric encryption that encrypts data one bit or one byte at a time, instead of in fixed-size blocks (like AES does).
It’s often used for real-time data streams such as voice, video, or wireless communication.
A keystream generator uses a secret key to produce a pseudorandom sequence of bits called the keystream.
Each bit of plaintext is XORed with the corresponding bit from the keystream.
The result is the ciphertext.
Decryption uses the same keystream and XOR operation:
(Plaintext ⊕ Keystream) ⊕ Keystream = PlaintextSymmetric encryption using the Stream cipher method are: Salsa20, ChaCha, SEAL, TWOPRIME, RC4, A5(GSM)
How do we use a Block Cipher?
NIST defines several was to do it (modes of operation)
A block cipher encrypts data in fixed-size blocks — usually 128 bits (16 bytes) at a time.
It uses the same secret key for both encryption and decryption (so it’s symmetric).
If your message is longer than 16 bytes, it’s split into multiple blocks — and if it’s shorter, padding is added.
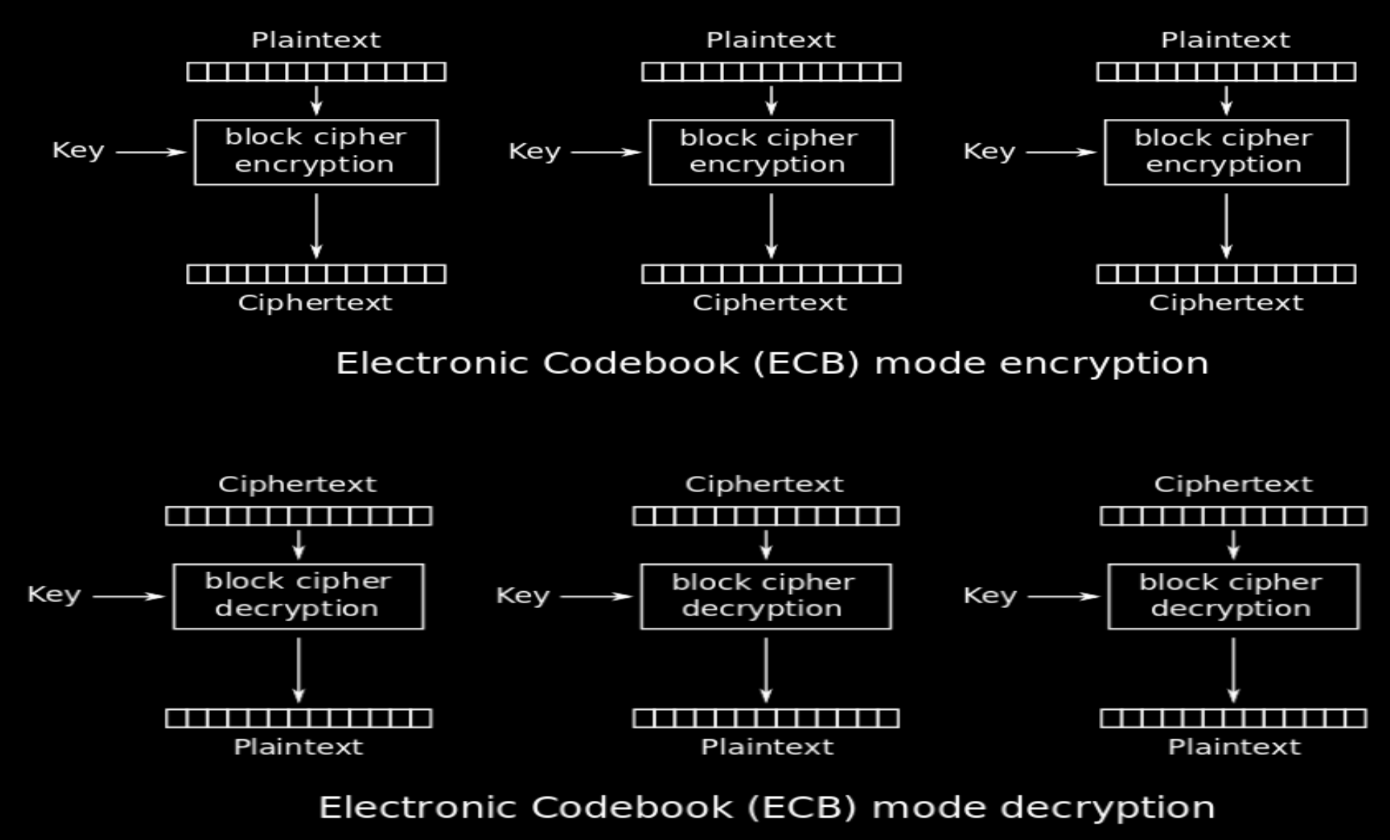
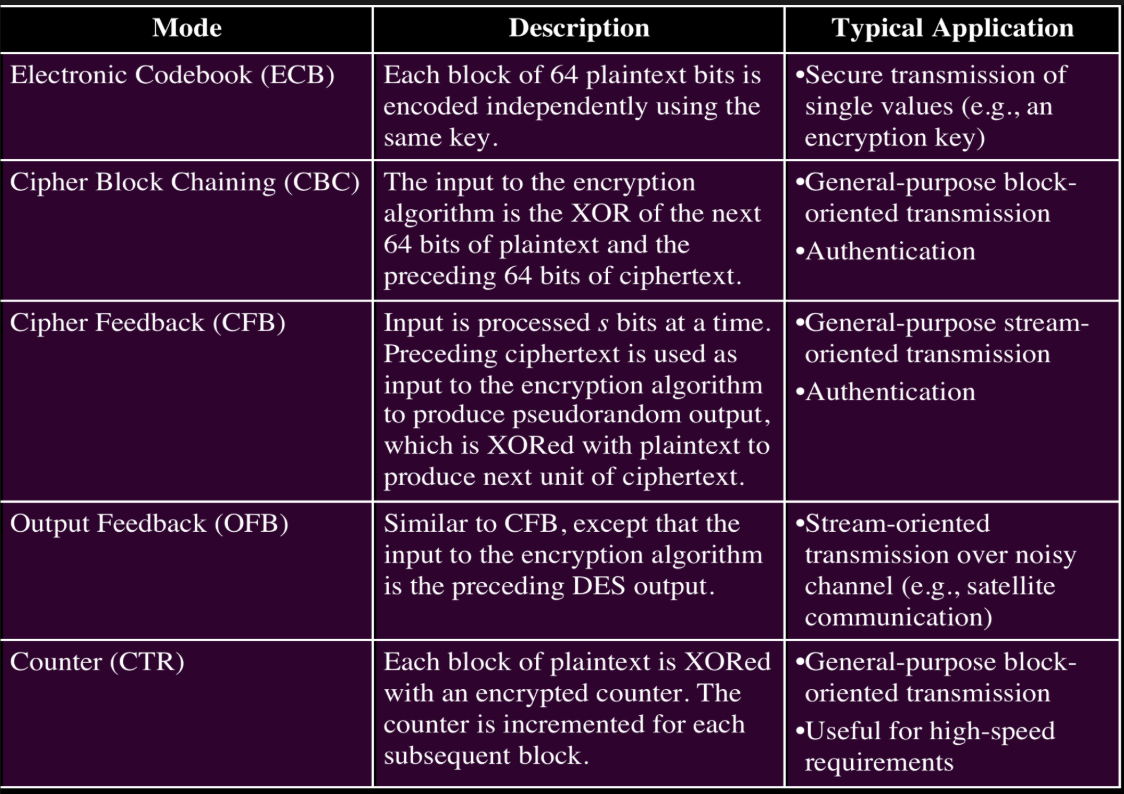
What’s the mode of operation for block cipher called Electronic Codebook (ECB)?
Electronic Code Book (ECB) encrypts each block of data (Plaintext) with the same key
The easiest way to use symmetric encryption
Weaknesses:
does not hide data patterns
not suitable for long messages or large files
vulnerable to replay attacks
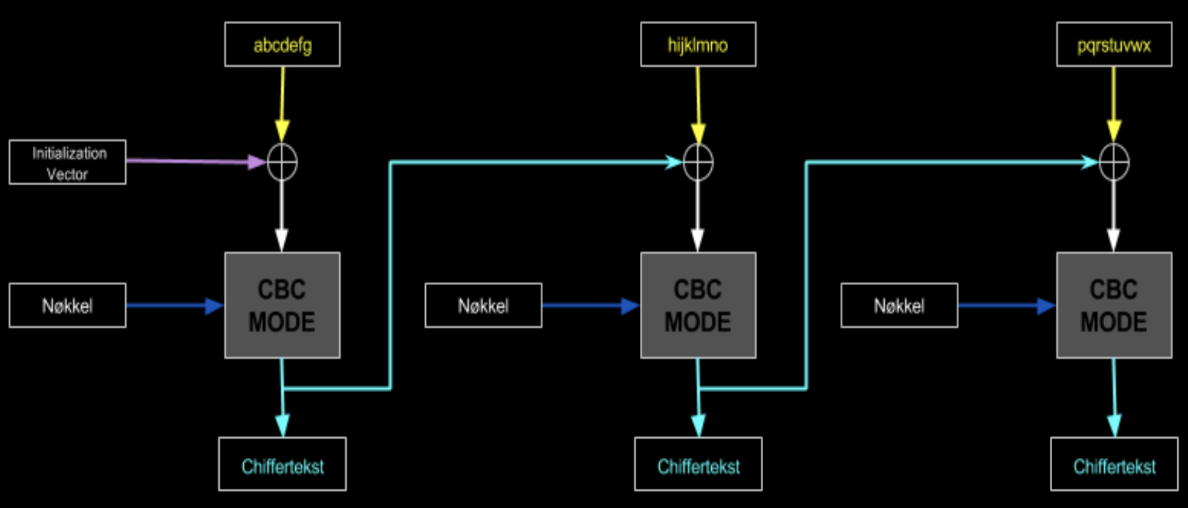
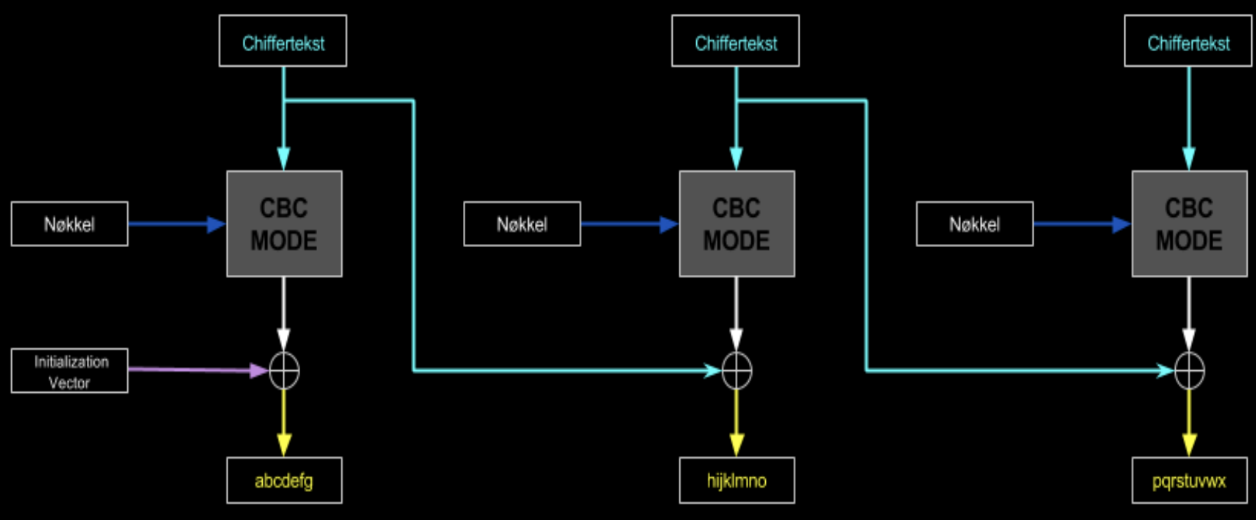
What’s the mode of operation for block cipher called Cipher Block Chaining (CBC)?
Cipher Block Chaining (CBC) solves the problem with Electronic Code Book (ECB) by randomizing the blocks before they are encrypted.
An XOR operation is performed on each subsequent plaintext block with the previous digit block and then performs the encryption.
To make each message unique, an initialization vector IV must be used inm the first block
The initialization Vector does not have to be secret, but it is important that it is random and that it is never used again with the same key
How do we use CBC (Cipher Block Chaining) mode to decrypt ciphertext?
In CBC decryption, each ciphertext block is decrypted first, then XORed with the previous ciphertext block (or the IV for the first block) to recover the plaintext.
What is message padding?
Symmetric algorithm such as 3DES and AES operate on blocks of plaintext data. For this to work, the length of plaintext must be exactly equal to the block length used by the algorithm. In reality, plaintext can be longer or shorter than an entire block (64, 128, 192 or 256 bits)
To get a whole block, a method called “padding is used. Padding is to add a few extra bits at the end of the data/text to get a block of 64 (3DES) or 128 bits (AES).
What are Block Cipher modes of operation and why do we need them?
ECB: Enkel, men utrygg – ingen sammenheng mellom blokker.
CBC: Kobler blokker sammen via XOR → bedre sikkerhet.
CFB/OFB: Gjør blokkchifferet om til strømchiffer – brukes for strøm-data.
CTR: Bruker teller som input – rask og kan parallellisere
What’s the strengths and weaknesses of symmetric cryptography?
Strengths:
Much faster (less computationally intesive) than asymmertric systems
Hard to break is using a large key size
Weaknesses:
Requires a secure mechanism to deliver keys properly
Each pair of users needs a unique key, so as the number of individuals increases, so does the number og keys, possibly making key management overwhelming
Provides confidentiality but not authenticity or non-repudiation
How does Asymmetric Cryptography (RSA) work?
Diffie and Hellman proposed the solution of using different keys for encryption and decryption.
The basis for asymmetric cryptography is the identification of a one-way function that is easy to calculate but difficult to invert without further information
Rivest-Shamir-Adelman (RSA) is an asymmetric encryption algorithm
RSA is a widely used asymmetric cryptographic algorithm. The algorithm is based on and depends on the degree of difficulty of factorizing large numbers (prime numbers)
Both Diffie-Hellman and RSA use Modular Math
What’s the strengths and weaknesses of asymmetric cryptography?
Strengths:
Better key distribution than symmtric cryptography
Better scalability than symmetric systems
Can provide authentication/authenticity and non-repudiation
Hard to break if using a large key size
Weaknesses:
Works much more slowly than symmetric systems
Mathematically intensive tasks specially when using large keys.
What is a Digital Signature and how can we use it to ensure desired security properties?
Digital signature: “A value computed with a cryptographic algorithm and associated with a data object in such a way that any recipient of the data can use the signature to verify the data’s origin and integrity.
We want a digital signature to have the following properties:
Unforgeable: it should be difficult for anyone other than the sender (Alice) to produce the signature (Alice, M)
Authentic: The recipient Bob can confirm that Alice signed the message/document M
Non-repudiation: Alice can not deny having produced the signature
Integrity: after being sent/transmittet, the message M can not be changed or tampered with.
Not reusable: the signature cannot be removed or disassembled and reused for another message.
Both symmetric and asymmetric encryption are suitable for digital signatures
How can Digital Signing with Symmetric Algorithms work?
When Alice and Bob want to ensure that a message is authentic and has not been changed, they can use a Message Authentication Code (MAC).
1. Alice and Bob must share a secret key K
Both sides use the same key.
The key must be exchanged over a secure channel, otherwise an attacker could forge MACs.
2. Alice sends a message with a MAC
Alice takes:
the message, and
the secret key K, and runs them through a MAC function (often a hash-based function like HMAC).
This produces a MAC value.
Alice sends (message + MAC) to Bob.
3. Bob verifies the message
Bob receives the message and MAC from Alice.
He uses the same key K to recompute the MAC on the received message.
If Bob’s computed MAC matches the MAC Alice sent:
→ The message is authentic and unchanged.If the MACs do not match:
→ The message is either altered or not from Alice, and Bob rejects it.
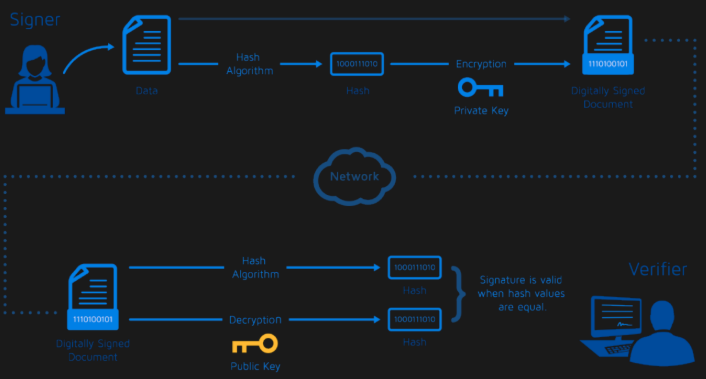
How can Digital Signing with Asymmetric Algorithms work?
Digital signatures allow Alice to prove that a message really comes from her and has not been modified.
This is done using asymmetric keys—a private key for signing and a public key for verification.
Alice creates a hash of the message and encrypts the hash with her private key to produce a digital signature. Bob decrypts the signature using Alice’s public key and compares the result to the hash of the received message. If they match, the signature is valid.
What are the challenges of using Asymmetric Cryptography?
How can Bob be sure about that it is actually Alice’s public key and not someone else’s?
Mybe Eva/Eve made a key pair, published the public ket and pretended to be Alice?
One solution: Trusted Third PArties (TTP)